On June 26, 2025, the Resupply stablecoin protocol deployed on the Ethereum mainnet was attacked, resulting in the loss of approximately $10 million in assets. Due to an issue in the implementation of the price oracle of the relevant contract, for newly created low-liquidity Markets, the attacker was able to manipulate the relative price (i.e., the exchange rate between the borrowed asset and the collateral asset) of the borrowed asset (reUSD issued by Resupply) through a donation attack, making it 0. This allowed the attacker to bypass the asset health check and borrow a large amount of reUSD for profit.
After BlockSec was the first in the network to publicly issue an early warning and provide a preliminary analysis (Tweet1, Tweet2), Resupply subsequently also published an official announcement, but did not elaborate on many technical details. This article will provide a more detailed analysis. On the other hand, after the attack, there was also intense community controversy among the project party and its stakeholders. This article will delve into and discuss the complex ecological relationships behind the protocol, for readers’ reference.
1. Background
1.1 About the Resupply Protocol
Resupply is a decentralized stablecoin protocol that belongs to the Curve ecosystem. The stablecoin issued by Resupply is called reUSD. This is a decentralized stablecoin backed by collateralized debt positions (CDPs), supported by other stablecoins — including crvUSD and frxUSD — that earn interest in lending markets on external platforms. Users can provide crvUSD and frxUSD to borrow reUSD, achieving refinancing of stablecoin assets.
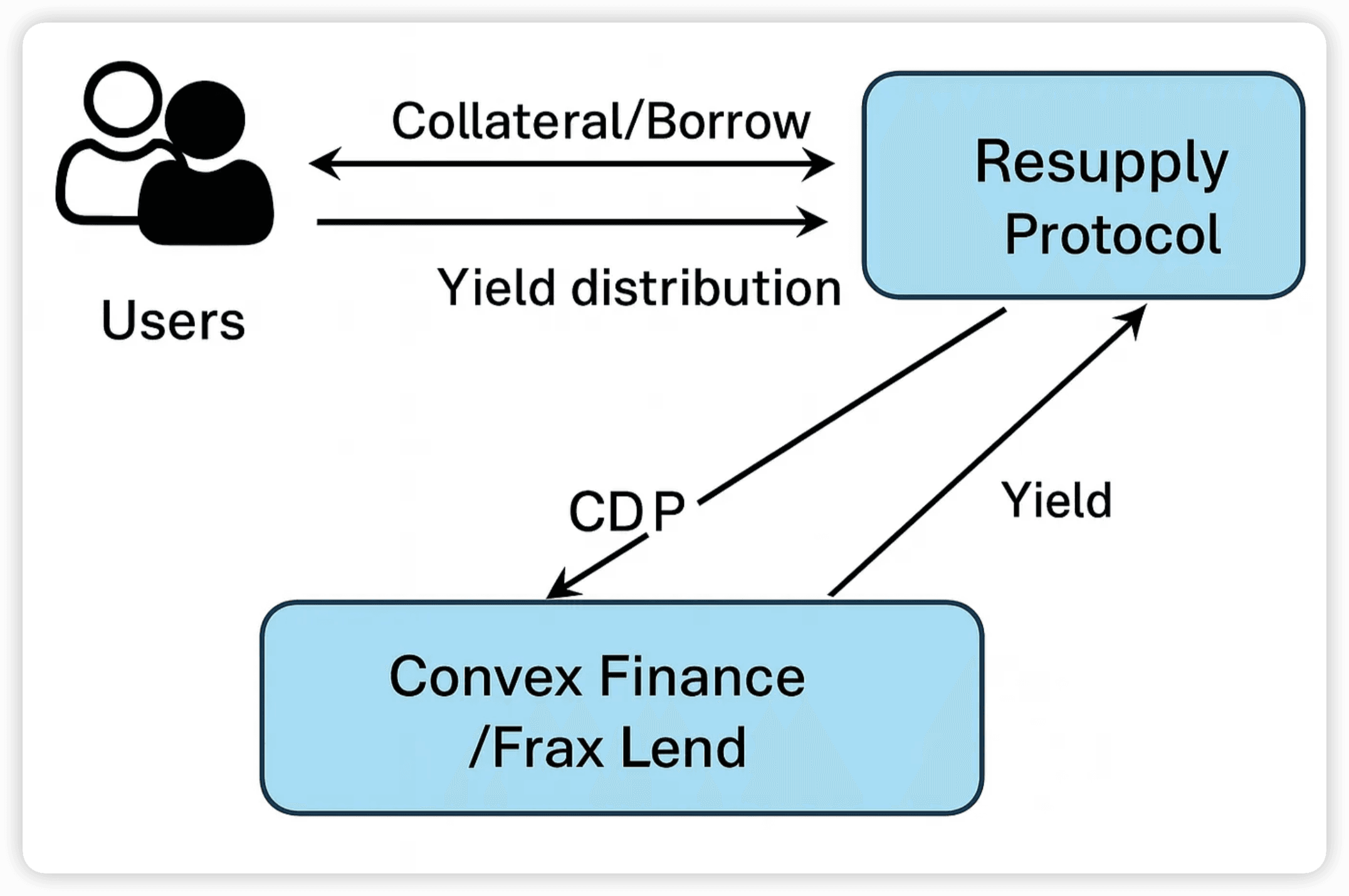
Specifically, users can perform lending-related operations in a Resupply Market deployed on-chain. The creation and behavior of Markets are managed through the DAO. Each Market specifies an ERC-4626 Vault as the collateral asset (collateral) and uses the asset corresponding to that Vault as the underlying. Users deposit collateral (the Vault or the Vault’s asset) in the Market to borrow reUSD.
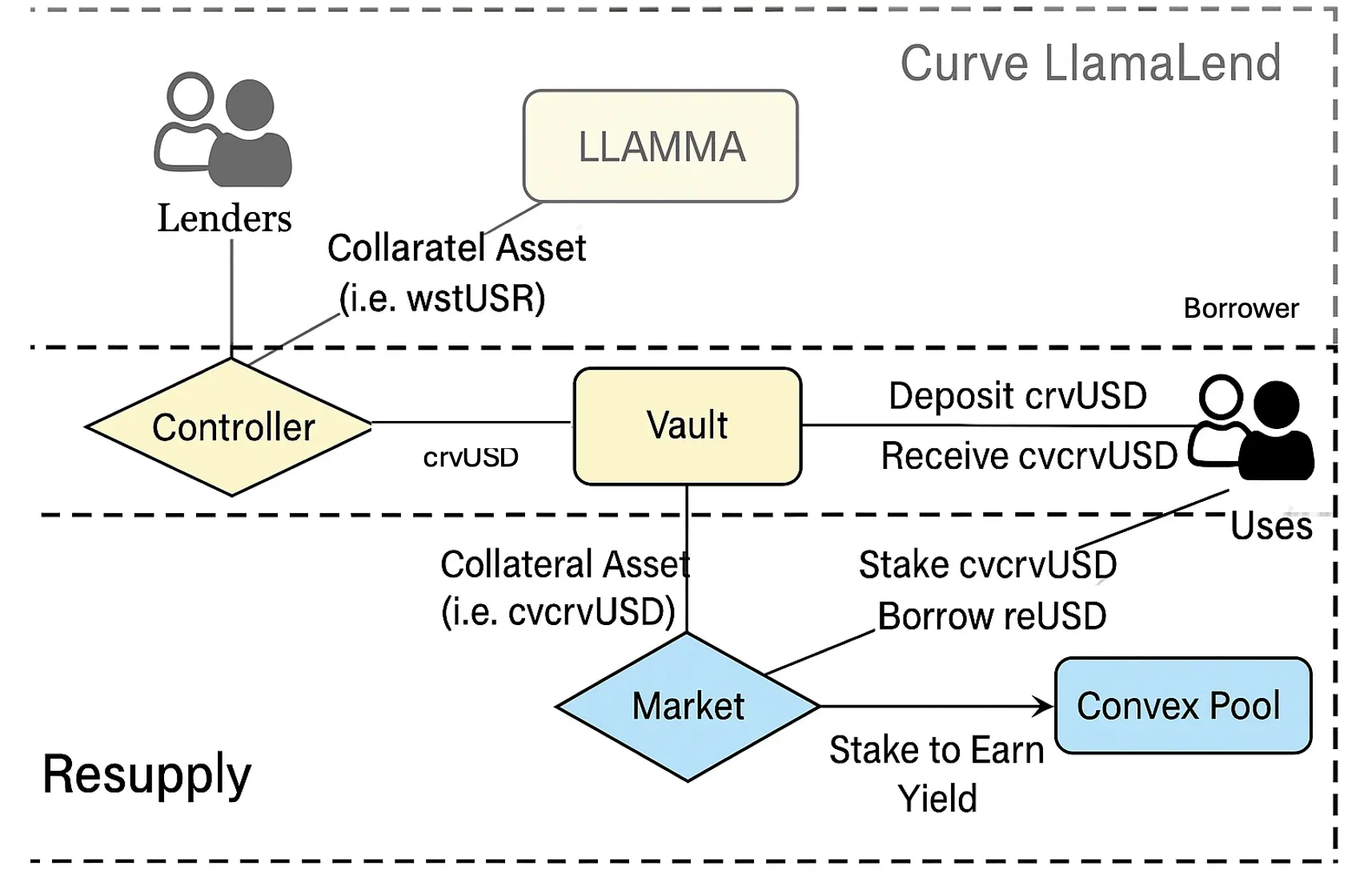
Taking the Market 0x6e90 and Vault 0x0114 involved in this attack as an example, the relevant assets (tokens) are as follows:
-
Market
0x6e90- underlying: crvUSD
- collateral: cvcrvUSD (i.e., Vault
0x0114) - borrowed: reUSD
-
Vault
0x0114- asset: crvUSD (actually stored in the Curve LlamaLend Controller, which is also a Market)
- collateral: wstUSR
- borrowed: crvUSD
- share: cvcrvUSD (the ERC-4626 token issued by the Vault)
In other words, users can pledge a certain amount of cvcrvUSD (or crvUSD, which will in practice be converted to cvcrvUSD via the Vault) in this Market to borrow reUSD.
1.2 How does the system determine whether a user is eligible to borrow an asset?
Similar to general lending protocols, the Resupply Market will also perform an asset health check on a user’s position (through the modifier isSolvent).
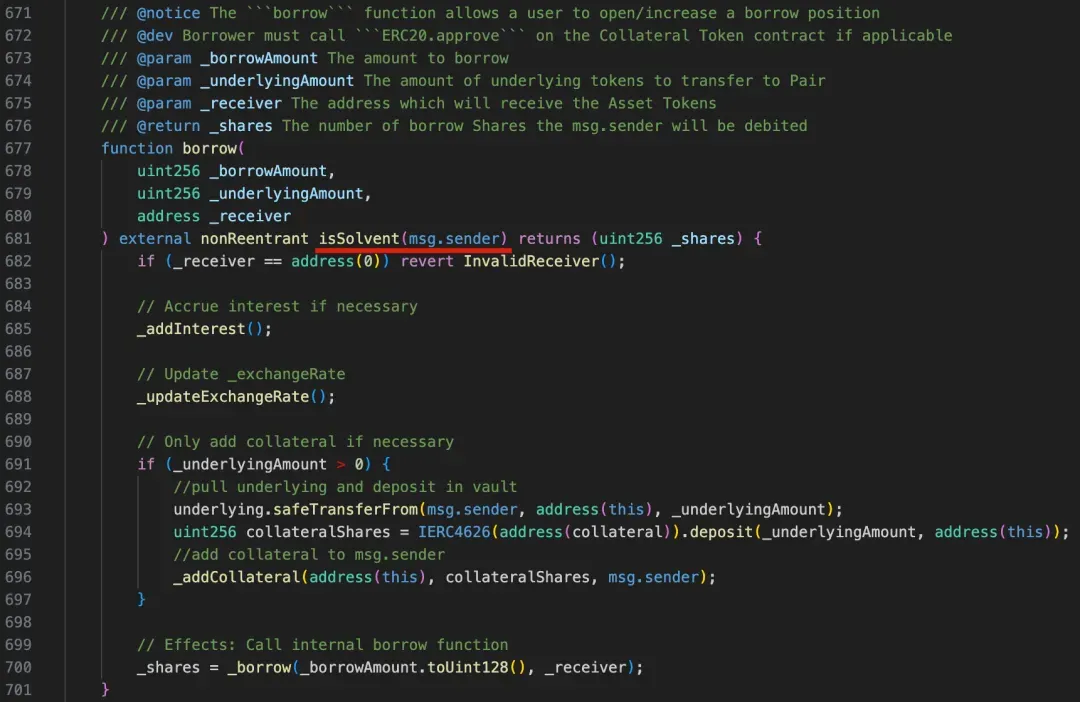
The isSolvent ultimately calls the _isSolvent function, which checks the LTV (Loan-to-Value ratio), requiring that the ratio between the borrowed asset and the collateral asset must not exceed the maximum value set by the system (_ltv <= maxLTV).
It can be seen that the calculation of LTV relies on the exchange rate (_exchangeRate), i.e., the price (exchange ratio) of the borrowed asset relative to the collateral asset.
2. Attack Analysis
2.1 Root Cause Analysis
From the contract code perspective, the key cause of the attack was that the price oracle implementation of the Resupply Market had a problem. For newly created low-liquidity Markets, the attacker could manipulate the exchange rate through a donation attack, thereby bypassing the health check and borrowing a large amount of reUSD for profit.
How to calculate exchange rate?

The formula is as following:
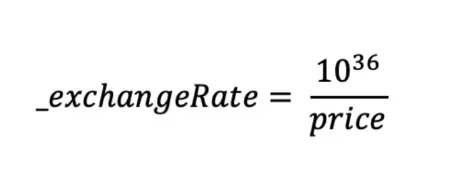
Obviously, if getPrices returns a price greater than 1e36, the downward rounding of integer division will result in _exchangeRate = 0.
How to manipulate price?
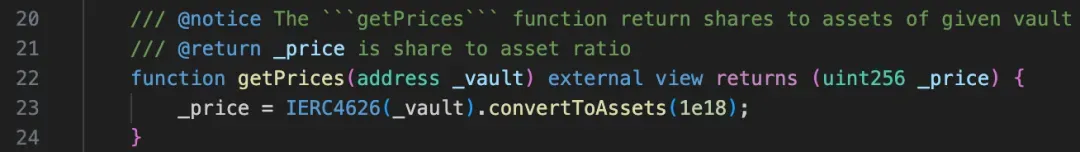
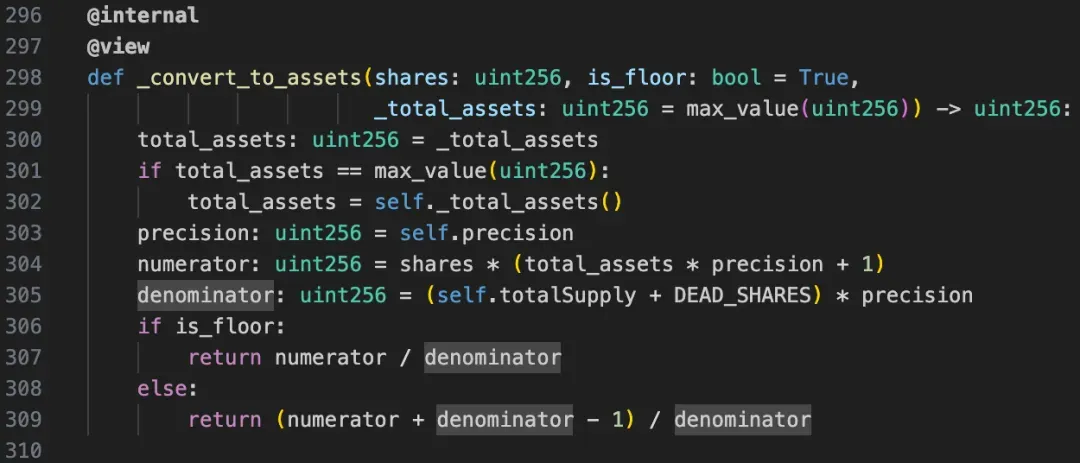
According to the code, the price can be calculated as follows:
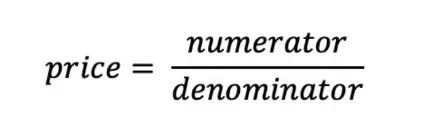
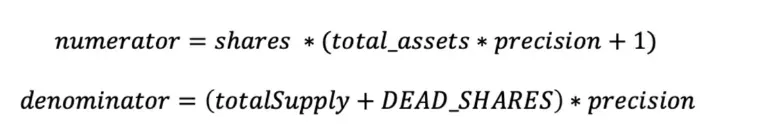
Since the code sets precision = 1, DEAD_SHARES = 1000, and shares = 1e18.
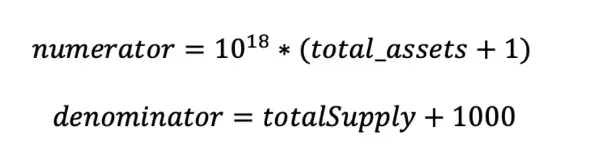
Finally, after substituting the variables, the price calculation formula is as follows:
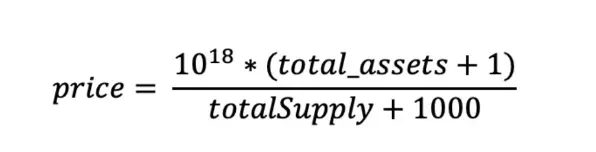
It can be seen that to amplify the value of price, the key is to widen the gap between total_assets and totalSupply, making total_assets extremely large while totalSupply remains very small. In the actual implementation of the Resupply protocol, total_assets in the formula depends on the underlying (crvUSD), and totalSupply depends on the shares (cvcrvUSD) corresponding to the overall liquidity in the Market. This is precisely the classic donation attack scenario.
2.2 Attack Transaction Analysis
According to the attack transaction [4], it can be analyzed that the attacker performed the following core steps:
-
Borrowed 4,000 USDC via flash loan and exchanged it for 3,999 crvUSD.
-
Donated 2,000 crvUSD to Controller
0x8970. Before the donation, Controller0x8970held 0 crvUSD. After the donation, the recorded amount of crvUSD became2000000000000000000000(with 18 decimals). -
Deposited approximately 2 crvUSD into Vault
0x0114and received 1 share (cvcrvUSD). At this point, the recorded amount of crvUSD was2002000000000000000001(with 18 decimals). -
Added 1 unit (i.e., 1 share of Vault
0x0114) of collateral to Market0x6e90. -
Borrowed 10,000,000 reUSD from Market
0x6e90. At this point,_exchangeRate = 0, resulting in_ltv = 0, so the_isSolventcheck passed.
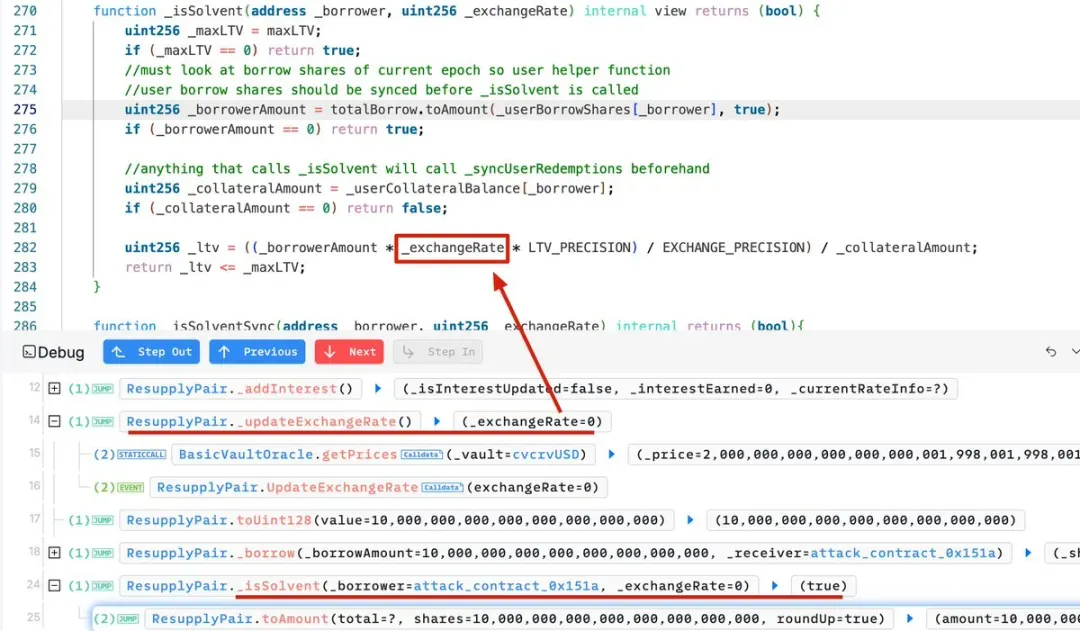
Why was _exchangeRate equal to 0? Because through the previous steps, the attacker manipulated the contract to reach the following state:
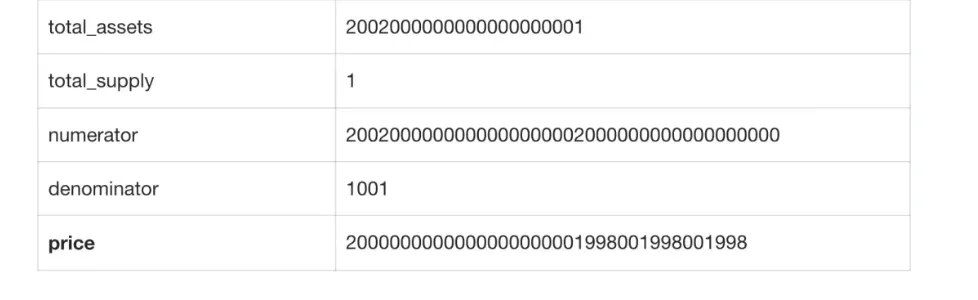
Recalling the calculation method of the exchange rate:
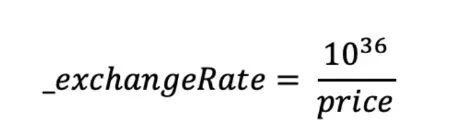
Since price > 1e36, _exchangeRate = 0.
- Exchanged the borrowed reUSD for profit.
3. Lessons Learned
The attacked Market in Resupply used a price oracle implementation similar to Curve’s template contract.
However, the Curve official documentation had already indicated the applicable scope of this implementation—unfortunately, Resupply did not seem to take this applicability warning into consideration in their deployment.
4. Relationships and Community Controversy
4.1 Complex Relationship Network of Five Major Projects in the Curve Ecosystem
To understand the deeper impact of the Resupply incident, we must first look at the complex relationships among the five core protocols within the Curve ecosystem.
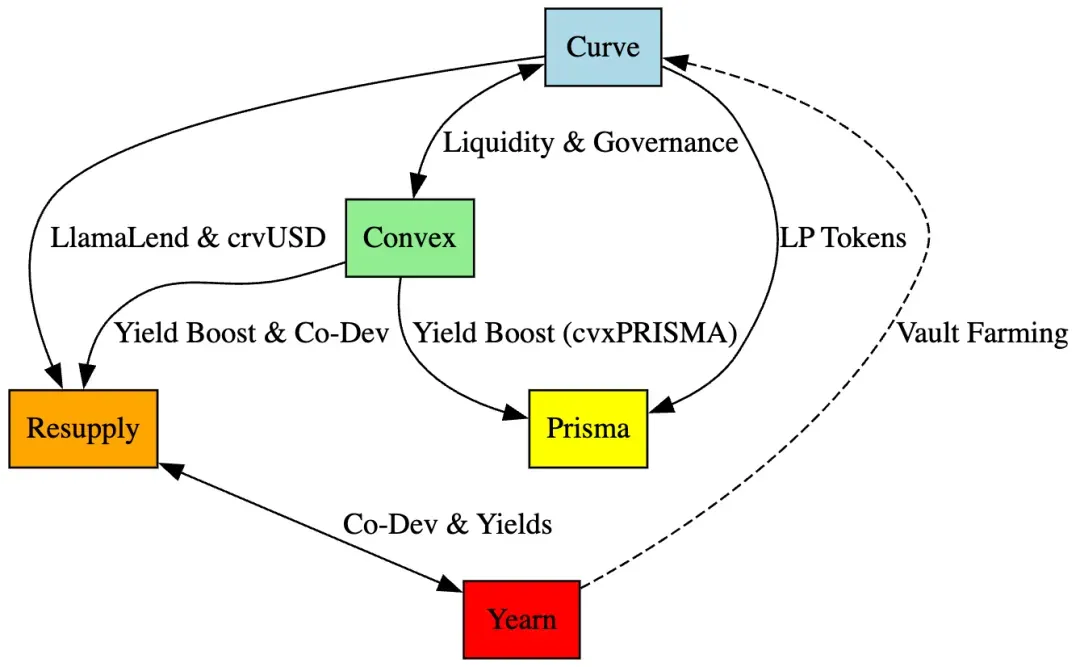
Curve Finance is the core of the entire ecosystem, providing liquidity pools, crvUSD, and the LlamaLend protocol, which underpin the operations of Resupply, Prisma, Convex, and Yearn. Convex optimizes Curve’s yield through staking and governance and provides additional reward mechanisms for Prisma and Resupply. Prisma relies on Curve’s LP tokens and Convex’s yield enhancement functions, while Resupply is directly based on Curve’s LlamaLend to issue reUSD and was jointly developed by Convex and Yearn. Yearn not only optimizes the yields of Curve pools but also promoted the development of Resupply through collaboration with Convex.
Curve Finance: As the core platform, Curve’s liquidity pools (such as the crvUSD pool) and LlamaLend protocol are directly used by Resupply to issue reUSD, by Prisma for staking LP tokens, by Yearn for yield optimization, and by Convex for governance voting..
Convex: Convex is Curve’s yield enhancement protocol. Users can stake Curve LP tokens to earn higher CRV rewards as well as Convex’s CVX tokens. Convex controls nearly 50% of Curve’s governance voting power and provides yield-boosting mechanisms for Prisma and Resupply.
Prisma : Prisma stakes Curve’s LP tokens, and users obtain enhanced rewards (cvxPRISMA) via Convex. Prisma relies on Curve’s liquidity and Convex’s yield mechanisms.
Yearn: Yearn is a yield aggregator that offers users high returns by optimizing the yields of Curve’s LP tokens (enhanced via Convex). Yearn collaborated with Convex to develop Resupply and extensively uses Curve pools in its yield strategies.
Resupply: Jointly developed by Convex and Yearn, it allows users to borrow reUSD by pledging stablecoins such as crvUSD and automatically stakes tokens on Convex to earn CRV and CVX rewards, forming a yield optimization loop.
4.2 Controversy and Impact
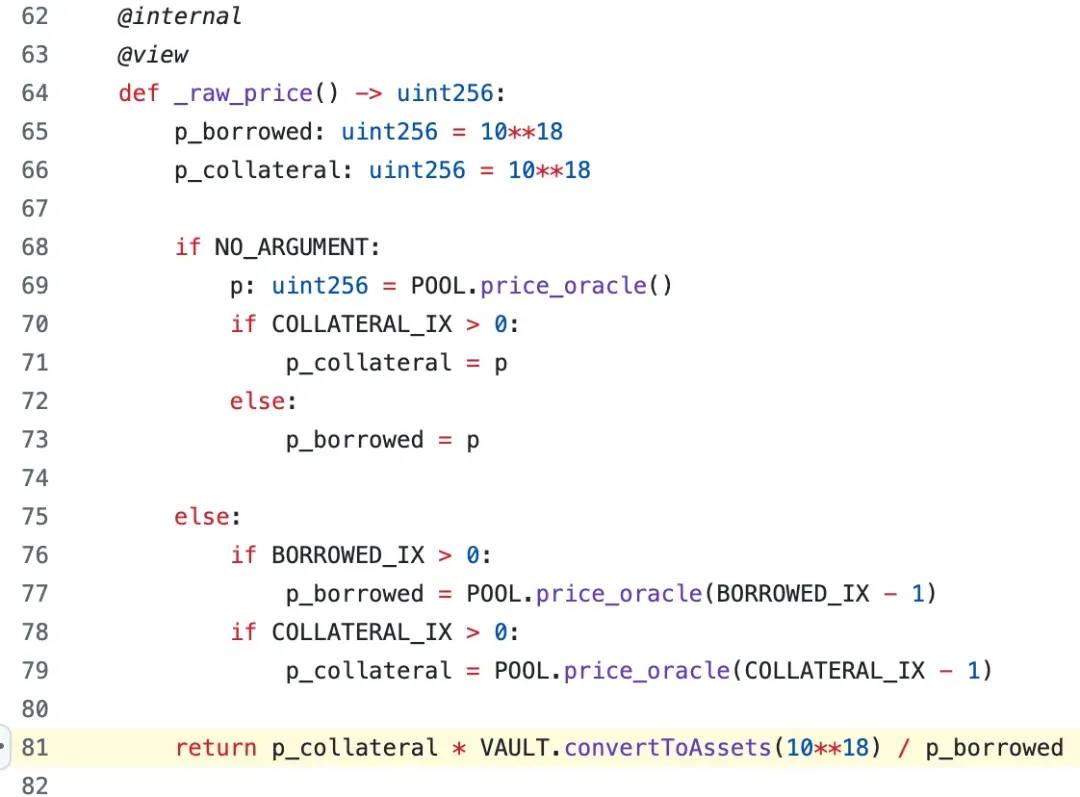
However, when Resupply was attacked, this complex web of relationships immediately became the focus of controversy. Curve founder Michael Egorov quickly distanced himself from Resupply, emphasizing:
“There is no single person from Curve working on that project… don’t generalize to Curve please.”
This statement of disassociation reflected how the intricate cooperative relationships within the DeFi ecosystem can be fragile in times of crisis.
These interrelated projects together form a highly coupled ecosystem — in such a system, any problem in one link can trigger a chain reaction. Therefore, it is no surprise that the Resupply attack incident sparked widespread community discussion about protocol interdependence and security.
5. Further Reflections
5.1 Timeline
-
May 17, 2025: Resupply official address
0x1f84deployed a new LlamaLend Market via Curve’s OneWay Lending Factory.- The Market used crvUSD as the lending asset and wstUSR as the collateral token.
- The ERC-4626 Vault contract was
0x0114, and the corresponding Controller was0x8970.
-
May 31, 2025: A new proposal wstUSR-long LlamaLend Market was published on Resupply’s governance page. This proposal aimed to allow users to mint reUSD via the LlamaLend Market.
-
June 11, 2025: The proposal was published on-chain.
-
June 26, 2025, 00:18:47 (UTC): The proposal passed, and Resupply’s official address
0x0417deployed a new ResupplyPair (i.e., the Resupply crvUSD/wstUSR Market)0x6e90, binding Vault0x0114and Controller0x8970.- Bound Vault 0x0114 and Controller 0x8970.
- Used the Vault’s collateralized debt position (i.e., cvcrvUSD, with crvUSD as the underlying) as collateral.
-
June 26, 2025, 01:53:59 (UTC): About 1.5 hours after the Market
0x6e90deployment, the attacker successfully executed the exploit. At the same time, BlockSec detected the attack and attempted to contact the project team. -
June 26, 2025, 02:26 (UTC): After failing to reach the team and confirming no further losses, BlockSec issued a public warning.
-
June 26, 2025, 02:53:23 (UTC): The project team paused the protocol.
5.2 If There Had Been Phalcon, the Tragedy Could Have Been Prevented
BlockSec Phalcon Security represents the latest breakthrough in DeFi security protection.By monitoring transactions at the mempool stage, Phalcon is able to identify abnormal patterns the instant an attack transaction enters the mempool.
The system, powered by an intelligent analysis engine, integrates over 200 typical attack signatures. In the past six months, it has maintained an ultra-low false positive rate of less than 0.0001%, achieving truly precise threat detection.
The system leverages a proprietary gas bidding strategy to ensure that the defense transaction outraces the attack transaction, while automatically triggering the protocol’s emergency pause function.
The entire response process supports multiple permission control modes — including EOA and multisig wallets — providing flexible security solutions for different types of protocols.
If Resupply had integrated the Phalcon system when deploying the Market, the attack could have been completely avoided
Within the 1.5 hours after Market 0x6e90 was deployed, the Phalcon system would have automatically detected the new Market deployment, intelligently analyzed its configuration parameters, and identified the potential risk of a donation attack.
The system would have immediately sent a risk alert to the project team, suggesting adding initial liquidity protection or adjusting relevant parameters.
Even after the attack occurred, deploying Phalcon would still bring tremendous value to Resupply and the entire Curve ecosystem
A transparent, real-time monitoring system demonstrates to users and the community the project team’s firm commitment to security, and the 24/7 continuous protection mechanism ensures that similar incidents never happen again. Public security monitoring data enhances project transparency and serves as a critical means to rebuild community confidence. For affected projects, proactively adopting a top-tier security solution proves their sense of responsibility for user fund safety, and partnering with an industry leader like BlockSec also provides a strong endorsement for the project’s reputation in the security field.
At present, more than $50 billion in assets have chosen to trust Phalcon’s protection. We have successfully stopped over 20 real-world hacking attacks, saving more than $20 million in asset losses. In the past six months, the system has maintained a perfect detection accuracy record and achieved millisecond-level response speeds, always staying one step ahead of attackers. Phalcon currently supports over 20 major blockchain networks, including Ethereum, BSC, and Arbitrum, providing comprehensive, cross-chain security protection for the DeFi ecosystem.
Resupply’s $10 million loss and countless other attack incidents tell us that in the DeFi world, security is not an option — it is a necessity for survival.
Don’t wait for the next attack to regret it. Deploy the strongest security protection for your protocol now.
BlockSec’s expert team is ready to conduct a comprehensive security assessment for your project.
🔗 Phalcon Security APP:
https://blocksec.com/phalcon/security
🔗 Book a demo:
https://blocksec.com/book-demo




