In October 2022, Mango Markets lost $116 million due to oracle price manipulation.
In May 2022, Venus lost $11.2 million because of oracle price update delay.
Last July, Rho Markets lost $7.6 million after a contract upgrade led to erroneous oracle pricing.
The truth is, these losses could have been completely avoided. How? Read on.
Oracles: The Lifeline of DeFi Protocols
Oracles, which feed data into blockchains, are foundational to DeFi use cases like lending and derivatives. Yet, many major projects—including Compound, Cream Finance, Mango Markets, Venus, and Rho Markets—have suffered significant losses due to oracle-related attacks.
Imagine you deposit an ETH into a lending platform, expecting to borrow some asset, only to find your collateral valued at over 63 thousand dollars! You might think you've hit the jackpot. For protocol teams, though, this is a nightmare scenario. This actually happened last year on Rho Markets.
Price Anomalies: The Overlooked Fatal Flaw
On July 19, 2024, Rho Markets upgraded its smart contracts to launch a new asset market. However, a misconfiguration in the deployment script caused the BTC and ETH prices from the oracle to be reversed. As a result, the ETH price was erroneously inflated by 20 times, allowing users to borrow massive amounts at a minimal cost—and ultimately leading to $7.6 million in losses.
Key Timeline (UTC):
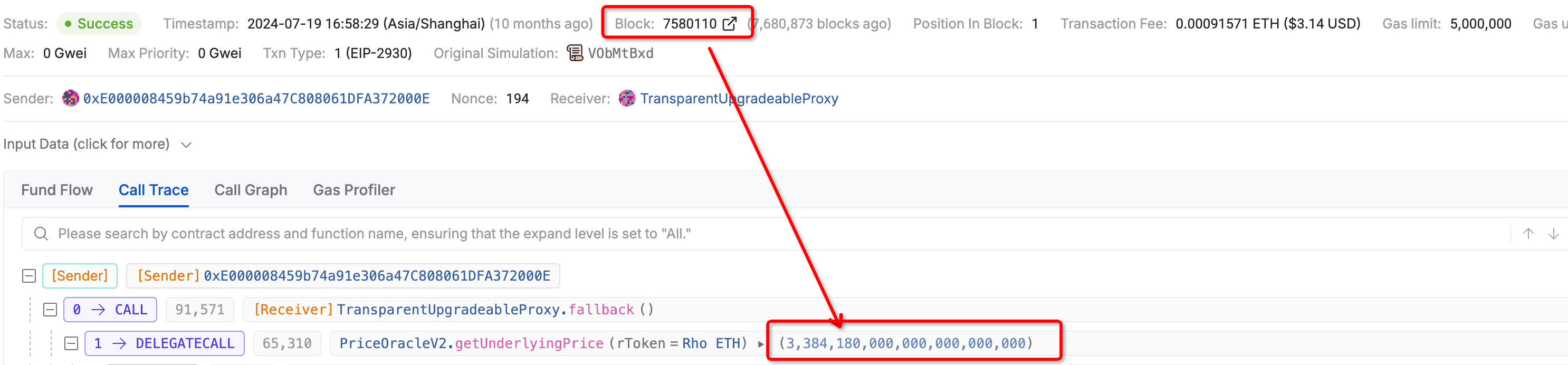
- 1️⃣ 08:58:29 (Block 7580110) — The oracle returned the normal ETH price.
-
2️⃣ 08:58:32 (Block 7580111) — The oracle contract was updated. Transaction hash: https://app.blocksec.com/explorer/tx/scroll/0x9d2388a0c449c6265b968d86f0f54e75a5b82e2b04176e35eefdff5f135547ec
-
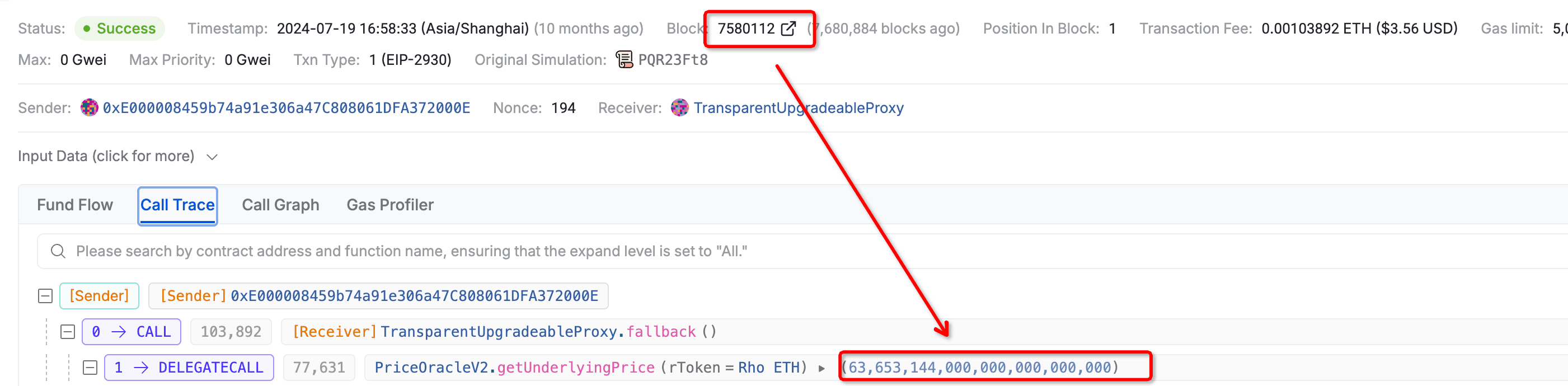
3️⃣ 08:58:34 (Block 7580112) — One block later, the ETH price returned by the oracle soared from $3,384 to $63,653 (BTC price was mistakenly applied to ETH), 17 times the actual value!
-
4️⃣ 08:59:49 — Just a minute later, the first attack was launched: an MEV bot used 84 ETH as collateral to borrow 942 wstETH. Repeating this process, the bot drained $7.6 million. Transaction hash of the first attack: https://app.blocksec.com/explorer/tx/scroll/0x0a7b4c6542eb8f37de788c8848324c0ae002919148a4426903b0fb4149f88f05
-
5️⃣ 10:33:01 — The vulnerable components on the protocol were disabled, but it was already too late.
If Rho Markets had deployed Phalcon's Oracle Monitors, how would things be different?
👉 👉 Phalcon would have instantly detected the abnormal price and triggered an automated emergency response—completely shutting down any opportunity for an attack.
Phalcon supports oracle price anomaly monitoring:
-
Price Deviation: Monitors the magnitude of oracle price changes and flags abrupt spikes or drops. (e.g., alert if the price changes by more than 200% between two samples)
-
Price Range: Sets acceptable price boundaries. (e.g., alert if price moves outside the $2,380–$4,380 range)
-
Price Mismatch: Compares base oracle's price with a reference oracle. (e.g., alert if prices differ by more than 30%)
Typically, the project team will rigorously check critical configs before contract upgrades or parameter changes. However, in this incident, a manual oversight led to the omission of oracle price checks. Although the lost assets were returned by the MEV bot in this case, such "luck" is rare in most attacks.
In reality, setting up any of the above monitors would have enabled the system to catch abnormal oracle values right away and alert the team through any of the seven supported notification channels. More importantly, manual intervention is often too slow—the time between an anomaly and an exploit can be extremely short (in this case, just one minute). With Phalcon, emergency defenses are triggered automatically, so attacks simply have no chance to happen.
Delays and Failures Can Also Be Deadly
In May 2022, as $LUNA's price continued to plunge, Chainlink's built-in circuit breaker was triggered, causing price updates for $LUNA to pause at $0.107. The Venus protocol failed to notice that in time and continued operating with the outdated price. Four hours later—by the time the team responded—the actual price had dropped to $0.01. During this period, several addresses used $LUNA as collateral to borrow large amounts of assets, resulting in a loss of about $11.2 million for the protocol.
If Venus had deployed Phalcon's Oracle Monitors, how would things be different?
👉 👉 Phalcon supports monitoring for price update delays and oracle health checks—ensuring timely and reliable price feeds. If any anomalies had occurred, the team would have been instantly alerted.
Many projects rely on a single oracle as their price source and lack mechanisms to guard against price anomalies. When things go wrong, attackers profit, users get liquidated, and project reputations take a hit.
Phalcon can monitor both custom and third-party oracles (such as Chainlink and Pyth), providing real-time assurance of price stability and accuracy, preventing liquidation and price manipulation risks.
What's BlockSec Phalcon?
Phalcon seamlessly combines Security Threat Prevention (Security APP) and Compliance Risk Management (Compliance APP), offering users an integrated solution for both security and compliance.

Security APP
🔗 https://blocksec.com/phalcon/security
Delivers comprehensive post-launch protection, including:
- Real-time attack monitoring
- Operational, interaction, financial, and custom risk monitoring
- Safe{Wallet} dynamic protection
- Flexible monitoring for token prices, amounts, key variables, sensitive events, and function calls
- Automated emergency response (supports EOA and multi-sig wallets)
Compliance APP
🔗 https://blocksec.com/phalcon/compliance
Screens addresses and monitors transactions in real-time, helping VASPs identify risk exposure and suspicious user activity to meet AML/CFT compliance requirements.
🔥 Try it Now
BlockSec Phalcon now supports 30+ major blockchains, including Ethereum, BSC, Solana, Base, Tron, Arbitrum, Avalanche, Optimism, Manta, Merlin, Mantle, Sei, Bitlayer, Core, BoB, Story, Sonic, Gnosis, and Berachain.
Book a product demo now! Click here or visit the link below. Get started in just 10 seconds—the first 30 sign-ups get a free trial!
🔗 Book a Demo: https://blocksec.com/book-demo




