On April 9, 2023, SushiSwap became the target of an exploit due to an Unverified External Parameter. The total loss is about $3.3 million.
As a leading protocol on Ethereum with a substantial user base, such top protocols are still susceptible to introducing serious new issues during contract upgrades. It's a reminder for the DeFi community that security should always be the top priority. Moreover, this security incident was triggered by a whitehat security researcher's attempt at a rescue, generating considerable debate within the community, and we provide a succinct introduction to this incident, highlighting it as one of the top ten security incidents of 2023.
Background
SushiSwap
SushiSwap, a renowned DEX, launched a vampire attack against Uniswap, achieving tremendous success. At its peak, its TVL reached $8 billion, and it still maintains around $400 million.
Approval
In short: permission for a contract to access and transfer out a specific token from your wallet.
For convenience, many contracts default to ask for unlimited approval. Many users, worried about security risks, only deposit small amounts into various protocols. However, these users grant unlimited funds approval to the protocols, If a protocol is compromised, all approved tokens in the account could be lost.
The Vulnerability
Unverified External Parameter
The RouteProcessor2 contract's processRoute() allows users complete control over the call flow (parameter route) .
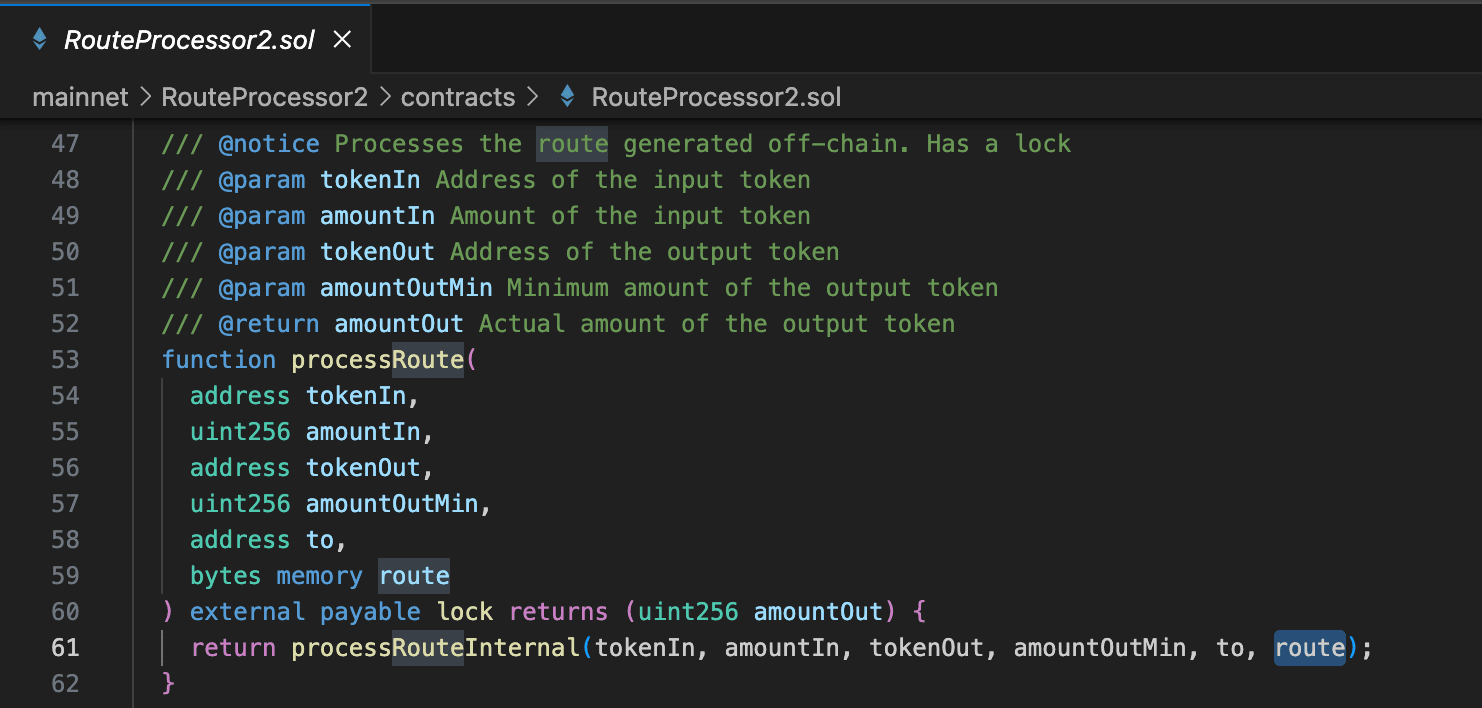
 And in
And in uniswapV3SwapCallback(), the safeTransferFrom()'s parameter from is decoded from the user-provided route.
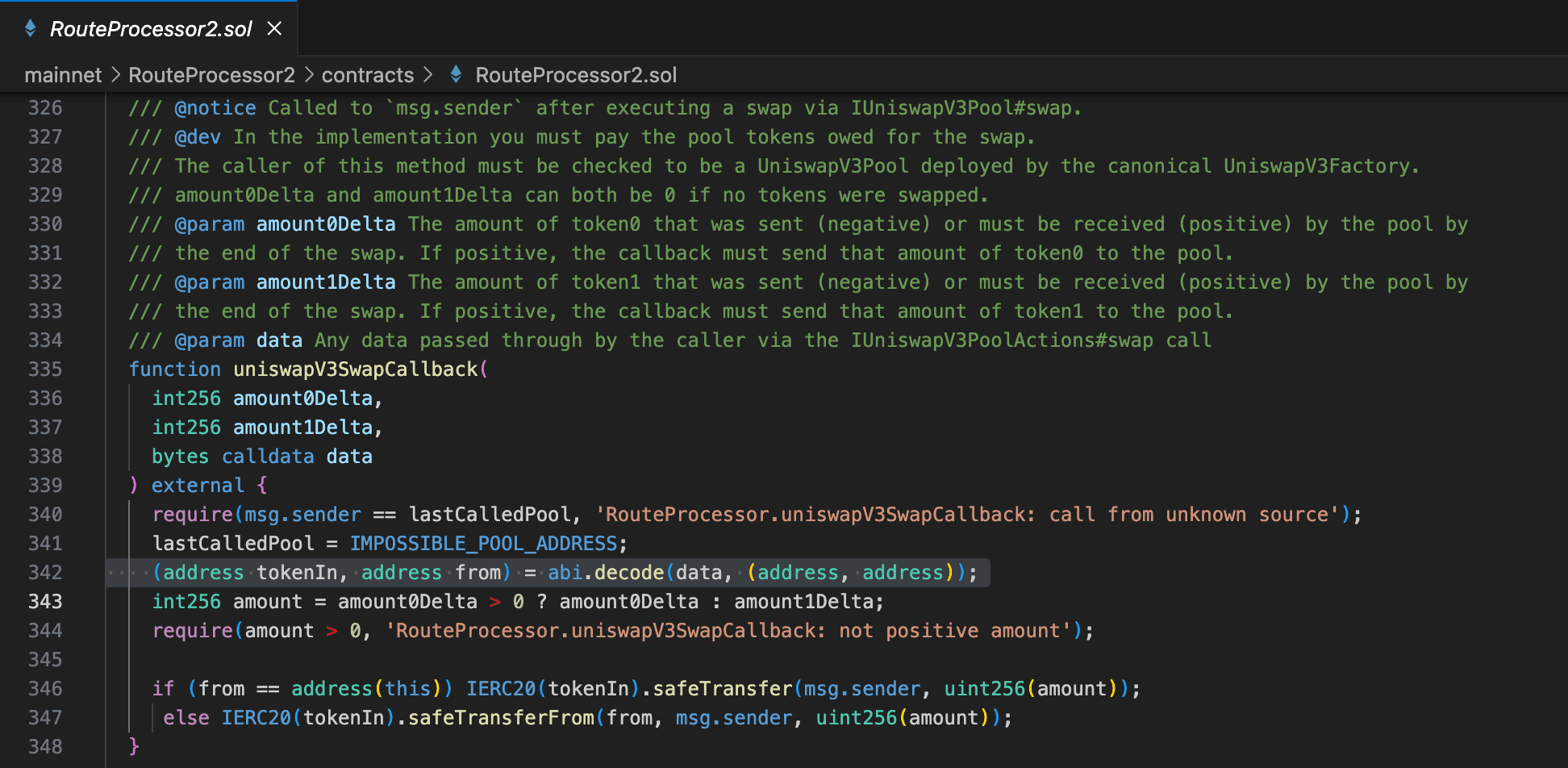 As a result, users who approved the RouteProcessor2 contract lost their assets.
As a result, users who approved the RouteProcessor2 contract lost their assets.
The Attack Process
This incident involved multiple attack transactions, but we'll use the first attack transaction as an example. Transaction: 0x43ff7e01423044cfb501b4fe9ef1386725c0ddc117dadd6e6620cb68bdeaf4f9
- The attacker called the vulnerable RouteProcessor2 contract's
processRoute()with a carefully constructed long argumentroute.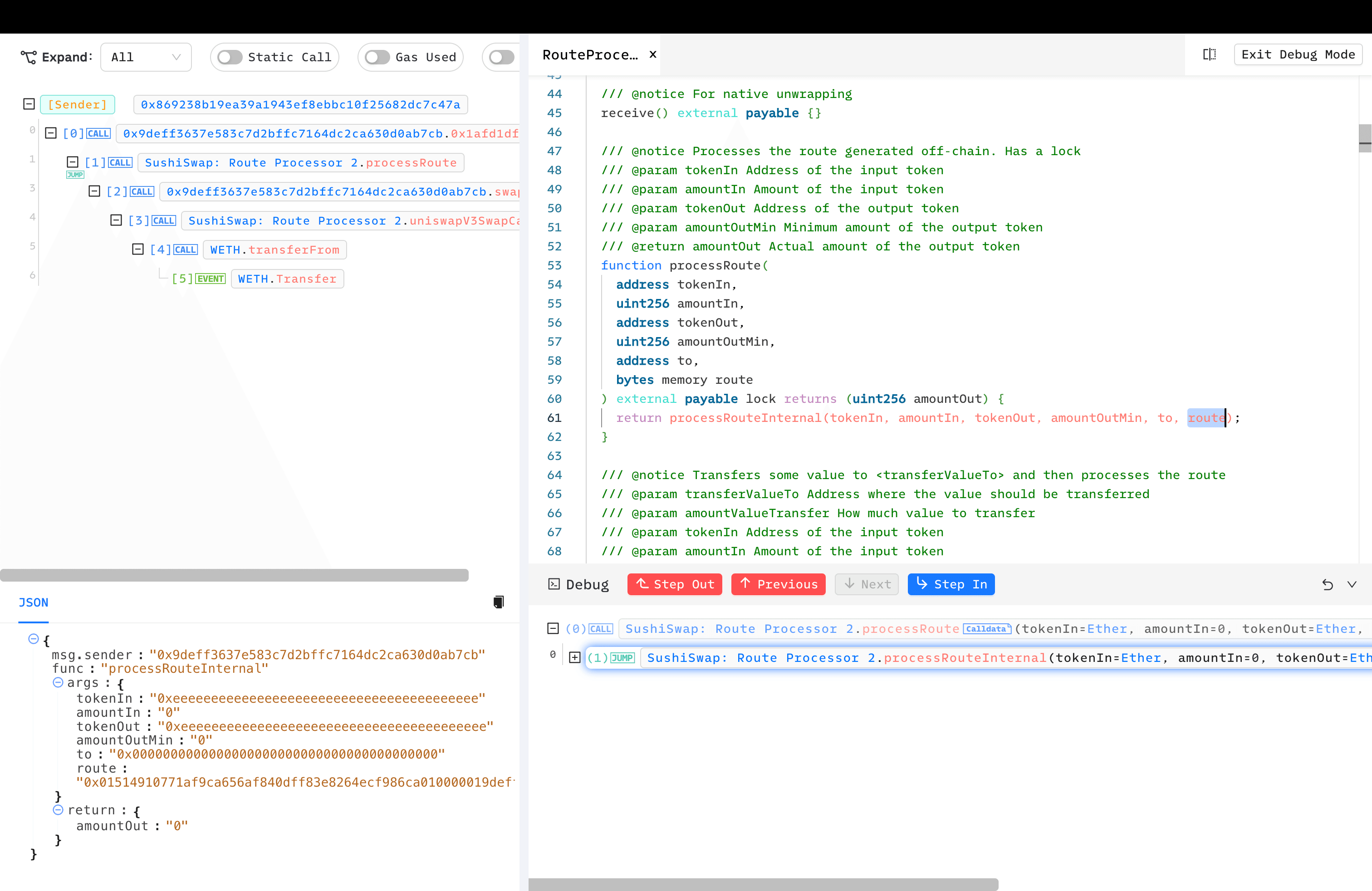
processRouteInternal()creates anInputStreambased on the route provided by the user.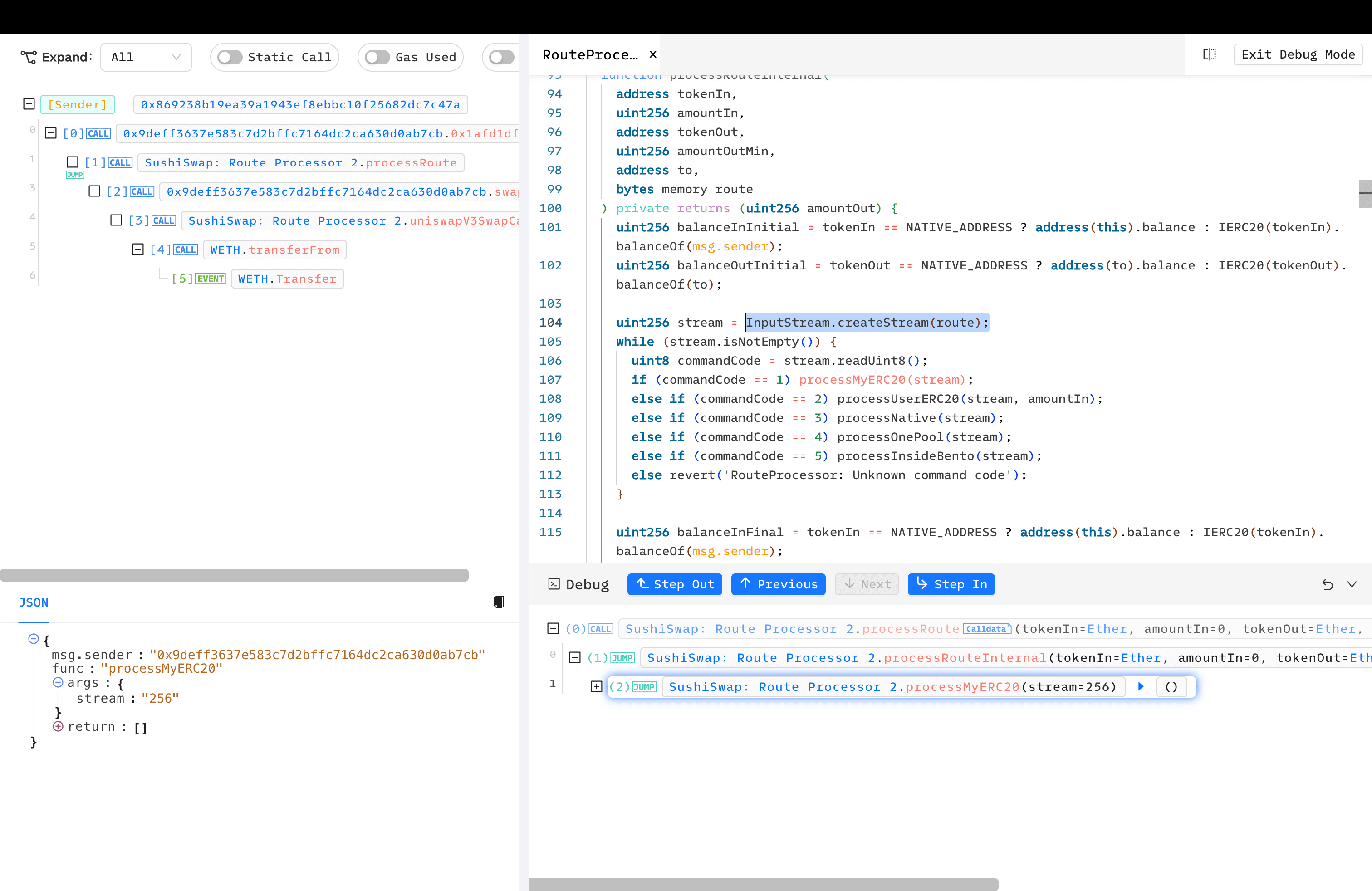
- The transaction followed the attacker's
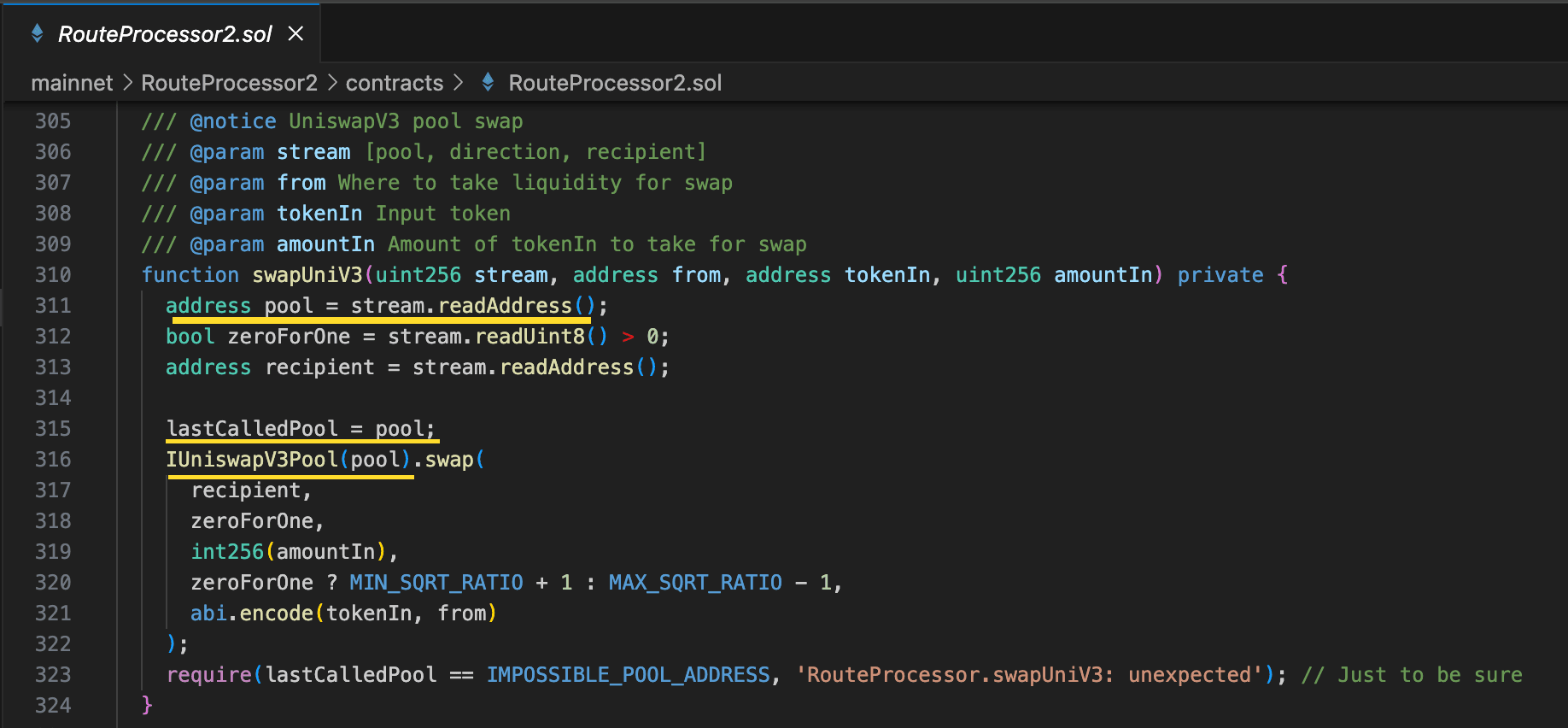
routeuntil reachingswapUniV3(). Note that thepoolis decoded from thestream, meaning the attacker controlled whichpooltoswap()in, setting it as thelastCalledPool.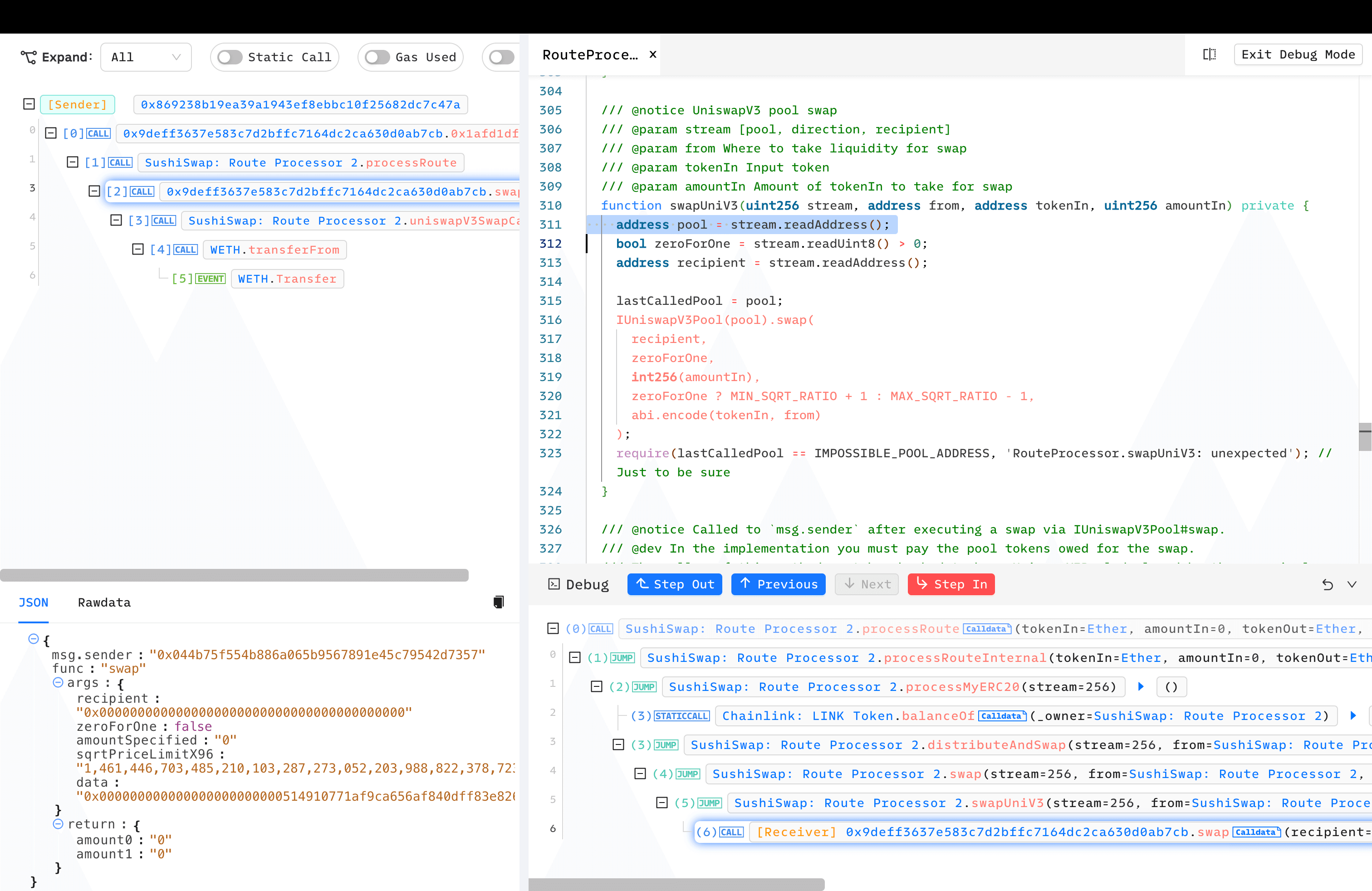
- This called the malicious contract deployed by the attacker, who then simply pass malicious
calldatato call back to RouteProcessor2'suniswapV3SwapCallback(). - uniswapV3SwapCallback() requires the
msg.sendercheck, but since thelastCalledPoolhad already been set to the malicious contract, the hacker bypassed the check. Importantly, thesafeTransferFrom()'s parameterfromwas decoded from the attacker-constructedcalldata.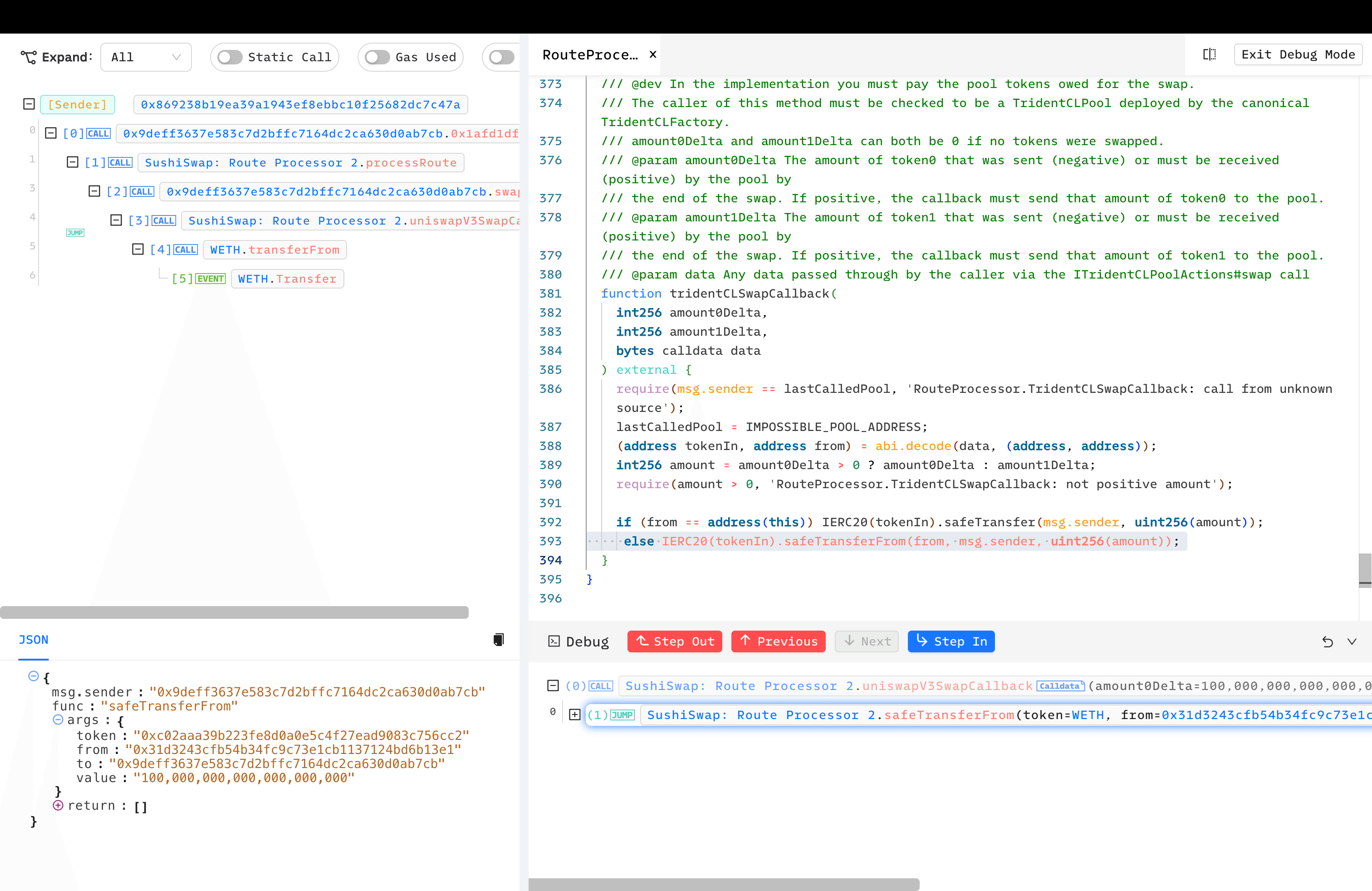
- Victim's assets are transferred to the malicious contract deployed by the attacker.
Controversial Whitehat Rescue
It’s worth mentioning that a whitehat by the username @trust__90 identified this issue and attempted to rescue funds, but this rescue attempt caused a disaster.
- Using the mempool to broadcast transactions instead of a private RPC.
- Attempting to rescue only 100 Ether instead of all at risk.
This opened the door for MEV Bots and other attackers to execute multiple copycat transactions, effectively draining most of the funds. After these events, @trust__90 faced backlash and sought to defend his actions.
People are saying all kinds of terrible things while being uninformed so allow me to share more details.
— Trust (@trust__90) April 10, 2023
I've initiated coordination privately with Immunefi officials 3 hours before the white-hack. 90 minutes later, I realized the asset is currently used by the frontend and…
BlockSec Rescue
In this attack, we also rescued 100 Ether and returned the funds to the victim, 0xsifu.
To date, we have successfully thwarted over 20 real-world hacks and rescued more than $14,000,000 worth of assets.Hey, @0xsifu We have successfully blocked an attack transaction and rescued 100 Ether. Please get in touch with us.
— BlockSec (@BlockSecTeam) April 9, 2023
Security Recommendations
Upgrades Should Always Be Audited
It's a reminder for the DeFi community that security should always be the top priority. Audits are not a guarantee of security, but the absence of an audit certainly does not ensure safety.
Mitigations for Approve Issue
The year 2023 saw numerous incidents involving approval attacks, and we seize this opportunity to reemphasize the importance of managing approvals. A security practice is to approve only the necessary amounts, or if convenience is a priority, to approve a slightly larger amount than needed.

BlockSec's MetaSuites offers a convenient Approval Diagnosis feature. Additionally, tools like Revoke Cash can be used to regularly check approval statuses.
Adopt Monitoring and Automatic Response Mechanisms
Ethereum is a dark forest, and everyone in the DeFi community faces various risks and challenges, even security experts. In 2023, we launched Phalcon, the industry's first automated response system designed not just for monitoring attacks but for actively blocking threats in real-time. Phalcon’s battle-tested capabilities have proven their effectiveness by successfully thwarting over 20 real-world hacks and rescuing more than $14,000,000 worth of assets. This innovation ensures that all stakeholders can sleep more soundly at night, knowing that proactive measures are in place to protect their investments.
Read other articles in this series:
- Lead-In: Top Ten "Awesome" Security Incidents in 2023
- #1: Harvesting MEV Bots by Exploiting Vulnerabilities in Flashbots Relay
- #2: Euler Finance Incident: The Largest Hack of 2023
- #3: KyberSwap Incident: Masterful Exploitation of Rounding Errors with Exceedingly Subtle Calculations
- #4: Curve Incident: Compiler Error Produces Faulty Bytecode from Innocent Source Code
- #5: Platypus Finance: Surviving Three Attacks with a Stroke of Luck
- #6: Hundred Finance Incident: Catalyzing the Wave of Precision-Related Exploits in Vulnerable Forked Protocols
- #7: ParaSpace Incident: A Race Against Time to Thwart the Industry's Most Critical Attack Yet
- #9: MEV Bot 0xd61492: From Predator to Prey in an Ingenious Exploit
- #10: ThirdWeb Incident: Incompatibility Between Trusted Modules Exposes Vulnerability




