
0. Review
- Secure the Solana Ecosystem (1) — Hello Solana
- Secure the Solana Ecosystem (2) — Calling Between Programs
- Secure the Solana Ecosystem (3) — Program Upgrade
- Secure the Solana Ecosystem (4) — Account Validation
1. Overview
In the previous blog, we discussed the account validation, which is important to access control, in Solana programs. However, for a decentralized DApp and to protect the potential private key leakage, multi-sig is very important. In this post, we will introduce the implementation of the Multi-Sig.
2. Concept of Muti-Sig
Multi-Sig is a digital signature scheme that allows a group of users to sign a single transaction. The transaction could be a call to a privilege function (e.g., mint), a fund transfer instruction, etc. The mechanism of multi-sig is that given n parties with their own private keys, at least m of the private keys must sign to execute the transaction. This can make the funds in DeFi much safe and can protect the potential risk like private key leakage and rug pull.
3. Usage of Multi-Sig
In Solana, there is a multi-sig program from Serum, which is quite similar to the logic of the multi-sig developed by OpenZeppelin. This allows multiple users to sign a transaction fully on-chain. However, if you can collect all the required signatures off-chain, the process can be easier. To illustrate it, we add the multi-sig functionality in the test code from the last post. All the test code can be found here.
3.1 Code Review
In the last introduced project, we replace the admin of the config account with a multisig account. In this case, to perform the instruction Lock and Unlock, the client will have to include enough signatures of the valid owners in the transaction.
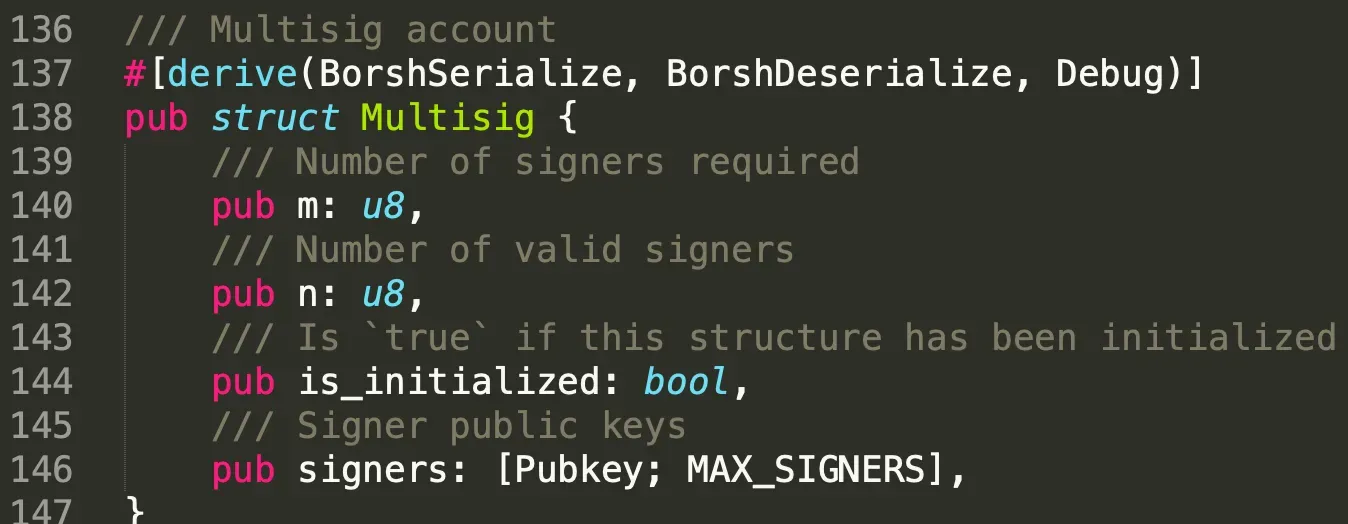
We add a struct named Multisig consisting of four attributes. They are the number of signatures required to execute the instruction, the total number of valid signers, the status of the account (whether it's initialized or not), and the array of valid signers' public keys.
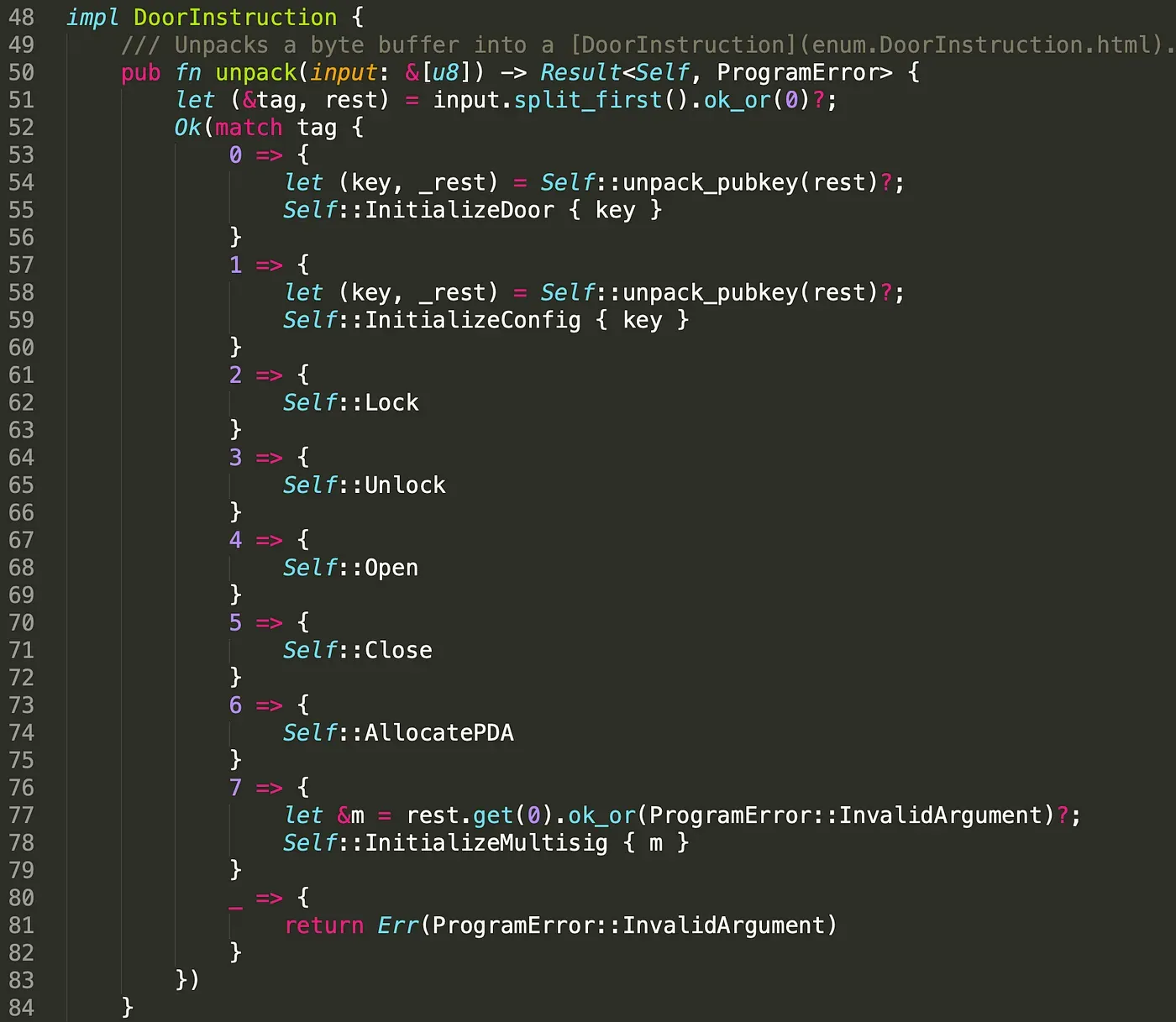
Correspondingly, we add the instruction InitializeMultisig in instruction.rs as well. Note that it receives the argument m (u8) from the client side. This value will be feed into the function InitializeMultisig().
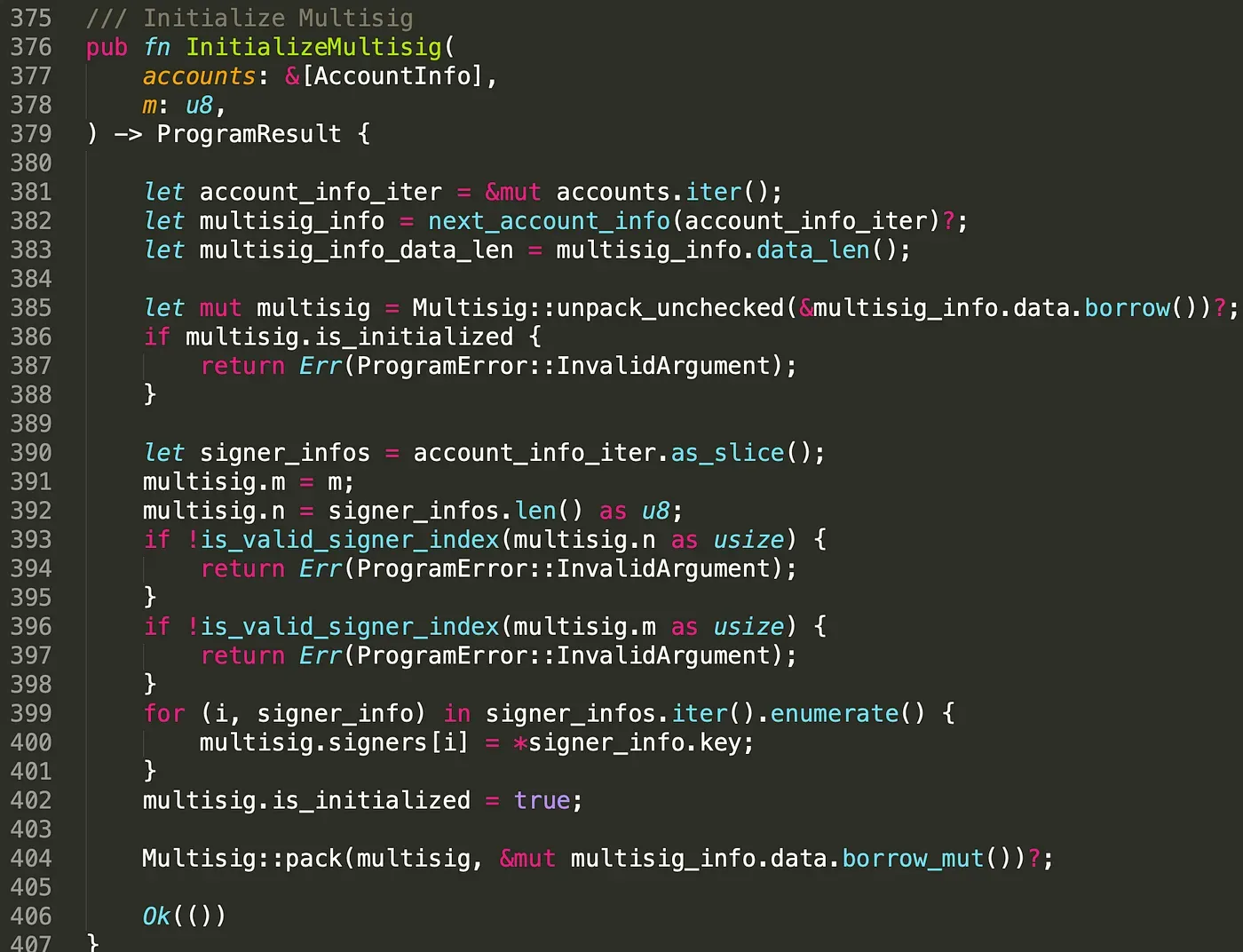
Function InitializeMultisig() receives the created accounts and the value m. To prevent the account from being re-initialized by malicious users, we validate whether the account has already been initialized (line 385-388). After that, we init the multi-sig account by assigning the value m, n and the public key of the signers.

In function Lock(), we check whether the admin account of the config account is a multi-sig one. If so, it will validate and count the signatures passed in (line 151 to 158). Once the number of valid signatures reaches or exceeds the required amount, doors will be locked (line 163 to 168). The implementation of the multi-sig in the function Unlock() is similar to Lock() function.
We deployed the program on testnet and it can be find in the following link.
https://explorer.solana.com/address/4g5ZA47pDQ1Bv93aNYdSKAXB6DvPAnnbi9cNEx7722SK?cluster=testnet
3.2 Send Transaction
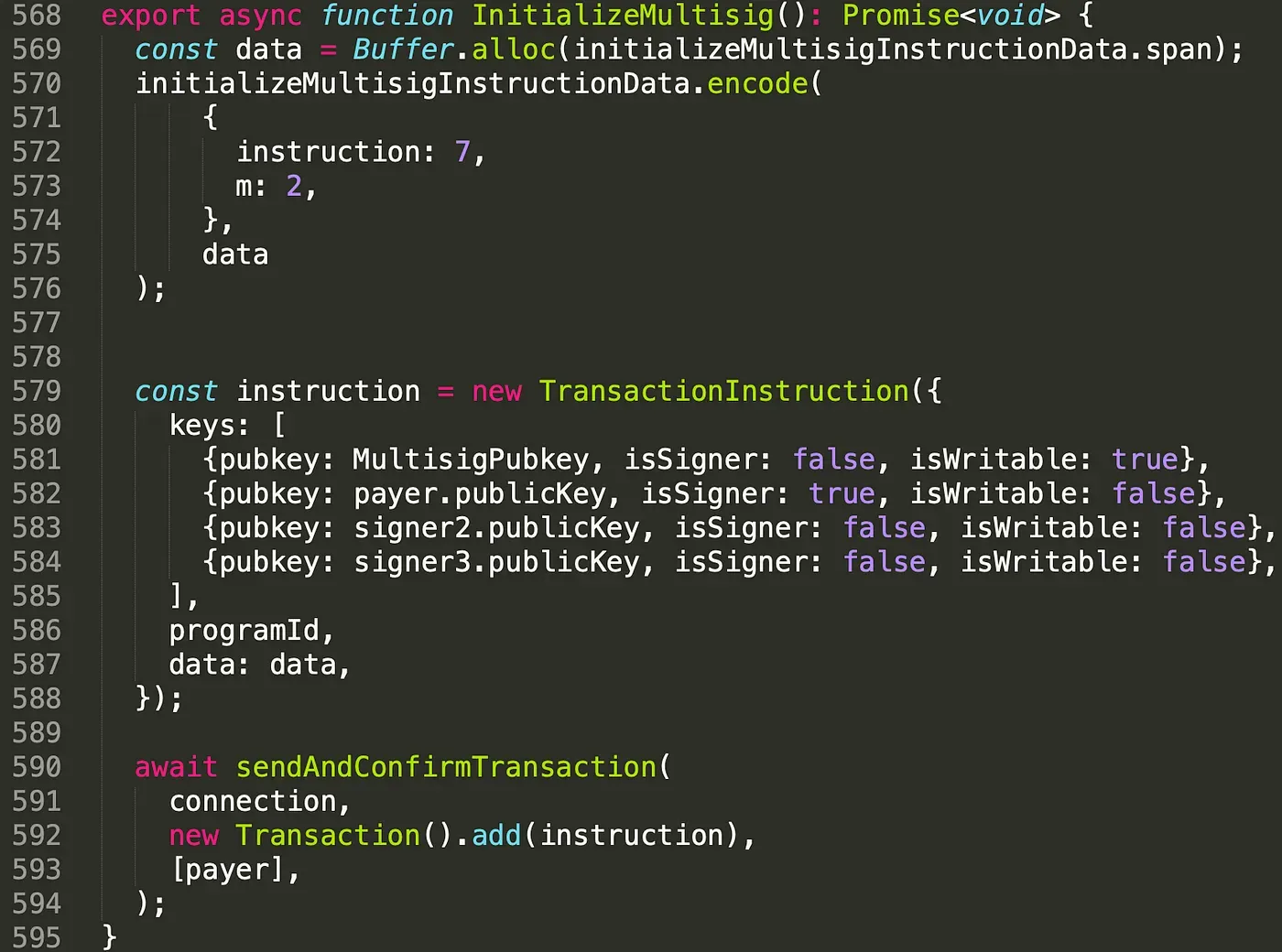
In function InitializeMultisig(), the keys includes four accounts. They are the multisig account and three valid signer's accounts. Note that one of the signers is also the fee payer of the transaction. We set the value of m to 2, which means two of the three signers' signatures is required to execute privilege functions.
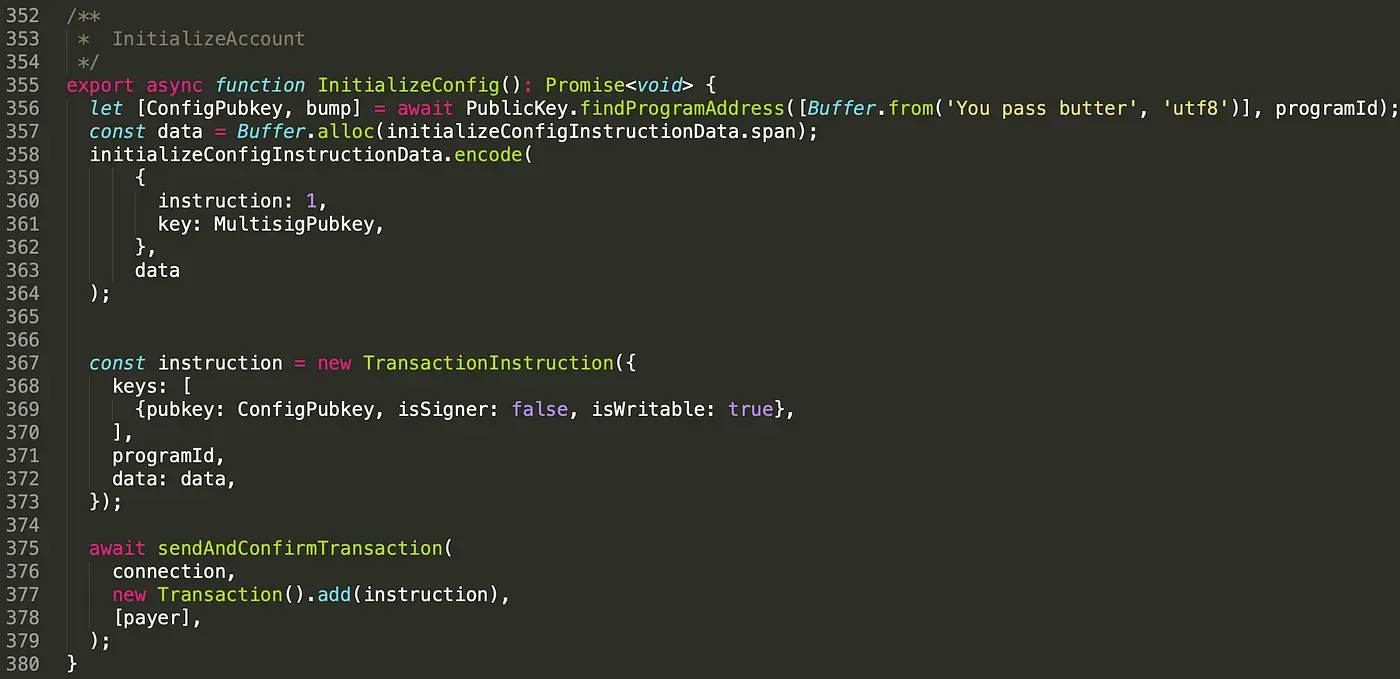
We also set the admin of the config account as the multisig account by passing the public key of the multisig account in the instruction data.
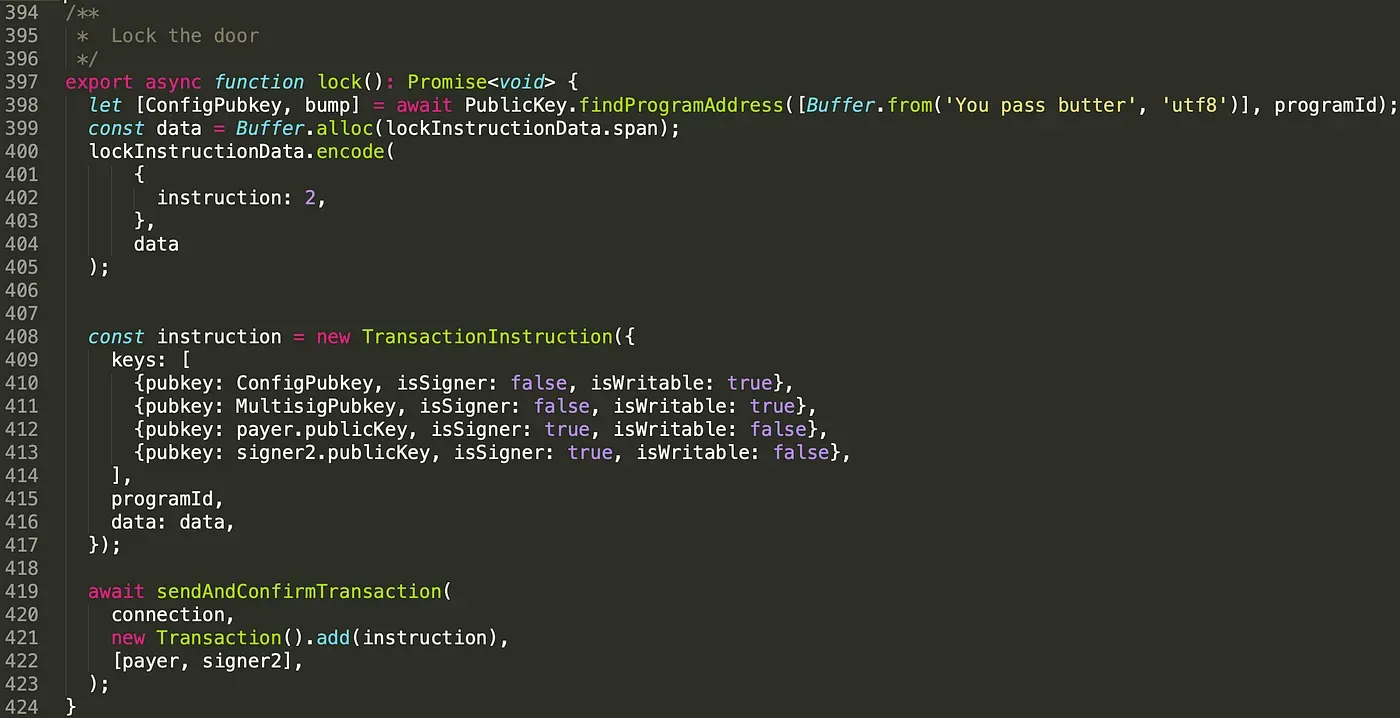
In function lock(), in addition to the config account (line 410), we pass in the multisig account (line 411), and two (at least) valid signers' accounts (line 412 - line 413). We set the attribute isSigner to be true for the signers. Again, the logic of the function unlock() is similar to it.
All the test transactions are listed below. The whole process is AllocatePDA()-> InitializeMultisig() -> InitializeDoor()-> InitializeConfig()-> Unlock() -> Open() -> Close()-> Lock().
https://explorer.solana.com/tx/2inXLHv34NzkmwmvQ7iimdNbEX2Hj8qWS3MVteAPtwhCAPy1yxXXdvfzMmUL7tESsd4wat4LMcPNiEQav18kQTrZ?cluster=testnet
https://explorer.solana.com/tx/4GErNusHLXpUHBsAJ55c7v1Ur1jfv5hAR88CK8nabLnzc92b1UhDnNRryKVjKmcnJDXppmyk6m5RUdpR2w7MEbrU?cluster=testnet
https://explorer.solana.com/tx/2S8h66oWfh7cn4fwFCVPtgGw1o3NgzyWwU1GyRpDjH4PEBfe8LDMZGAEBYLRJpzL3anH9ENShntjg3q5K8gcZSrN?cluster=testnet
https://explorer.solana.com/tx/nVKxPYegbpH324y57uHDZiajpNA5u4bSSJ2gHFHHRx4GJBy1DcpxnccKh1Ltkv9dah1qJNi9jWuBnXbyHWXCJyw?cluster=testnet
https://explorer.solana.com/tx/3KK5CU88oV59VfdTrNpT4LsiUsetuGdc6qW3sNyyGEWVYtKJfD6XA2Nfknrriwuka9wknHpZs3WZ1WkeduDA1pZX?cluster=testnet
https://explorer.solana.com/tx/3rFo37CrLSsMehLk4kwmMSDnbRfLfoPCWZzRDXhwwLg1uq32gu4ddxkYYB3pJX1yiMN8MofnV1Y9CSaf8bQaNJ9Y?cluster=testnet
https://explorer.solana.com/tx/5yFq4dZAMpccn96jKNkYFVcmhmtrwZYSFEQ6pkNgSMd7e1Vy1ztAM3RdFUZjEtThjFssz1TFytowePPyY59we9rX?cluster=testnet
https://explorer.solana.com/tx/3Ut4DqjCQi1MoCsjRx24DxykyDMsmyRsjJSXS7D4FBeZQwrx4UzxWt2gDe6YRiwUHzFkH3eWkFHub6FNSp2Us4Q7?cluster=testnet
3.3 Test Transaction
To test if the multi-sig really works, we modify the script of the client.
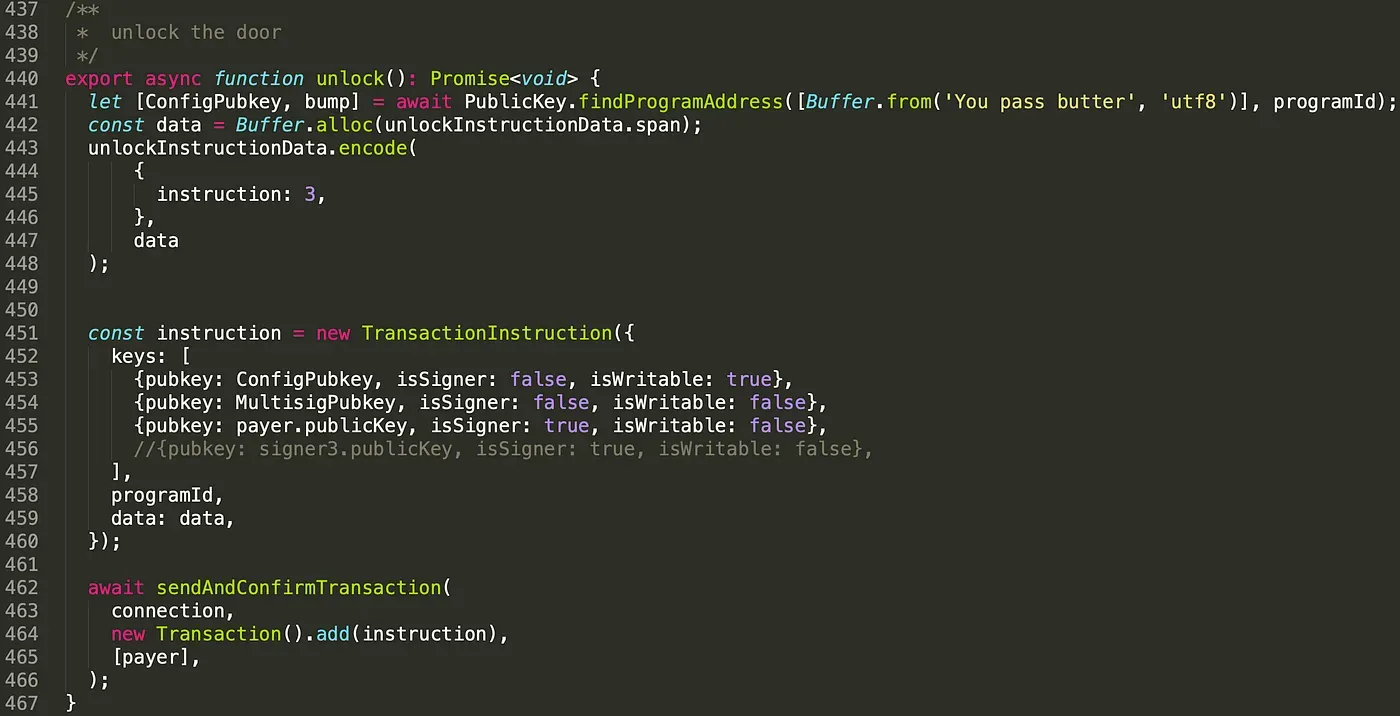
As shown above, we only pass in one signer account, and provide only one valid signature.
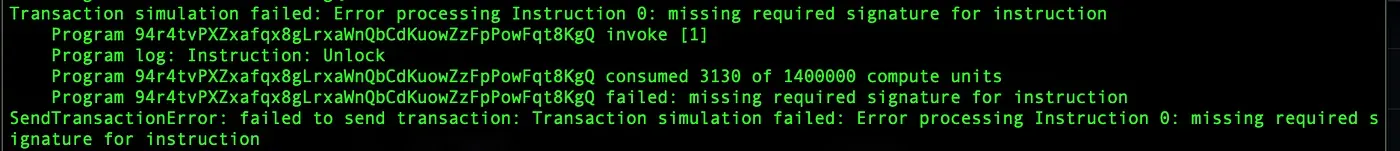
We noticed that the door cannot be unlocked due to insufficient signatures.
4. Summary
In this article, we introduce the simple implementation of the multi-sig in Solana. It’s for the scenario that you are able to collect the signatures from multiple users off-chain. The scenario that the transactions are required to be signed fully on-chain will be introduced later. Keep following, and we will share more in the upcoming posts.
Read other articles in this series:
- Secure the Solana Ecosystem (1) — Hello Solana
- Secure the Solana Ecosystem (2) — Calling Between Programs
- Secure the Solana Ecosystem (3) — Program Upgrade
- Secure the Solana Ecosystem (4) — Account Validation
- Secure the Solana Ecosystem (6) — Multi-Sig2
- Secure the Solana Ecosystem (7) — Type Confusion
About BlockSec
BlockSec is a pioneering blockchain security company established in 2021 by a group of globally distinguished security experts. The company is committed to enhancing security and usability for the emerging Web3 world in order to facilitate its mass adoption. To this end, BlockSec provides smart contract and EVM chain security auditing services, the Phalcon platform for security development and blocking threats proactively, the MetaSleuth platform for fund tracking and investigation, and MetaSuites extension for web3 builders surfing efficiently in the crypto world.
To date, the company has served over 300 esteemed clients such as MetaMask, Uniswap Foundation, Compound, Forta, and PancakeSwap, and received tens of millions of US dollars in two rounds of financing from preeminent investors, including Matrix Partners, Vitalbridge Capital, and Fenbushi Capital.
Official website: https://blocksec.com/
Official Twitter account: https://twitter.com/BlockSecTeam




