This article summarizes key findings from the paper "Towards Understanding and Analyzing Instant Cryptocurrency Exchanges," which has been accepted by ACM SIGMETRICS 2025.
The world of cryptocurrency is constantly evolving, bringing forth innovative services designed to enhance user experience. One such innovation is Instant Cryptocurrency Exchanges (ICEs), platforms created to simplify the process of swapping digital assets across different blockchains. However, as with many emerging technologies, the very features that offer convenience can also be exploited for nefarious purposes.
In the BlockSec team’s recent paper, "Towards Understanding and Analyzing Instant Cryptocurrency Exchanges", we conducted a comprehensive study of ICEs, aiming to reveal their operational mechanics, legitimate uses, and, most importantly, how they are being exploited for illicit activities such as money laundering. Additionally, we developed a systematic methodology to trace illicit funds flowing through ICE services.
Understanding ICEs: The Basic Workflow
Before diving into the darker aspects, it's essential to understand how ICEs generally function. We summarized a typical four-step process for ICE operations (as illustrated in Figure 1):
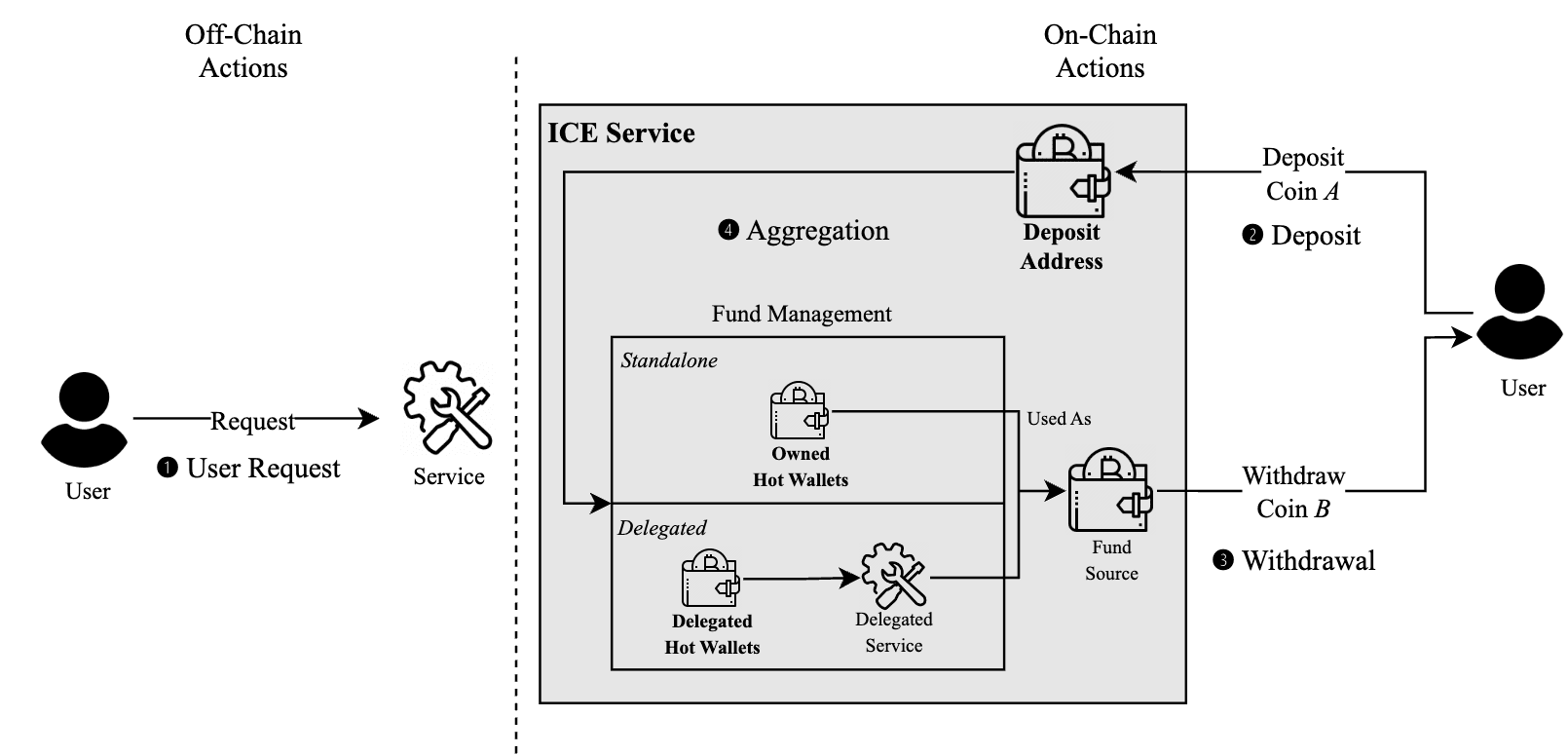
- User Request (Off-Chain)
The process begins with a user initiating a request on the ICE platform. This request, which happens off-chain, includes details like the source and target cryptocurrencies, the amounts, and the destination address for the exchanged funds. This off-chain nature contributes to user privacy but also creates challenges in tracing.
- Deposit (On-Chain)
The ICE service generates a unique deposit address for the user, who then transfers their source cryptocurrency to this address. This transaction is recorded on the source blockchain.
- Fund Management & Withdrawal (On-Chain)
Once the deposit is confirmed, the ICE service manages the "instant exchange." Using its liquidity pools (or collaborating with others, categorized into "Standalone" and "Delegated" types), it sends the target cryptocurrency to the user’s destination address. This withdrawal is recorded on the target blockchain.
- Aggregation (On-Chain)
ICE services often consolidate funds from multiple deposit addresses into larger hot wallets for easier management. This is also an on-chain activity.
While the user’s initial request occurs off-chain, the deposit and withdrawal transactions are on-chain. However, linking a specific deposit to a specific withdrawal is difficult because the ICE service acts as an intermediary, mixing funds from multiple users.
The Double-Edged Sword: Convenience vs. Illicit Use
ICEs offer undeniable convenience: fast, cross-chain swaps often without the stringent Know Your Customer (KYC) procedures required by centralized exchanges (CEXes). Unfortunately, this lack of strict KYC, combined with incomplete on-chain data for individual user requests, creates an attractive loophole for illicit actors.
Our research uncovered alarming statistics about the misuse of ICEs:
- A total of $12,473,290 in illegal funds were laundered through ICE services analyzed.
- 432 malicious addresses (involved in phishing, scams, etc.) received their initial funding from ICEs, making these platforms an entry point for illicit activities.
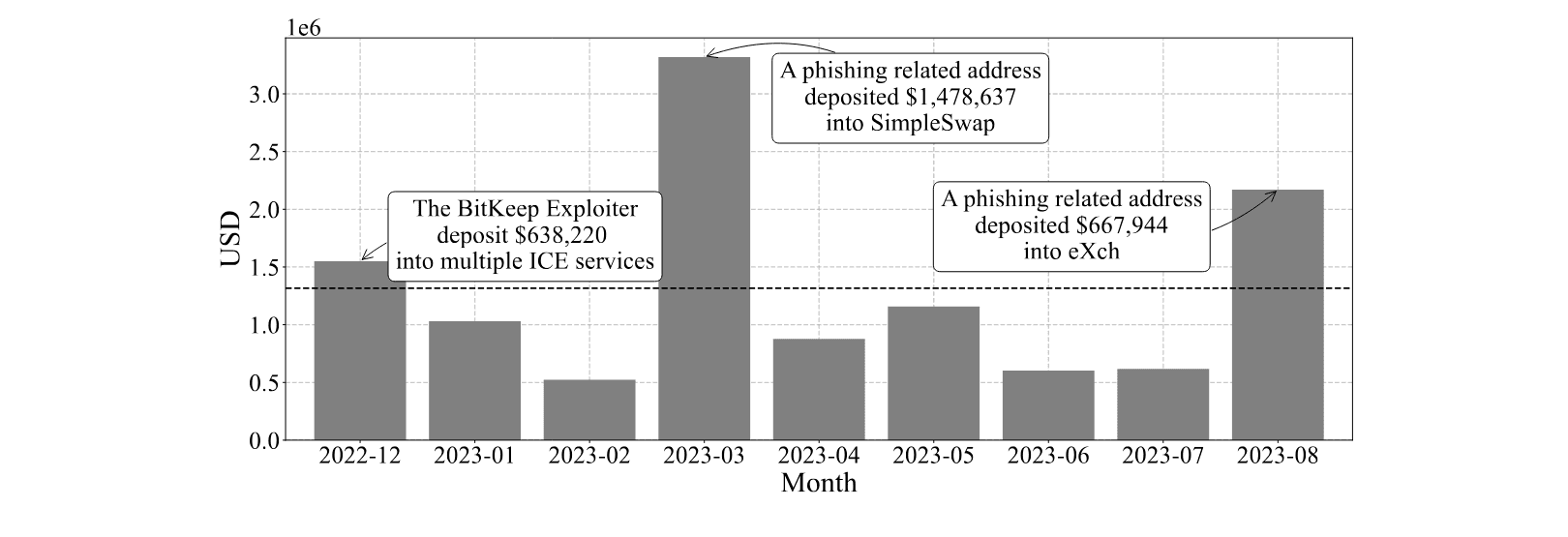
A stark example is the BitKeep incident, where attackers laundered over $2 million through multiple ICEs. These platforms effectively break the chain of traceability, making it harder for authorities to follow the money trail.
Unmasking the Shadows: Our Tracing Methodology
Despite the challenges, breaking the anonymity ICEs provide is not impossible. In our paper, we proposed a heuristic-based matching algorithm to correlate user deposits and withdrawals within account-based blockchains (like Ethereum and other EVM-compatible chains).
This algorithm is based on insights from our analysis:
- Transaction Ordering: A withdrawal transaction from the ICE service must occur after the user's deposit is confirmed.
- Low Price Deviation & Request Frequency: ICE user requests generally closely match market prices. Moreover, despite the high transaction volume, individual deposit and withdrawal transactions can often be distinguished by timestamps and values.
- Efficiency of ICEs: ICE platforms pride themselves on speed, with withdrawals initiated promptly after deposit confirmations.
The matching algorithm operates in three phases:
- Operation Identification: Identify all deposit and withdrawal operations related to the ICE service by analyzing transactions associated with its known hot wallets across blockchains.
- Value Calculation: Calculate the dollar value of each identified deposit and withdrawal operation at the time of the transaction using historical price data.
- Matching: Match deposits with potential withdrawals based on two metrics: the difference in dollar value (V) and the time difference (T) between the deposit and withdrawal. Address reuse is also factored in, as users may use the same address across chains or transactions.
Key Findings from Our Tracing Algorithm
We evaluated our algorithm using ground-truth data (historical user requests provided by two ICE services, FixedFloat and SideShift) and achieved an overall accuracy rate exceeding 80%. This is significant, showing that despite ICEs’ opaque nature, a substantial portion of transactions can be linked.
This ability to link deposits and withdrawals has profound implications for tracing illicit funds. For example, our analysis of malicious funds deposited into ICEs revealed common patterns:
- A large portion of illicit funds withdrawn from ICEs on Ethereum were sent to other Ethereum addresses, using ICEs as internal mixers to break the on-chain link. Many of these funds were ultimately deposited into centralized exchanges.
- TRON was another popular destination blockchain for laundered funds.
Our case studies, such as the address "Fake_Phishing11675," illustrated how illicit profits flowed through ICEs (like FixedFloat, in this case), sometimes involving multiple hops, before arriving at centralized exchanges. Even in complex scenarios, our algorithm successfully uncovered these paths.
Implications of Our Research
Our research demonstrates that while ICEs provide valuable services, their current operational models can be exploited. The tracing methodology we developed provides a new tool for researchers, cybersecurity firms, and law enforcement agencies to combat financial crime in the crypto space. It highlights that the "privacy" offered by some ICEs is not unbreakable. By systematically analyzing on-chain data, we can begin to de-anonymize illicit transactions and understand the broader money laundering ecosystem.
Our findings call for a nuanced discussion about regulation and AML (Anti-Money Laundering) policies for ICEs. While overly strict regulations could stifle innovation, the current landscape clearly enables significant abuse. A balanced approach—combining better self-regulation by ICEs, privacy-preserving analytics, and advanced tracing tools like ours—may help achieve better outcomes.
Redefining Compliance with Cutting-Edge Research
In the face of evolving tactics for money laundering and other illicit activities, BlockSec believes only continuous, advanced research capabilities can provide effective risk protection and compliance support.
BlockSec was co-founded by professors from Zhejiang University and top blockchain security experts, with a core team comprising graduates from leading universities worldwide. The team has long been dedicated to pioneering blockchain security research, achieving breakthroughs in phishing prevention, fund tracing, and AML analysis. Our work has been featured at prestigious conferences such as ACM SIGMETRICS, NDSS Symposium, CCS, and WWW. We incorporated academic insights and technical advancements into the design of the Phalcon Compliance APP, helping Virtual Asset Service Providers (VASPs) meet evolving compliance and risk management needs.
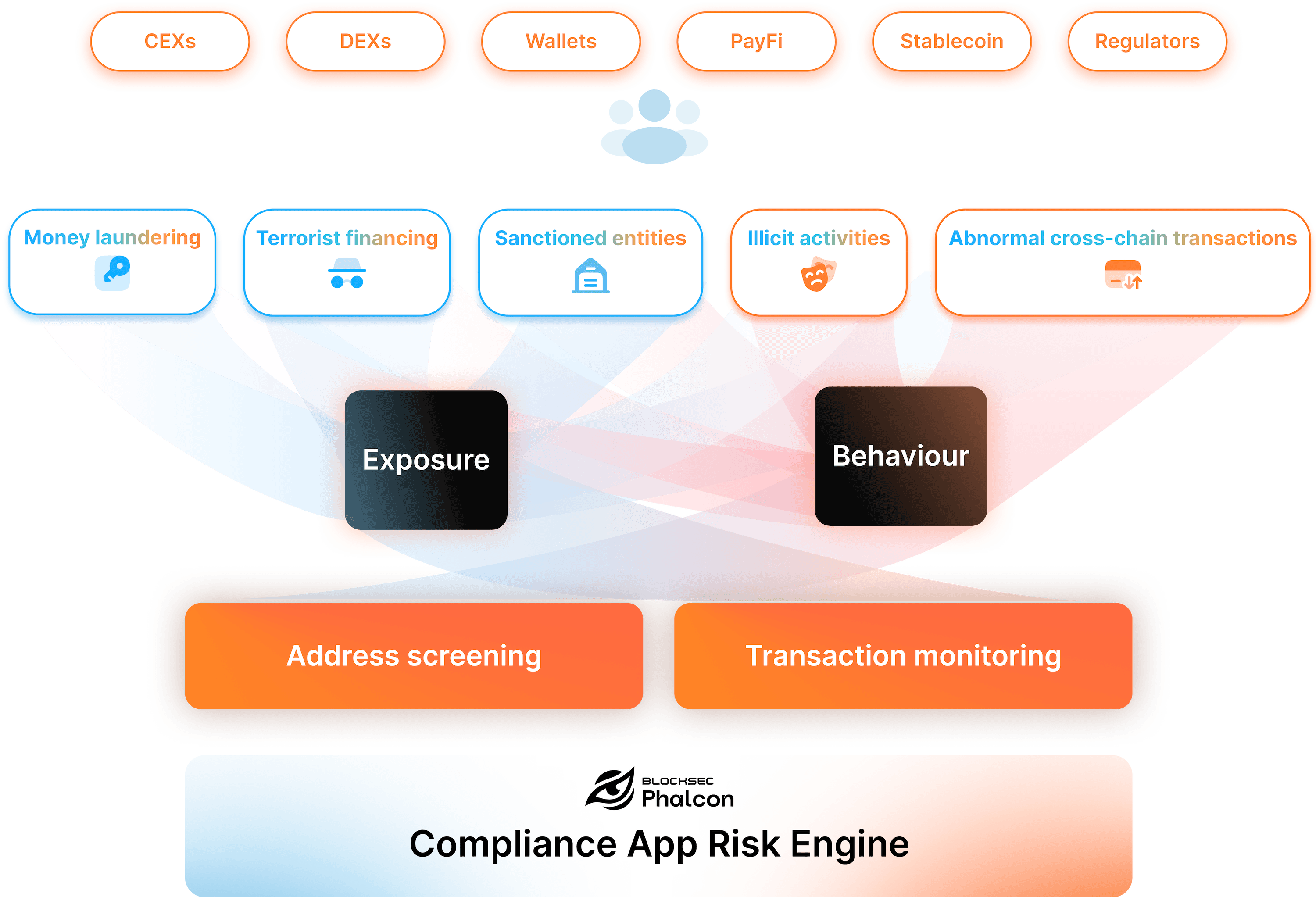
The Phalcon Compliance APP integrates key features such as 400M+ address labels, unlimited-hop tracing, and customizable risk rules. Users can import addresses and transactions to automatically analyze on-chain behaviors and assess risk exposures, enabling precise identification of threats related to money laundering, terrorist financing, phishing, scams, and other illicit activities. The system supports automated alerts, collaborative workflows, blacklist management, and one-click generation of STR reports compliant with regulations in jurisdictions like the U.S., Singapore, and Hong Kong. These features allow organizations to efficiently identify, manage, and respond to compliance risks, ensuring end-to-end dynamic risk management.
- 🔗 Book a product demo: https://blocksec.com/book-demo
About BlockSec
BlockSec is a globally leading blockchain security company, founded in 2021 by a team of renowned security experts. Committed to advancing the security and usability of the Web3 ecosystem, BlockSec offers comprehensive solutions—including code auditing, the Phalcon security and compliance management platform, and the MetaSleuth fund investigation and tracking platform.
To date, BlockSec has served over 500 distinguished clients worldwide. The client roster includes leading Web3 companies such as Coinbase, Cobo, Uniswap, Compound, MetaMask, Bybit, Mantle, Puffer, FBTC, Manta, Merlin, and PancakeSwap, as well as prominent regulatory and consulting institutions, including the United Nations, FBI, SFC, PwC, and FTI Consulting.
Website: https://blocksec.com




