Background
L2 chains, with the advantage of improving the scalability of blockchain, have gained rapid growth in recent years. According to the data on L2BEAT, there are 58 active L2 projects, and the TVL (on Jun 26, 2024) is over $43 billion.
The motivation of L2 chains is solving the scaling issue in L1 chains, e.g., Ethereum. One respective method is called rollups, which bundles L2 transactions into L1 chains. Transactions are executed in L2 chains and the results (states) are committed on L1. By doing so, the L2’s security is guaranteed by L1 chains, which are further ensured by their consensus mechanism. The following figure shows the basic idea of rollup-based L2 chains.
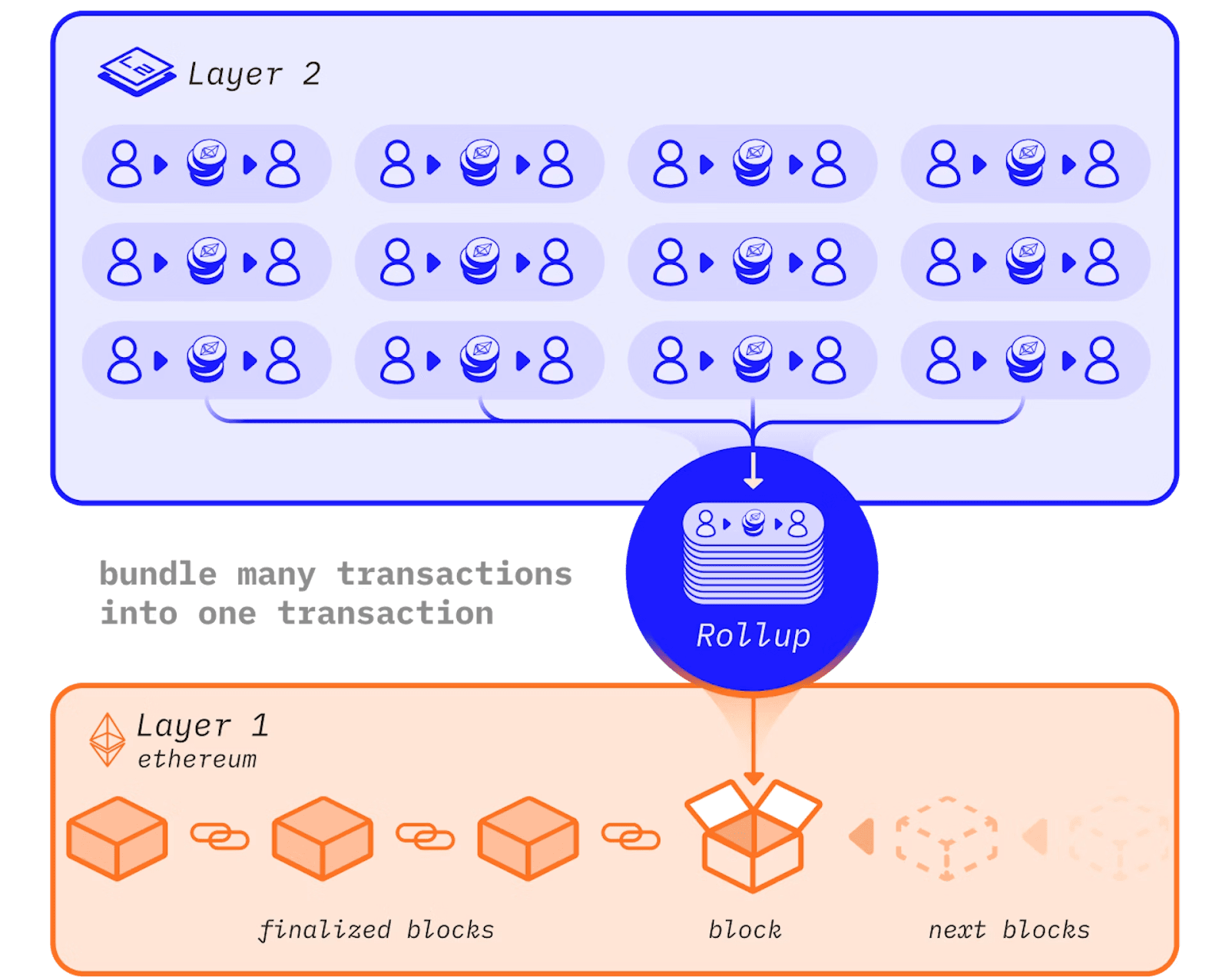
Rollups
Currently, the implementation of rollups mainly falls into two categories, i.e., zero-knowledge rollups and optimistic rollups. The basic idea of zero-knowledge rollup is that it exudes a batch of transactions and only commits necessary summary on the L1 chain, which shows the state changes of L2 transactions and proofs of these changes that can be verified through cryptographic algorithms.
The optimistic rollups are called "optimistic" because they assume transactions are valid and do not provide proof of state changes on L1 chains. Anyone can challenge the submitted data in a time window with proof of fraud. If the challenge is legitimate (that means the data committed into L1 contains invalid ones), then the sequencer who is responsible for including the fraud transactions will receive a penalty.
Sequencer
Sequencers in Rollups are critical parts, which are responsible for executing and batching L2 transactions and submitting them on L1 chains. For instance, in the optimistic rollups, a sequencer typically contains a node that receives L2 transactions, an execution virtual machine (Geth), batch proposers (or submitters) to submit the batch on L1 chains, and some other auxiliary components. In a nutshell, the sequencer is the component to pack transactions on L2 chains.
Sequencers can be operated in a centralized or decentralized way. In the centralized way, a sequencer (or multiple sequencers) is controlled by some centralized entities. On the contrary, decentralized sequencers will be selected in a pool using a permissionless way. Both ways have their pros and cons. Specifically, the centralized sequencers are more efficient and easy to implement, but with the possibility of a single point of failure. The decentralized sequencers are more robust but have more complicated design and implementation efforts.
According to the L2BEAT, centralized sequencers are the most common way for the L2 chains, including arbitrum, Optimism, zkSync Era, etc.
Why Security is Important for L2 Chain
Since L2 solves the scalability issue, it streamlines the user experience, reduces user cost, and attracts a lot of attention from users. However, security remains an issue from users’ perspective, because the hacks to the protocols will cause huge losses. For instance, the hack to the SonneFinance on Optimism caused more than 20 million USD loss due to precision loss. Liner even pauses its sequencer to prevent the attacker from dumping the token in the Velocore security incident.
Security is crucial for L2 chain operators due to the highly competitive landscape of L2 chains. Enhanced security attracts more users and increases the Total Value Locked (TVL), fostering a thriving ecosystem. This creates a positive feedback loop, where improved security leads to greater adoption, which in turn stimulates further growth and prosperity. Therefore, prioritizing security is essential for L2 chains to stand out and succeed in the market.
Current Solutions
Currently, security for L2 chains relies heavily on the security audits of the protocols themselves, and ad hoc monitoring solutions. These solutions have the following drawbacks.
Code Auditing
Security auditing itself cannot address all security concerns.
First, code auditing is a pre-launch security solution. After the deployment of the smart contracts on the chain, the zero-day vulnerabilities that were missed during the code auditing could be exploited. Previous security incidents have proven that some hacked protocols have gone through audits from reputable auditors (not to mention that some protocols may not afford the cost of such auditing).
Second, code auditing can only audit the static view of the code. It will miss the runtime states that will be changed by the configuration and parameters upgrade for the smart contracts.
Ad hoc Attack Monitoring
Some protocols will adopt the monitoring tools (either from some providers or through in-house development). However, the attack monitoring system relies on the domain knowledge of high-level security experts to be effective and maintain a low rate of false positives. What’s more important, they lack an automatic way to respond to the detected security incidents. Manual interventions often prove to be too late. In the case of the attack on Nomad Bridge last August, it took the project team over three hours to respond. The recent attack on KyberSwap also saw a response time of nearly two hours.
What’s more important, this needs the protocol to implement this monitoring system with their own cost of time and integration efforts. If we can achieve built-in security on the chain level, this offers a superior solution for both protocols and users. It ensures ongoing security without the need for costly integrations, providing a more robust and seamless security framework.
Our Solution: Sequencer Threat Overwatch Program
BlockSec is a pioneer in this direction. As early as 2022, we proposed the concept of “making blockchain attack blockable” and successfully blocked a series of hacks and rescued more than 20 million USD. With the development of L2 chains, we push this direction a little further and present an innovative security solution to make L2 with built-in security, using the attack detection capability of our Phalcon product. We define this built-in security solution at the sequencer level, empowered by Phalcon, as the Sequencer Threat Overwatch Program (STOP).
The basic idea of STOP is that we can integrate the attack detection engine into the sequencer of L2 chains. Each L2 transaction will go through the attack detection engine before being included in L2 chains. If the attack detection engine thinks it’s a malicious transaction, it can be put into quarantine for further inspection. By doing so, it can prevent attack transactions from going into the L2 chains in the first place, without any effort and cost from the protocols and users.
Though this idea looks straightforward, deploying this system has considerable design challenges.
-
First, how to make the system a non-intrusive one? That’s because if the integration requires a deep hook into the sequencer, this may bring compatibility, robustness, and maintenance issues.
-
Second, how to make this system efficient? That’s because they may have thousands of transactions that need to be processed in seconds. How to hook into the sequencer while at the same time does not affect the throughput of the L2 chains needs to be addressed.
-
Third, how to maintain a low false positive rate to not affect the legitimate transaction. If legitimate transactions are miscategorized and put into quarantine, it will highly affect the usability of the chain and even cause the user to miss profit opportunities.
Our solution successfully solves the challenge with a non-intrusive architecture, with an attack detection engine powered by Phalcon. Specifically, we introduce a threat inspection node in the L2 chain before the sequencer. This threat inspection node communicates with Phalcon to scan each transaction and return the result. The malicious transactions recognized by Phalcon will be put into quarantine, and the passed ones will go to the mempool of the sequencer. The following figure shows the overall system architecture.
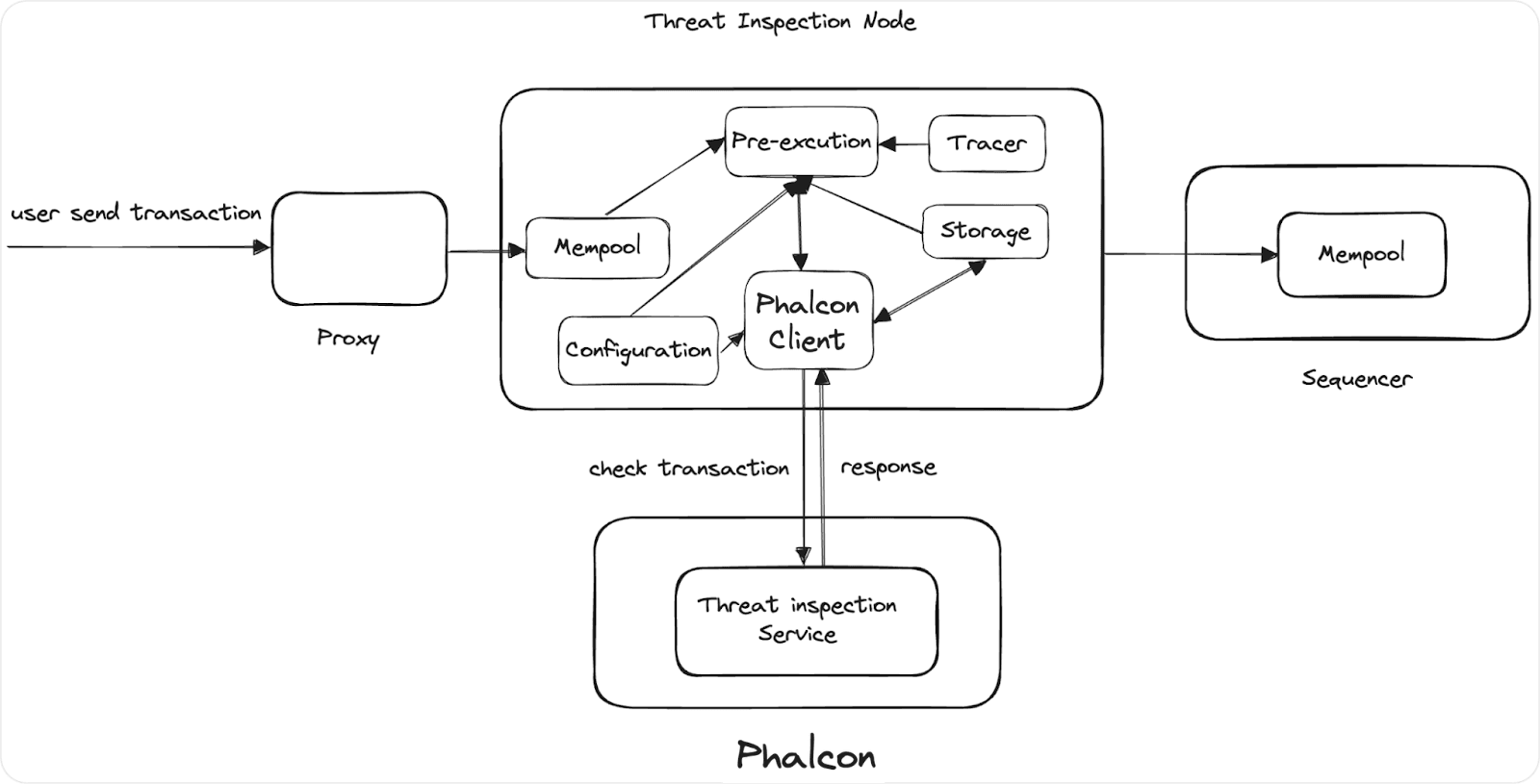
Our attack detection engine is highly efficient and accurate. It can typically finish the detection of a transaction within a couple of milliseconds, with less than 0.0001% false positive rate. Coupled with other self-defined rules, this false positive rate can be further reduced. Note that this engine has been battle-tested with the successful story of detecting and blocking multiple hacks. See the list of (public) disclosed security incidents detected by our engine and the successful story of attack blocking.
Besides, the STOP system couples with a dashboard for the chain operator to further vet the transactions inside the quarantine. With the help of our Phalcon Explorer, the analyst can fully identify the root cause of the hack transactions, and take further action.
Manta: First L2 with Built-in Security
We are thrilled to partner with Manta to bring this initiative to life, making Manta Pacific the first L2 with built-in security. Specifically, BlockSec and Manta co-developed STOP, an innovative Layer 2 security solution. Each transaction on Manta Pacific will be scanned by BlockSec Phalcon's attack detection engine, preventing attack transactions from going into the L2 chains in the first place.
The collaboration brings robust security enhancements to Manta Pacific while ensuring that its usability and efficiency remain unaffected. At the same time, protocols and users are protected without investing additional time and effort. We commend Manta's proactive approach to sequencer-level security and its commitment to making Manta Pacific such a highly secure, high-performance, and user-friendly L2 chain. It is encouraging to see more chains and protocol projects prioritize security, enabling users to interact confidently and safely.
Conclusion
In this blog, we propose the architecture to provide built-in security to L2 chains. We hope this pioneering direction and insights can help the whole community to solve security issues from the ground up and protect users. In the future, we will continue to explore and deliver even more innovative security solutions, ensuring that our systems remain at the forefront of blockchain security and provide the highest level of protection for our users.
References
https://blocksec.com/blog/blocksec-perspectives-and-solutions-on-the-security-of-l2-blockchains
https://blocksec.com/blog/how-L2-blockchains-can-do-better-to-protect-their-users
https://ethereum.org/en/layer-2/
https://docs.optimism.io/stack/components
About BlockSec
BlockSec is a full-stack Web3 security service provider. The company is committed to enhancing security and usability for the emerging Web3 world in order to facilitate its mass adoption. To this end, BlockSec provides smart contract and EVM chain security auditing services, the Phalcon platform for security development and blocking threats proactively, the MetaSleuth platform for fund tracking and investigation, and MetaSuites extension for web3 builders surfing efficiently in the crypto world.
To date, the company has served over 300 clients such as Uniswap Foundation, Compound, Forta, and PancakeSwap, and received tens of millions of US dollars in two rounds of financing from preeminent investors, including Matrix Partners, Vitalbridge Capital, and Fenbushi Capital.
-
Website: https://blocksec.com/
-
Email: [email protected]
-
Twitter:https://twitter.com/BlockSecTeam
-
MetaSleuth: https://metasleuth.io/
-
MetaSuites: https://blocksec.com/metasuites




