Those who cannot remember the past are condemned to repeat it.
In 2023, we've seen many security incidents that have caused serious losses to the community. They were tragedies for those affected. However, these incidents provide lessons to warn the community that security should be a priority.
Among the incidents, BlockSec handpicked ten exceptional cases, each with a unique reason. Some were rife with high drama; some featured "innovative" attack strategies, some led to significant financial losses, and some exploited previously unknown attack surfaces.
In this blog, we will illustrate the top ten security incidents that are worth mentioning in 2023 and their reasons. For each security incident, we will also present the root cause and the attack steps in separate blog posts.
#1 Harvesting MEV Bots by Exploiting Vulnerabilities in Flashbots Relay
Summary
On April 3, 2023, an attacker leveraged a vulnerability existing in the Flashbots relay to attack multiple MEV Bots, profiting around $20 million. The root cause of this attack is that a private transaction could be leaked to the public pool under certain conditions, and the attacker could back-run the leaked transaction to get profits.
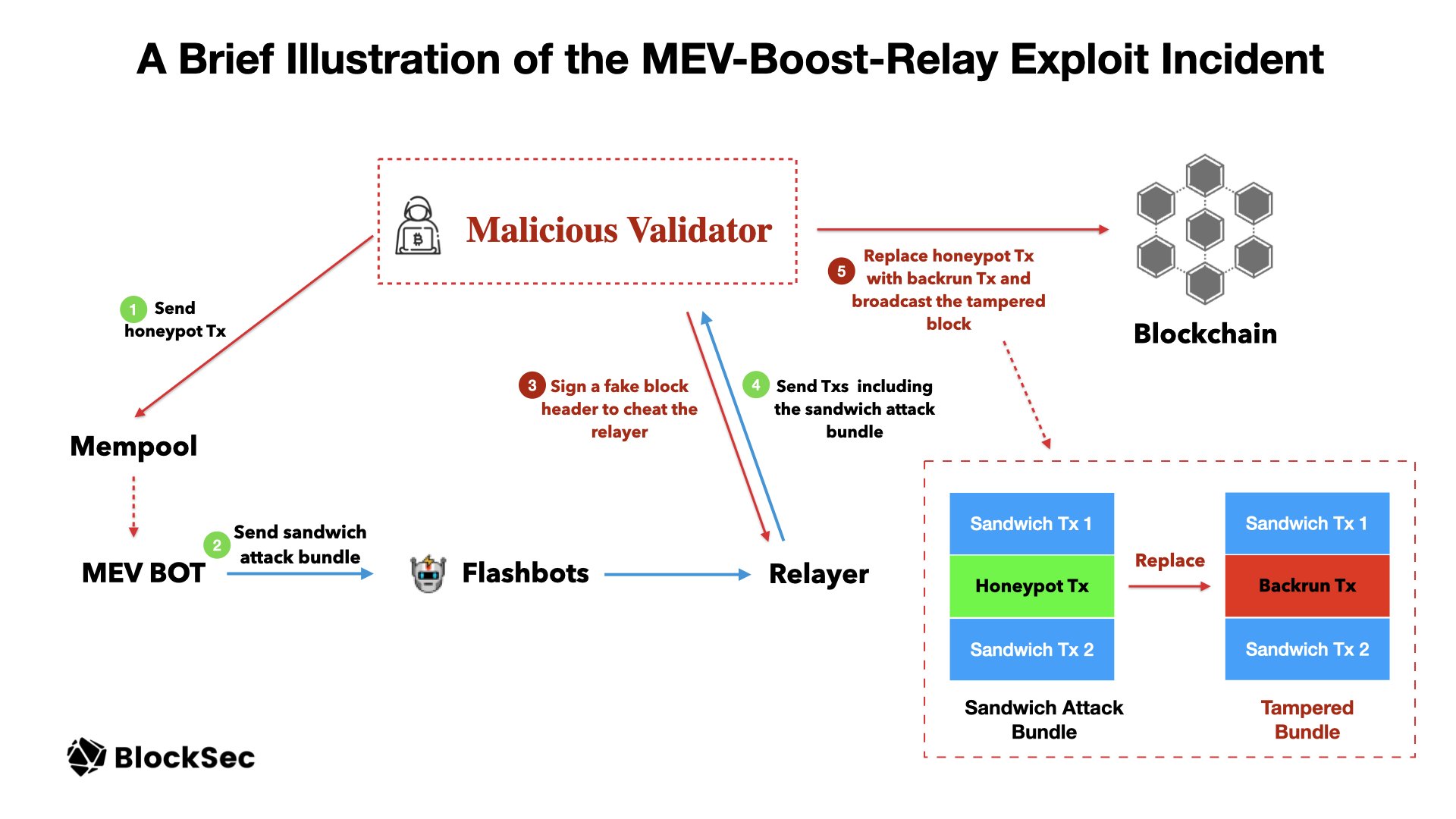
Reason for Selection
The attacker used sophisticated methods to harvest MEV Bots by exploiting a Flashbots zero-day vulnerability, creating honeypot transactions to lure victims, and implementing tactics to evade detection. This is, so far, the most sophisticated attack, which combines the vulnerability in underlying blockchain infrastructure with a leveraged attack strategy that has had a significant financial impact.
🧐 Learn about the root cause and the attack steps in detail.
#2: Euler Finance Incident: The Largest Hack of 2023
Summary
On March 13, 2023, Euler Finance suffered a flash loan attack on its lending pool, leading to losses of nearly $200 million. The attack stemmed from the donateToReserves() function lacking insolvency checks. This omission allowed attackers to contribute assets from a heavily leveraged position, reducing the position's health below 100% and incurring bad debt.
Euler's design incorporates a dynamic close factor for soft liquidations, meaning the lower the health of a position, the more collateral is eligible for liquidation—up to 75% in the event of bad debt, based on this incident's data. The liquidation of substantially discounted collateral, therefore, permitted the attacker to settle the flash loan and secure a profit.
Reason for Selection
A record-breaking $197 million in funds was stolen by a 20-year-old Argentinian named Federico Jaime, who presented the media with “a winding, sometimes confusing, and even contradictory narrative.” Nonetheless, “all of the recoverable funds” were later returned to Euler Finance's treasury address. However, a small portion of them (around $200K) was “unwittingly” sent to the Lazarus Group—an alleged state-sponsored North Korean crime syndicate sanctioned by the US Treasury.
🧐 Learn about the root cause and the attack steps in detail.
#3: KyberSwap Incident: Masterful Exploitation of Rounding Errors with Exceedingly Subtle Calculations
Summary
On November 23, 2023, there were a series of attacks targeting KyberSwap. These attacks resulted in a total loss of over $48 million. The fundamental issue originated from incorrect rounding direction during KyberSwap's reinvestment process. This subsequently led to improper tick calculations and, ultimately, to double counting of liquidity.
Reason for Selection
This 2023 attack stands out for its complexity, featuring exceptionally nuanced calculations and serving as a prime example of the many precision-related security incidents that have significantly tested the community. Moreover, after extensive negotiations with authorities, the attacker issued a provocatively toned message to the public, asserting a demand for total control over the protocol.
🧐 Learn about the root cause and the attack steps in detail.
#4: Curve Incident: Compiler Error Produces Faulty Bytecode from Innocent Source Code
Summary
On July 30, 2023, a series of exploits targeted multiple Curve pools, resulting in losses of millions of dollars. It was a typical reentrancy attack with a non-typical root cause, stemming from a compiler bug that led to the absence of reentrancy protection. Specifically, there was a mistake in which the reentrant locks for different functions within a smart contract were assigned different storage slots. As a result, smart contracts compiled using Vyper versions 0.2.15, 0.2.16, and 0.3.0 were vulnerable.
Reason for Selection
The vulnerability originated from the compiler, not the source code. It's the first time a compiler bug has led to a huge financial loss.
🧐 Learn about the root cause and the attack steps in detail.
#5: Platypus Finance Incidents: Surviving Three Attacks with a Stroke of Luck
Summary
Platypus Finance is a legendary DeFi protocol that miraculously endured three successive attacks, as follows:
- On February 17, 2023, it experienced a hack due to an incorrect solvency check, resulting in a total loss of about $9.05M. Of this, $2.4M was rescued with BlockSec's help. Approximately 380K tokens were stuck in the Aave contract and were then returned.
- On July 12, 2023, it was hacked, with around $50K lost due to ignoring the price gap between stablecoins.
- On October 12, 2023, it suffered from price manipulation attacks, with around $2.2M lost. After negotiating with the exploiter, 90% of the stolen funds were returned.
It is said, “A person's destiny, of course, depends on one's own efforts, but one must also consider the course of history.” Obviously, the project is lucky to survive all those attacks. Our analysis of these three exploits shows that the logical flaws could be avoidable -- if with careful audit or more active security measures.
Reason for Selection
- Surviving once is tough, but doing so thrice must be considered legendary.
- The project was hit by three distinct attacks, each targeting a different vulnerability.
- The proactive actions by BlockSec helped the project to rescue $2.4M.
🧐 Learn about the root cause and the attack steps in detail.
#6: Hundred Finance Incident: Catalyzing the Wave of Precision-Related Exploits in Vulnerable Forked Protocols Throughout 2023
Summary
On April 16th, 2023, Hundred Finance, a Compound v2 fork, was attacked, leading to a loss of about $6.8 million. The attack involved two primary root causes:
- An incorrect rounding issue;
- Empty markets that allowed the attacker to manipulate the exchange rate.
Specifically, the precision issue is exploited to affect the redemption and withdrawal of collateral. Markets or pools that are not properly initialized may face a liquidity shortage, which can lead to manipulation and a resulting liquidity imbalance between the underlying asset and the corresponding share token (e.g., Compound's cToken). Consequently, the share token's price may inflate, allowing it to be used as collateral—with only a minimal amount, or slightly more, of the original asset—to borrow other valuable underlying assets. Ultimately, the attackers were able to redeem and withdraw the original underlying asset due to a loss of precision.
This incident on Hundred Finance, and a subsequent one targeting HopeLend, an Aave v2 fork, unveiled a new paradigm of exploitations that could potentially target these two prominent protocols and their forks by manipulating the LP token rates. Subsequently, a series of similar attacks was observed.
Reason for Selection
Hundred Finance, the first Compound V2 fork to suffer a hack due to precision loss, set the stage for a series of similar DeFi security breaches. Moreover, this incident may have catalyzed the subsequent wave of attacks on Aave V2-forked protocols.
🧐 Learn about the root cause and the attack steps in detail.
#7: ParaSpace Incident: A Race Against Time to Thwart the Industry's Most Critical Attack Yet
Summary
On March 17, 2023, due to a vulnerability in the price oracle, ParaSpace became the target of a hacker attack. After the hacker's three failed attempts, the BlockSec Phalcon system intervened in a timely manner, saving over 5 million dollars worth of ETH through a rescue operation.
Reason for Selection
Industry's Most Important Block: over $5M rescued by BlockSec Phalcon System
🧐 Learn about the root cause and the attack steps in detail.
#8: SushiSwap Incident: An Attempt Rescue Leads to a Series of Copycat Attacks
Summary
On April 9, 2023, SushiSwap fell victim to an exploit caused by an Unverified External Parameter. The protocol itself was unscathed, but users who had granted permissions to the RouteProcessor2 contract were the primary targets. The nature of the attack, which focused on users with active authorization to the contract and its ease of replication, led to substantial user losses.
BlockSec successfully rescued 100 Ether and returned to the victim. A whitehat with the username @trust__90 made the first attempt to rescue funds, but this effort unfortunately failed. The method used by the whitehat was easily replicable and only aimed at saving a small portion of the total funds at risk. This opened the door for attackers to execute multiple copycat transactions, effectively draining most of the funds.
Reason for Selection
- SushiSwap, which was under attack, is a leading protocol on Ethereum with a large user base. The attack had a wide-ranging impact.
- The whitehat rescue unfortunately failed, leading to several copycat attacks. This raises questions about how to perform a whitehat rescue and how to manage it correctly.
🧐 Learn about the root cause and the attack steps in detail.
#9: MEV Bot 0xd61492: From Predator to Prey in Flash Loan Exploit
Summary
On August 3, 2023, an MEV Bot on Arbitrum was attacked, resulting in a loss of $800K. The root cause of this attack was Insufficient User Input Verification. The attacker deceived the "Arbitrage MEV Bot" (0x8db0ef) into borrowing from the "Vault MEV Bot" (0xd61492), thereby activating the flash loan mechanism. Simultaneously, the attacker, posing as a flash loan provider, appropriated all assets loaned to the "Arbitrage MEV Bot" and seized the approval from the "Vault MEV Bot".
Considering the intricate interactions between MEV Bots and their lack of open-source verification, it's perplexing how the attacker pinpointed and navigated this elaborate exploit path.
Reason for Selection
Arbitrage MEV Bots are often regarded as a mysterious predator due to their non-open-source nature. Understanding the exact logic behind these MEV Bots can be challenging. However, most of them utilize flash loans to maximize the utilization rate of funds, which creates opportunities for attackers. The MEV Bot 0xd61492 hack is a real case for exploiting the interaction between the Bot and the flash loan provider.
The interesting parts of this incident include:
- First, the vulnerability hidden within the complex callback functions of the MEV Bot modules.
- Second, bypassing restrictions in the multi-contract MEV Bot system.
🧐 Learn about the root cause and the attack steps in detail.
#10: ThirdWeb Incident: Incompatibility Between Trusted Modules Exposes Vulnerability
Summary
On December 5, 2023, ThirdWeb's smart contracts were reported to be vulnerable. The issue is an incompatibility problem involving the ERC-2771 and Multicall standards. ERC-2771 defines an interface for receiving meta-transactions through a trusted forwarder, while Multicall allows for batching multiple function calls within a single transaction. The vulnerability occurs when a call, forwarded by a trusted forwarder, retrieves the actual caller address from the calldata, which can be manipulated by an attacker. Although each standard operates correctly on its own, their combined usage can break certain assumptions and lead to unexpected security issues.
Reason for Selection
Both ERC-2771 and Multicall standards are implemented in popular development libraries such as OpenZeppelin and ThirdWeb. Developers often place their trust in these well-established codebases and might overlook them during code audits. This oversight can introduce new security vulnerabilities, even if the individual modules are not inherently flawed. Third-party libraries play a crucial role in software security, a fact that is often overlooked.
🧐 Learn about the root cause and the attack steps in detail.
Conclusion
In this blog post, we have outlined ten significant security incidents from 2023. As the often-quoted saying goes, *"What we learn from history is that we do not learn from history." This remains painfully relevant, especially in the context of security incidents. We hope that this blog, along with subsequent entries, will enable the community to learn more effectively from past incidents and prevent similar mistakes in the coming year.
As a full-stack security service provider, BlockSec always aims to assist the community. BlockSec's approach to DeFi protocol security is comprehensive. We employ state-of-the-art auditing techniques, automated attack defense tools, and security incident management. This positions us as a vital partner for protocols aiming to strengthen their security posture and safeguard user assets against the evolving threats in the DeFi landscape of 2024.
Stay tuned for more blogs in this series.
Read other articles in this series:
- #1: Harvesting MEV Bots by Exploiting Vulnerabilities in Flashbots Relay
- #2: Euler Finance Incident: The Largest Hack of 2023
- #3: KyberSwap Incident: Masterful Exploitation of Rounding Errors with Exceedingly Subtle Calculations
- #4: Curve Incident: Compiler Error Produces Faulty Bytecode from Innocent Source Code
- #5: Platypus Finance: Surviving Three Attacks with a Stroke of Luck
- #6: Hundred Finance Incident: Catalyzing the Wave of Precision-Related Exploits in Vulnerable Forked Protocols
- #7: ParaSpace Incident: A Race Against Time to Thwart the Industry's Most Critical Attack Yet
- #8: SushiSwap Incident: A Clumsy Rescue Attempt Leads to a Series of Copycat Attacks
- #9: MEV Bot 0xd61492: From Predator to Prey in an Ingenious Exploit
- #10: ThirdWeb Incident: Incompatibility Between Trusted Modules Exposes Vulnerability




