PolyNetwork遭到黑客攻击,超过3亿美元被盗。攻击者在多个链上执行了攻击。在本篇博客中,我们将以以太坊上的攻击交易(0xd8c1f7424593ddba11a0e072b61082bf3d931583cb75f7843fc2a8685d20033a)来分析此次黑客攻击的可能原因。我们初步分析表明,一种可能的原因是用于签名跨链消息的私钥泄露,或者PolyNetwork的签名过程中存在一个被滥用来签名伪造消息的bug。
免责声明:本博客仅包含我们基于以太坊链上数据进行的初步分析结果。在获得Poly Network的进一步信息之前,我们无法验证我们的发现。
更新于 2021/08/12:进一步信息显示,攻击原因是 keeper 被攻击者修改(而非私钥泄露)。我们对 keeper 变更交易为何能够执行进行了更深入的分析。
交易和调用追踪
我们使用我们的交易分析系统来恢复追踪。
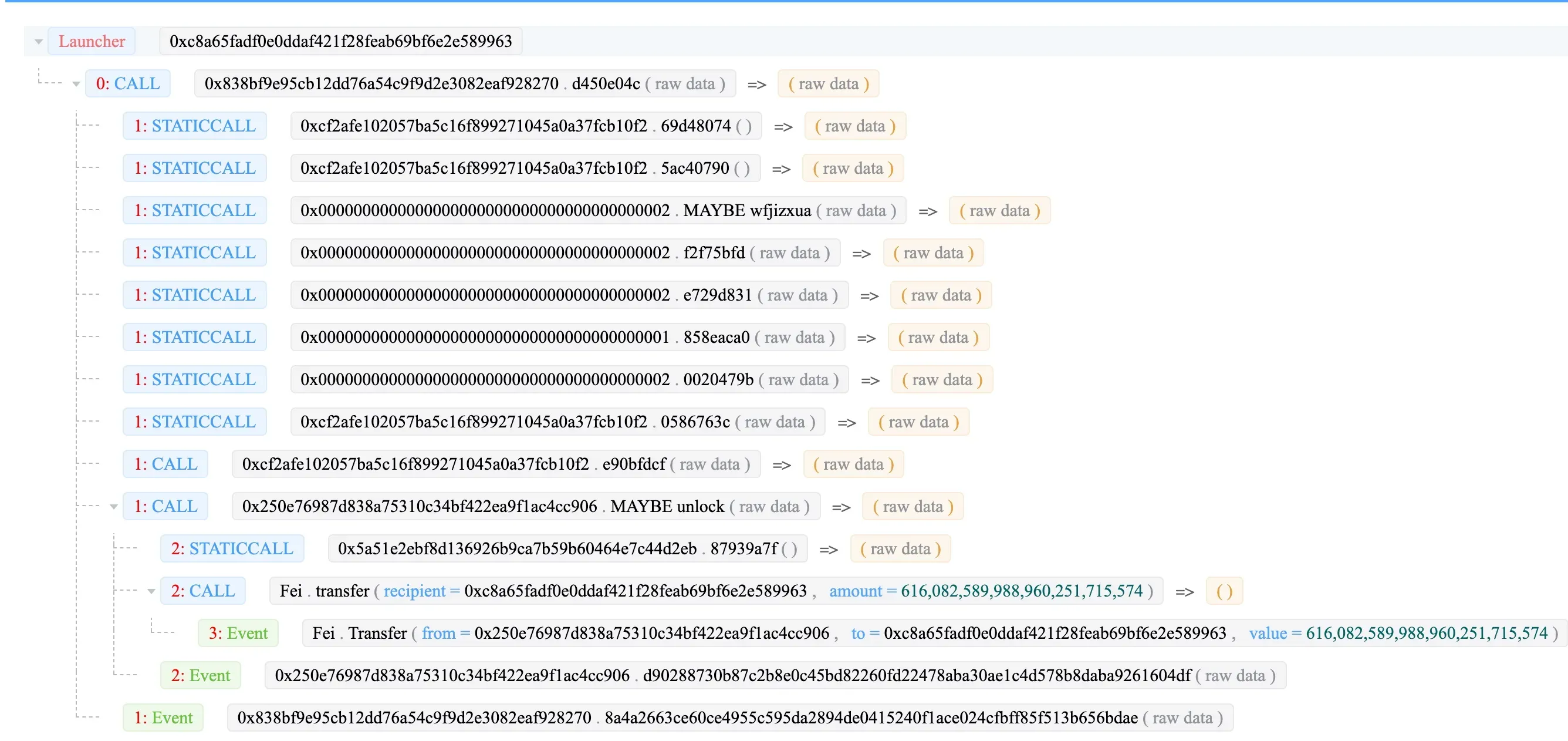
攻击者 -> EthCrossChainManager -> EthCrossChainData -> LockProxy -> managerProxyContractforLockProxy
- 0xc8a65fadf0e0ddaf421f28feab69bf6e2e589963:攻击者
- 0x838bf9e95cb12dd76a54c9f9d2e3082eaf928270:EthCrossChainManager
- 0xcf2afe102057ba5c16f899271045a0a37fcb10f2:EthCrossChainData
- 0x250e76987d838a75310c34bf422ea9f1ac4cc906:LockProxy
- 0x5a51e2ebf8d136926b9ca7b59b60464e7c44d2eb:LockProxy 的 managerProxyContract
函数签名:
- d450e04c (verifyHeaderAndExecuteTx)
- 69d48074 (getCurEpochConPubKeyBytes)
- 5ac40790 (getCurEpochStartHeight)
- 0586763c (checkIfFromChainTxExist)
- e90bfdcf (markFromChainTxExist(uint64,bytes32))
攻击主流程
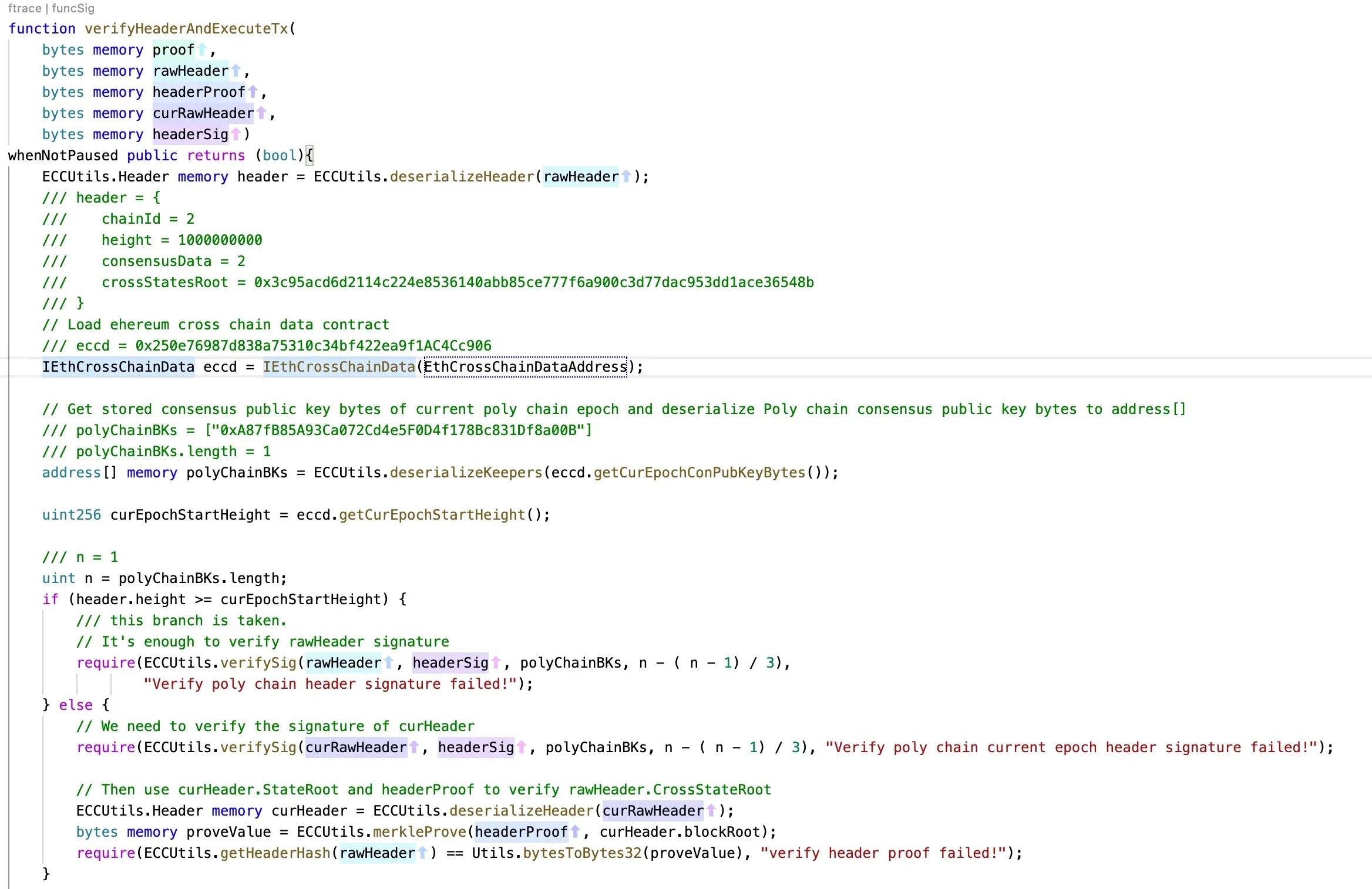
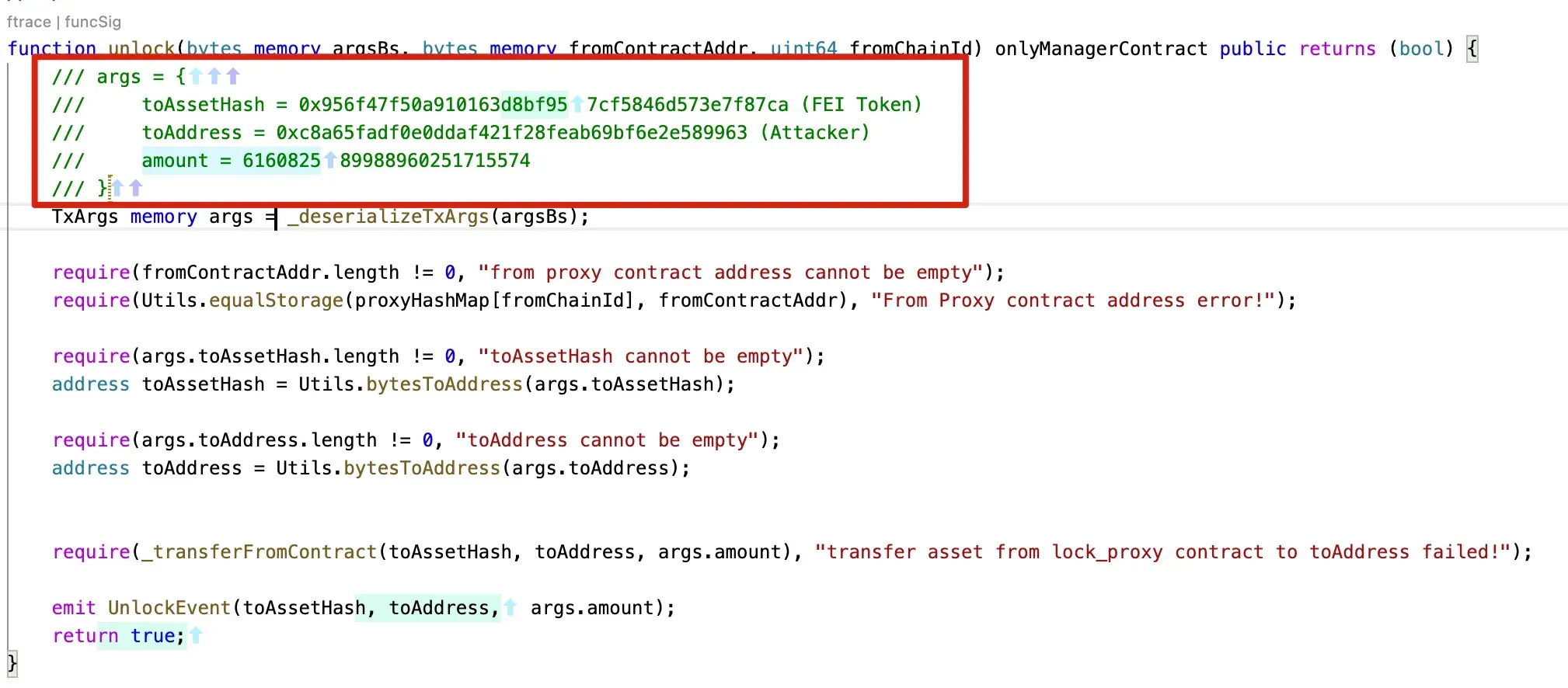
攻击的主流程是攻击者将签名后的数据传递给 verifyHeaderAndExecuteTx() 函数。该函数将解码数据并验证用于签名数据的签名。如果此过程通过,则消息中指定的函数(以及合约地址)将被执行。在此次攻击中,调用了智能合约 0x250e76987d838a75310c34bf422ea9f1ac4cc906 的 unlock 函数,将 Fei 转账给攻击者。
总而言之,此次攻击是由于向 verifyHeaderAndExecuteTx 函数传递了有效参数。而这些参数能够通过签名验证过程。之后,消息中指定的交易将被执行(类似于软件安全中的任意命令执行)。
为了更好地理解这个过程,我们恢复了调用追踪的关键值。
函数:verifyHeaderAndExecuteTx:
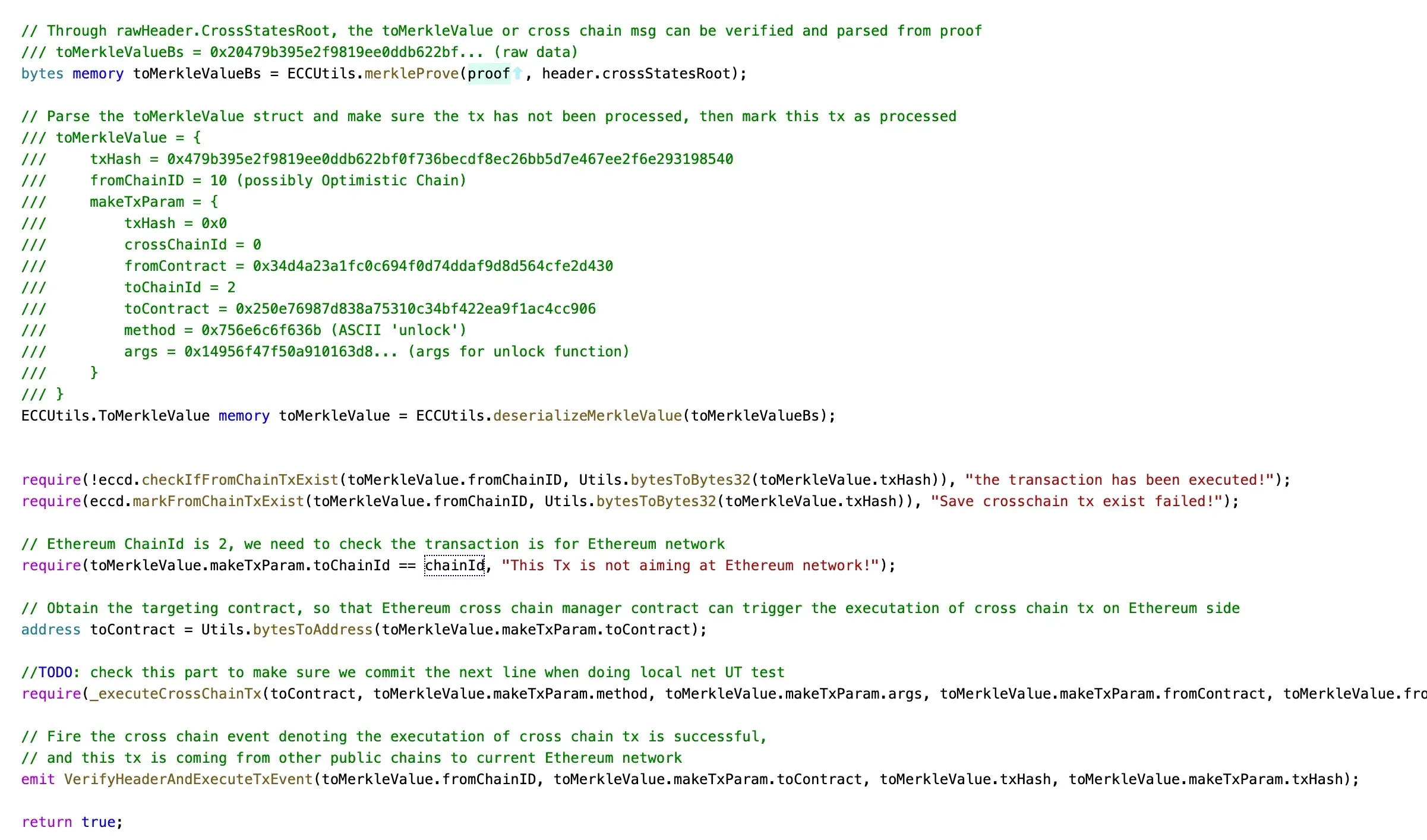
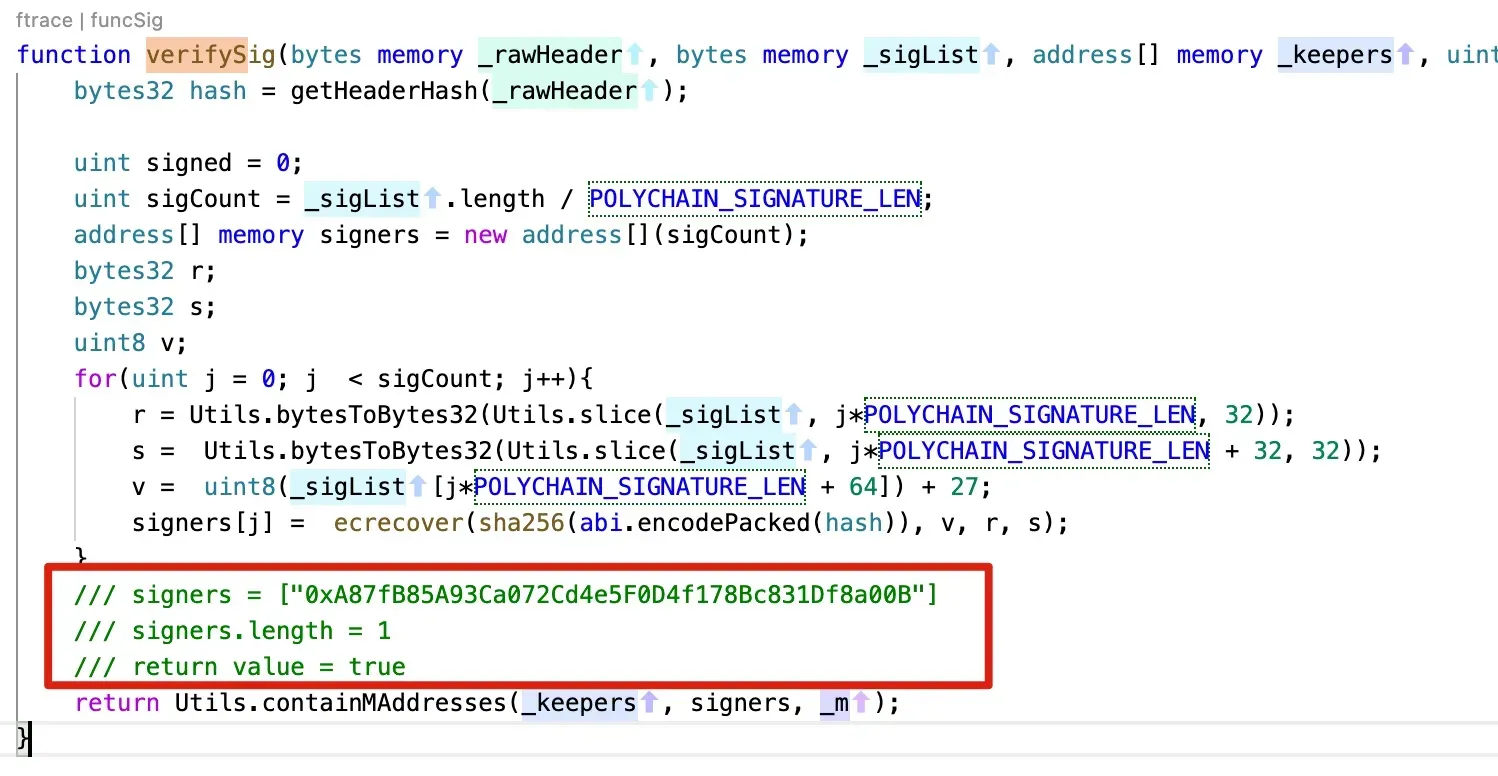
verifySig
unlock
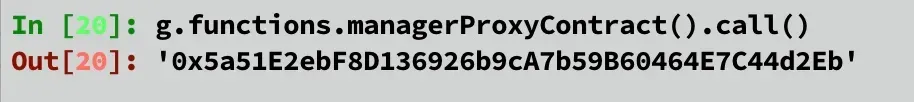
LockProxy 中的 managerProxyContract 变量。它与 unlock 函数的调用者地址值匹配。
结论
从恢复的值中,我们发现:
- 攻击者向
verifyHeaderAndExecuteTx函数提供了一个有效的签名消息。 - LockProxy 智能合约中的
onlyManagerContract修饰符未被绕过。
基于这两个观察,我们推测:
- 攻击者可能拥有用于签名消息的合法密钥,这表明签名密钥可能已泄露。
或者
- PolyNetwork 的签名过程中存在一个 bug,该 bug 被滥用来签名伪造的消息。
然而,我们没有更多的链下数据来验证我们的发现。我们希望我们的分析能为进一步的调查提供帮助。
鸣谢:Yufeng Hu, Siwei Wu, Lei Wu, Yajin Zhou @BlockSec
Twitter:https://twitter.com/BlockSecTeam




