In the world of DeFi, no project can guarantee itself to always be safe. However, this is not the reason for us to bury our heads in the sand. In the face of threats, on the one hand, we need to be well-prepared and continuously improve our incident response plans. On the other hand, we should be able to respond swiftly and cut losses promptly when risks arise.
However, manual interventions often prove to be too late. In the case of the attack on Nomad Bridge last August, it took the project team over three hours to respond. The recent attack on KyberSwap also saw a response time of nearly two hours.
To do a good job, one must first have the right tools! In addition to monitoring attacks, Phalcon can even assist projects in automatically triggering preset incident response mechanisms (including pausing and frontrunning) in critical situations. This reduces the response time from several hours to within one block time.
A Recap of the KyberSwap Incident
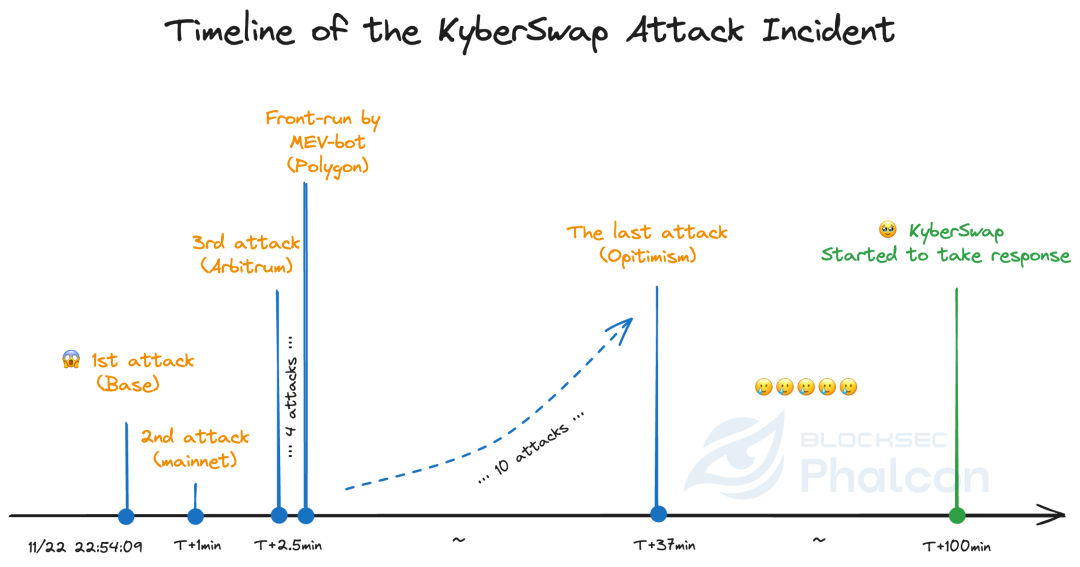
1>> On 11/22/2023 at 22:54:09 UTC, Phalcon detected the first attack against KyberSwap, which occurred on the Base chain and resulted in a loss of $857,025.
2>> One minute later, Phalcon detected another attack in the form of a private transaction, which occurred on the Ethereum mainnet and resulted in a loss of $64,896.
3>> Starting from 11/22/2023 at 22:56:34 UTC, the attacker launched multiple attacks on Arbitrum, Optimism, Polygon, and Avalanche.
4>> The attacker's partial attack transactions on Polygon and on Avalanche were frontrunned by another "seasoned" MEV Bot. The latter gained profits of approximately $5.36 million.
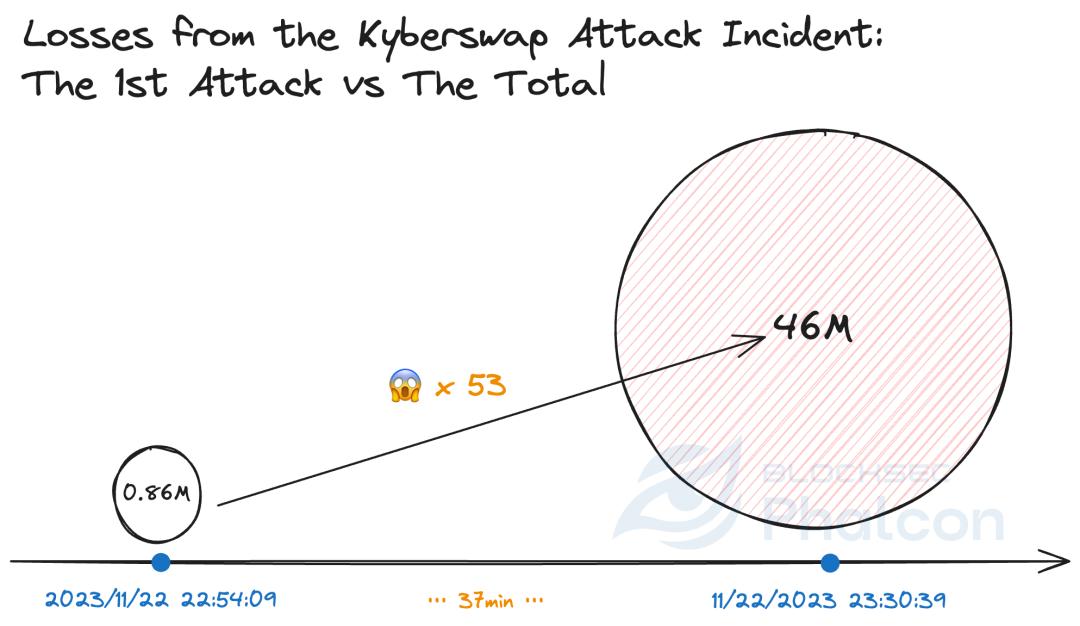
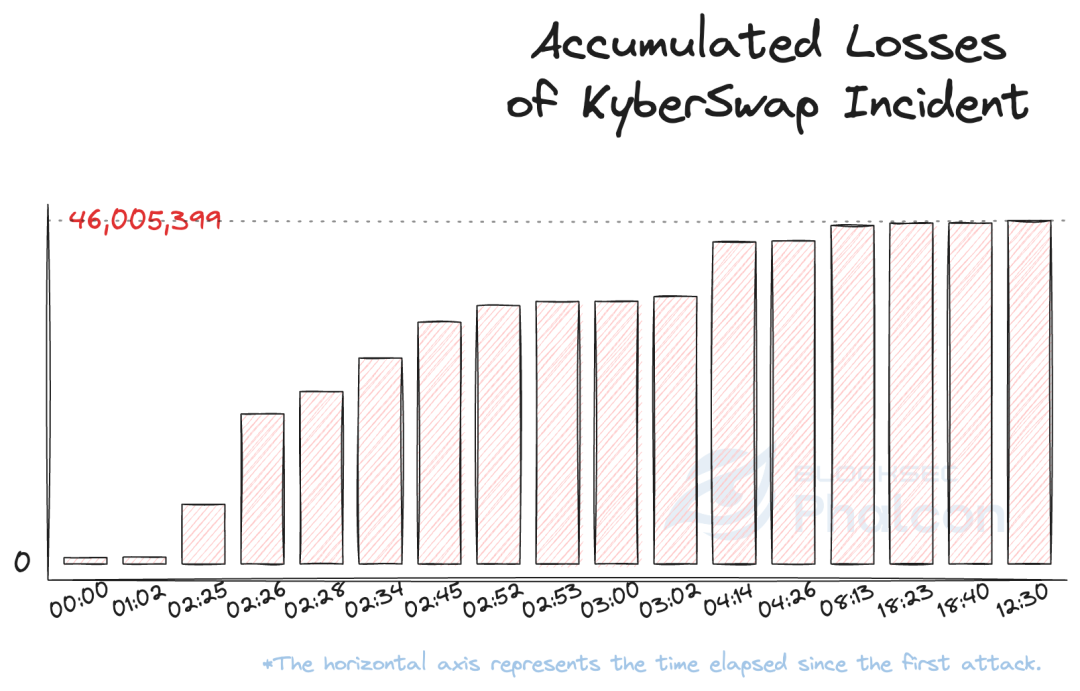
5>> On 11/22/2023 at 23:30:39 UTC, the attacker concluded the attacks after about 37 minutes, during which the attacker initiated 17 attack transactions across six chains and caused a loss of $46 million (excluding "secondary" attacks from imitators).
6>> On 11/23/2023 at 0:36:47 UTC, approximately 100 minutes after the first attack, the protocol team began pausing the protocols on different chains. 🥲
A Typical Attack Path: Private Transaction & Multi-chain Attack
Why Is "Automated Incident Response" Crucial for Web3 Security?
100min vs 12s; $46, 000, 000 vs $860,000
As soon as Phalcon detects the first attack, it can automatically trigger protocol pausing or other preset response actions. It can also simultaneously pause the same protocol on other chains. In the case of the KyberSwap incident, Phalcon can reduce the loss to $860,000 (the loss in the first attack) instead of the current $46, 000, 000.
Phalcon supports both single and multi-signature scenarios, ensuring that incident response mechanisms can be executed immediately.
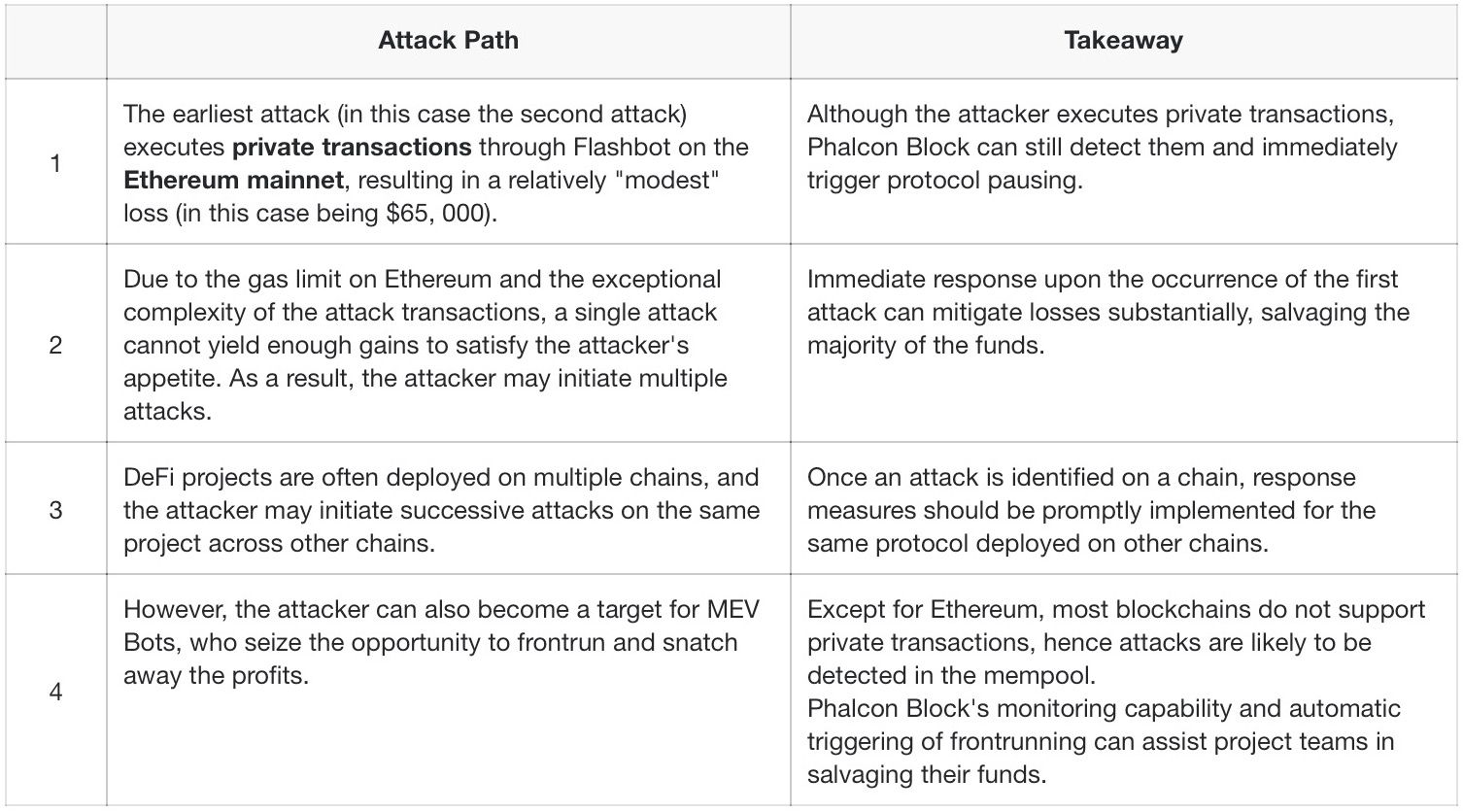
A single private transaction won't be an attacker's only move
Over 90% of attackers won't stop after executing a single private transaction, and attacks normally do not occur solely on the mainnet.
In the KyberSwap incident, only three out of 17 attack transactions were conducted through private transactions. The loss from the first private transaction accounted for 0.14% of the total loss, and the three private transactions together amounted to 16%. The first attack transaction, which was not a private transaction, caused 2% of the total loss.
This shows that even if hackers execute private transactions, losses can still be significantly reduced as long as the attack is detected in time and effective response measures are taken promptly!
When an attack occurs, time is money
Since there is no cooperation established between us and KyberSwap, when we detected the attack against KyberSwap, we could only try to reach out to the team through public channels as soon as possible.
Regrettably, for the project team, even if they receive the threat intelligence at this point, it would be too late to respond manually. Keeping decentralized governance in mind, KyberSwap adopts a multi-sig approach for important actions. In other words, upon receiving the threat intelligence, the project team needs to:
- immediately assess the intelligence, including determining whether there is an attack, the risk level and whether countermeasures should be taken;
- engage in multi-party consultations and reach consensus on response measures;
- have multiple parties sign the response transactions...
While the attack is still underway and every second counts! Indeed, over a hundred minutes passed between the occurrence of the first attack and the moment the project team started to respond. 😢
By adopting the solution provided by Phalcon, the project team can integrate Phalcon through various methods without affecting multi-signature governance. This allows for immediate response in the event of an incident, with automated execution of response measures!
How Can Project Teams Respond to Security Threats?
Solution 1
- Establish a monitoring system (instead of relying solely on alert information from Twitter).
- Develop risk assessment criteria and corresponding incident response plans.
- Set up a dedicated incident response team.
- Set up a 24/7 operations and maintenance team.
- ...
Solution 2
If you subscribe to Phalcon, the system and our security experts will help you complete all of the above tasks! It includes:
- precise and comprehensive monitoring of external threats;
- flexible configuration of various monitoring rules;
- intelligent risk grading;
- automated and fast responses (such as protocol pausing and frontrunning).
You can ensure the safety of your protocol without the need for 24/7 operations and maintenance.
Phalcon has been officially launched. Feel free to inquire or book a demo.
References
[1] BlockSec | Analysis of the Causes Behind the KyberSwap Incident
[2] MetaSleuth | Fund Flow Tracing Analysis of the KyberSwap Incident
Read more:
BlockSec | Yet Another Tragedy of Precision Loss: An In-Depth Analysis of the KyberSwap Incident
About BlockSec
BlockSec is a pioneering blockchain security company established in 2021 by a group of globally distinguished security experts. The company is committed to enhancing security and usability for the emerging Web3 world in order to facilitate its mass adoption. To this end, BlockSec provides smart contract and EVM chain security auditing services, the Phalcon platform for security development and blocking threats proactively, the MetaSleuth platform for fund tracking and investigation, and MetaDock extension for web3 builders surfing efficiently in the crypto world.
To date, the company has served over 300 esteemed clients such as MetaMask, Uniswap Foundation, Compound, Forta, and PancakeSwap, and received tens of millions of US dollars in two rounds of financing from preeminent investors, including Matrix Partners, Vitalbridge Capital, and Fenbushi Capital.
Twitter account of BlockSec: https://twitter.com/BlockSecTeam
Twitter account of Phalcon: https://twitter.com/Phalcon_xyz




