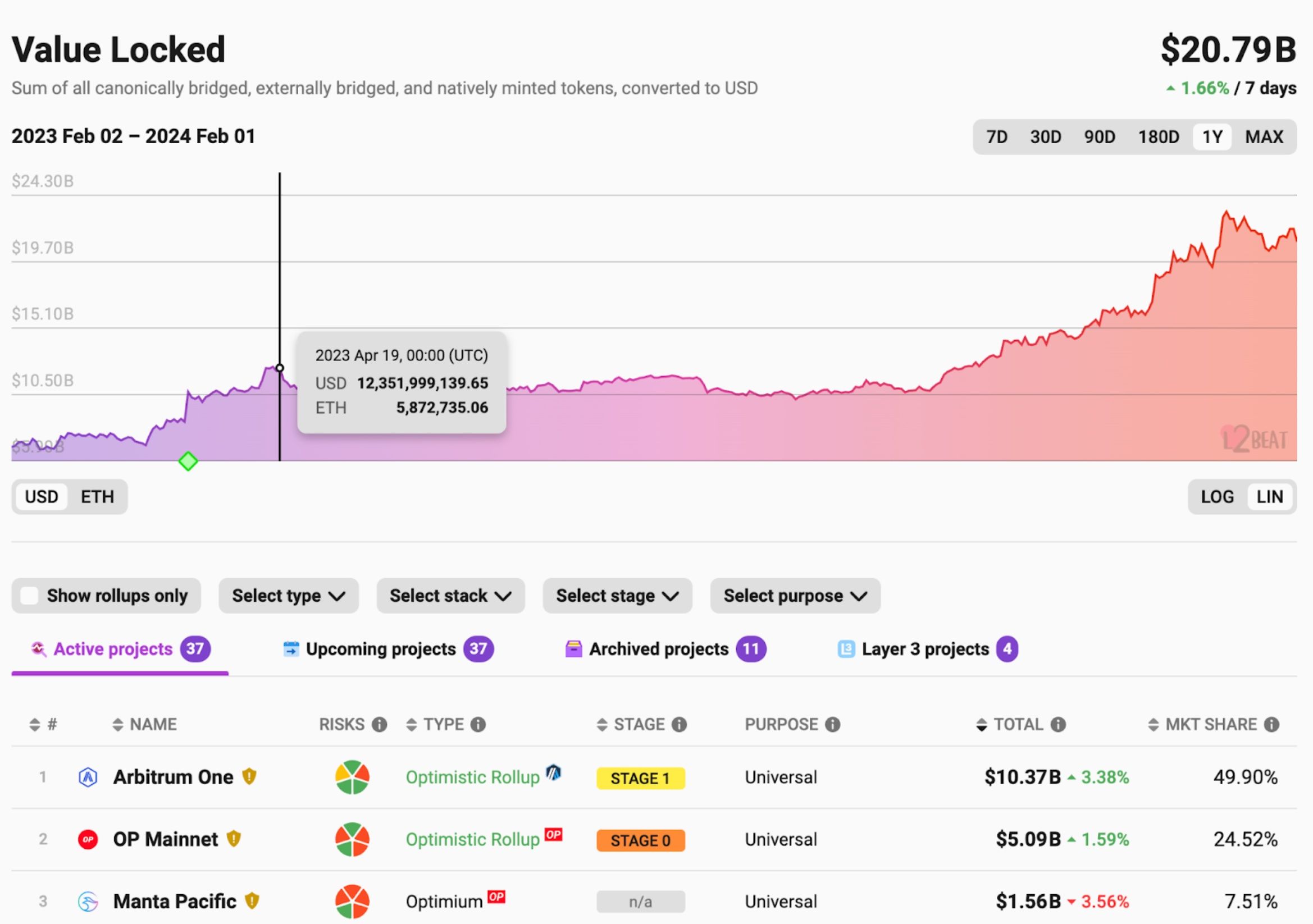
L2 solutions have been gaining significant popularity recently in the blockchain space to solve the scalability issue of blockchains. With L2 solutions, applications can even develop their own chains called application chains to handle high-frequency transactions. According to the data on L2beat, there are 37 active projects, and the TVL (on Feb 1, 2024) is $20.79 billion.
However, with the popularity of the L2 blockchains, we found some security challenges need to be addressed, including how to ensure the security of private keys, how to secure the cross-chain and top protocol transactions, how to provide security development infrastructure for developers, etc.
In this blog, we will first systematically review these challenges and then propose our solutions.
Why L2
Why do we need L2 blockchains? We think there are different reasons from technical and financial perspectives.
Technical Perspective
The motivation behind L2 blockchains is to solve the scalability issue of L1 blockchains. The basic idea is that instead of submitting all transactions into L1 chains (which are already congested due to block size and consensus mechanism), transactions can be executed on a separate chain (called L2 chain) and only submit the summary of state changes into the L1 chain, as shown in the following picture from Chainlink.
 Image Source: ChainLink
Image Source: ChainLink
Financial Perspective
Another motivation is from the financial perspective, i.e., constructing an ecosystem on a new application chain. This can offer several benefits for the applications.
-
First, the application chain can have faster transaction processing and less gas consumption to save user costs and improve usability. This can lead to increased economic growth for the application chain.
-
Second, the chain can provide customized incentive mechanisms for the developers and business partners. For instance, they can share the gas fee with them and even have new markets like transaction auctions on that.
-
Third, by constructing an ecosystem, the chain can invite more business partners to join this system and meet the requirements that cannot be satisfied (or are too expensive) on the L1 blockchain.
Of course, what we have discussed so far is about the L2 chains based on Ethereum. We also see some L2 solutions called BTC L2. We will not illustrate them in detail, but we see that some of them are taking the liquidity provided by the BTC network (including BTC and other tokens like NFT and inscriptions) and bridging to an EVM-compatible chain.
Security Requirements & Challenges
We think there are a couple of security challenges that need to be considered by the L2 blockchain operators. This is even crucial since the L2 blockchain emerged too fast, so the underlying infrastructure, the operation experience, and the security knowledge of the L2 blockchain’s operations are lagged behind. This may cause damage to the whole ecosystem for each L2 chain.
-
First, the L2 chain itself should have a good perception of the security of the top protocols on the chain, especially for the application chain where the main TVLs are from a few protocols. It requires the capability to detect suspicious and malicious smart contracts and transactions in real time and take action immediately. A procedure for responding to security incidents should be established to deal with attacks.
-
Second, an architecture to secure the private keys used by the L2 chains should be used. For instance, in the OP rollup stack, the sequencer is used to sign blocks on L2, and the batcher is used to publish transactions on L1. If these critical private keys are leaked, then the whole security of the L2 chains will be compromised.
-
Third, the security tools or frameworks should be developed for the chain. For instance, tools for analyzing suspicious transactions and performing security testing should be developed. Security researchers from the community can leverage these tools to analyze the transactions to understand their security impacts quickly.
-
Last but not least, the security of the underlying cloud infrastructure for the L2 chains should be considered. For instance, the L2 nodes can be DDoSed, and the access token of the cloud infrastructure could be leaked in different ways, e.g., social engineering attacks. Mitigations and security policies should be prepared in advance.
Our Solution
As a full-stack security provider, BlockSec can be a deep security partner and help secure the L2 blockchains through our services and tools.
-
High-quality security code auditing. BlockSec provides diligent code auditing services to DeFi protocols. By leveraging the static analysis tool, dynamic fuzzing, and differential testing framework backed by academic research, our code audits cover protocols and the underlying EVM execution engine. We have detected multiple vulnerabilities in the blockchain execution engine (EVM and RBPF), being rewarded more than 1M USD.
-
Attack transaction monitoring and blocking. With the battle-tested techniques, BlockSec Phalcon can help L2 monitor attack transactions, including the direct transactions to the L2 and the cross-chain transactions from L1. Besides, we can also help secure the bridged assets from other L1/L2 chains through token bridges, e.g., LayerZero or Celer. Also, a more proactive solution to block the attack transactions can be deeply integrated into the L2 chains (contact us for more information on this).
-
A hardware-based solution to secure the private keys. We provide services to generate and manage private keys and sign transactions inside secure hardware. It has all the hot wallet’s advantages and cold wallet’s security. It can sign the transactions securely, with the extensibility to support more algorithms if necessary. It’s more flexible, more efficient, and more practical than other solutions, such as MPC and HSM.
-
Security development tools and platforms. The Phalcon Explorer is a defacto analysis tool for the security community to analyze attack transactions to understand the root cause. It has been leveraged by the community to analyze hundreds of security incidents. Phalcon Fork is a platform that can be used to perform security testing on a Forked network with mirrored states. Please don't hesitate to contact us to support your L2 chains with our tools.
-
Security Incident Response. BlockSec is always the fastest (if not the first) security vendor to identify attack root causes and vulnerabilities in DeFi hacks. We can help protocols review the security patches (Telcoin), provide the white fund rescue [e.g., AnySwap, TransitSwap, Paraspace, Loot], track hacker's fund flow, and pinpoint the identity of the Hopeland attacker.
Summary
The propriety of the L2 blockchain creates opportunities but also faces serious security challenges. Our security solutions can help L2 blockchains to audit the code, detect and block hacks, secure the private keys, provide security development tools, and help resolve security incidents.
Action today to contact us ([email protected]) to secure your L2 chains and earn the trust of your users!




