On January 28, the QBridge was attacked and the asset values around 80M USDs were stolen. After the analysis, we found that the root cause in the code is the implementation of the safeTransfer (and safeTransferFrom) function.
The Root Cause
First, the project does not use the popular OpenZeppelin SafeERC20 library for the token transfer. Instead, they implemented a library called SafeToken.
Second, the implementation does not check the target is a valid contract (or whether it's a zero address).
Third, the low-level call of the EVM does not return false when the target contract is zero. This contradicts the developer's common sense.

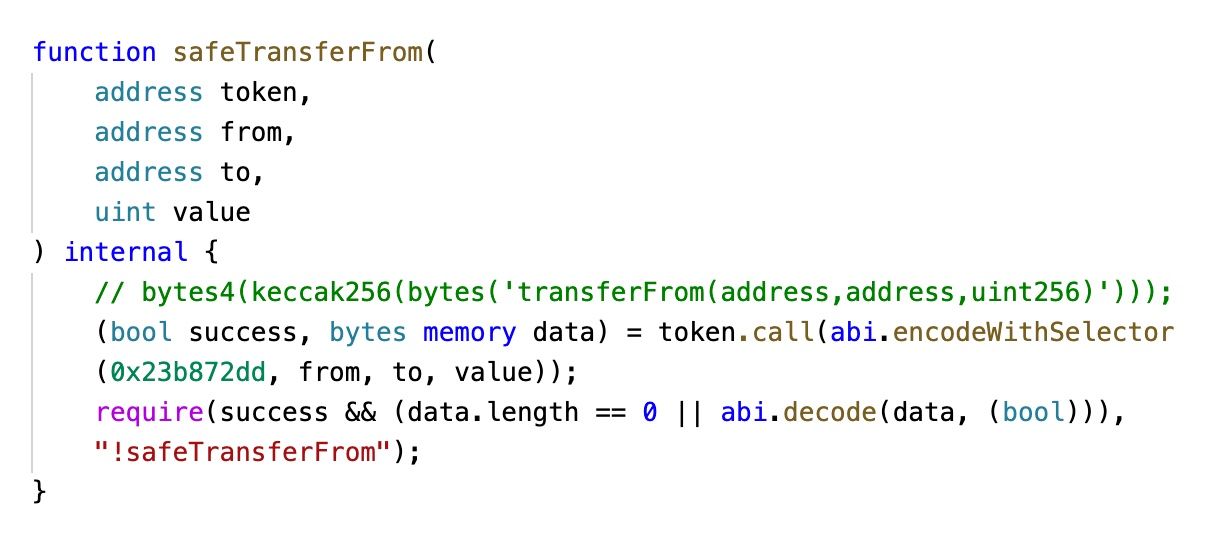
Of course, the incident also has some other reasons, e.g., the zero address is put into the whitelist. However, if the code can properly handle this special case, then it's not vulnerable.
BTW: There exist other projects using the similar code. They may be susceptible to the similar issue.
Experiment
To confirm the third reason that VM does not return false when the target contract is zero, we developed a test contract, as shown in the following.
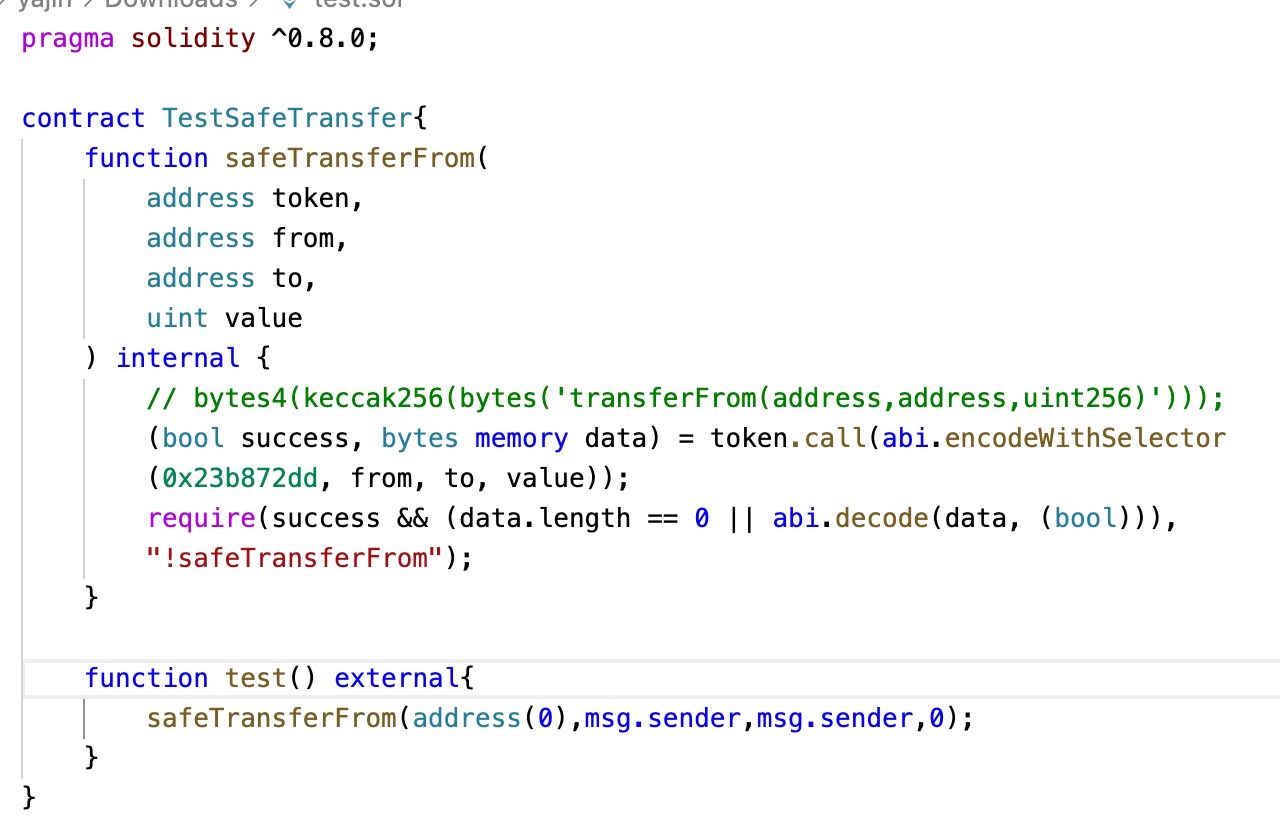
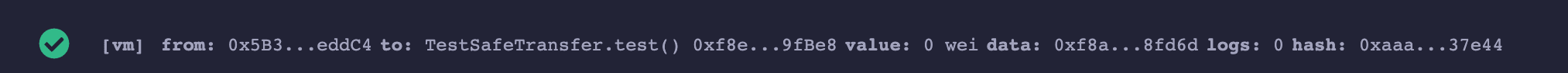
The execution of TestSafeTransfer.test() will not revert.
Lessons and How to Mitigate the Risk
We suggest that
- Use the popular library instead of inventing your own wheel, unless you have a very very good reason,
- check the balance before and after the asset transfer to ensure that number of the transferred asset compiles the expectation. This can also avoid the issue of the deflation and inflation token.
About BlockSec
BlockSec is a pioneering blockchain security company established in 2021 by a group of globally distinguished security experts. The company is committed to enhancing security and usability for the emerging Web3 world in order to facilitate its mass adoption. To this end, BlockSec provides smart contract and EVM chain security auditing services, the Phalcon platform for security development and blocking threats proactively, the MetaSleuth platform for fund tracking and investigation, and MetaDock extension for web3 builders surfing efficiently in the crypto world.
To date, the company has served over 300 esteemed clients such as MetaMask, Uniswap Foundation, Compound, Forta, and PancakeSwap, and received tens of millions of US dollars in two rounds of financing from preeminent investors, including Matrix Partners, Vitalbridge Capital, and Fenbushi Capital.
Official website: https://blocksec.com/
Official Twitter account: https://twitter.com/BlockSecTeam




