On November 19, 2025, the U.S. Treasury's OFAC sanctioned Ryan James Wedding. He is a former Canadian Olympic snowboarder. His key associates and businesses were also sanctioned. This action froze all their assets in the U.S. and banned Americans from doing any business with them.
Soon after, the U.S. State Department raised the reward for his capture to $15 million. The Mexican Embassy published guides on how to report tips. At the same time, the FBI, the Royal Canadian Mounted Police (RCMP), and Mexican police launched a joint global hunt. This operation against the "Olympian Drug Lord" reveals the dark link between cryptocurrency, drug trafficking, and serial murders.
Using on-chain tracking and special research, BlockSec has traced Wedding’s path from a sports star to a crime boss. Our analysis explains exactly how he used blockchain technology to build a "hidden" network for illegal money.
From Olympian to "Most Wanted"

Ryan James Wedding was born in 1976 in Thunder Bay, Ontario. He was once a promising star in winter sports. With his sharp skills and steady performance, he made the Canadian National Team. He represented his country at the 2002 Salt Lake City Winter Olympics in the men's parallel giant slalom. At that time, he was a face of Canadian winter sports. He loved the spotlight, but this attention also fueled a dangerous desire for quick success.
After the Olympics, Wedding’s life took a sharp turn. He turned down offers to stay on the team and left his skiing career behind. He joined the risky world of business instead. Later, he linked up with international drug traffickers. In 2008, he was arrested in California for smuggling cocaine. He was sentenced to four years in prison in 2010. However, prison did not reform him. Instead, it became a launching pad for his crime career. He met other criminals behind bars who helped him build a future drug network. After his release, he dropped his "Olympic athlete" mask completely. He took the nickname "El Jefe," which means "The Boss" in Spanish. He formed the Ryan Wedding Drug Trafficking Organization, which authorities now list as a major crime group.
Wedding’s group is known for being violent and highly organized. They work closely with Mexico’s Sinaloa Cartel, which the U.S. labeled a terrorist organization in 2024. Together, they move cocaine from production sites in Colombia through Mexico and finally into the U.S. and Canada. They traffic about 60 tons of drugs a year. This illegal business involves over $1 billion annually and is a major threat to Canadian national security.
Wedding uses deadly force to protect this network. In November 2023, he ordered an attack on a family in Ontario because of a stolen drug shipment. This brutal attack killed two parents and left one person badly hurt. Between April and May 2024, his gang committed two more murders to punish people who owed drug debts. In January 2025, he tried to cover his tracks by ordering the killing of a federal witness, Acevedo Garcia, in Colombia. The victim was shot five times in a restaurant and died instantly. Wedding’s lawyer even helped plan this crime and suggested killing the witness to make the charges go away.
In March 2025, Wedding was officially added to the FBI’s Ten Most Wanted Fugitives list. He replaced the fugitive Alexis Flores. Interpol also issued a Red Notice for his arrest. Today, he is hiding in Mexico. He is protected by a high-ranking cartel member known as "El General." Wedding runs his crime network remotely using encrypted messaging apps. He also uses Mexican companies like VRG Energéticos and Grupo RVG Combustibles as a legal front to hide his criminal activities.
The Money Laundering Process
The indictment states that the Wedding criminal group launders drug profits. They use U.S. dollars, Canadian dollars, and cryptocurrency for this. For their crypto assets, they use a specific method to hide the trail. They break large amounts of money into many small transfers. These funds move quickly through intermediate USDT wallets. Finally, all the money arrives in a central Tether wallet that Wedding controls directly.
Several key people handle these laundering tasks. The main operators are Sokolovski, Hossain, and Canastillo-Madrid. They work alongside other individuals, some known and some unknown to the grand jury. Together, they serve as members of the "Wedding Criminal Organization."

Laundering of Drug Proceeds
d. The Wedding Criminal Enterprise would conceal thesignificant proceeds of its cocaine sales in U.s. and Canadiandollars and cryptocurrencies.
e. With respect to the use of cryptocurrencies, to obsure the original source of the funds, members and associates ofthe wedding Criminal Enterprise would use a sophisticated Tether network to: (1) break large amounts of money into smaller transfers and (2) quickly use intermediary USDT wallets to move funds before ultimately reaching a hub Tether wallet controlled by defendant WEDDING.
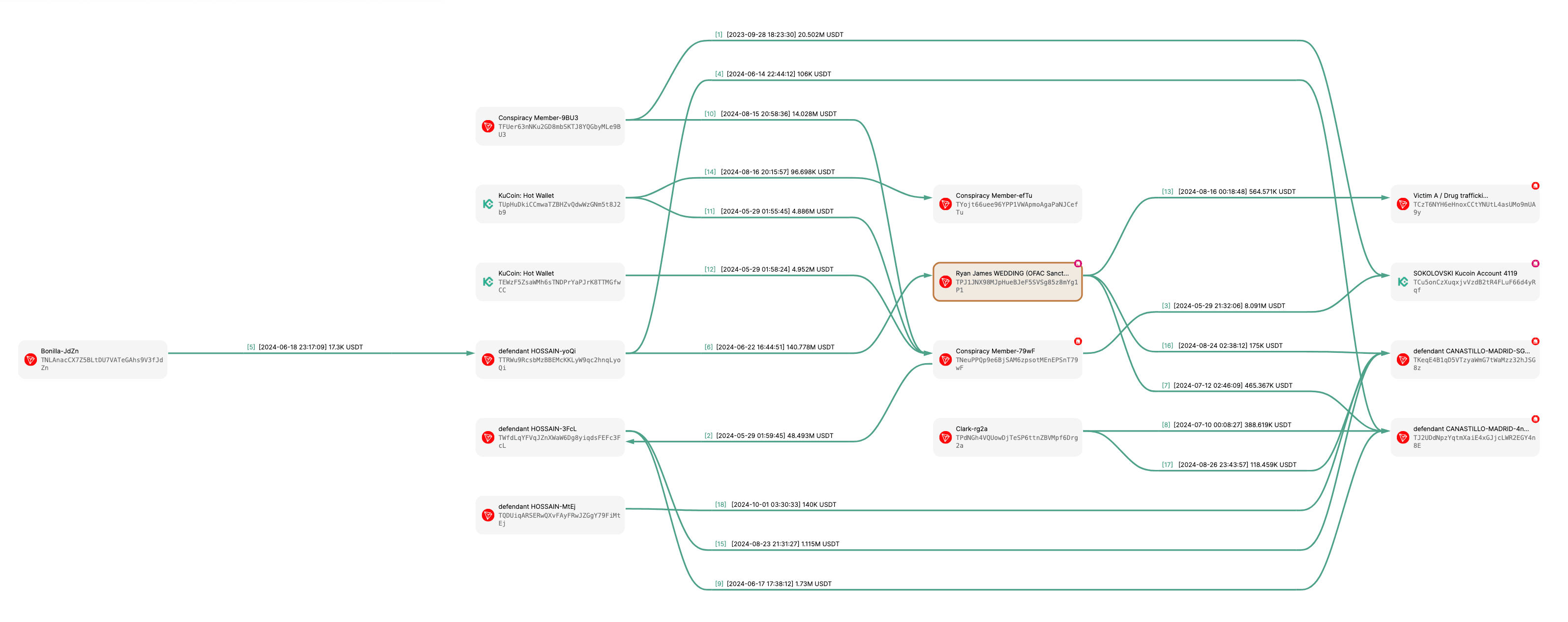
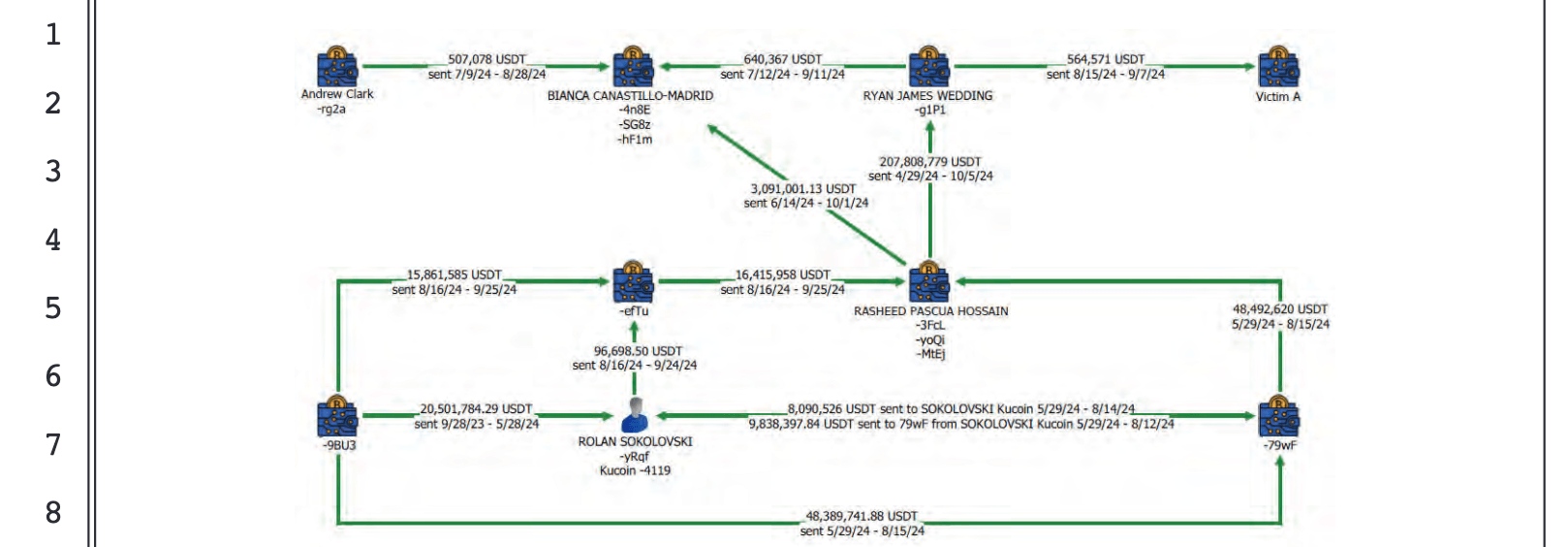
f. Defendants SOKOLOVSKI, HOSSAIN and CANASTILLO-MADRID, ad others known and unknown to the Grand Jury, would serve members and associates of the Wedding Criminal Enterprise, namely, defendant WEDDING and Clark, by concealing their drug trafficking proceeds and by using those proceeds to facilitate and further the objectives ofthe enterprise. A truncated flow chart illustrating this laundering system is depicted in the diagram below.
 The text below describes the specific details of the money laundering process.
The text below describes the specific details of the money laundering process.
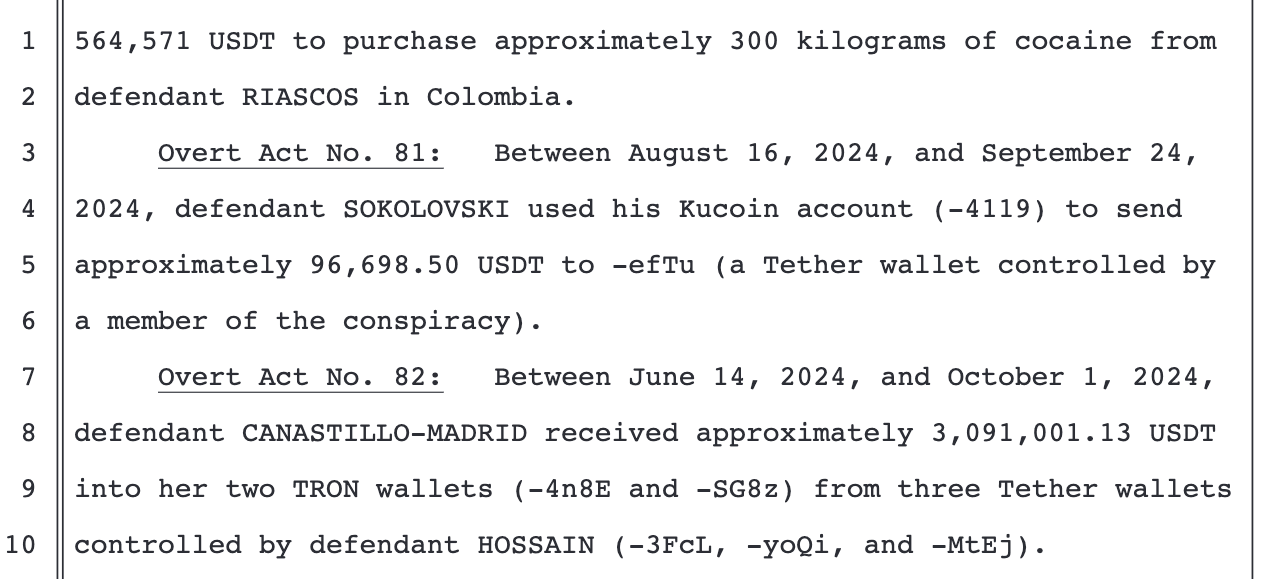
LAUNDERING OF DRUG PROCEEDS
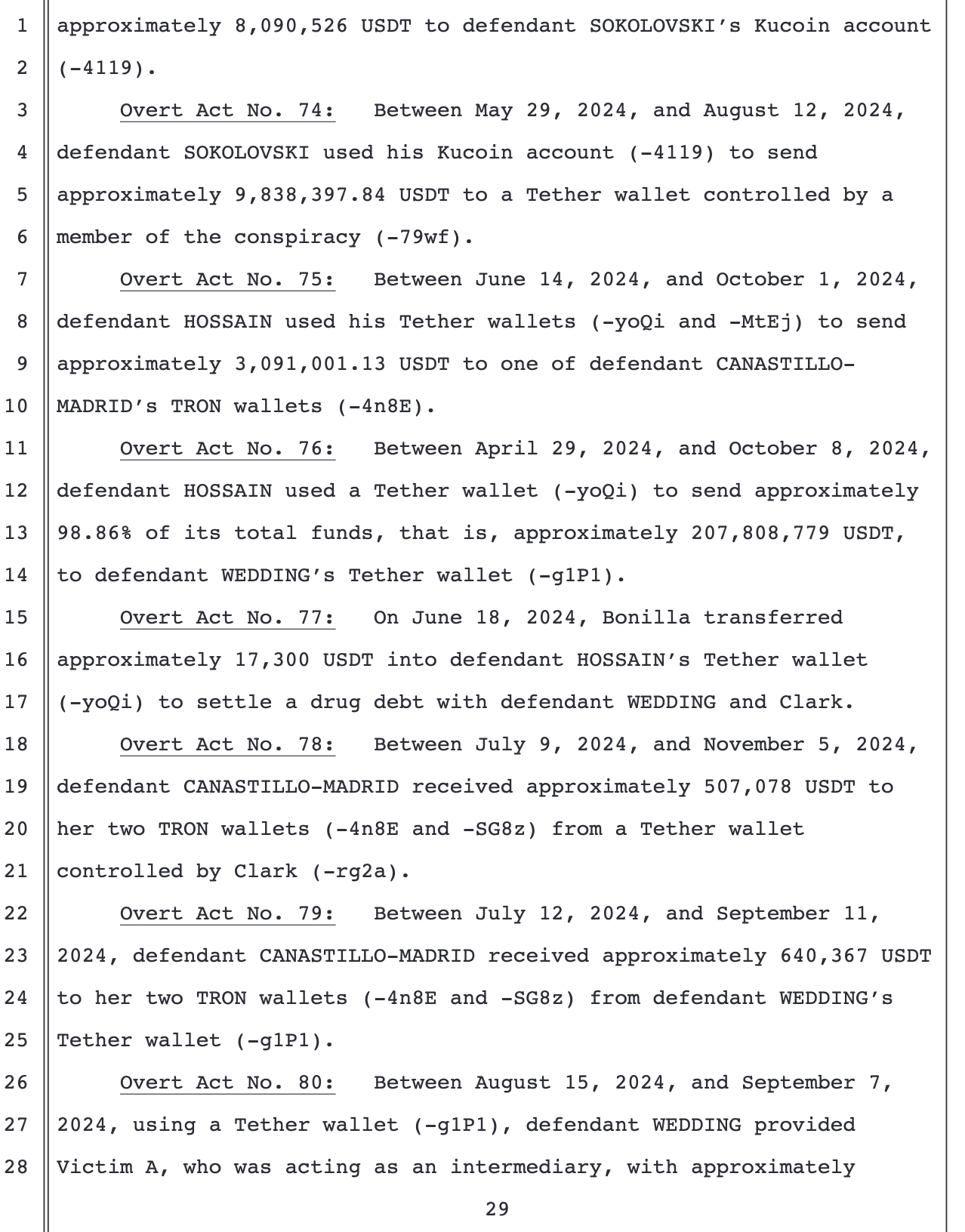
Overt Act No.71: Between September 28, 2023,and May 28, 2024, defendant SOKOLOVSKI received in his Kucoin account (-4119) approximately 20,501,784.29 USDT from a Tether wallet controlled by a member of the conspiracy (-9BU3).
Overt Act No.72: Between May29,2024,and August15, 2024, defendant HOSSAIN received in his Tether wallet (-3FcL) approximately 48,492,620 USDT from a Tether wallet controlled by a member of theconspiracy (-79wf).
Overt Act No.73: Between May 29, 2024, and August14, 2024, a member of the conspiracy used a Tether wallet (-79wf) to send approximately 8,090,526 USDT to defendant SOKOLOVSKI's Kucoin account (-4119).
Overt Act No. 74: Between May29, 2024, and August12, 2024 defendant SOKOLOVSKI used his Kucoin account (-4119) to send approximately 9,838,397.84 USDT to a Tether wallet controlled by a member of the conspiracy (-79wf).
Overt Act No.75: Between June 14, 2024, and October 1, 2024, defendant HOSSAIN used his Tether wallets (-yoQi and -MtEj) to send approximately 3,091,001.13 USDT to one of defendant CANASTILLO-MADRID's TRON wallets (-4n8E).
Overt Act No.76: Between April29, 2024, and October8, 2024, defendant HOSSAIN used a Tether wallet (-yoQi) to send approximately 98.86% of its total funds, that is, approximately 207,808,779 USDT, to defendant WEDDING's Tether wallet (-glPl).
Overt Act No.77: On June 18, 2024, Bonilla transferred approximately 17,300 USDT into defendant HOSSAIN's Tether wallet (-yoQi) to settle a drug debt with defendant WEDDING and Clark.
Overt Act No.78: Between July 9, 2024, and November5, 2024, defendant CANASTILLO-MADRID received approximately 507,078 USDT to her two TRON wallets (-4n8E and -SG8z) from a Tether wallet controlled by Clark (-rg2a).
Overt Act No79: Between July12, 2024, and September 11, 2024, defendant CANASTILLO-MADRID received approximately 640,367 USDT to her two TRON wallets (-4n8E and-SG8z) from defendant WEDDING'S Tether wallet (-g1P1).
Overt Act No.80: Between August 15, 2024, and September 7, 2024, using a Tether wallet (-glPl), defendant WEDDING provided Victim A, who was acting as an intermediary, with approximately 564,571 USDT to purchase approximately 300 kilograms of cocaine from defendant RIASCOS in Colombia.
Overt Act No.8l: Between August16, 2024, and September 24, 2024, defendant SOKOLOVSKI used his Kucoin account (-4119) to send approximately 96,698.50 UsDT to -efTu (a Tether wallet controlled by a member of the conspiracy).
Overt Act No.82: Between June 14, 2024, and October 1, 2024, defendant CANASTIILO-MADRID received approximately 3,091,001.13 USDT into her two TRON wallets (-4n8E and -SG8z) from three Tether wallets controlled by defendant HOSSAIN (-3FcL,-yoQi,and -MtEj).
We have visualized the money laundering process in the chart below.
We looked at the direct deposits and withdrawals for these addresses. This helped us understand where the funds came from and where they went. We focused on transfers over $100,000 to create the relationship map shown below.
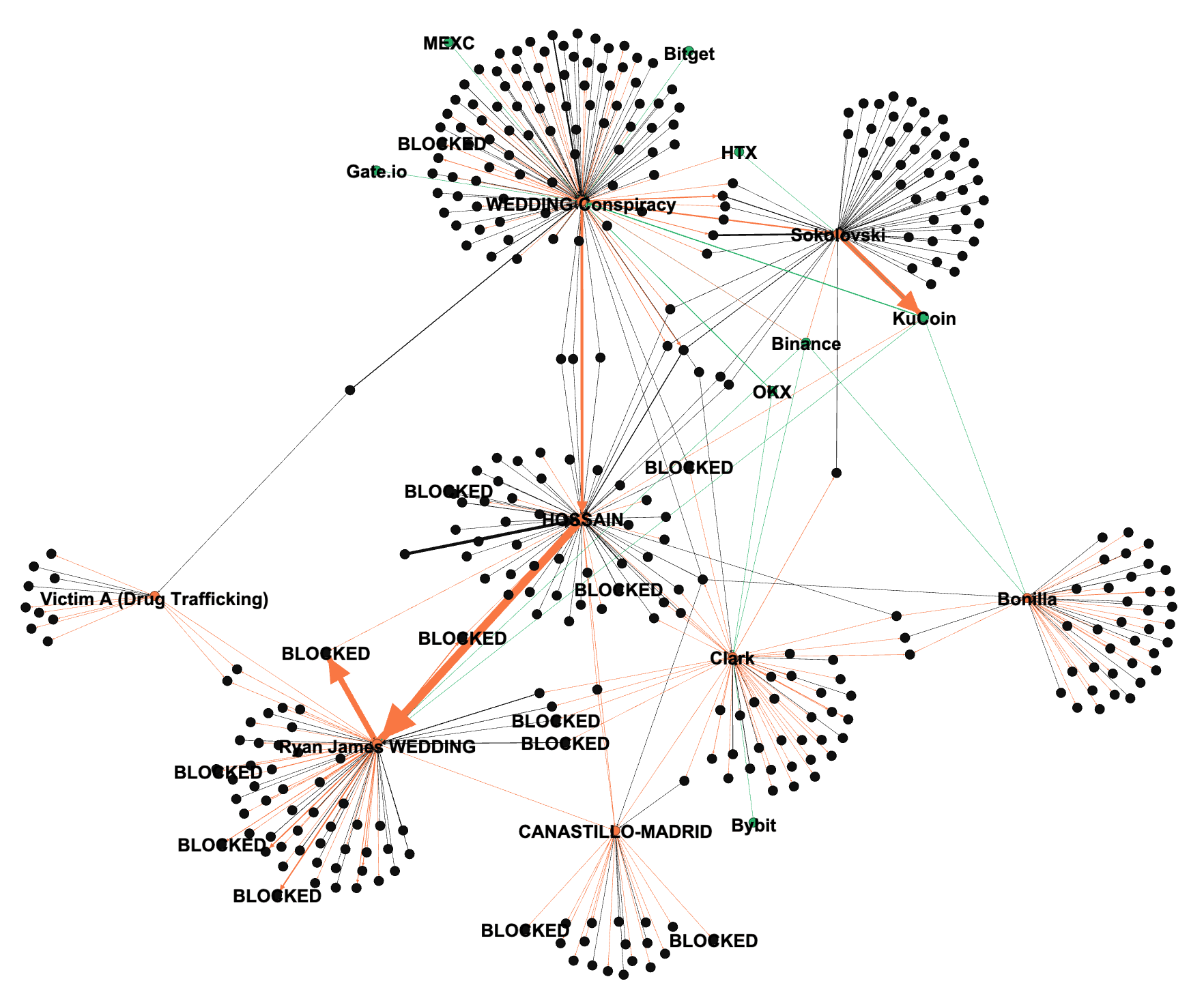
Key Funding Nodes and Roles
The relationship map shows that Hossain and Sokolovski act as two major collection centers for money. Most of the funds flowing into these centers come from a group of addresses labeled as the Wedding Conspiracy.
The Wedding Conspiracy group appears to manage the early stages of money laundering and drug deals. These addresses likely process the initial funds and then send the cleaned money down to the next nodes in the chain.
The money moves in two very different directions from these points:
-
Most of the money sent to Sokolovski eventually flows into KuCoin. This shows that his main role is to use a centralized exchange to finish the laundering process and turn the crypto into cash.
-
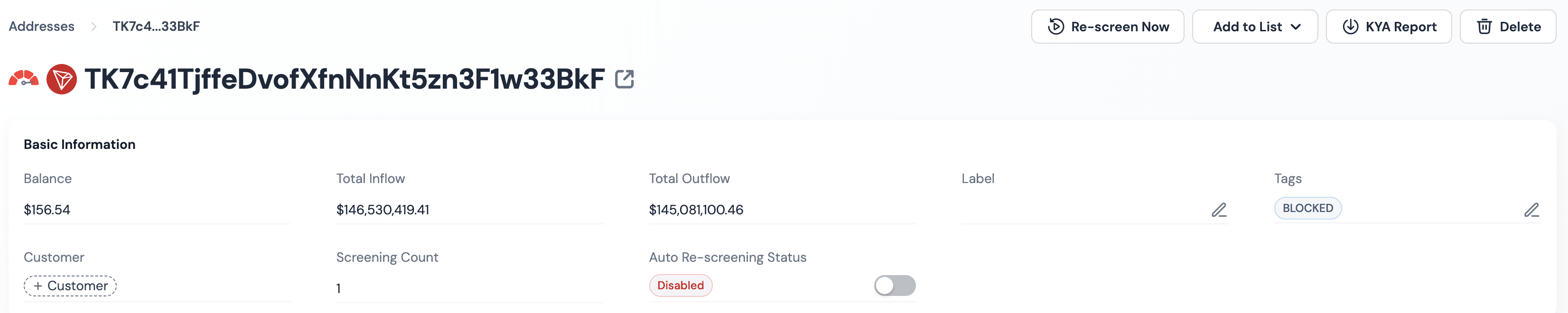
The money sent to Hossain mainly moves to addresses controlled by Ryan James Wedding. From there, the funds were sent to a specific address. This address, TK7c41TjffeDvofXfnNnKt5zn3F1w33BkF(SUSPECT-33BkF), has since been blocked by Tether.
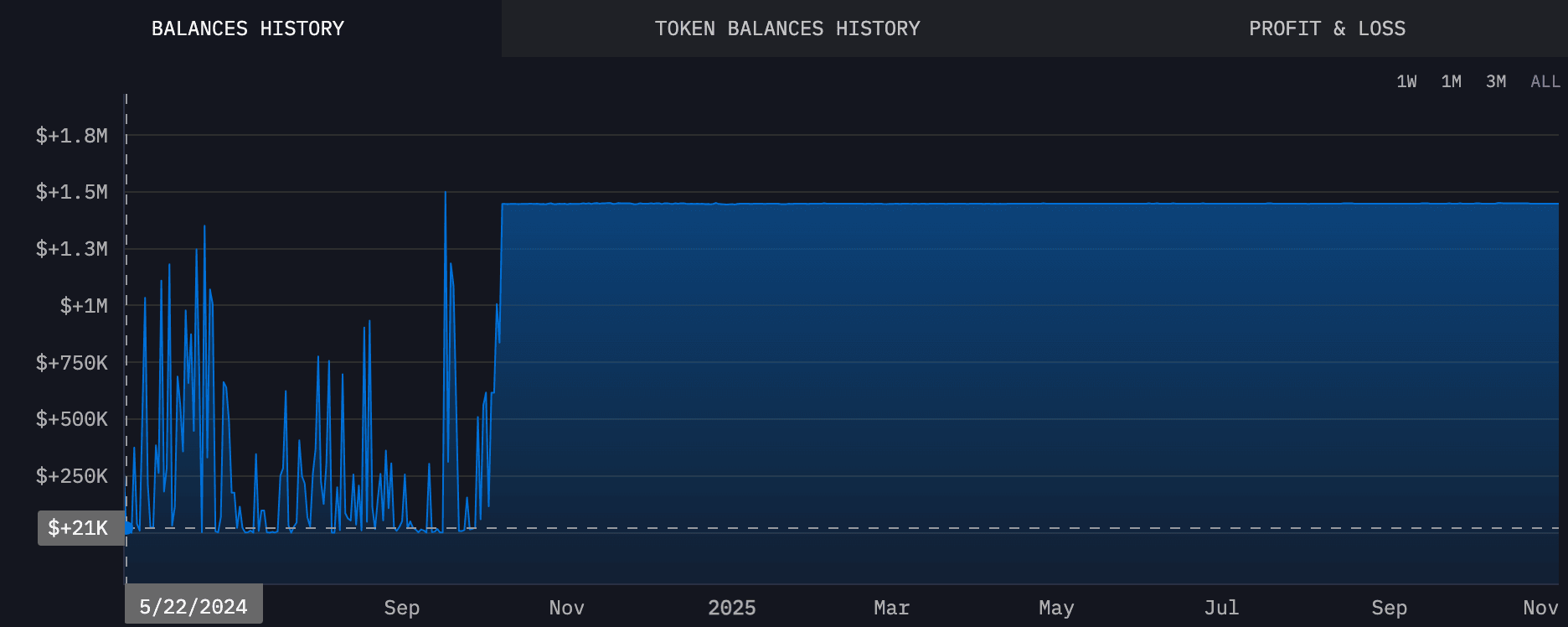
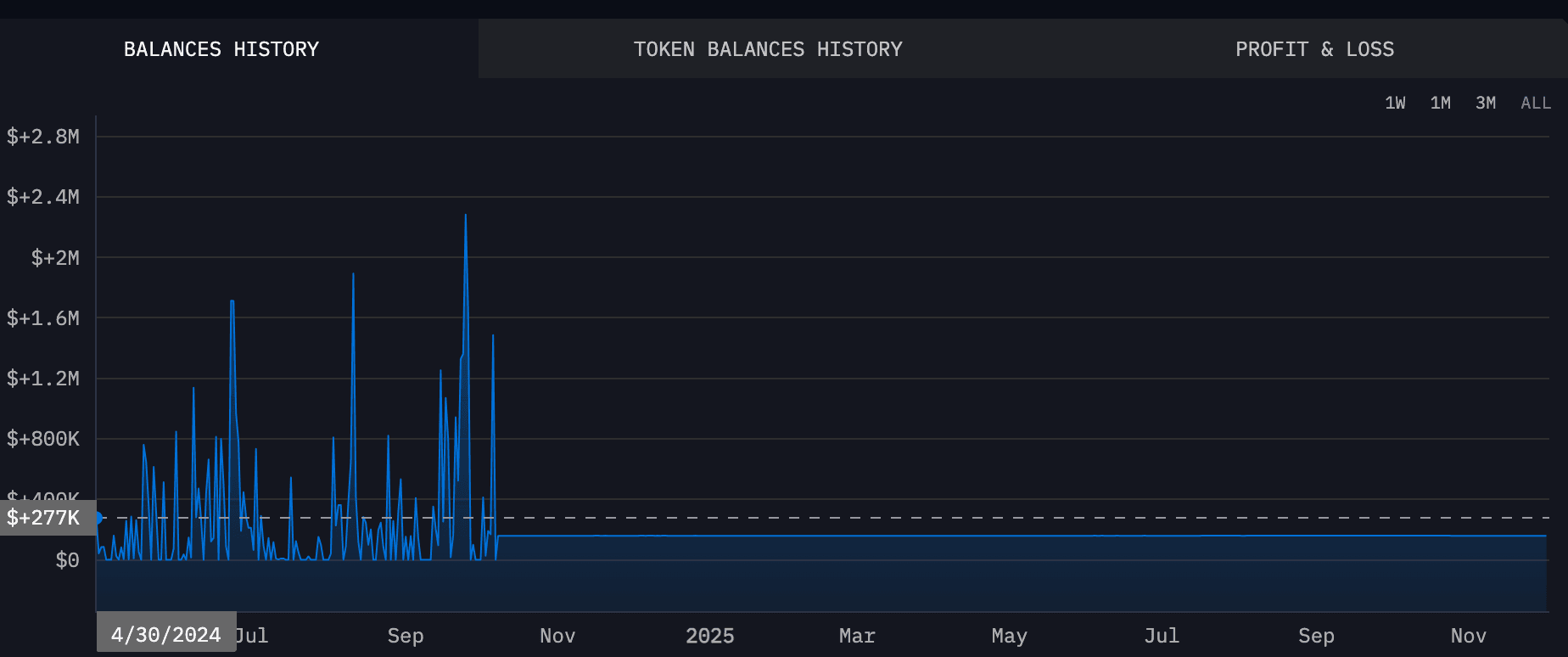
On-chain analysis shows that SUSPECT-33BkF and WEDDING-g1P1 were active during the same periods. Their activity schedules are almost identical. Based on this, it is reasonable to believe that Wedding used SUSPECT-33BkF as a backup or extension address to continue his money laundering.
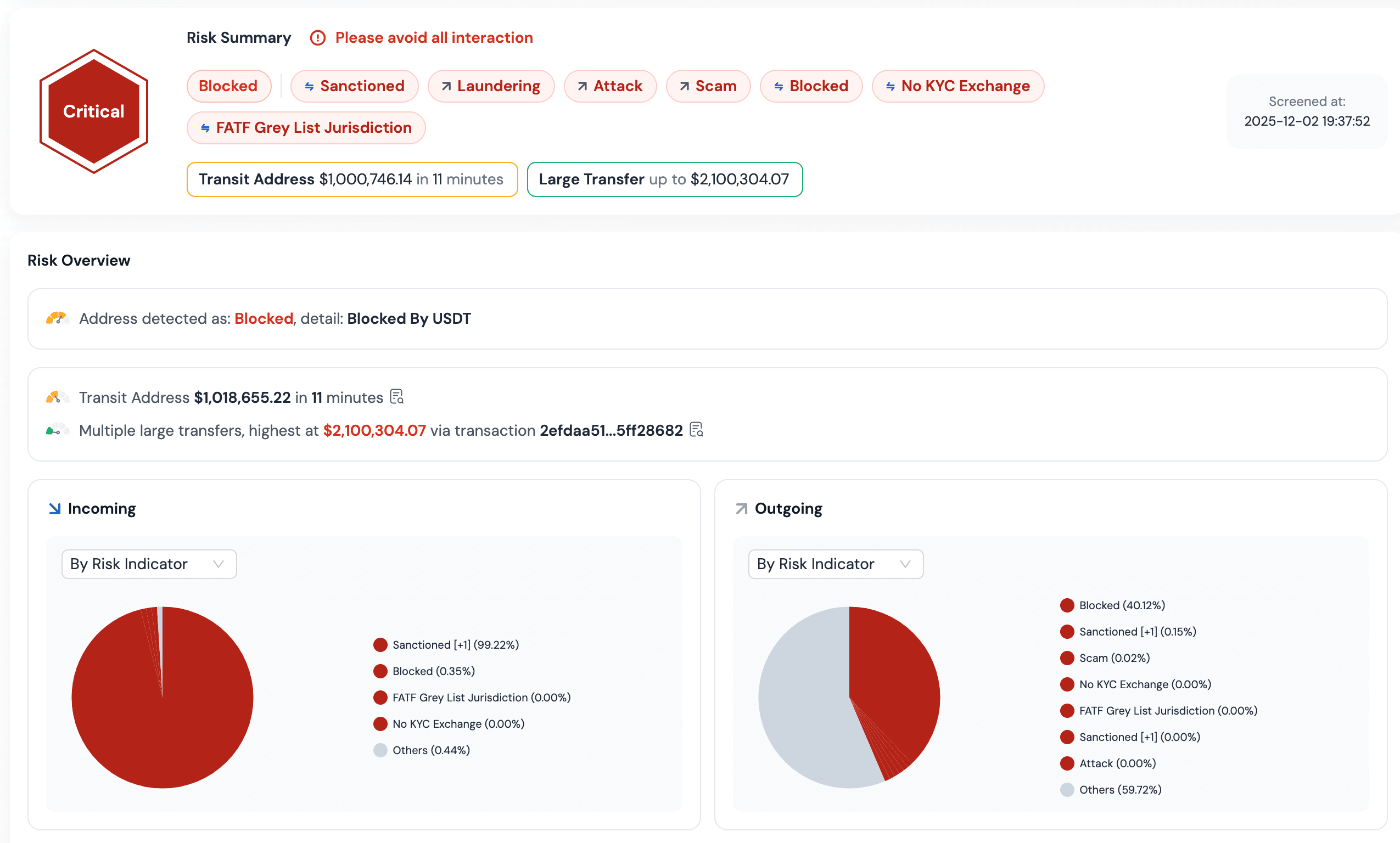
Further analysis of SUSPECT-33BkF using the BlockSec Compliance platform reveals more details:
-
About 99.22% of the money coming in came from sanctioned or flagged addresses. These are all linked to Wedding in this case.
-
Nearly 40% of the money going out was sent to addresses that are currently blocked by Tether.
Both the source and the destination of the funds are heavily tied to high-risk groups. This confirms that this address plays a key role in the money laundering chain of the Wedding criminal group.
Conclusion: Defending Against Crime in the Crypto Era
The Wedding case is not an isolated event. BlockSec research shows that international crimes involving privacy coins rose by 187% in 2024. Criminal groups are becoming more professional and global in how they use crypto. This case shows gaps in regulation. It also offers a guide for law enforcement and security firms.
For everyday users, it is important to avoid the trap of thinking that "anonymous" means "safe." This case proves that experts can still trace transactions. If a user interacts with a criminal address by mistake, they risk having their assets frozen. It is best to use regulated exchanges and avoid platforms that do not require ID checks. Regularly checking your wallet for risks with security tools is also a smart move.
For law enforcement and the industry, coordinated action is essential. BlockSec’s work shows that blockchain technology is actually a powerful tool to fight crime. By grouping addresses and tracking cross-chain moves, we can pull back the mask on criminal activity. In the future, countries must share more data and force exchanges to monitor transactions in real time. This will help stop illegal funds at the source.
The fall of Ryan Wedding is a tragic story. He went from an Olympic star to a name on a sanctions list. His story reminds us that while technology is neutral, it must be used for good. BlockSec will continue to build better tracking models to protect users and support law enforcement. Our goal is a crypto world that is safe, legal, and trusted.
Currently, Ryan James Wedding is still hiding in Mexico. The U.S. State Department has raised the reward for his capture to $15 million. This includes $10 million from a drug reward program and $5 million from the FBI. The Mexican Embassy has even posted guides on how to report tips. Anyone with information on his location, phone numbers, or associates can claim the reward through these channels:
-
FBI: Visit the "Ten Most Wanted" page at www.fbi.gov/wanted/topten to submit a tip.
-
Fiscalía General de la República (FGR): Use the encrypted platform from Fiscalía General de la República (FGR).
-
Interpol: Contact a regional Interpol office to share details with the joint task force.
The FBI guarantees that all tips are private. You can claim the reward without ever revealing your identity.