On July 21st, our DeFiRanger system reported a couple of suspicious transactions. After manual analysis, we confirm that these transactions are attacks to Sanshu Inu. Specifically, the Memstake contract of Sanshu Inu was attacked by abusing the deflation mechanism.
In the following, we will use multiple attack transactions to illustrate the attack process.
Attack Flow
The following figure lists some of the transactions launched by the attacker (0x333).
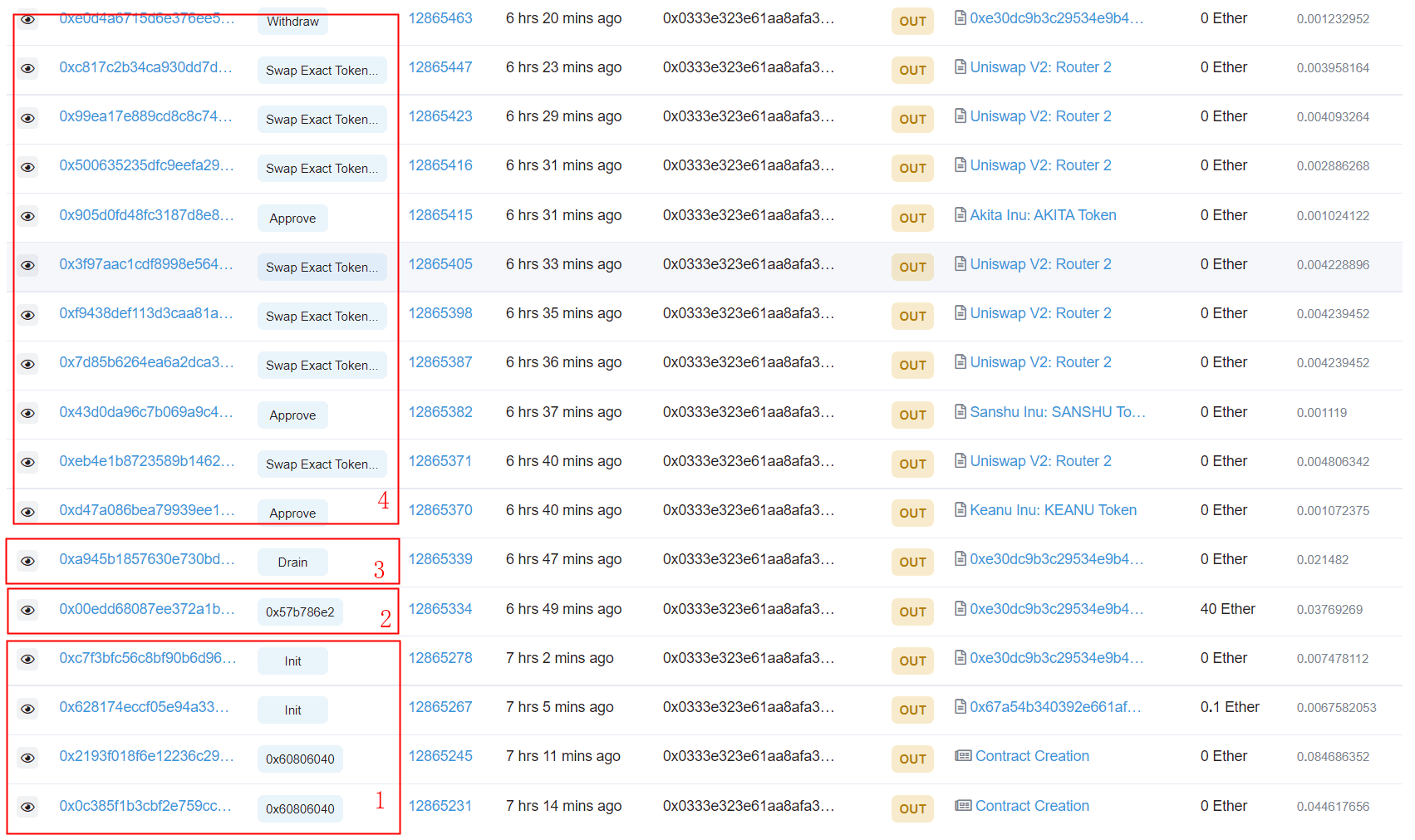
The attack consists of four steps. The critical one is the second step, which leverages the deflation mechanism of the ERC20 token to manipulate the reward calculation of the Memstake smart contract.
-
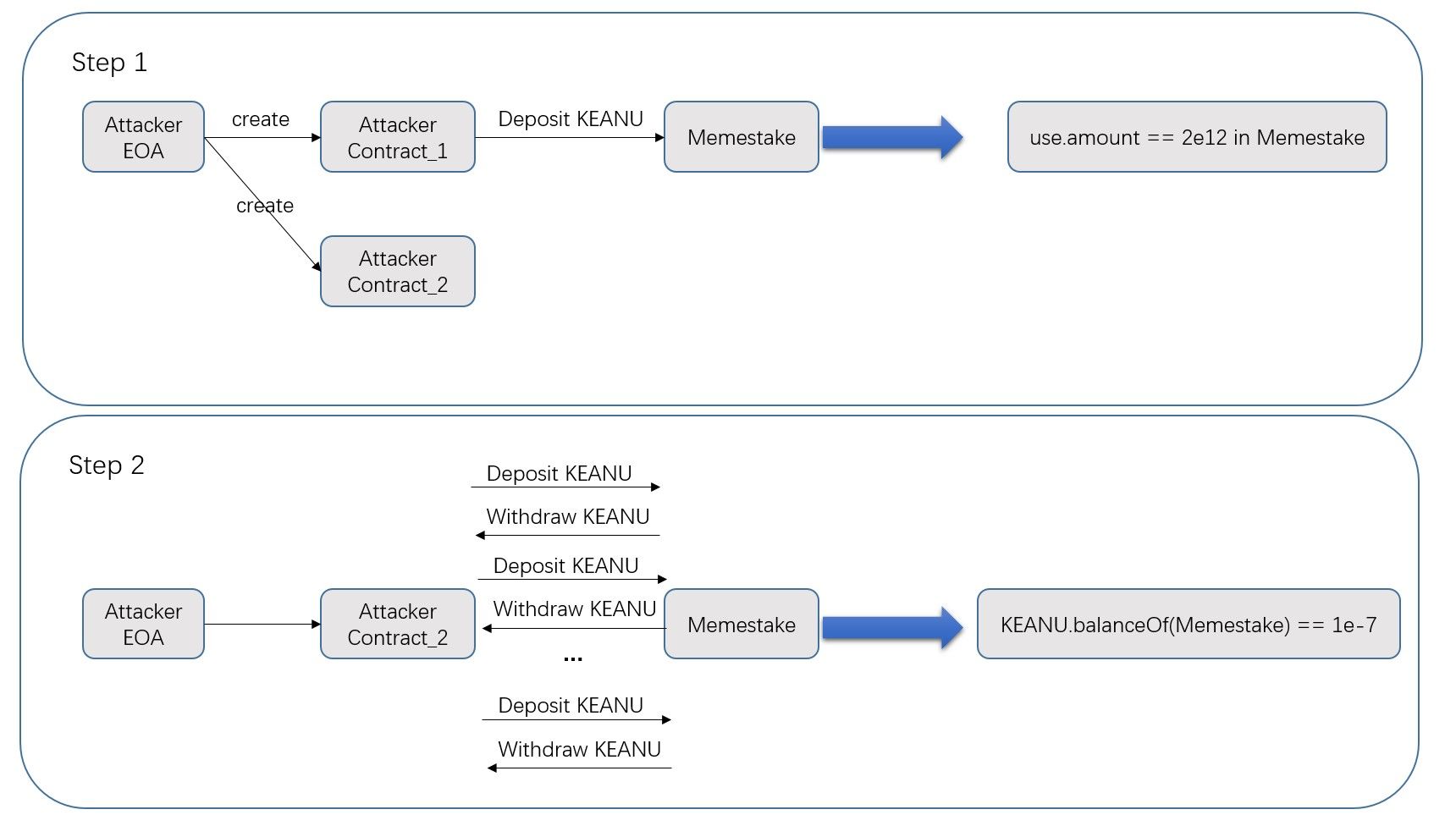
Step 1 (preparation): The attacker creates two attack contracts. The first one is a contract that deposits 2,049B KEANU. The second one is the attack contract.
-
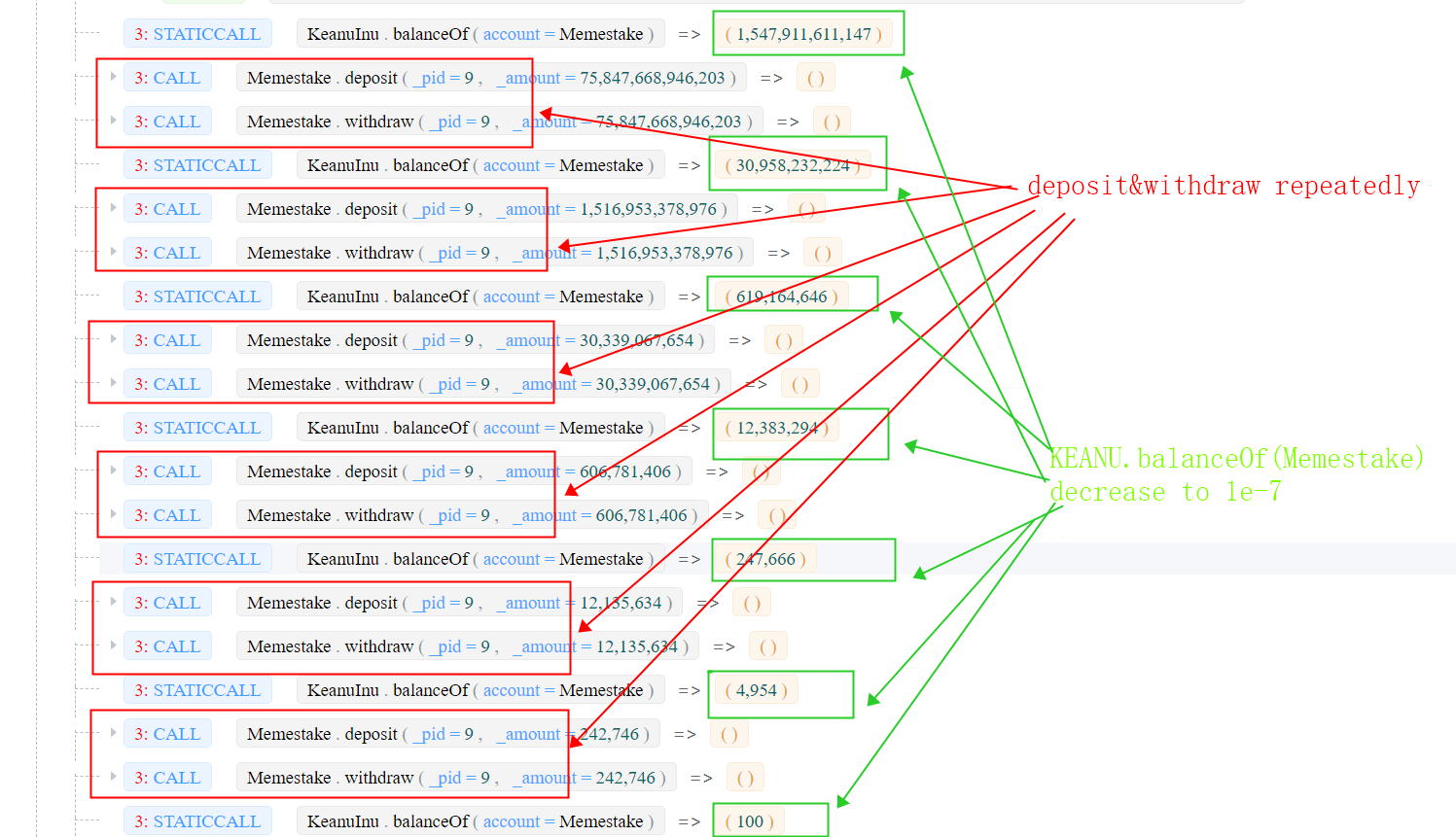
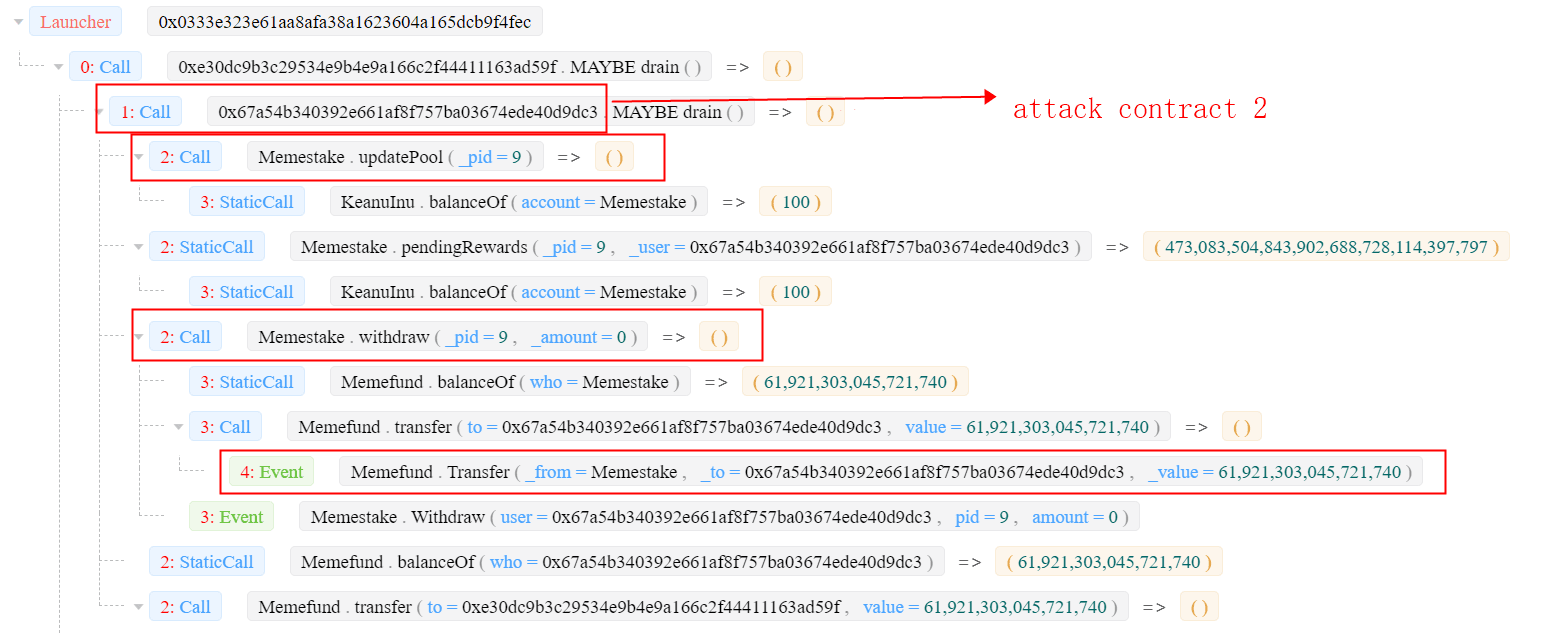
step 2 (manipulation): the attacker first borrows a large number of KEANU tokens using the flash loan (Towards A First Step to Understand Flash Loan and Its Applications in DeFi Ecosystem (SBC 2021)) from uniswapV2, and then deposits the tokens into/withdraws from the Memestake using the second smart contract created in step 1. Since the KEANU has a deflation mechanism, which burns 2% tokens for each transaction, the real number of tokens deposited into the Memestake is smaller than the value (
user.amount) maintained by the Memestake contract. The attacker repeats this process and makes the number of KEANU tokens inside the Memestake decrease to a small one (1e-07). See the transaction 0x00ed and the following figure.
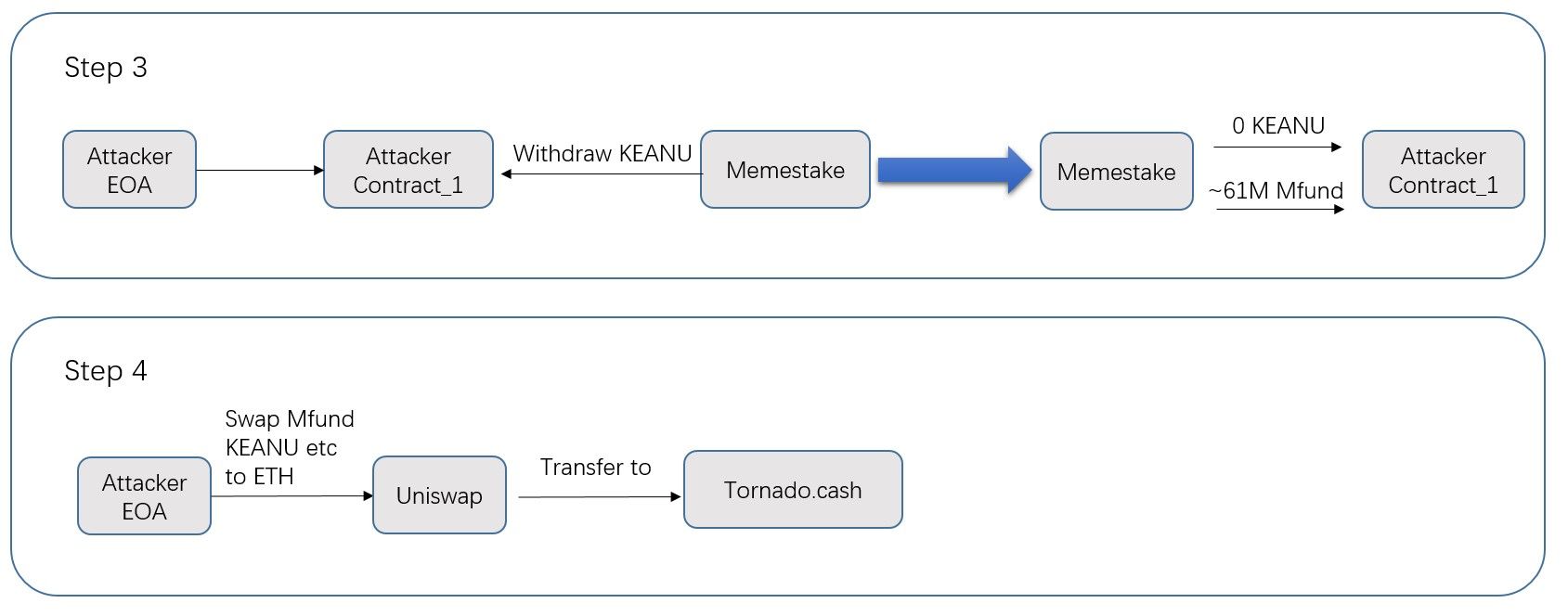
- Step 3 (making profit): The attacker invokes the
Memestake.updatePool()to update theaccMfundPerShare. This value relies on the number of KEANU tokens (which was manipulated in the second step.) Then the attacker obtains a large number of Mfund(~61M). See the transaction 0xa945 for more details.
- Step 4 (swapping to WETH): The attacker swaps the MFund and KEANU to WETH and launder the money through Tornado.Cash. The attacker gained 55.9484578158357 ETH as profits.
MISC
Interestingly, the second/third step of the attack is related to Flashbots. The second step buys KEANU with 38 ETH (0x00ed). This transaction is attacked by a sandwidth attack (through Flashbots) -- which makes the attacker himself a victim of a sandwidth attack. The third step (0xa945) sells MFund in uniswap, which creates an arbitrage opportunity that was captured by a Flashbots searcher.
About BlockSec
BlockSec is a pioneering blockchain security company established in 2021 by a group of globally distinguished security experts. The company is committed to enhancing security and usability for the emerging Web3 world in order to facilitate its mass adoption. To this end, BlockSec provides smart contract and EVM chain security auditing services, the Phalcon platform for security development and blocking threats proactively, the MetaSleuth platform for fund tracking and investigation, and MetaDock extension for web3 builders surfing efficiently in the crypto world.
To date, the company has served over 300 esteemed clients such as MetaMask, Uniswap Foundation, Compound, Forta, and PancakeSwap, and received tens of millions of US dollars in two rounds of financing from preeminent investors, including Matrix Partners, Vitalbridge Capital, and Fenbushi Capital.
Official website: https://blocksec.com/
Official Twitter account: https://twitter.com/BlockSecTeam




