Introduction
As blockchain technology advances, the ecosystem sees an influx of new protocols and increased user engagement, attracting substantial investments. This growth is accompanied by a heightened risk of hacker attacks, which can lead to significant financial losses for protocol operators and users alike.
In such a dynamic environment, the importance of a reliable security monitoring platform cannot be overstated. These platforms are essential for the early detection of potential security threats. Once an attack is identified, the platform alerts users promptly, allowing them to take immediate action to mitigate the impact. This timely response capability is crucial in preventing larger losses and ensuring the overall safety and resilience of blockchain transactions and operations.
What is a Security Monitoring Platform?
A security monitoring platform for blockchain is a critical tool designed to constantly oversee the network for any signs of malicious activity or vulnerabilities. This involves the real-time analysis of transactions, smart contract executions, and overall network behavior to detect anomalies that could indicate a security threat.
Why Projects Need Security Monitoring Platforms
Once a decentralized finance (DeFi) protocol is live, it immediately faces various security challenges that can threaten its operations and user assets. Here are key reasons why security monitoring platforms are essential:
- External Dependencies: DeFi projects often depend on external services such as oracles or interoperability bridges to function. These external connections are critical but can introduce vulnerabilities if compromised. Security monitoring platforms can detect anomalies in these dependencies, alerting teams to potential threats promptly.
- Zero-Day Attacks: Zero-day attacks represent a significant threat as they exploit previously unknown vulnerabilities. These attacks are particularly dangerous because they can occur without detection, allowing attackers to inflict damage or steal assets. Security monitoring platforms use advanced algorithms to detect abnormal patterns and behaviors that may indicate the presence of such exploits, providing an early warning system.
- Unaudited Contract Upgrades: It is common for DeFi protocols to frequently update their systems to add new features or address known bugs. However, some of these updates may be pushed live without comprehensive audits, introducing new vulnerabilities. Security monitoring platforms can detect and alert users about potential security threats that may arise from these new updates. This capability ensures that even if a new vulnerability is exploited, the platform can immediately inform users, allowing them to take swift action to mitigate the attack.
By implementing a robust security monitoring platform, DeFi protocols can enhance their resilience against attacks, protect user assets, and maintain trust within the community.
The Critical Standards of Security Monitoring Platforms: Emphasizing False Positives (FP)
In the realm of security monitoring platforms, the metrics of False Positives (FP) and True Positives (TP) play pivotal roles in determining the system's effectiveness. While True Positives are essential for identifying real threats accurately, the impact of False Positives deserves special attention due to its broader implications on operational efficiency and trust.
False Positives (FP) occur when a security system incorrectly identifies benign activities as threats. This misidentification can lead to several negative consequences:
- Operational Disruption: Each false positive requires investigation by the security team, consuming valuable time and resources that could be better spent on genuine threats. This inefficiency not only strains resources but also diverts attention from real security incidents.
- Credibility Loss: A high rate of false positives can erode trust in the security monitoring platform. Frequent false alerts condition users to ignore warnings, potentially leading to complacency. In a scenario akin to the "boy who cried wolf," important alerts might be dismissed as just another false alarm, increasing the risk that actual threats go unaddressed.
- Resource Drain: Continually verifying the accuracy of each alert places an unnecessary burden on the personnel. Over time, this can lead to fatigue, reduced vigilance, and even burnout among team members tasked with managing security alerts.
- Delayed Response: When teams are overwhelmed with false positives, the response time to actual threats can be significantly delayed. This delay can be critical, as the speed at which a threat is neutralized often determines the extent of damage it can cause.
Minimizing false positives is therefore not just about reducing annoyance; it's about maintaining operational integrity and ensuring that real threats receive the swift and serious attention they require. Effective security monitoring systems must strike a delicate balance—maximizing true positives while minimizing false positives—to provide reliable and efficient protection.
Phalcon: The Blockchain Security Monitoring Platform with the Lowest False Positive Rate
Phalcon is an innovative platform developed by BlockSec that can monitor hack attempts in real time. It helps users and protocol operators detect suspicious transactions and receive instant alerts, so they can take response measures to mitigate losses.
Phalcon distinguishes itself by maintaining a false positive rate of less than 0.001%. This precision is achieved through sophisticated AI algorithms and a deep understanding of DeFi Semantics and blockchain mechanics, which allows Phalcon to distinguish between legitimate and malicious activities with unparalleled accuracy.
Even more, users can enhance precision by customizing their own trigger rules, such as changes in token amounts, prices, key variables, sensitive events, and function invocations. An alert or action is only triggered when a transaction meets both the specified risk level and user-defined trigger rules, further minimizing false positives to the lowest level possible.
Phalcon: Comprehensive Risk Monitoring in Blockchain Operations
Phalcon extends its monitoring capabilities beyond mere attack detection, encompassing a wide range of operational risks within blockchain projects. It keeps a vigilant eye on critical changes such as modifications to admin keys, role grants, key variables, and contract upgrades. Additionally, Phalcon monitors adjustments in time locks, new proposals, and price oracles, ensuring comprehensive oversight and enhanced security throughout the lifecycle of blockchain operations.
Beyond Threar Monitoring: The Solution of Attack Blocking
While conventional monitoring platforms focus on detection and reporting, Phalcon goes a step further by integrating direct attack blocking mechanisms. This innovative approach addresses the limitations of traditional systems, where the time between threat detection and response can be critical.
The Limitations of Mere Attack Monitoring
Despite the capability of monitoring platforms to identify threats, there are inherent limitations to consider. There are instances where the intended recipients may not immediately notice these alerts, resulting in delayed responses, even slight delays can mean missing the optimal window for effective countermeasures. Additionally, even if an alert is detected immediately, it often requires discussions and consensus among multiple parties to decide on the best course of action, which involves signing off on these measures. This process usually takes several hours, further delaying the response, and potentially compromising the effectiveness of the interventions.
Direct Attack Mitigation with Phalcon
Phalcon is revolutionizing blockchain security with its proactive approach to threat mitigation. Upon detecting an attack, Phalcon goes beyond merely notifying users; it actively intervenes to mitigate potential damages. This direct action includes capabilities such as pausing pools, withdrawing funds, or even pre-emptively transferring assets to predetermined accounts specified by the user.
By implementing these immediate defensive measures, Phalcon effectively reduces potential losses to zero, providing a robust layer of security that actively prevents financial harm before it can occur. Phalcon equips its users with advanced real-time monitoring and proactive intervention capabilities, significantly enhancing the security, operational efficiency, and financial stability of their blockchain activities.
Record-Proven Attack Monitoring and Blocking Capability
Phalcon's capabilities in threat monitoring and attack blocking have been rigorously tested in real-world scenarios, showcasing its effectiveness in protecting digital assets.
For instance, during an attack on Loot, where a malicious proposal aimed to drain 477 ETH from LootDAO, Phalcon immediately detected the threat and notified the project's team, successfully preventing a potential loss of approximately $1,200,000. Similarly, when Paraspace faced an attack, Phalcon swiftly initiated a rescue transaction that saved around $5,000,000 worth of assets.
Over the course of two years of operation within its internal systems, Phalcon has successfully blocked over 20 attacks, saving digital assets valued at over $15 million.
How to subscribe to Phalcon?
Phalcon is a SaaS platform. To subscribe to Phalcon, visit BlockSec's official website and navigate to the Phalcon product page. There, you will find information about the different subscription plans and pricing options. Choose the plan that best suits your organization's needs and budget. Once you have selected a plan, follow the instructions to complete the subscription process, which may involve providing your contact and payment details.
Access the platform: https://phalcon.blocksec.com/block
Subscribe directly: https://account.blocksec.com/login?referer=https%3A%2F%2Fapp.blocksec.com%2Fsubscribe%2Fblock%2Fcustomize
Book a demo: https://calendly.com/blocksec/phalcon-collaboration
Conclusion
In the dynamic and rapidly evolving world of blockchain technology, robust security is essential for maintaining trust and reliability. Phalcon stands out as a significant leap forward in this domain, with its low false positive rate and superior attack blocking capabilities. Offering more than mere detection, Phalcon actively prevents threats, ensuring that blockchain operations are both secure and efficient.
Phalcon transcends the role of a conventional tool; it acts as a comprehensive security partner for blockchain projects. Its advanced capabilities support these projects in safeguarding their operations against the diverse and ever-growing threats in the digital landscape. This level of protection is crucial for any blockchain endeavor aiming to maintain integrity and confidence among its users.
About Phalcon
🔗 https://blocksec.com/phalcon

Phalcon is a security platform developed by BlockSec to monitor and block hacks. The system detects suspicious transactions, instantly alerts users, and takes automated actions in response.
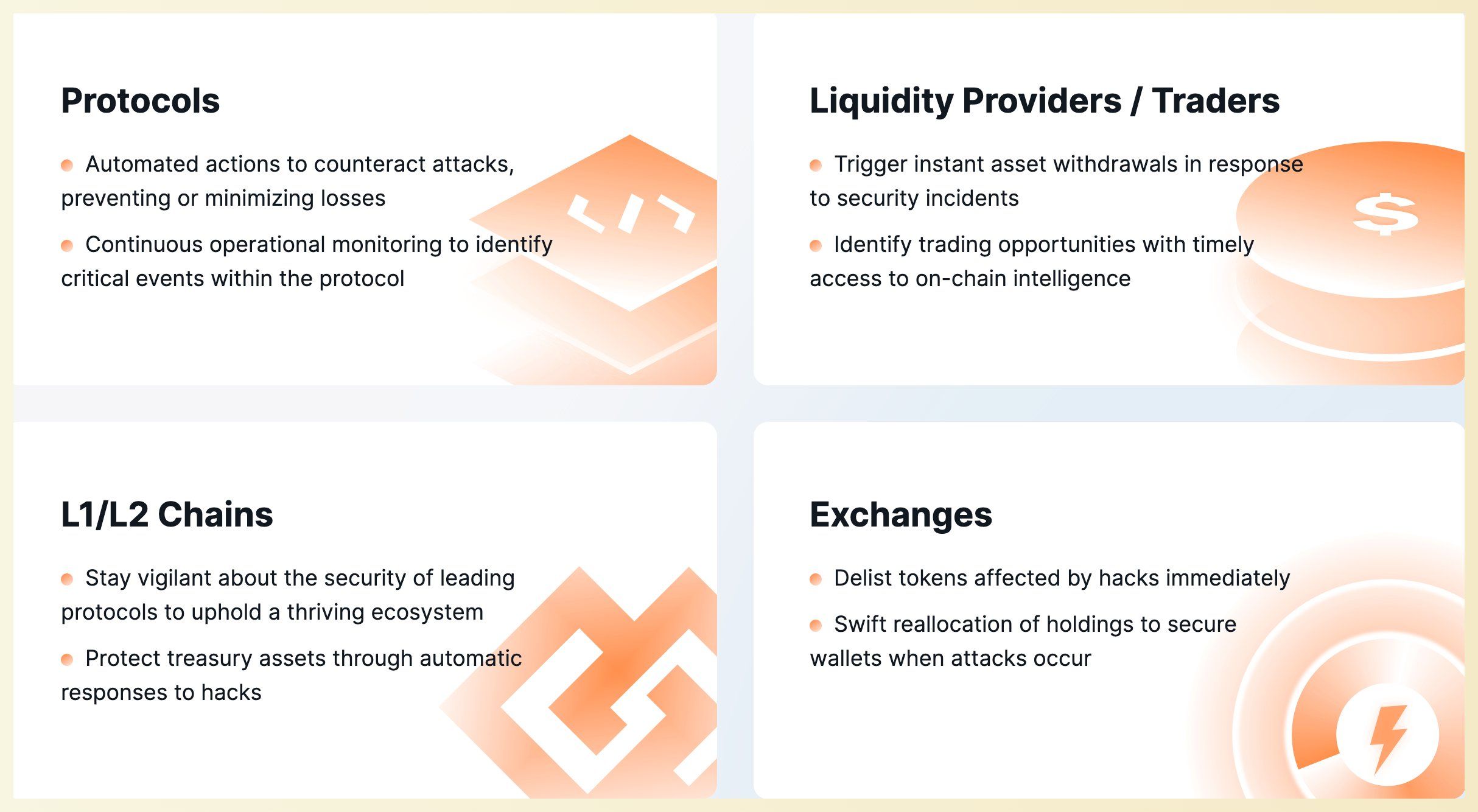
Phalcon's Key Advantages:
- Precise detection with minimal to zero FPs.
- Monitors both hacks and operational risks like privilege changes.
- Initiates automatic actions, with support for user-defined responses.
- Enables code-free configuration of monitors and actions.




