Security at a Glance 👀
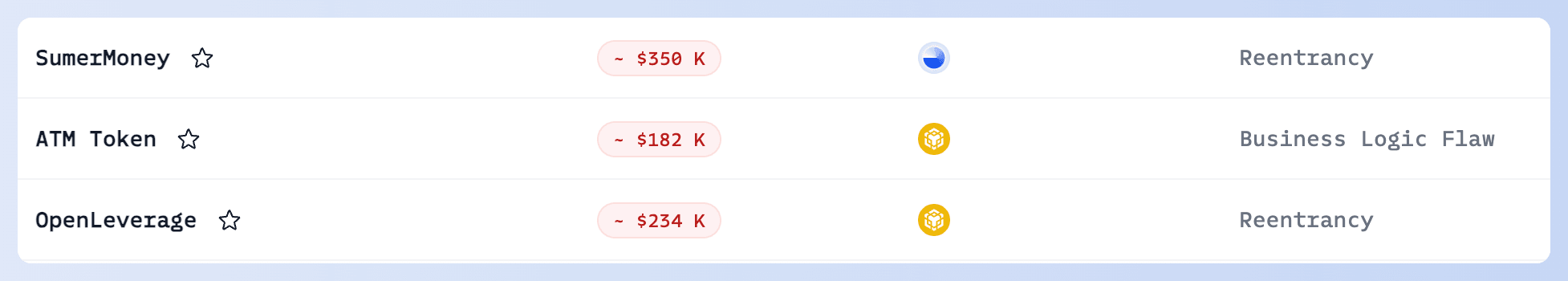
In April 2024, security incidents related to DeFi vulnerability exploits resulted in a total loss of ~$5 million. Most security incidents were caused by "Unverified User Input" and "Access Control Issues", with significant incidents involving Hedgey Finance and SaitaChain.
Advice to Developers: Carefully check the access control of critical functions and the content of user inputs, especially for protocols with flexible calldata. Click here to review past related incidents.
- Hedgey Finance Incident
On April 19, @hedgeyfinance on Ethereum was exploited, resulting in a loss of more than $1.8M. The root cause is Unverified User Input. It's important to note that while the project team and a security company claimed losses of $40M, the actual profits for the attacker were limited due to the lack of liquidity in the token. Ultimately, the attacker may have only cashed out a few hundred dollars, so we do not trust these statistics. Click here to view the root cause.
- SaitaChain Incident
On April 24, SaitaChain’s Xbridge was attacked, losing about $1M due to an Access Control Issue. The attacker was able to transfer all tokens by listing a token for just 0.15 Ether. We detected the attack immediately and notified the project team.
- Unknown Contract (0x80a0)
On April 15, unknown contract (0x80a0) on BSC was attacked, resulting in a loss of ~$600 K. The root cause was Unverified User Input. Check the alert.
- Pike Finance Incident
On April 26, Pike Finance lost approximately $300K on Ethereum, Arbitrum, and Optimism chains. The root cause is Unverified User Input, led by a forged CCTP message to drain USDC. We detected the incident immediately, but as the contract was not open source, we had to wait for the project team to confirm and take action before disclosing an attack transaction.
- The United States' First Smart Contract Exploitation Case
In the United States' first case involving smart contract exploitation, the defendant was found guilty of misappropriating assets exceeding $12M and was sentenced to 3 years in prison with the confiscation of the proceeds.
The exploitation involved CremaFinance and NIRVANA FINANCE. More than $8.8M was misappropriated from CremaFinance alone. Following negotiations, CremaFinance agreed to pay $1.5M (45,455 SOL) as a white hat bounty. Here this the fund flow analysis of CremaFinance Incident that we conducted using MetaSleuth.
👉 To learn more about attack transactions, root causes, and PoCs for various security incidents, please visit our Security Incident List.
Blog Articles
This blog presents EigenLayer's basic idea and illustrates the new security threats in the restaking ecosystem.
In this blog, we will show how to use MetaSleuth to track the "smart" money on the meme $TIM token on Solana, which was criticized as the project insider who made millions of USD by buying $TIM tokens.
The blog exposes the "Inferno Drainer" phishing scam that causes substantial losses and advises users to transact cautiously to avoid such frauds.
In this blog, we will show a new type of Web3 phishing and provide suggestions for how to avoid being phished.
The blog provides an overview of drainer-related hacking incidents targeting Web3 users, highlighting the methods employed by hackers and aiming to enhance users' awareness and protection against these tactics.
Product Updates
- 🥳 Phalcon's Big Upgrade!
Protocols and LPs can now monitor key variables, including nested structs, mappings, and arrays—especially those involving complex data structures. Users can select variables and configure monitoring expressions in 10 seconds, without coding! Read more
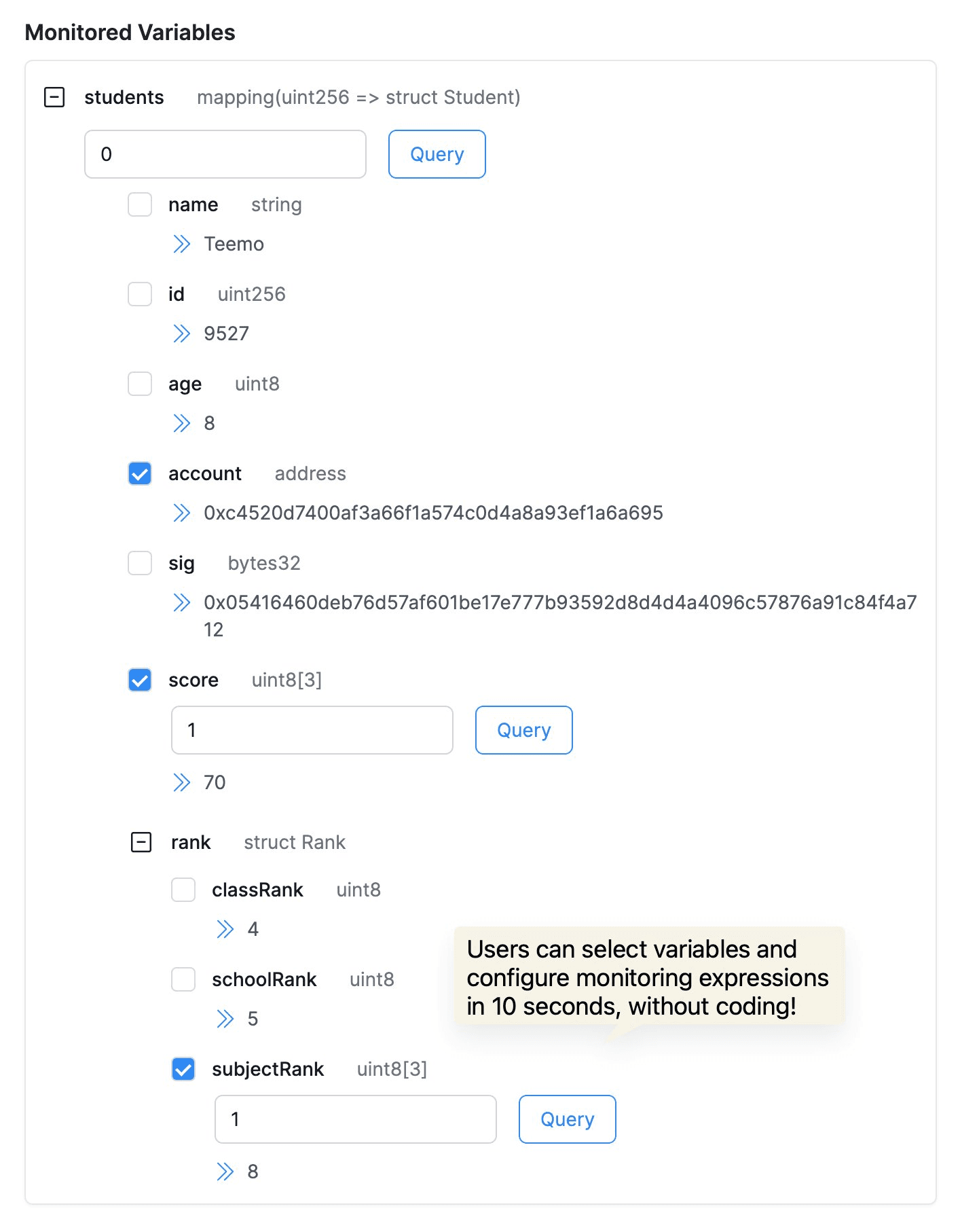
This upgrade empowers developers, security researchers, and LPs to better understand and monitor transactions and protocol statuses, quickly identifying security threats or configuration errors to maintain protocol stability and secure funds.
- 🥳 We have improved the UI of Phalcon Explorer!
It now supports full-screen mode (Shift+F shortcut), allowing developers and security researchers to use it more immersively and focus on analysis. Give it a try!
Full-screen support of BlockSec Phalcon Explorer @Phalcon_xyz https://t.co/w4YFhCxpjT pic.twitter.com/vshmXAW3m8
— BlockSec (@BlockSecTeam) April 12, 2024
Partnership
- Merlin ✖️ BlockSec
BlockSec Phalcon now fully supports Merlin, the top BTC L2! 🎉 After ETH, BSC, and Arbitrum, Merlin is the fourth chain supported by Phalcon!
🛡️ BlockSec Phalcon is actively monitoring the on-chain activities on Merlin Chain 24/7 and providing timely alerts to Merlin Chain. Starting now, protocol teams and investors on Merlin Chain can also subscribe to Phalcon to gain crypto hack monitoring and blocking capabilities.
🚀 Phalcon Explorer also supports Merlin! Explore transaction traces, balance changes, and fund flows easily. For some mainstream contracts without source codes on The Merlin Blockchain Explorer, it offers access to verified contracts.

- Forta ✖️ BlockSec
Honored to be part of the @FortaNetwork ecosystem! Let's work together to make Web3 safer! 🙌 https://t.co/e87inYgJKN
— BlockSec (@BlockSecTeam) April 25, 2024
About BlockSec
BlockSec is a pioneering blockchain security company established in 2021 by a group of globally distinguished security experts. The company is committed to enhancing security and usability for the emerging Web3 world in order to facilitate its mass adoption. To this end, BlockSec provides smart contract and EVM chain security auditing services, the Phalcon platform for security development and blocking threats proactively, the MetaSleuth platform for fund tracking and investigation, and MetaSuites extension for web3 builders surfing efficiently in the crypto world.
To date, the company has served over 300 esteemed clients such as MetaMask, Uniswap Foundation, Compound, Forta, and PancakeSwap, and received tens of millions of US dollars in two rounds of financing from preeminent investors, including Matrix Partners, Vitalbridge Capital, and Fenbushi Capital.
Official website: https://blocksec.com/
Official Twitter account: https://twitter.com/BlockSecTeam




