Since BlockSec’s debut in 2021, we have long maintained that code auditing alone cannot solve Web3 security issues. Therefore, we have been investing in exploring new paradigms for Web3 security. Thus we created Phalcon, the world's first crypto hack-blocking system.
Before the launch of Phalcon, the system had been running internally for 2 years, successfully blocking over 20 hacks, and rescuing more than 20 million USD worth of assets, including $3.8 million for Saddle Finance, $2.4 million for Platypus, $5 million for ParaSpace, and more.
In this series of articles, we will present representative successful stories of our system Phalcon. Today let's take a look at the industry's first "hacking back" that rescued $300,000.
How We Recover the Stolen Funds for TransitSwap (and BabySwap)
The ever-evolving contest between attack and defense reflects the real world's diversity and color. Our experience demonstrates that proactive threat prevention is not a single unique skill; rather, it's a systematic approach that combines various security know-how and efforts.
This story highlights the intricate dance of cybersecurity as we recall our experiences with the BabySwap and TransitSwap attacks on BSC. For a detailed analysis, please refer to our previous report.
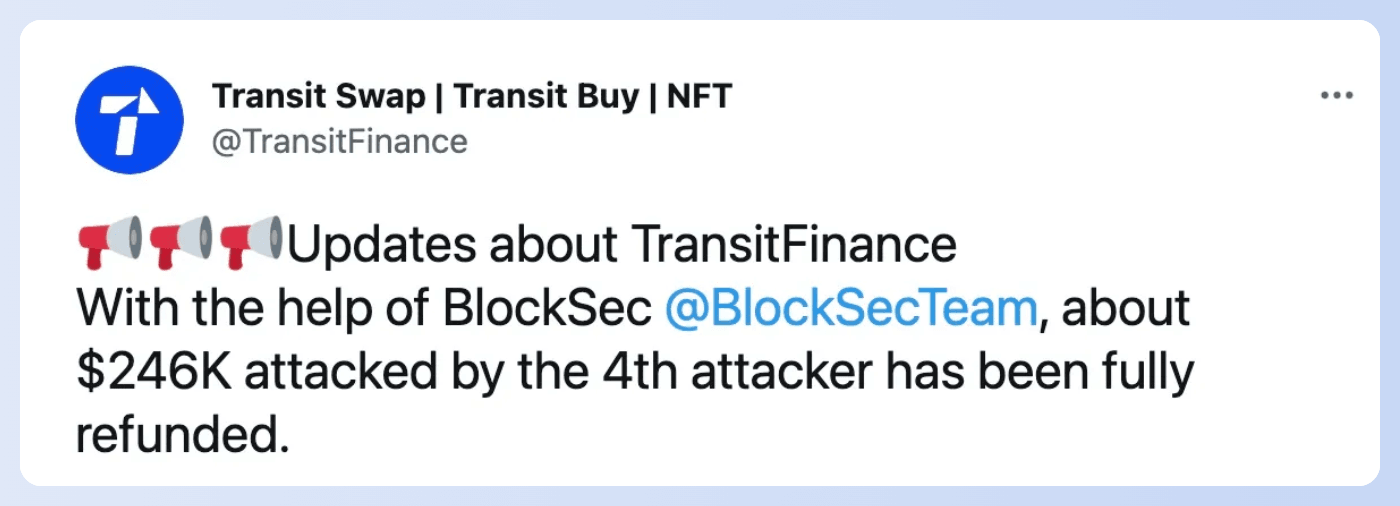
On October 1, 2022, at 14:47 UTC, our internal system identified an attack transaction. During our investigation, we discovered that the transaction was initiated by a bot account that front-ran the original attack. The account exhibited a pattern with eight leading zeros, suggesting that it was generated by the vulnerable Profanity Tool.
Opportunity favors the prepared, and we had already developed a rescue tool to recover the private key of vulnerable profanity addresses, based on our previous efforts.
By 16:10 UTC, our tool swiftly recovered the bot's private key in just 20 minutes. We promptly transferred the funds to a secure account, as per our standard rescue procedure. This measure ensured that others who might recover the private key would not be able to access the account and compromise the funds.
However, we faced a hurdle: the funds were in the contract deployed by the bot, not its EOA account. Decompiling the contract, we identified a withdraw function that could be used to retrieve the funds (as shown in the following figure).
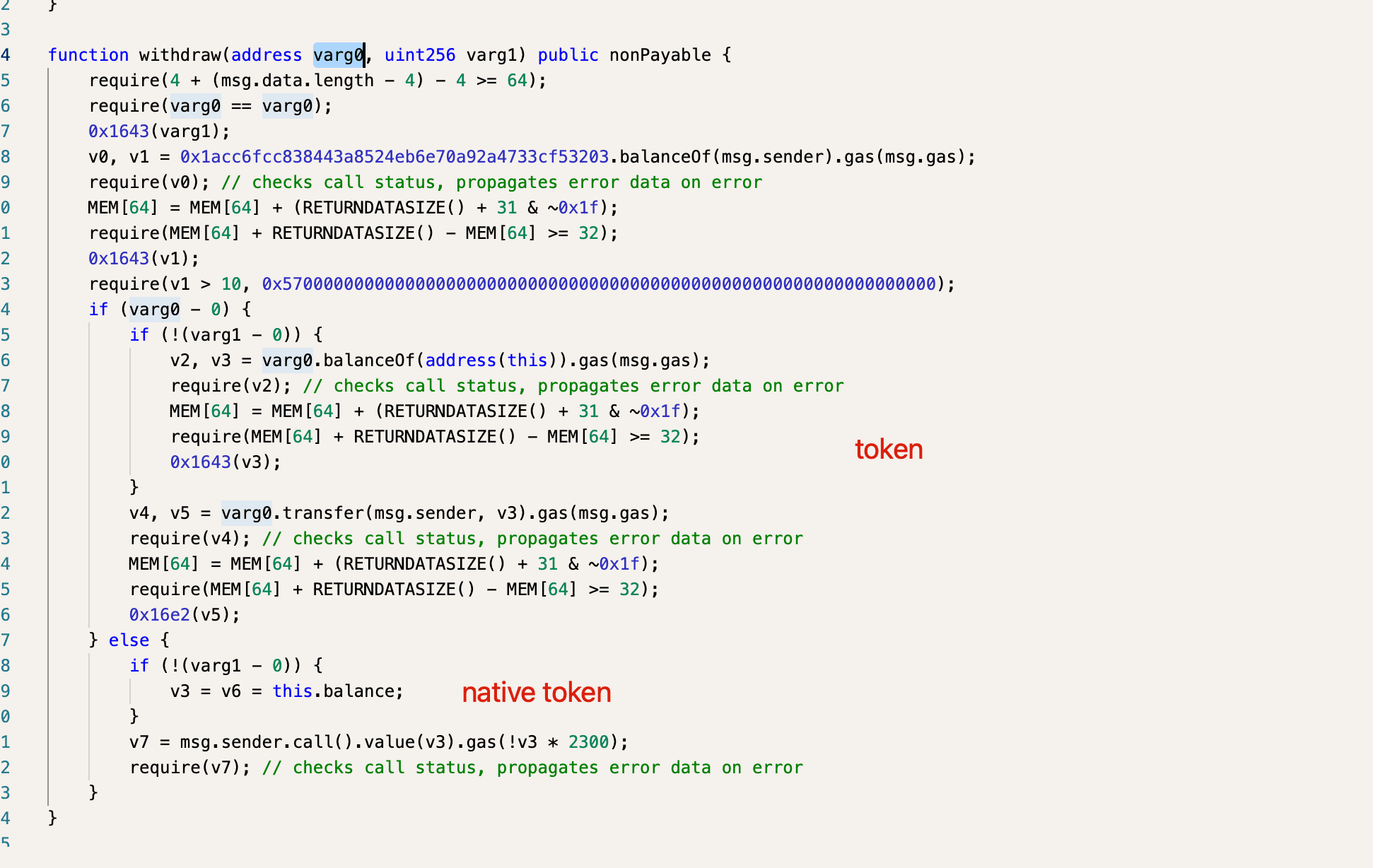
With the token address as the first argument and zero as the second, we executed a transaction, successfully withdrawing the funds from the contract to the bot and then transferring them to our secure account.
A few hours later, our system detected another attack on TransitSwap. Among several attack transactions, one was again front-run by the bot. However, since the contract deployed by the bot differed from the previous one, the function to transfer the funds out was also different.
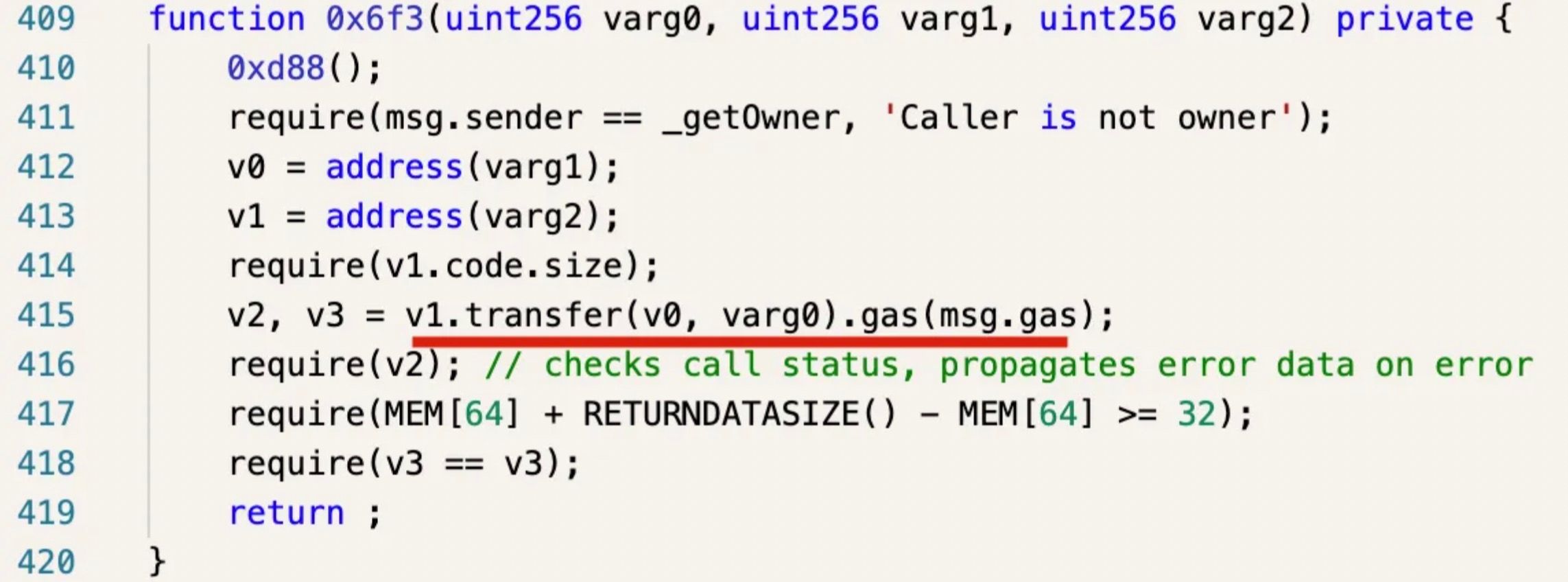
We decided to return the funds to the attacked projects (rather than the bot) for the following reasons:
- First, the bot obtained the funds by front-running attack transactions, which we consider to be an attack itself;
- Second, the funds belonged to the victims of the attack, i.e., the users of the affected DeFi protocols. These users had already suffered due to vulnerabilities in the DeFi protocol and deserved to receive the funds from the attackers.
The systematic approach significantly benefits us in addressing real-world security threats, emphasizing the importance of continuous learning and adaptation in the ever-changing landscape of cybersecurity.
How to Access the Service
- Phalcon is a SaaS platform. You can log in to our website to explore features, view pricing, and subscribe directly.
- You can also book a demo to learn more about Phalcon and receive expert security advice.
Let Phalcon build a defense line for your protocol. It doesn't require much work on the protocol side and would never bring in additional risk. It's just like a shield providing an additional layer of safety. Book a demo now!
See More Success Stories of Phalcon
- Blocked HomeCoin Attack: Industry's First Successful Blocking Story
- Blocked Saddle Finance Attack: Industry's First Influential Blocking to Rescue $3,800,000
- Blocked Platypus Attack: Industry's First Counter-Exploitation of a Hacker's Contract
- Blocked Paraspace Attack: Industry's Most Important Block that Rescued $5,000,000
- Blocked Loot Attack: How Phalcon Saved $1.2M from Malicious Proposal
About Phalcon
Phalcon is an attack monitoring and automated blocking platform launched by BlockSec. The platform is capable of accurately identifying attacks and automatically blocking them. Phalcon aims to provide comprehensive post-launch security protection for Web3 projects, including continuous monitoring, attack blocking, and emergency response, safeguarding on-chain assets for protocol providers, LPs, and DAO organization participants.
To date, Phalcon has successfully blocked over 20 hacker attacks, rescuing more than $20 million in assets. Even in the early customer stage, Phalcon gained recognition and a grant from the top DeFi protocol Compound and established an attack-blocking platform for it.
Website: https://blocksec.com/phalcon
Twitter: @Phalcon_xyz
Telegram: https://t.me/BlockSecTeam




