Summary
Platypus Finance is an AMM protocol on the Avalanche blockchain. It has been attacked three times, as follows:
- On February 17, 2023, it experienced a hack due to an incorrect solvency check, resulting in a total loss of about $9.05M. Of this, $2.4M was rescued with BlockSec's help. Approximately 380K tokens were stuck in the Aave contract and were then returned.
- On July 12, 2023, it was hacked, with around $50K lost due to ignoring the price gap between stablecoins.
- On October 12, 2023, it suffered from price manipulation attacks, with around $2.2M lost. After negotiating with the exploiter, 90% of the stolen funds were returned.
The project is lucky to have survived all those attacks. Our analysis of these three exploits shows that the logical flaws could be avoided if a careful audit or more active security measures were used.
Attack One
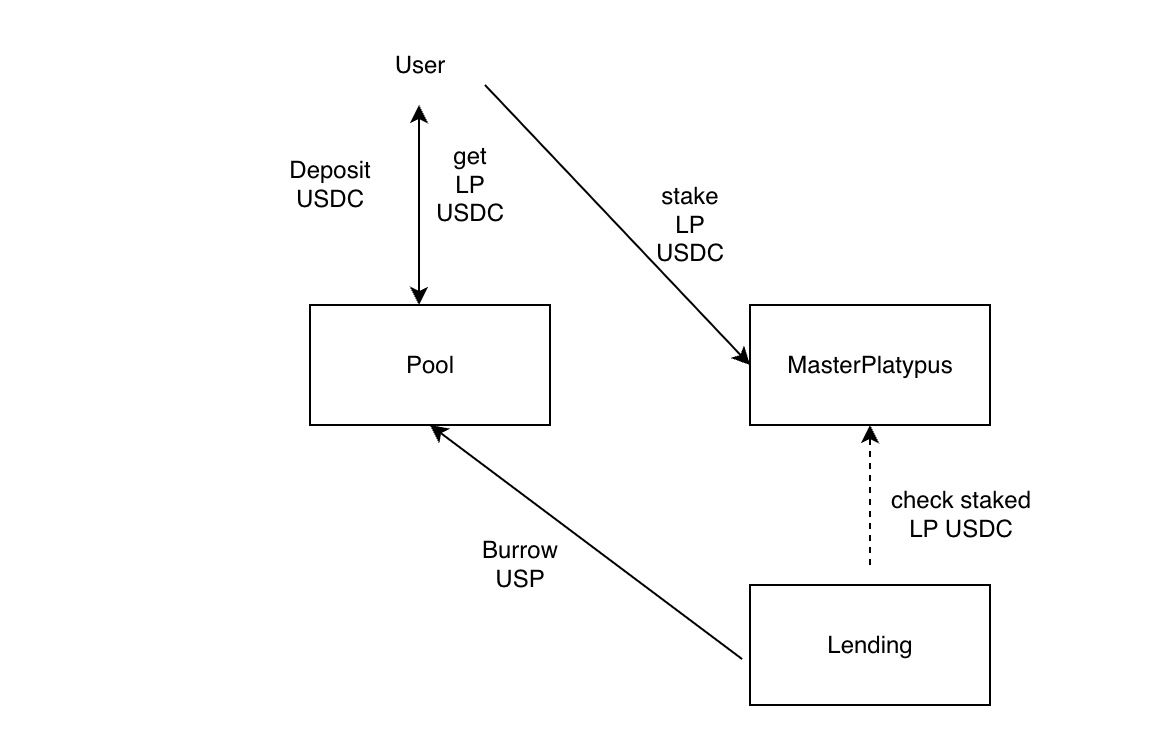
To understand this security incident, one must understand the workflow of several smart contracts. The rough process is that:
- A user can deposit a token into a pool to become an LP and receive an LP token.
- The LP token can be staked in MasterPlatypus to receive rewards. The LP token will be transferred to the MasterPlatypus contract during this process.
- The LP token can be used as collateral to borrow other assets to improve asset efficiency.
The following figure shows the interactions.
Vulnerability Analysis
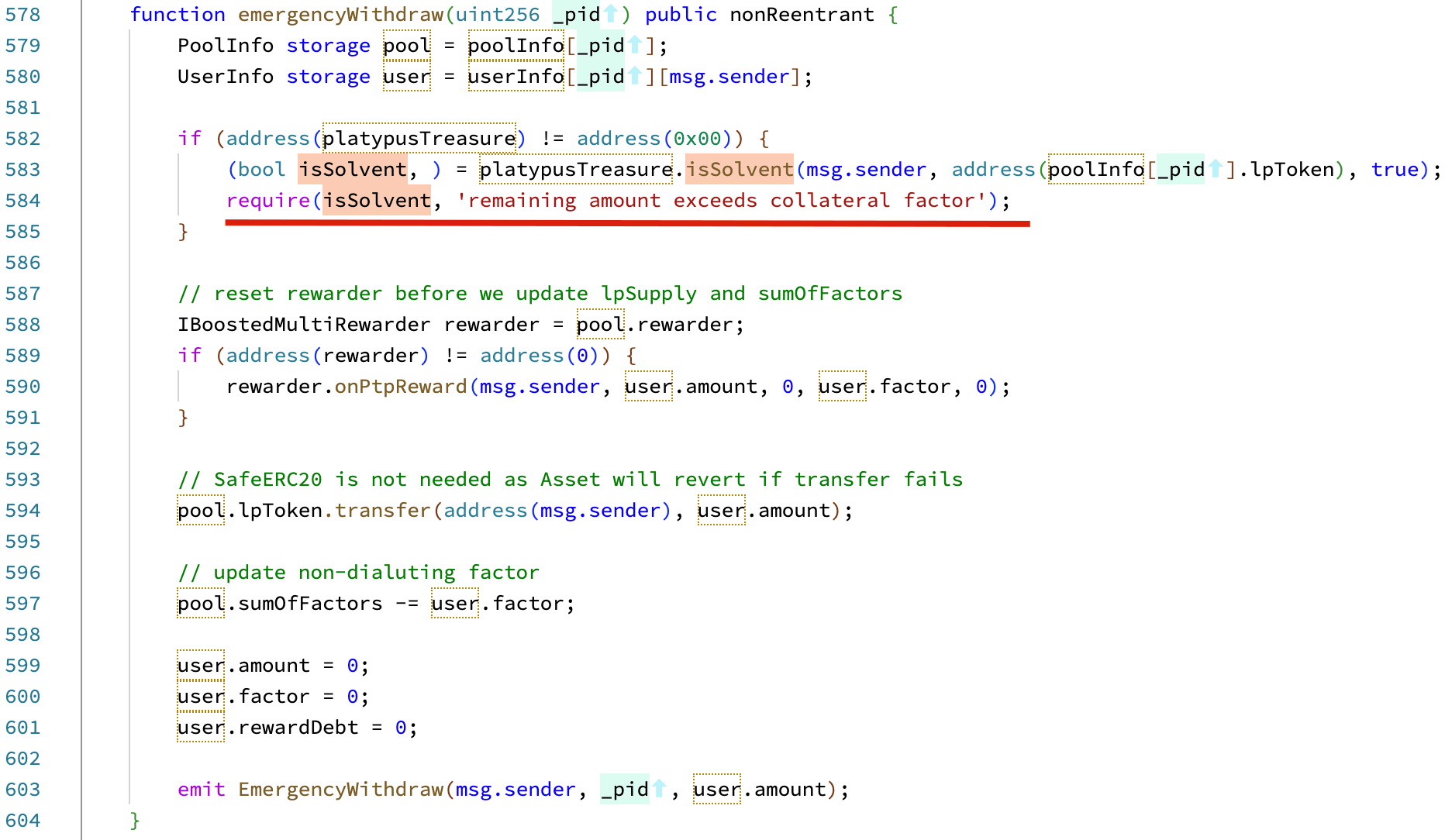
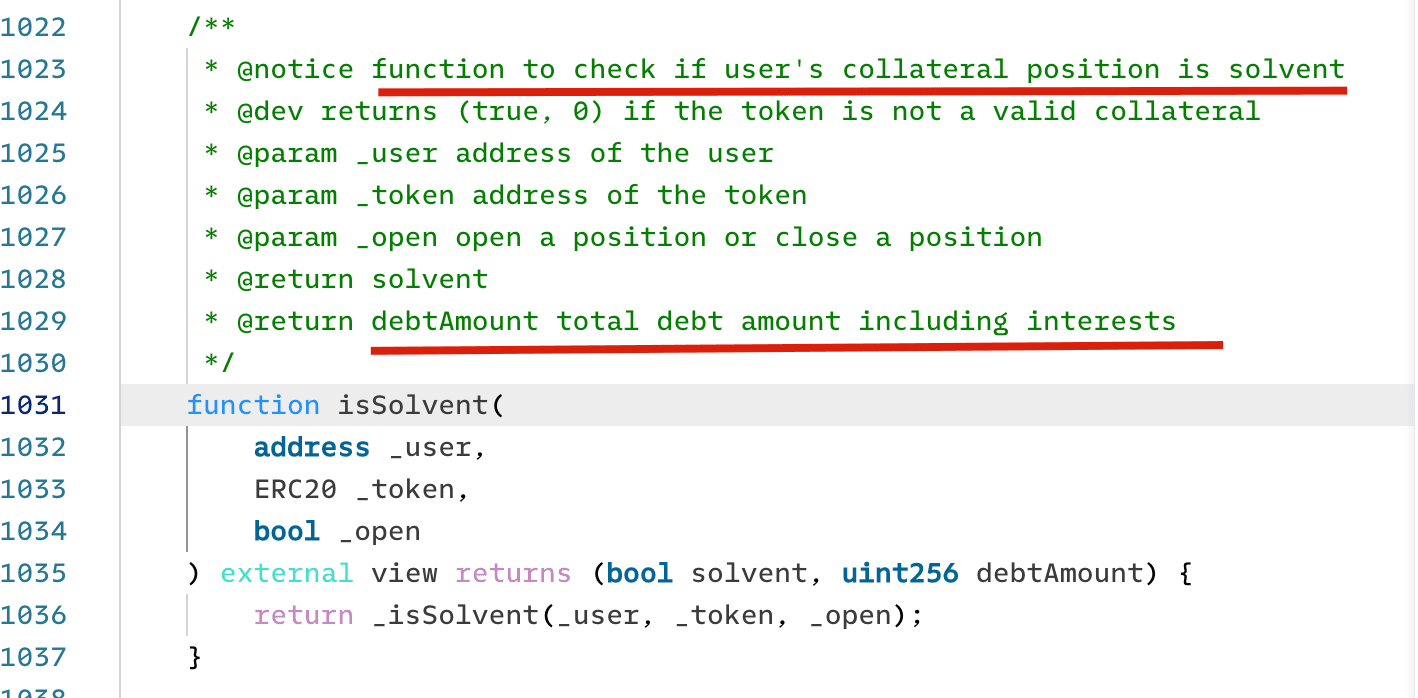
The vulnerability exists from a function named emergencyWithdraw inside the MasterPlatypus contract. In emergencies, this function should be used to withdraw the staked LP tokens in the MasterPlatypus contract. In this function, the contract checks whether the user is Solvent to allow the withdrawal. The logic checks whether users have any bad debt (i.e., whether the collateral can be used to pay the debt). If not, the users can withdraw the staked LP tokens.
However, this logic is flawed. The user is Solvent only means that the user’s collateral can pay for his/her debt. However, it does NOT check whether the user remains Solvent after emergently withdrawing the staked tokens. An attacker can leverage this flaw to borrow the assets and then emergently withdraw the staked LP tokens as well (without repaying the debts). See the detailed analysis in Immunefi's Blog.
Attack Analysis
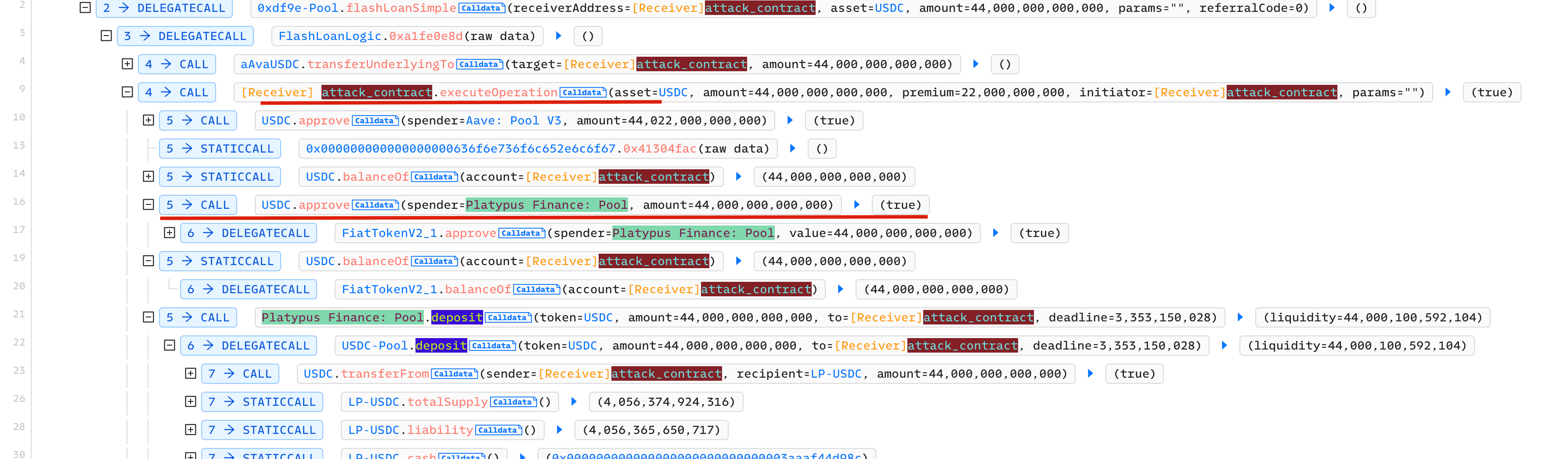
We use an attack transaction as an example to show the whole attack process.
Step 1: Borrow 44 million USDC Flashloan from AAVE
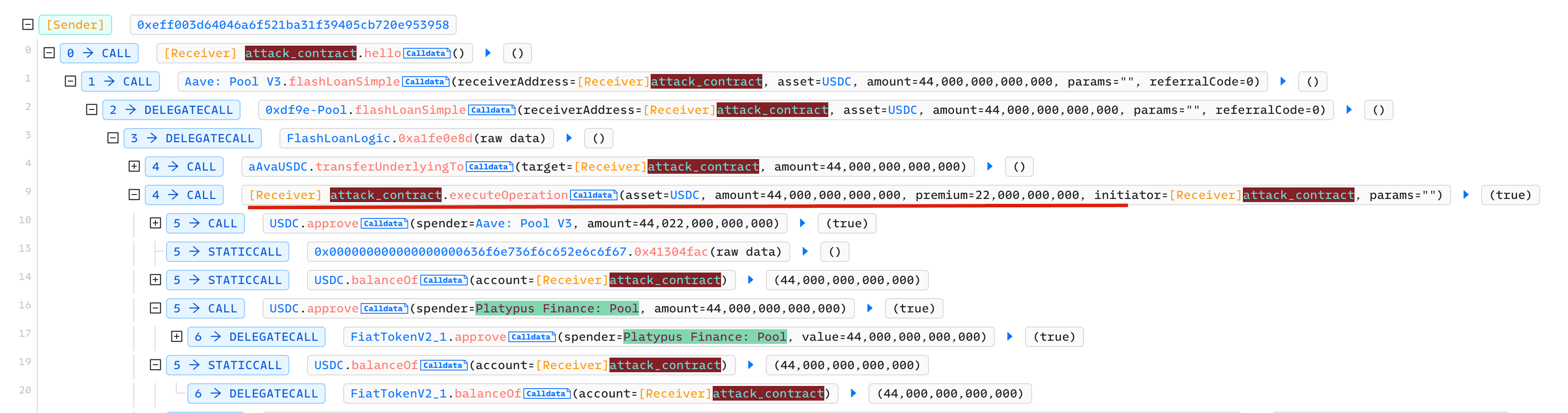
Step 2: Deposit 44 million USDC into the pool to get LP-USDC
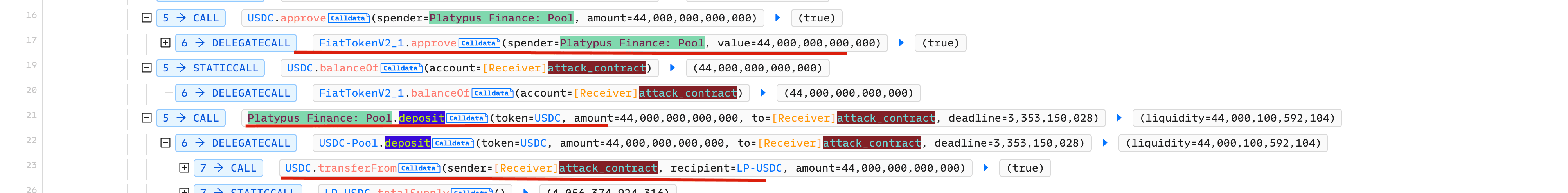
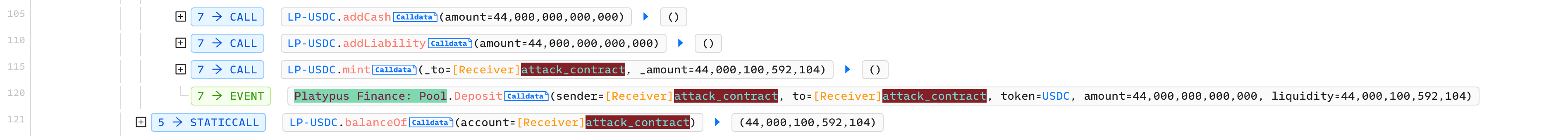
Step 3: Deposit LP-USDC into MasterPlatypus
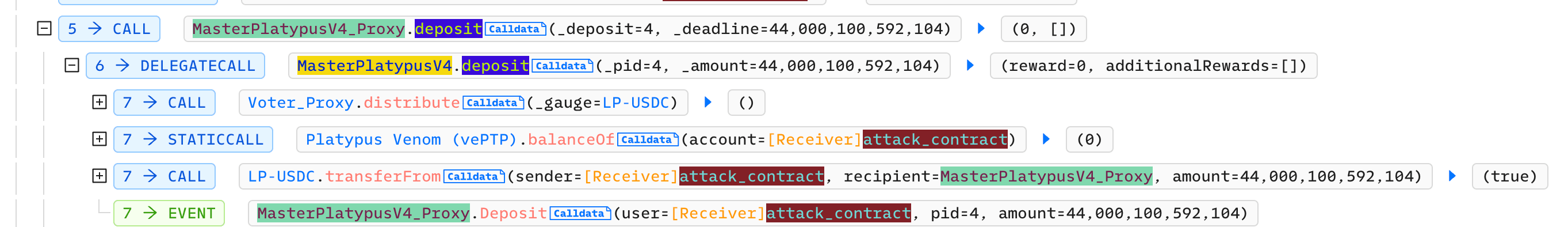
Step 4: Use LP-USDC as collatorel to borrow USP

Step 5: Execute the emergencyWithdraw function to launch the attack
The attacker get the LP-USDC without paying the USP debt.

Step 6: Withdraw LP-USDC from the pool to get USDC
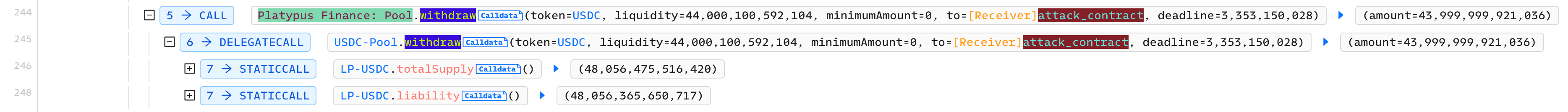

Step 7: Sell USP for profits

However, the profits are left inside the attack contract. In fact, the attacker can set up a new receipt address for the swap to get profits.
BlockSec's Rescue
We found that the attacker left the profits inside the attack contract. Besides, there is no logic inside the attack contract to withdraw the assets. However, we found a vulnerability in the attack contract, which can be leveraged to hack back to withdraw part of the assets inside the contract.
Specifically, there is access control of the flashloan callback function, which means anyone can invoke this callback function. This is also the root cause of many MEV bots being attacked.
Besides, inside the callback function, the attacker contract approves the USDC token to the Platypus finance pool contract. And this pool contract is upgradable!
By combining the previous two, we can rescue the USDC inside the attack contract by
- Upgrade the Platypus finance pool contract to include a logic to withdraw the USDC inside the contract
- Invoke the callback of the attack contract to approve the USDC to the pool contract
- The pool contract can replace any function (that will be executec by the attack contract) to transfer from the USDC from the attack contract (since the attack contract approves the USDC to the pool contract).
Here is the transaction to rescue 2.4 Million USDC.

Other Two Attacks
Please refer to the following links for more details about the other two attacks.
-
Attack-II: July-11-2023, The protocol assumes that the ratio between USDC and USDT is 1:1, which deviates from market fluctuations, resulting in a flawed withdrawal logic. The link to one attack transaction. There are a couple of ones.
-
Attack-III: October-12-2023, due to the manipulated
cashandliabilitywhich affected the swap price. [The first attack transaction | The second attack transaction]
Summary
The three attacks exploited different vulnerabilities in the protocol. Even though some other vendors have audited the protocol, the attacker still found the loophole and successfully exploited the protocol. Fortunately, some assets were rescued, but we cannot expect to be always lucky. More security measures including attack monitoring and automatic response, should be adopted to secure the protocol and user assets.
Read other articles in this series:
- Lead-In: Top Ten "Awesome" Security Incidents in 2023
- #1: Harvesting MEV Bots by Exploiting Vulnerabilities in Flashbots Relay
- #2: Euler Finance Incident: The Largest Hack of 2023
- #3: KyberSwap Incident: Masterful Exploitation of Rounding Errors with Exceedingly Subtle Calculations
- #4: Curve Incident: Compiler Error Produces Faulty Bytecode from Innocent Source Code
- #6: Hundred Finance Incident: Catalyzing the Wave of Precision-Related Exploits in Vulnerable Forked Protocols
- #7: ParaSpace Incident: A Race Against Time to Thwart the Industry's Most Critical Attack Yet
- #8: SushiSwap Incident: A Clumsy Rescue Attempt Leads to a Series of Copycat Attacks
- #9: MEV Bot 0xd61492: From Predator to Prey in an Ingenious Exploit
- #10: ThirdWeb Incident: Incompatibility Between Trusted Modules Exposes Vulnerability




