BlockSec's latest study on transaction-based phishing on Ethereum has recently been accepted for full paper publication at ACM CCS 2023!
As one of the top four conferences in the field of computer security, ACM CCS maintains a low acceptance rate for submitted papers, with only around 18% being accepted over the past five years. The conference focuses on collecting the latest advancements from research institutions and tech companies across the globe in network security, privacy protection, and applied cryptography.
At the ACM CCS 2023 conference held in Copenhagen, Denmark, we will be presenting BlockSec's latest research findings on transaction-based phishing on Ethereum, as well as our large-scale TxPHISH website detection system, TxPhishScope.
Rampant TxPHISH Scams on Ethereum
As users trade tokens by sending transactions on Ethereum, a new form of phishing scam has emerged. Unlike traditional ones that target victims’ personal or financial information, this type of phishing steals users’ assets through transactions. Specifically, scammers trick victims into signing transactions or messages that enable them to withdraw the victims’ tokens in transactions. Since the phishing scam mainly involves victims’ signing transactions, we name it TxPHISH.
From January to November 2023, we witnessed 12 large-scale TxPhish incidents, which led to a collective loss worth more than $85 million (with an average loss of over $7 million per large-scale incident). In reality, this type of phishing scam is happening every day. Just within the last 7 days, MetaSleuth alone has reported over 100 phishing alerts, with user losses caused by phishing transactions reaching up to $2.45 million. Therefore, conducting in-depth research on TxPHISH websites holds profound significance for blockchain security.
TxPhishScope: Our Large-Scale TxPHISH Website Detection System
Based on the core characteristics of phishing transactions, we designed a large-scale TxPHISH website detection system called TxPhishScope (this system also provides support for our other products such as MetaDock and MetaSleuth).
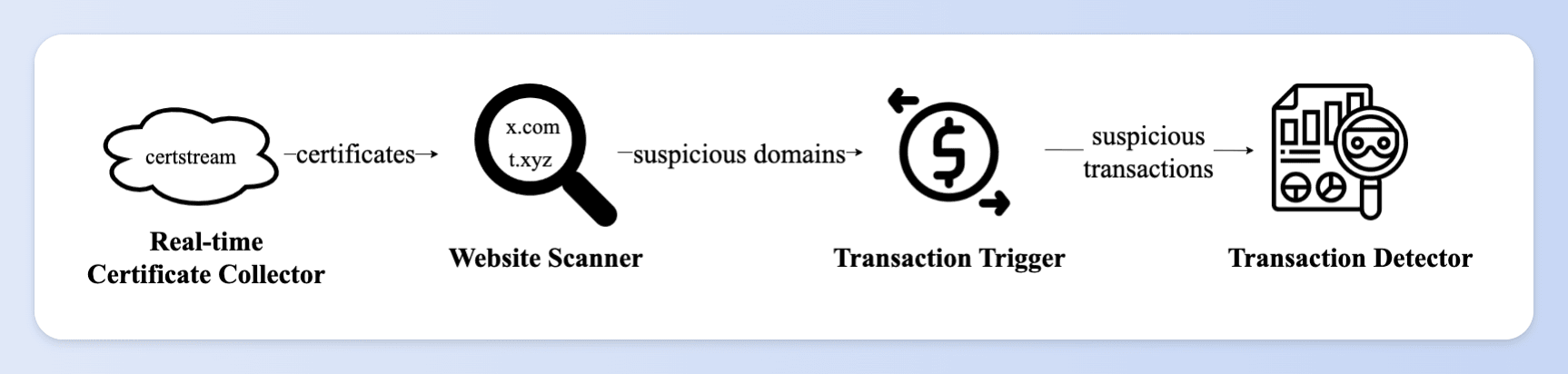
TxPhishScope first collects real-time issued website certificates from the Certificate Transparency Log network and retrieves suspicious domains. After that, TxPhishScope dynamically visits the websites and then triggers a simulation execution of transactions. It decides whether the transaction is a phishing transaction based on the results of the simulation execution. If it is a phishing transaction, TxPhishScope automatically saves the evidence chain (including transaction content and website content).
We have had TxPhishScope in operation since November 2022. To protect users, we have reported 33,130 TxPHISH websites and 3,981 phishing accounts to Ethereum security communities, including MetaMask Forta, and Etherscan. Additionally, we provided evidence of phishing activities to project teams, such as FixedFloat, SimpleSwap, and Binance, to assist in recovering users' funds. Currently, TxPhishScope is still providing real-time reports of TxPHISH websites and phishing accounts for the Forta Scam Bot.
You can click here to experience this service.
Features and Money Laundering Patterns of TxPHISH Websites
Furthermore, through large-scale measurement studies, we conducted in-depth research on the characteristics of TxPHISH websites and systematically analyzed the phishing fund flows. We found that these websites have short lifespans, low deployment costs, fast update frequency, and are highly deceptive. Web3 security companies can develop new detection tools and algorithms based on these characteristics to accurately and timely identify TxPHISH websites.
At the same time, we found that the money laundering patterns of most phishing accounts are relatively fixed, with a significant portion of funds flowing into exchanges. This finding helps in understanding the direction of fund flows and facilitating the timely recovery of stolen funds.
We are well aware that protecting users from TxPHISH requires the combined efforts of multiple Web3 service providers. Therefore, we will share our latest research findings at the ACM CCS conference, which is the first large-scale detection and measurement study of TxPHISH websites. We hope that by sharing our findings, Web3 practitioners will be able to more fully understand the features and money laundering patterns of TxPHISH websites, allowing them to improve their defense strategies and mechanisms and protect users against transaction-based phishing scams.
Time: November 27, 11:00 AM (UTC +1)
Session: ATTACKS & THREATS
Presenter: Bowen He, member of BlockSec research team (first author of the paper)
Topic: TxPhishScope: Towards Detecting and Understanding Transaction-based Phishing on Ethereum
You can click here to view the full paper.
About BlockSec
BlockSec is a pioneering blockchain security company established in 2021 by a group of globally distinguished security experts. The company is committed to enhancing security and usability for the emerging Web3 world in order to facilitate its mass adoption. To this end, BlockSec provides smart contract and EVM chain security auditing services, the Phalcon platform for security development and blocking threats proactively, the MetaSleuth platform for fund tracking and investigation, and MetaDock extension for web3 builders surfing efficiently in the crypto world.
To date, the company has served over 300 esteemed clients such as MetaMask, Uniswap Foundation, Compound, Forta, and PancakeSwap, and received tens of millions of US dollars in two rounds of financing from preeminent investors, including Matrix Partners, Vitalbridge Capital, and Fenbushi Capital.
Official website: https://blocksec.com/
Official Twitter account: https://twitter.com/BlockSecTeam




