On 30th Nov, our security incident monitoring system ThunderForecast discovered an attack on Loopring protocol (Blog in EN, CN) through scanning history transactions among the Ethereum. As a conclusion, the root cause of this attack is the lack of access control on the sellTokenForLRC function. The attacker took advantage of 80.97 ETH, which is equivalent to 48,849.2 USD based on the price at that time.
On 11th Dec 2020, our monitoring system ThunderForecast reported a series of transactions trading with an abnormal trade rate. Then, we used the EthScope system developed by our research team to analyze these transactions and discovered that this is an attack leveraging a vulnerability of Seal Finance Protocol for the arbitrage purpose.
What is Seal?
Mentioned at the Seal whitepaper: "SEAL - An experimental protocol that serves as an intermediary between major DeFi protocol tokens, creating deeper liquidity in between". Up to now, there exist over 10 liquidity pools which hook Seal with other different well-known tokens(such as UNI, YFI, USDT, SNX and etc.). To earn the bonus, the investor needs to deposit LP tokens into the SEAL reward contract and trigger the breed() function in the contract Farm to produce new SEAL tokens. The Farm contract is deployed in every Seal pool and the function breed() in the contract is used to issue new Seal tokens. As the setting of breed(), it issues an additional 1.6% of Seal Token. Furthermore, 0.8% of issued Seal tokens are exchanged to another token which is deposited into the pool with the other 0.8% of issued Seal tokens as liquidity. However, since there is no access control designed for the breed() function, anyone can trigger this function and this primitive design becomes the root cause of this reported attack.
The following is the confirmed source code of function breed():
function breed() external {
require(now / 1 days > today);
today += 1;
uint256 sealPairAmount = seal.balanceOf(address(cSeal));
uint256 tokenPairAmount = token.balanceOf(address(cSeal));
uint256 newSeal = sealPairAmount.mul(spawnRate).div(1e18);
uint256 amount = UniswapV2Library.getAmountOut(newSeal, sealPairAmount, tokenPairAmount);
seal.mint(address(cSeal), newSeal);
if(address(seal) < address(token))
cSeal.swap(0, amount, address(this), "");
else
cSeal.swap(amount, 0, address(this), "");
token.transfer(address(cSeal), amount);
seal.mint(address(cSeal), newSeal);
cSeal.mint(address(this));
}Details
We now start revealing more details of this attack with one attacking transaction. In this transaction, the attacker repeats the attacking logic for 10 Seal pools to maximize their profit. For the following analysis, we focus on the attack launched in the Seal-SNX pool.
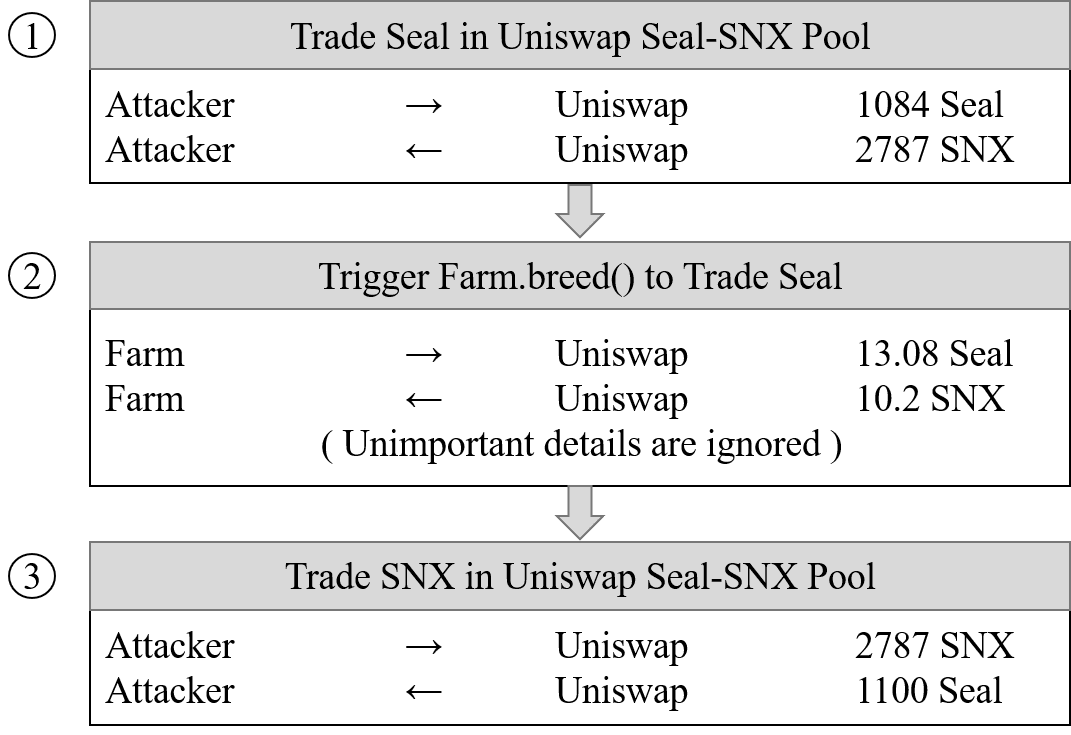
There are three steps involved:
- Step 1: Swap 1,084 Seal to 2,787 SNX in the Seal-SNX pool. The trade rate is: 1 Seal = 2.57 SNX.
- Step 2: Trigger
breed()function inFarmcontract. This function issues 13.08 Seal and swaps it to 10.20 SNX. The trade rate now is: 1 SNX = 0.78 Seal. The reason is that most of the SNX in the pool is swapped to Seal and causes a huge difference between SNX and Seal in terms of the amount. Then, based on the price calculation algorithm of Uniswap, SNX becomes extremely valuable(price increases over 3 times) in the pool. - Step 3: Swap 2787 SNX to 1100 Seal in the Seal-SNX pool. Since the exchange further increases the price of SNX, the attacker arb out more Seal tokens (extra 16 Seal).
To further measure and confirm the loss, we replayed breed() function under the block status, which is before the attack, by using our system EthScope. As a result, Farm issued 18 additional Seal tokens compared to normal invocation. The attacker grabs out 16 Seal and only 2 Seal are left in the pool.
Gain & Loss
In this transaction, the attacker gains total of 175 Seal.
The Scale of the Attack
Up to 13th December 2020, there are 3 malicious contracts(0x49f93e, 0x8b3710, 0x0f20b6) deployed on-chain and 22 transactions are successfully launched to rap 4,247 Seal tokens. Based on the price at the moment, the attacker earns about 58,467 USD through leveraging the vulnerability of Seal protocol. It is worth to mention that the vulnerability of Seal protocol is still under the attack!!!
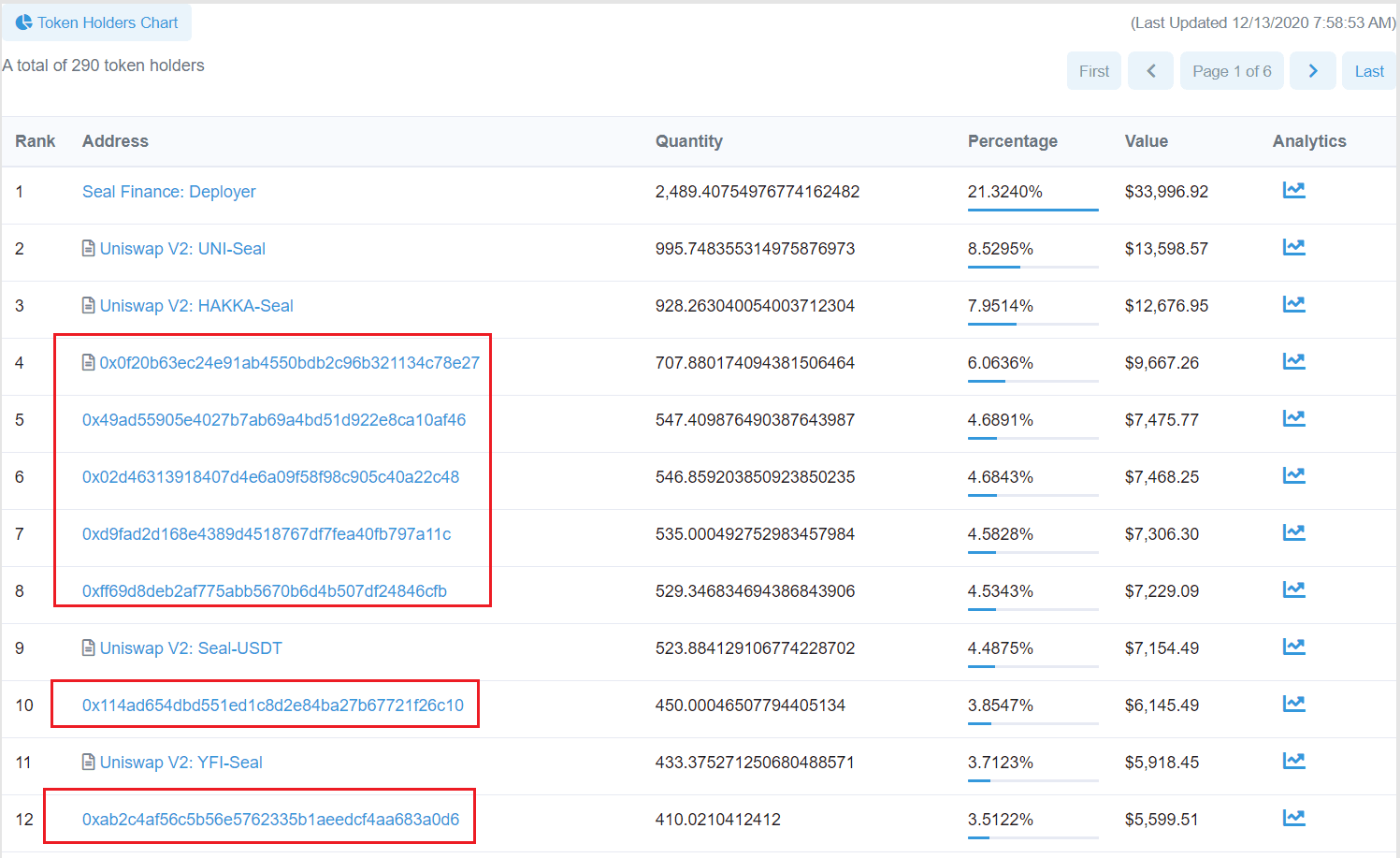
Furthermore, through analysing the flow of gained Seal tokens, we discover that around 900 Seal tokens are deposited into DEX and the rest is distributed into 6 different addresses. As shown in the following figure, those addresses are all top holders of Seal tokens apart from Seal Finance and the liquidity pool in the Uniswap V2.
The End
With the development of the DeFi eco-system in Ethereum, various security problems are gradually popping out. In fact, the root cause, which is access control, behind the attack causes a considerable loss (58,467USD) on Seal through launching 22 transactions up to 13th December 2020.
Update (2021/01/04)
After the first attack on 11/30, 2020, the attacker has deployed a third attack contract and launched five attacks. The last attack was on 12/24, 2020 and transferred the obtained Seal tokens to this address . During this process, the attacker obtained 6,021 Seal Tokens.
Timeline:
- 2020/12/11: Suspicious transactions were found
- 2020/12/12: Complete the analysis
- 2020/12/13: Reported to Seal Finance
- 2021/01/03:Details were released
- 2021/01/03: CVE-2021–3006 is assigned
About BlockSec
BlockSec is a pioneering blockchain security company established in 2021 by a group of globally distinguished security experts. The company is committed to enhancing security and usability for the emerging Web3 world in order to facilitate its mass adoption. To this end, BlockSec provides smart contract and EVM chain security auditing services, the Phalcon platform for security development and blocking threats proactively, the MetaSleuth platform for fund tracking and investigation, and MetaSuites extension for web3 builders surfing efficiently in the crypto world.
To date, the company has served over 300 esteemed clients such as MetaMask, Uniswap Foundation, Compound, Forta, and PancakeSwap, and received tens of millions of US dollars in two rounds of financing from preeminent investors, including Matrix Partners, Vitalbridge Capital, and Fenbushi Capital.
Official website: https://blocksec.com/
Official Twitter account: https://twitter.com/BlockSecTeam




