One Platform for Crypto Compliance and Security
Intelligent Compliance. Confident Growth.
Screen, alert, and trace.
Stop illicit funds before they move.
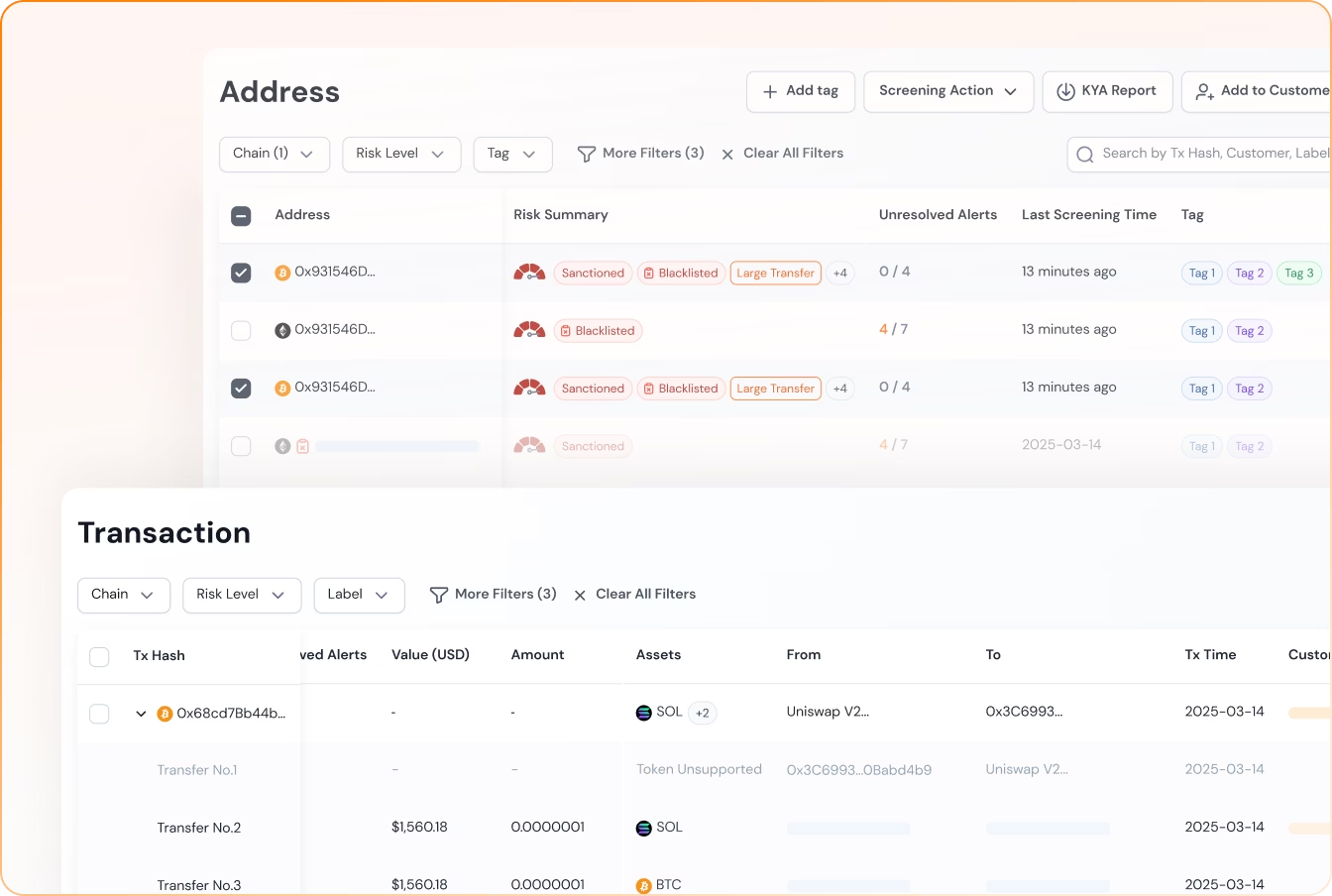
Intelligent and Instant KYA and KYT
Screen counterparties, trace unlimited-hop fund flows, and monitor transactions in real time to reduce AML exposure and keep your Web3 operations compliant.
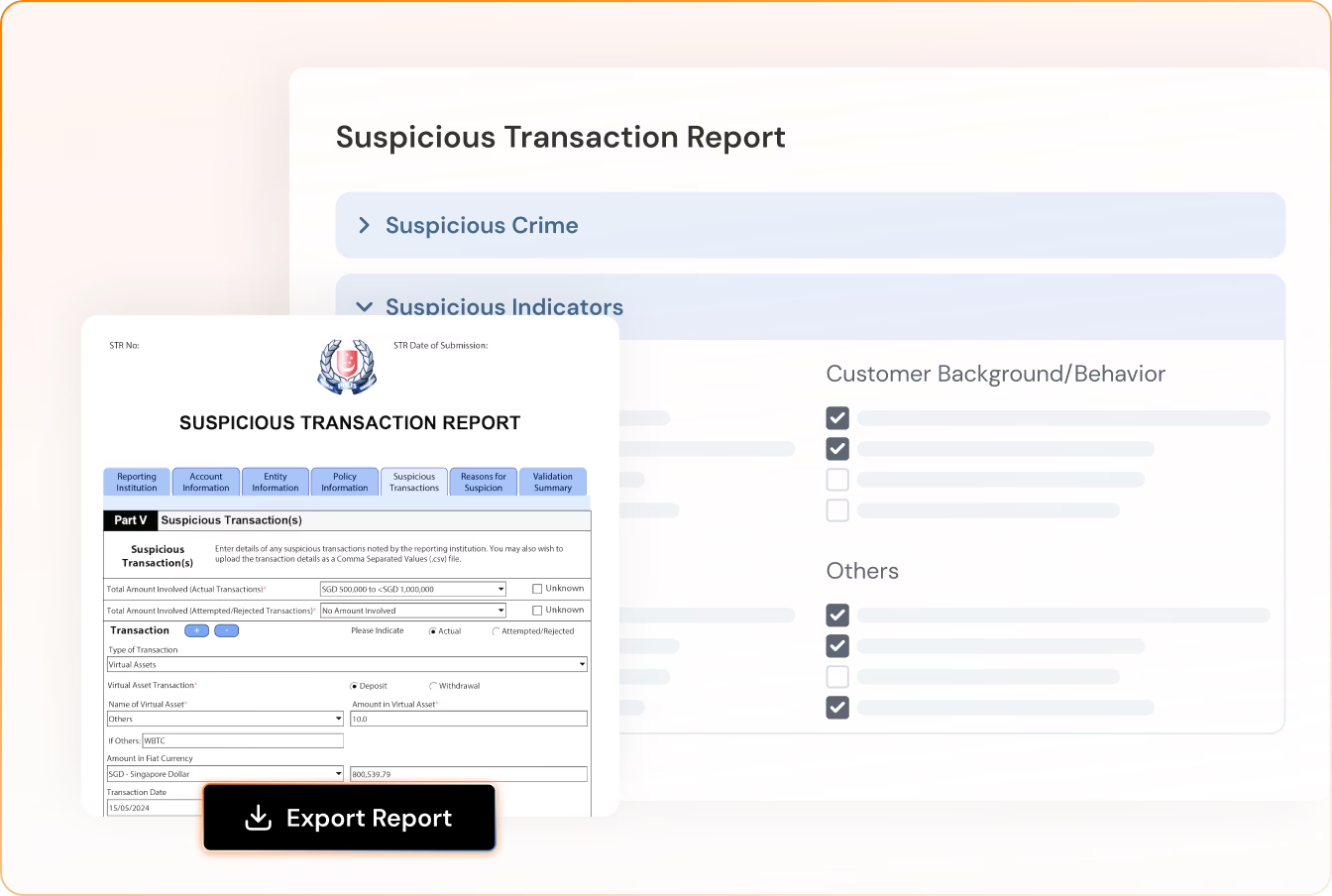
Generate Audit-Ready STR Reports in Seconds
Turn alerts and cases into structured reports, with key evidence and risk context, for faster internal review and regulatory filing.
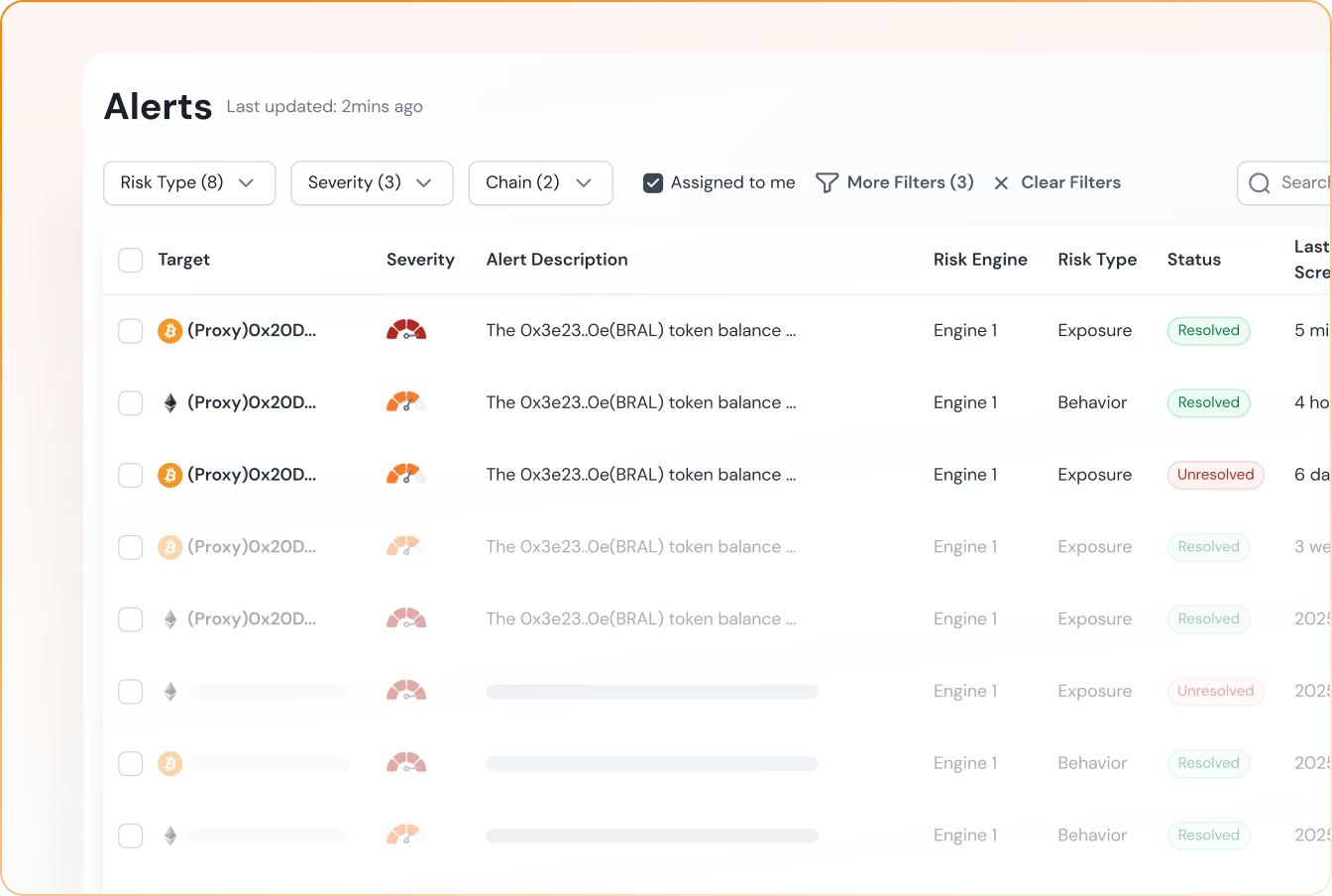
Get Real-Time Alerts on Illicit Funds
Monitor illicit fund inflows before they are withdrawn, and receive real-time alerts to stop laundering at the source.
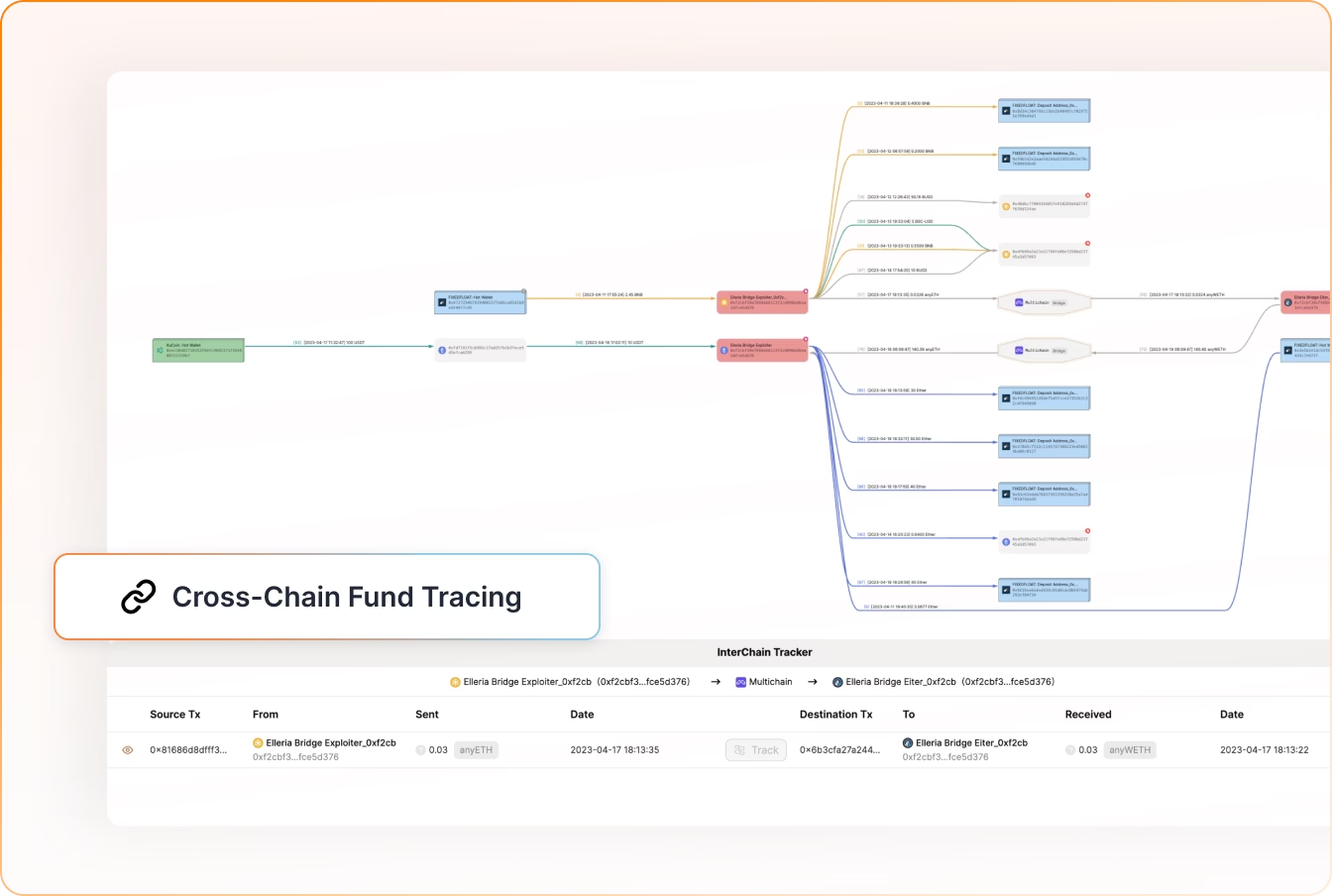
Trace Cross-Chain Flows and Investigate with Evidence
Visualize transaction paths, cluster entities, uncover hidden connections, and produce evidence-ready outputs for investigators, law enforcement, and regulators.
Global Compliance Trusted in 50+ Countries
















































Deep Audits. Safer Launches.
Validate design, code, and business logic.
Find edge cases fast with clear, actionable feedback.
Audits for Contracts, Wallets, and Chains
Audit smart contracts, wallets, and blockchain infrastructure across major chains and languages, backed by deep protocol understanding and complete coverage.
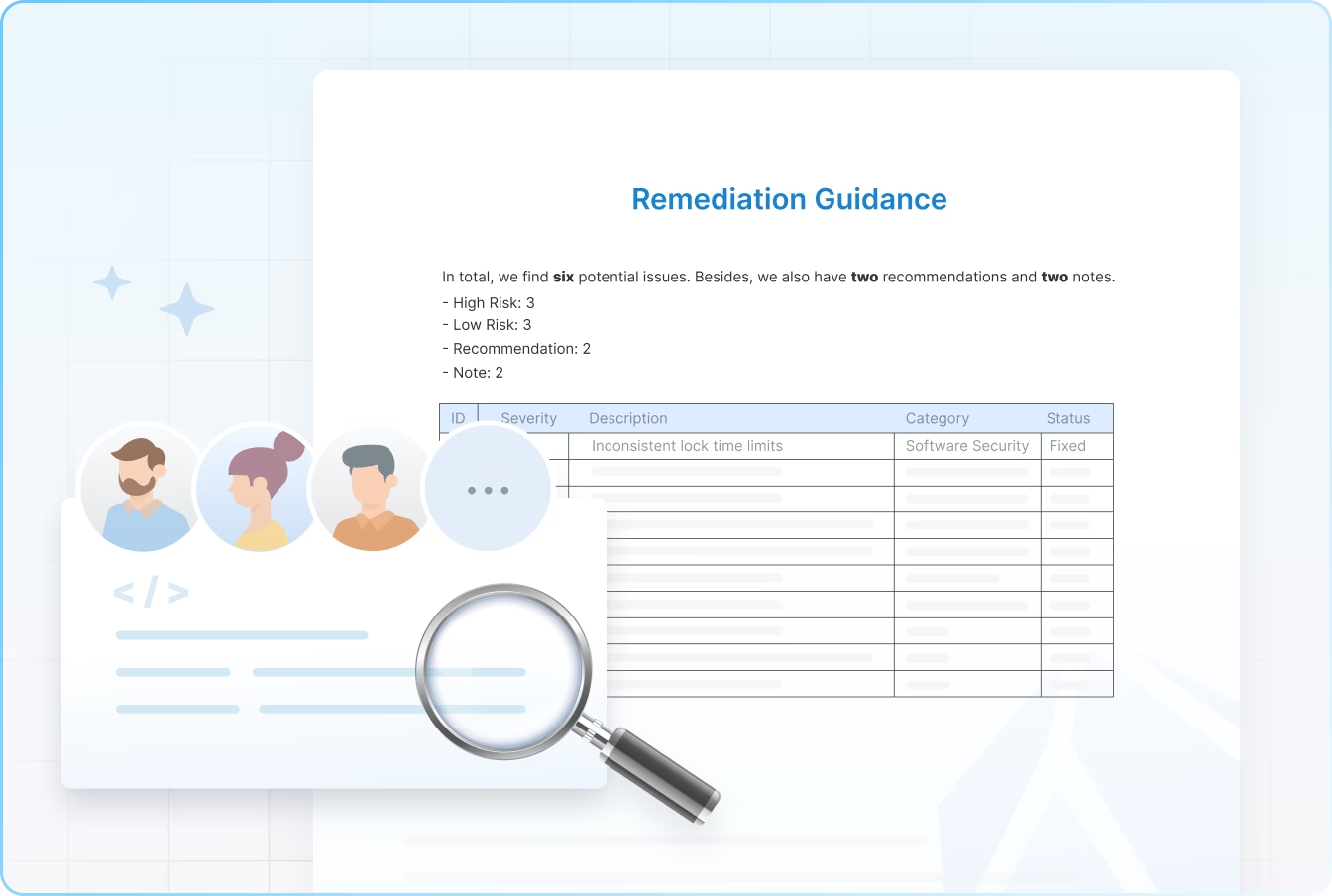
Multi-Auditor Cross-Review with Actionable Fixes
Dedicated teams run independent reviews and systematic cross-checks, then deliver clear, implementable remediation guidance through fast, efficient communication.
Architecture and Threat Modeling that Matters
Start from system design, asset flows, and trust boundaries, identify realistic attack paths, and focus on business logic, edge cases, and pre-launch risk reduction.
In-House Tooling to Uncover Hidden Vulnerabilities
Battle-tested differential testing and customized fuzzing, proven across millions in bug bounties, uncover inconsistencies, edge-case failures, and hidden vulnerabilities.
Audit Reports
View More Reports
Morph


Real-Time Monitoring. Automatic Protection.
Detect, Alert, and Block. Stop hacks across protocols, wallets, and L2s before execution.


Phalcon Security
Detect every threat, alert what matters, and block attacks.


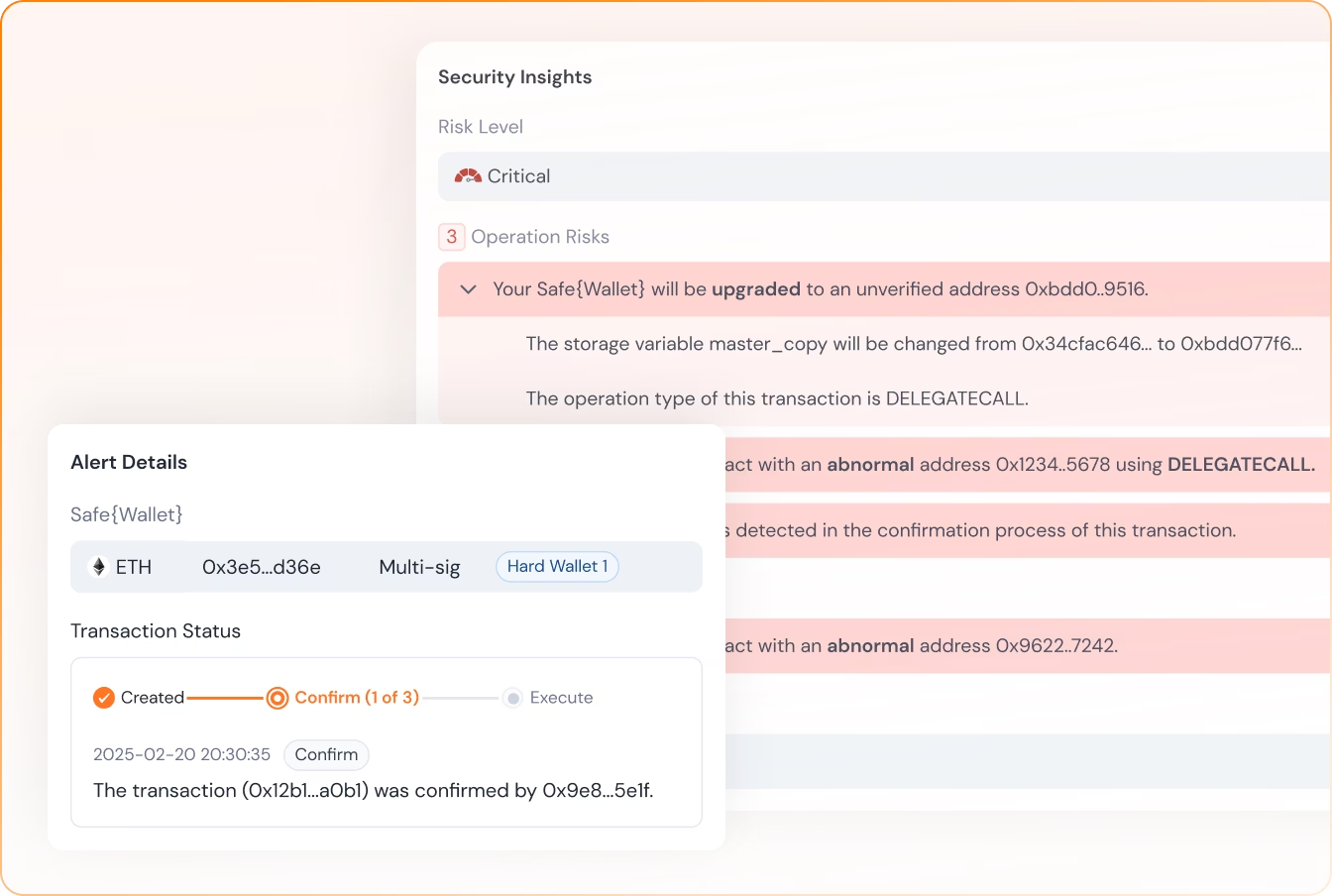
Safe{Wallet} Monitor
Analyze and simulate to ensure your Safe{Wallet}'s security.


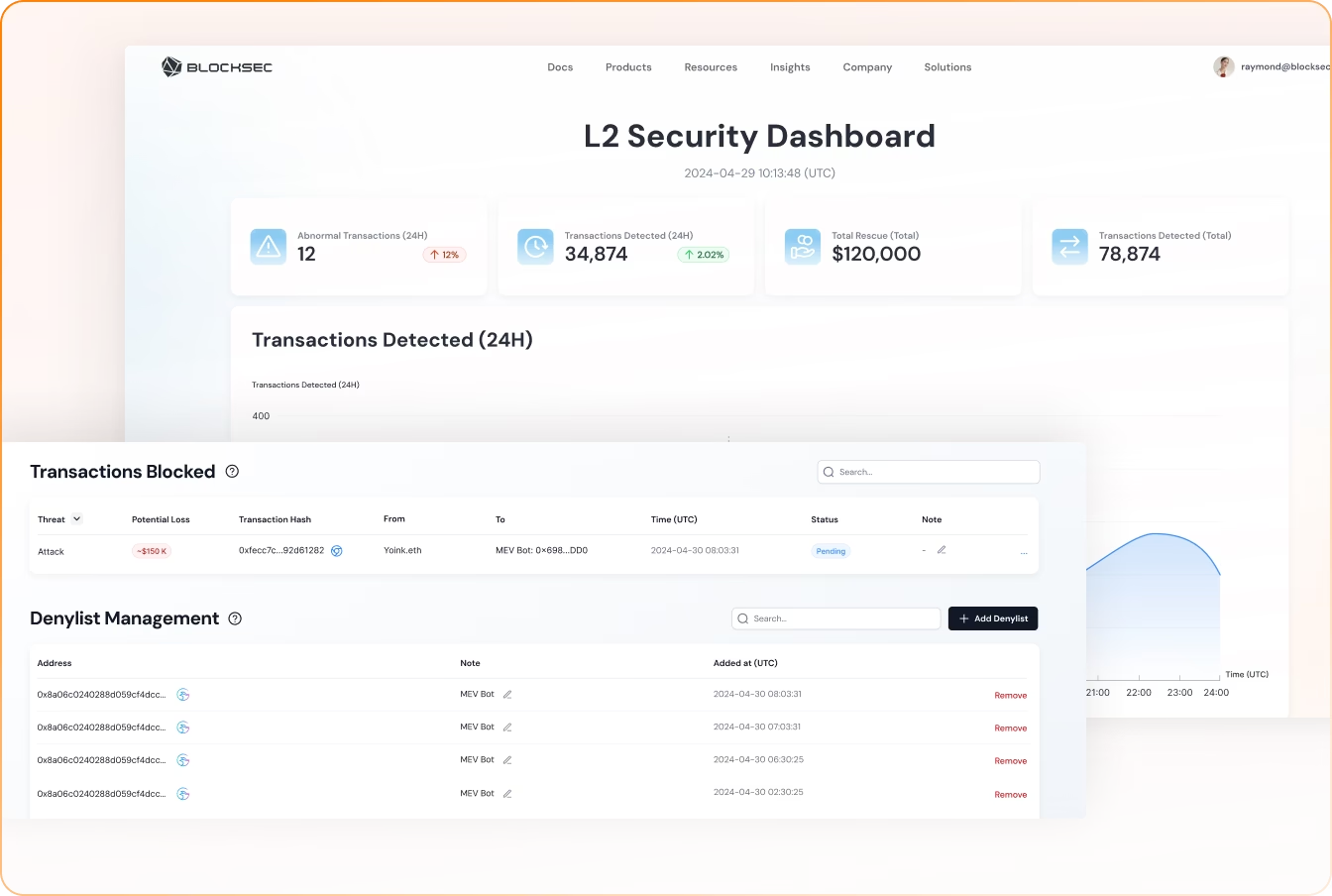
STOP for L2 Chains
Secure your L1/L2 chains, wallets against systemic risk.
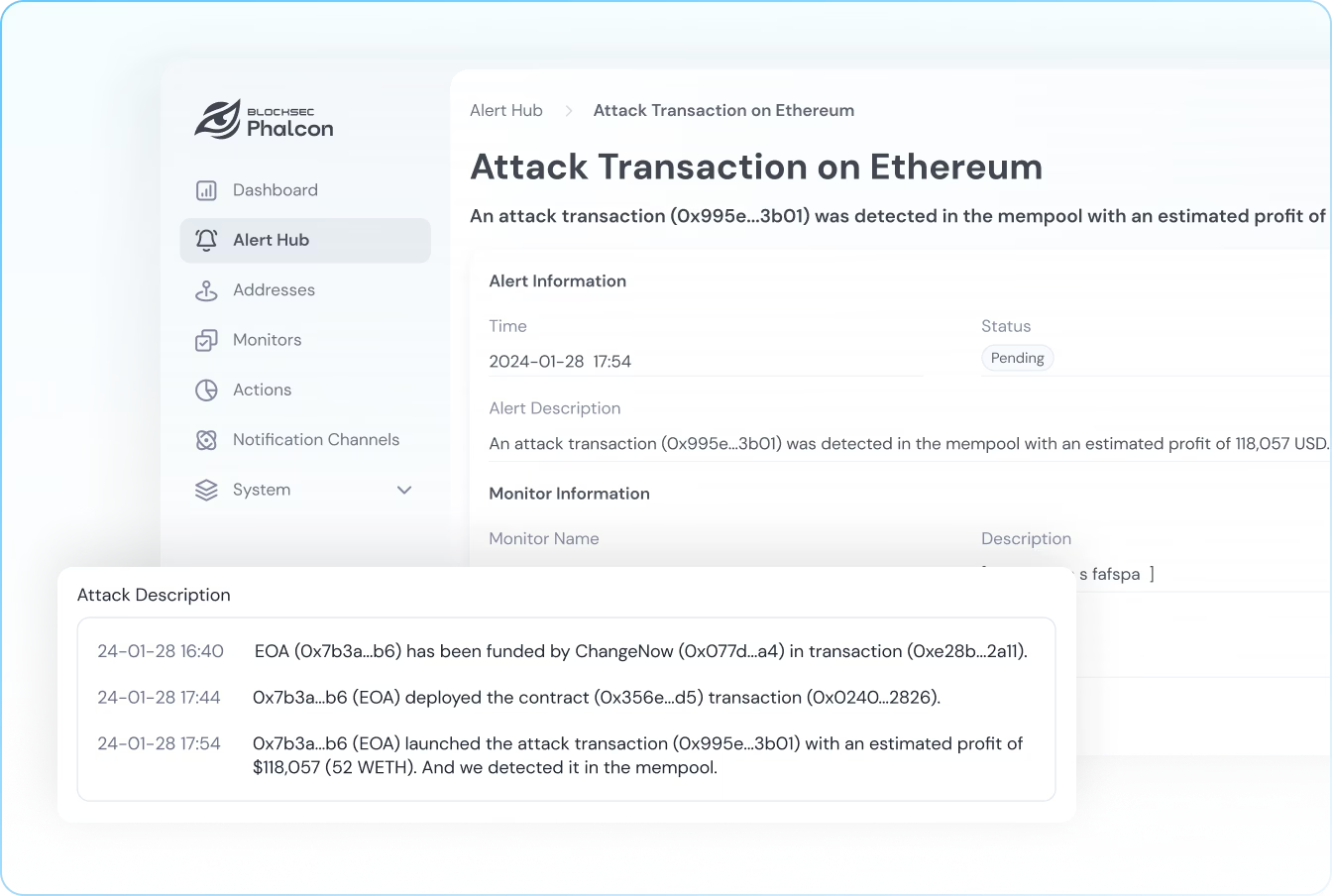
Gain Precise Attack Intelligence
Scan mempool early, scrutinize 200+ hacking signals, and detect threats with the highest precision.
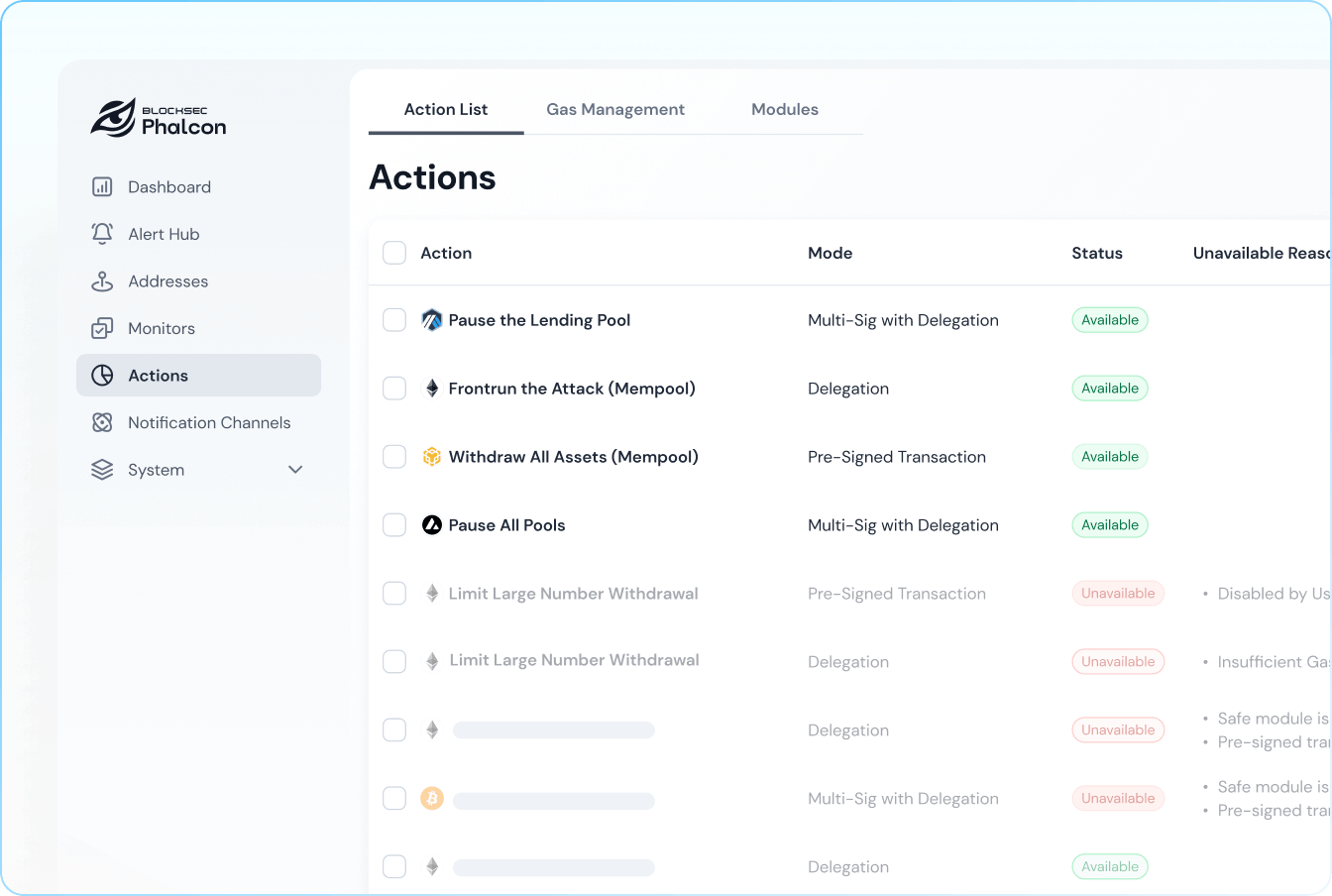
Block Hacks Before Execution
Automatically initiate response actions, place your transaction ahead of attackers, and block hacks before execution.
Sign What You See
Translate complex Safe{Wallet} transactions into human-readable insights, simulate outcomes, and alert suspicious activities before you sign.
STOP Hacks at L2 Sequencers
Screen transactions in milliseconds, block malicious ones with high precision, and blacklist attacker addresses automatically.
Visulize, simulate, and debug on-chain transactions with an intuitive interface.

Testimonials and Endorsements
Trusted by 500+ clients
from Web3 leaders to global regulators

Full Security & Compliance
Partner with BlockSec for end-to-end blockchain security and compliance.



Recent Blogs
Ready to get started?
Sign in to continue, or contact sales to discuss the right product, plan and integration path for your team.

Start your integration
Get compliant faster with KYA and KYT APIs, built for crypto payment, CEX, and DEX.

Request a security audit
Deep audits of code and business logic, with edge-case coverage and actionable fixes.