On Aug 08 2021 (Beijing Time, block height 12982491), Zerogoki was attacked, which caused a loss of 670K USD. After the investigation, we found that it’s related to the compromised price oracle. The attacker provides a price oracle signed by legitimate private keys, which contain crafted number of tokens to be swapped. However the reason why the attacker can construct a valid signature is unknown yet.
Code Analysis
We first performed an analysis on the attacked contract (0x80ecdb90).
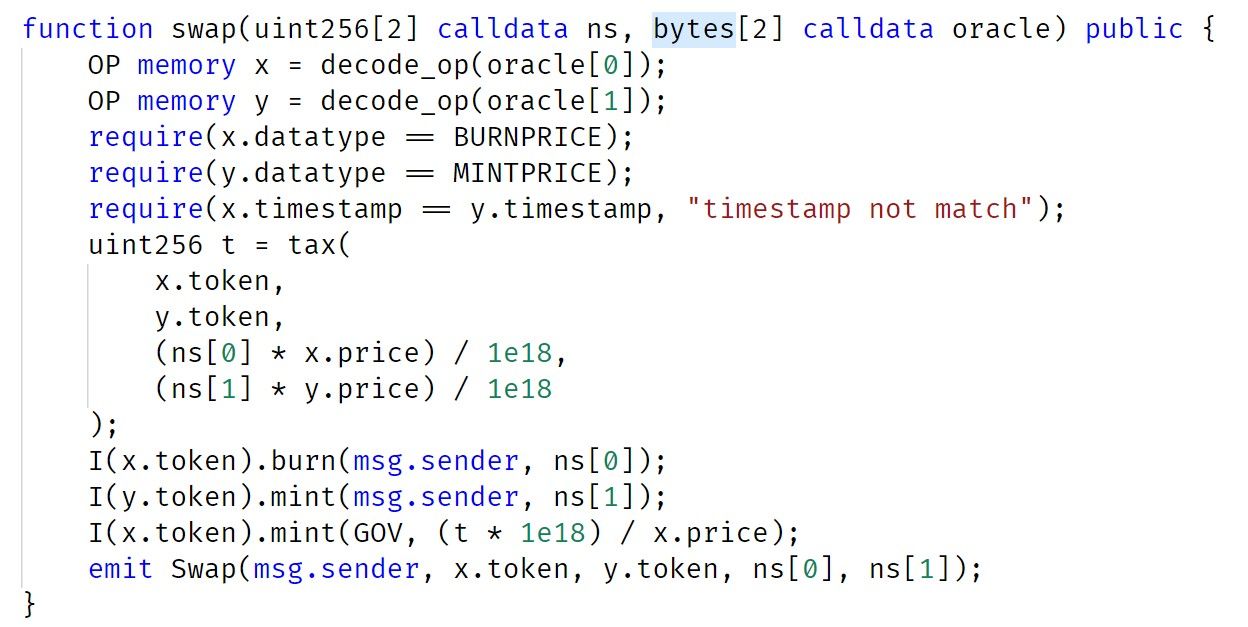
The swap function calls decode_op to obtain the information in the oracle. After performing the validation, the contract then burns the ns[0] x.token, mints ns[1] y.token and pays the swap fee to the GOV contract.
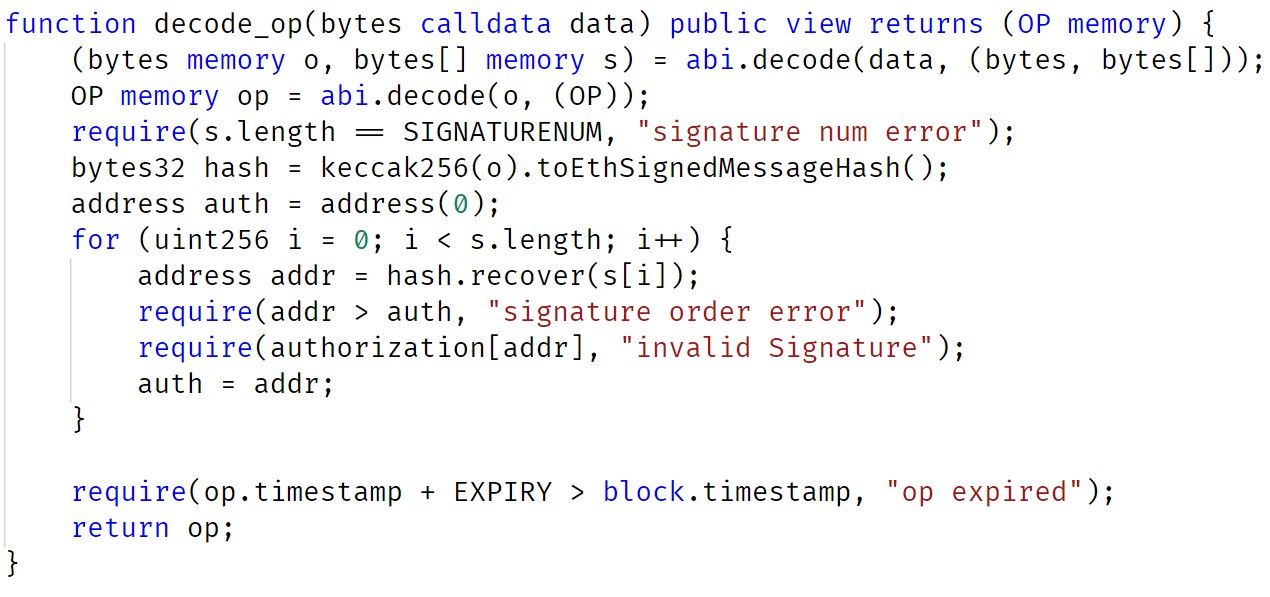
From the implementation of the decode_op, there exists three signatures in the parameter. These signatures need to be checked (and authorization) before performing the token swap (burning and minting).
In summary, the first parameter ns of the swap function defines the number of tokens to be swapped. The second parameter contains the signatures that need to be validated. When the validation passes, the number of tokens swapped is defined in the first parameter (ns).
Attack Analysis
In the attack transaction, 0x81e5f715,the attacker constructs a message contains valid signatures and passed a crafted ns parameter (which contains a large number of zUSD). As a result, the attacker used 300 REI to swap 700k zUSD.
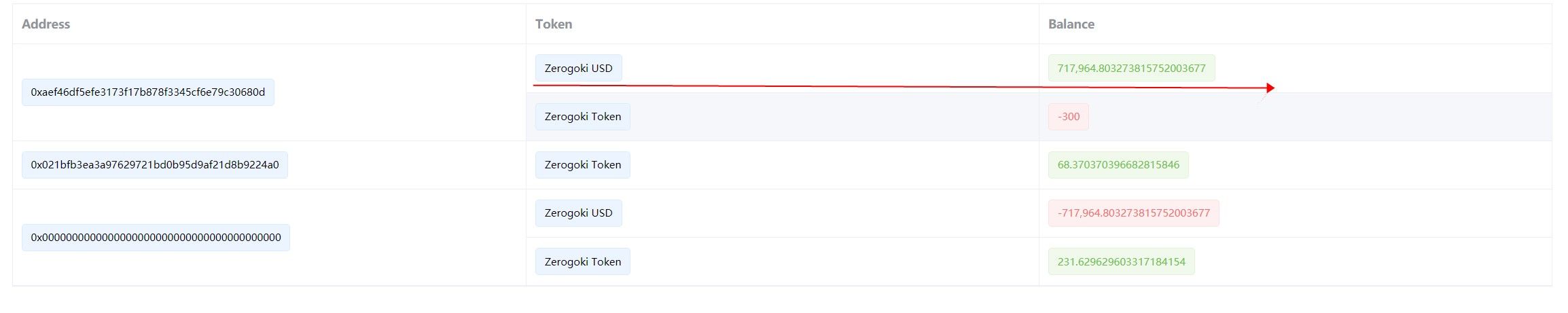
Three addresses that are collated with the signatures are:
0x0d93A21b4A971dF713CfC057e43F5D230E76261C
0x3054e19707447800f0666ba274a249fc9a67aa4a
0x4448993f493b1d8d9ed51f22f1d30b9b4377dfd2However, we do not have information why the private keys of these addresses have been leaked, at the current stage.
Takeaway
Making a DeFi project secure is not an easy job. Besides the code audit, we think the community should take a proactive method to monitor the project status, and block the attack before it even takes place.
About BlockSec
BlockSec is a pioneering blockchain security company established in 2021 by a group of globally distinguished security experts. The company is committed to enhancing security and usability for the emerging Web3 world in order to facilitate its mass adoption. To this end, BlockSec provides smart contract and EVM chain security auditing services, the Phalcon platform for security development and blocking threats proactively, the MetaSleuth platform for fund tracking and investigation, and MetaSuites extension for web3 builders surfing efficiently in the crypto world.
To date, the company has served over 300 esteemed clients such as MetaMask, Uniswap Foundation, Compound, Forta, and PancakeSwap, and received tens of millions of US dollars in two rounds of financing from preeminent investors, including Matrix Partners, Vitalbridge Capital, and Fenbushi Capital.
Official website: https://blocksec.com/
Official Twitter account: https://twitter.com/BlockSecTeam




