Case Background
At 2 PM UTC on October 23, the SHAR token made a dramatic debut, soaring from an opening price of $0.00056 to $0.05986, with its market capitalization skyrocketing from zero to $60 million within just one hour—an almost 100-fold increase. In the following hours, some negative news emerged about the SHAR team, alleging their involvement in KOL manipulation. Then SHAR’s price dropped to $0.02393 within the next three hours. Despite the negative news, many users believed it wouldn’t significantly affect the project, as several prominent KOLs continued to buy the tokens and expressed their optimism about SHAR’s future. From 6 PM to 8 PM, the token price gradually rebounded to $0.042.
At 9:26 PM UTC on October 23, a transaction initiated by address CHj3 swapped 500,000,000 SHAR (nearly 50% of the total supply) for 19,619 WSOL, nearly draining the liquidity pool. The swap caused SHAR’s price to plummet to $0.0013, with its market capitalization dropping to $3 million, all within a single minute. SHAR coin holders were hit with a rug pull.
Money Flow Analysis through MetaSleuth
Using MetaSleuth, we can clearly trace the flow of funds in this rug pull incident and uncover some valuable clues. Earlier between October 20 and October 22, the perpetrator (the entity who controls address CHj3) of this rug incident withdrew a total of 6045 SOL from four exchanges (Binance 2 2595sol, KuCoin 950sol, MEXC 1 580sol and OKX 1 1920sol) and distributed it across 14 addresses. All 14 of these addresses were controlled by the perpetrator, serving the dual purpose of artificially inflating the SHAR price and accumulating large amounts of SHAR prepared for the final dump. Below is the fund flow from the four exchanges to the 14 addresses.
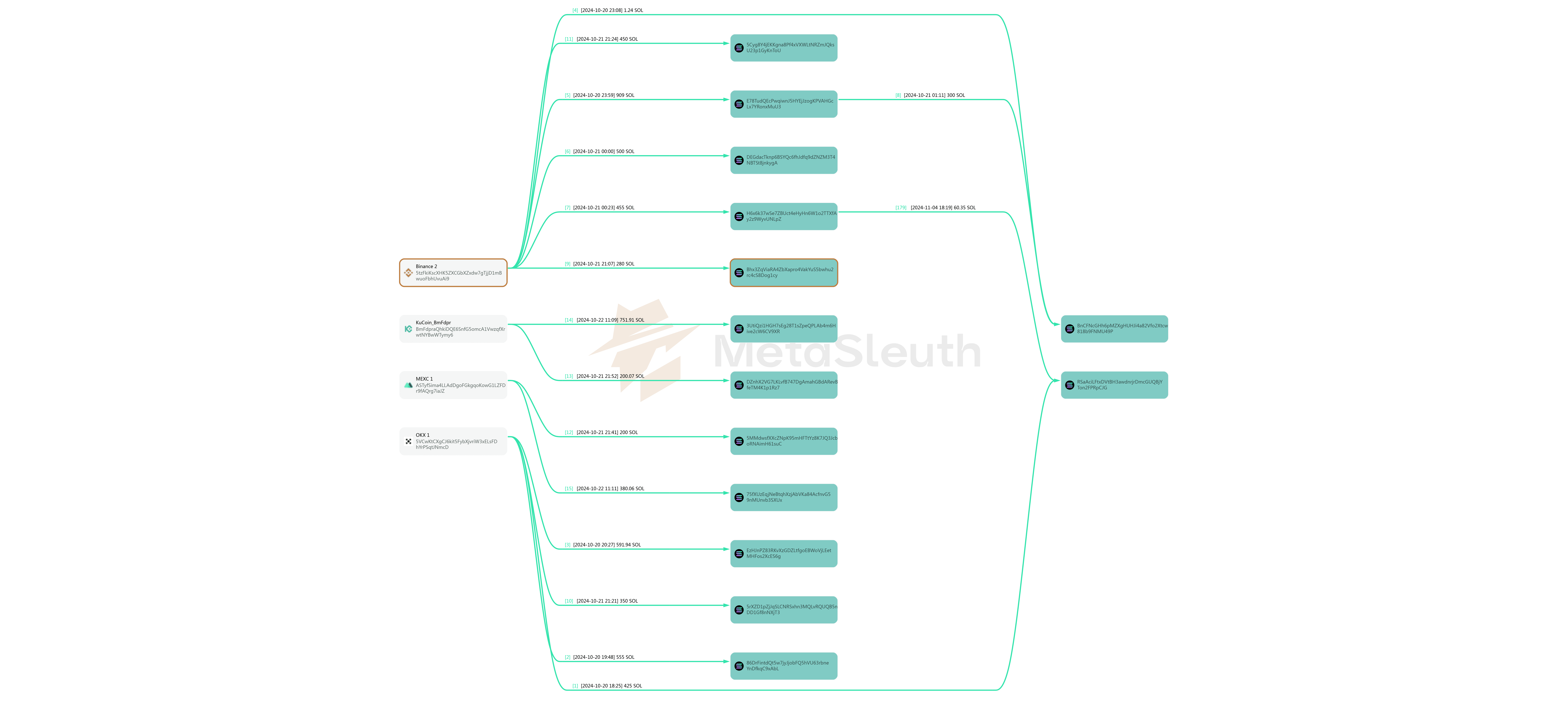
At 2 PM UTC on October 23rd, within two minutes of SHAR's launch, these 14 addresses swapped all of their held SOL for SHAR, injecting significant value into the liquidity pool and rapidly driving up the SHAR price. Here are some examples of the swap transactions (txs for buying SHAR): Q81H, 4Jxa, 5q5n, 3xvB. In the next half of an hour after acquiring SHAR, the perpetrator transferred all of the SHAR held by these 14 addresses to 104 other addresses under its control, further dispersing the tokens. Below is the asset flow graph showing distribution of SHAR, for 4 of the 14 addresses.
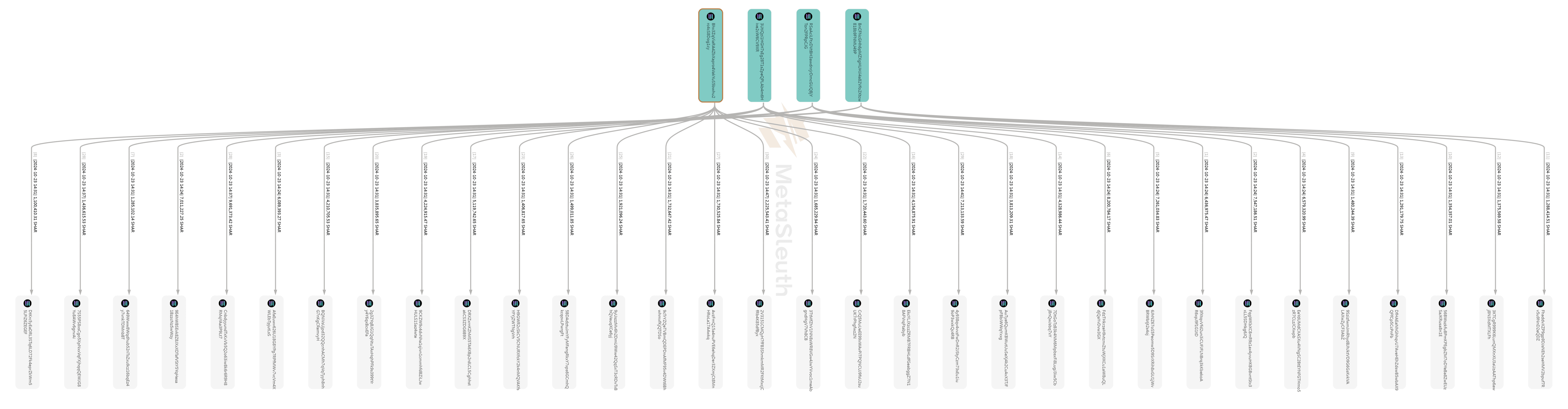
This dispersion strategy made it appear as though no single address held a large amount of SHAR on-chain, which helped reduce external concerns about the security of the SHAR asset. However, through analyzing the flow of funds, it becomes clear that although the large amount of SHAR was spread across numerous addresses, they were ultimately controlled by the same entity (the perpetrator). The perpetrator retained the ability to sell off all of these SHAR tokens at any time and drain the potential value from the pool, indicating that SHAR carries a significant security risk.
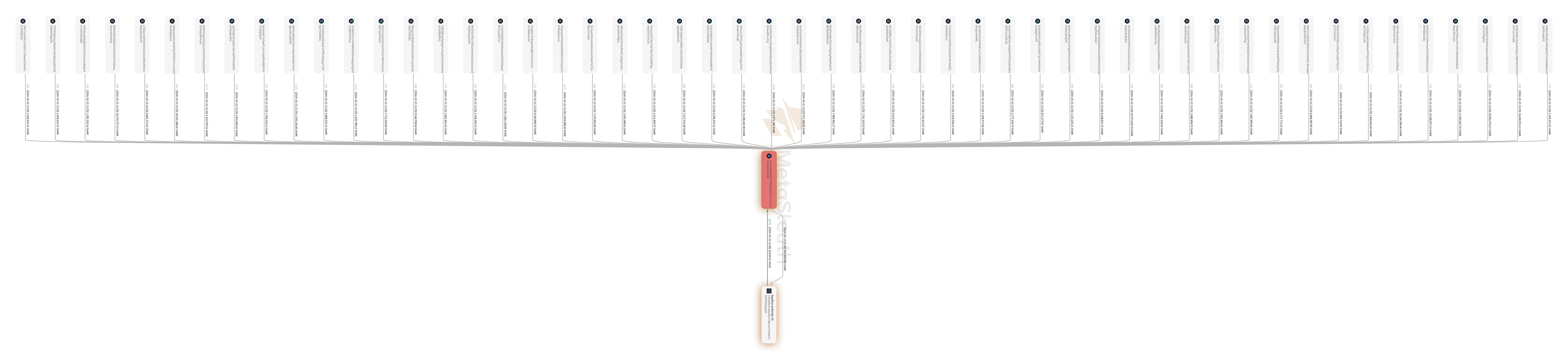
Finally, as the price of SHAR increased, the perpetrator seized what it believed to be the right opportunity. At 9:25 PM on October 23rd, the perpetrator simultaneously transferred all the SHAR coins from the 104 addresses it controlled and consolidated them into the address CHj3. One minute later, address CHj3 initiated a transaction, selling off the accumulated 500,000,000 SHAR tokens in one go. The liquidity pool was almost completely drained of SOL, and the perpetrator received 19,619 SOL tokens, worth approximately $4.2 million. At 9:26 PM on October 23rd, all users still holding SHAR became victims of the dump, as the value of the SHAR in their possession plummeted to one-tenth of its original value in just one minute. The following graph shows the SHAR coins being consolidated from 52 of the 104 addresses to address CHj3 and then being dumped to the pool.
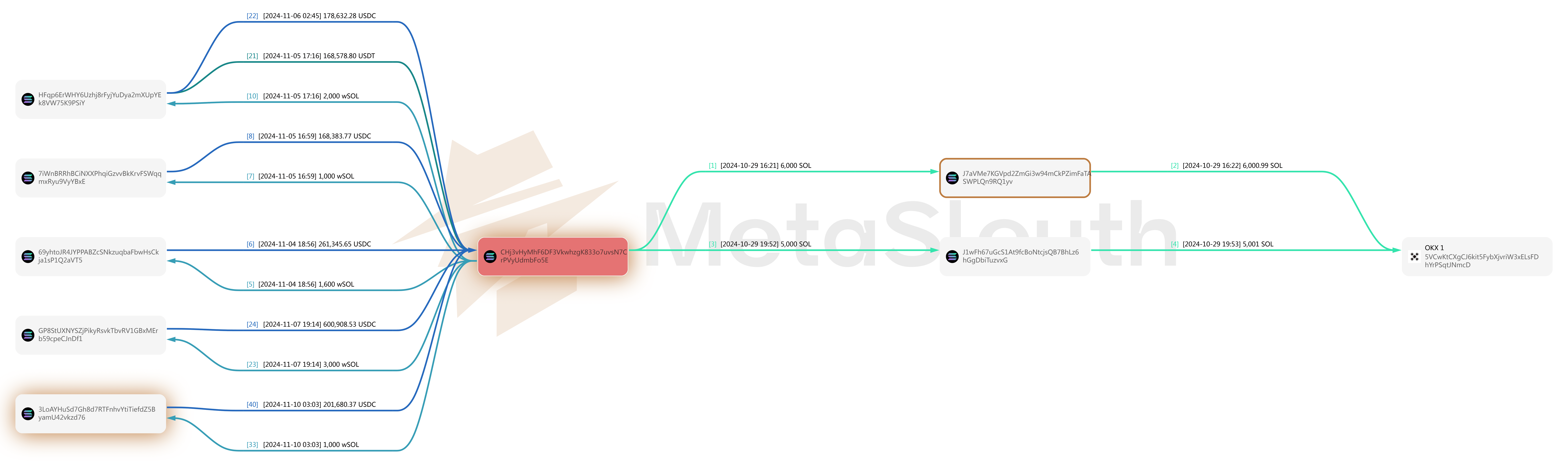
To trace how the perpetrator cashed out the ill-gotten gains, we continued to follow the movement of the 19,619 SOL. These 19,619 SOL remained in address CHj3 for nearly a week, until 4:21 PM on October 29th, when the perpetrator initiated two transactions ajqYwt and 3uD6Ys to transfer 6,000 SOL to another address J7aV under its control. Over the following 20 minutes, the perpetrator deposited the 6,000 SOL to the OKX exchange through two additional transactions 5STJND and 3z6C72. Then at 7:52 PM, another 5,000 SOL was transferred out to the address J1wF, and these SOLs were also sent to the OKX exchange at 7:53 PM. Then, between November 4th and November 10th, the perpetrator gradually swapped the remaining 8,600 SOL held in address CHj3 for USDC and USDT. We list all the swap transactions here: 2rGGMf, 5cWJte, 4AE6z7, 5HovYa, 4Da6zR, 5P9rmx, 5AAHn1, 5nm1Xy, Mn3Rxa. As of the time of writing, 8:30 AM UTC on November 14th, all of the 1.41M USDC and 168K USDT obtained through the swaps remain in address CHj3. And address CHj3 still holds approximately 19 SOL tokens that have not yet been swapped. This is the current disposition of the ill-gotten 19,619 SOL. The following graph illustrates the swaps on the left and deposits to OKX on the right.
Some of the Relevant Addresses and Transactions
The address responsible for the dump: CHj3vHyMhF6DF3VkwhzgK833o7uvsN7CrPVyUdmbFo5E.
14 addresses accumulating 500,000,000 SHAR at the beginning:
- E78TudQEcPwqiwnJ5HYEjJzogKPVAHGcLx7YRonxMuU3
- 5Cyg8Y4jEKKgna8Pf4xVXWLtNRZmJQksU23p1GyKnToU
- EzHJnPZ83RKvXzGDZLtfgoEBWoVjLEetMHFos2XcES6g
- 5rXZD1pZjJqSLCNRSxhn3MQLvRQUQB5nDD1Gf8nNXjT3
- 5MMdwsfXXcZNpK95mHFTtYz8K7JQ3JcboRNAimH61suC
- DZnhX2VG7LKLvfB747DgAmahGBdARevBfeTM4K1p1Rz7
- BnCFNcGHh6pMZXgHUHJi4a82Vfo2Xtcw818b9FNMU49P
- 75fXUzEqjNeBtqhXzjAbVKa84AcfnvG59nMUnvb3SXUx
- DEGdacTknp6BSYQc6fhJdfq9dZNZM3T4NBTSt8jnkygA
- H6x6k37wSe7ZBUct4eHyHn6W1o2TTXfAy2z9WyvUNLpZ
- Bhx3ZqViaRA4ZbXapro4VakYuS5bwhu2rc4cS8Dog1cy
- RSaAciLFtxDVtBH3awdnrjrDmcGUQBjYTon2FPRpCJG
- 3UtiQzi1HGH7sEg28T1sZpeQPLAb4m6Hive2cW6CV9XR
- 86DrFintdQt5w7jyJjobFQ5hVU63rbneYnDfkqC9xAbL
transaction depositing the ill-gotten gains to OKX1 (5VCwKtCXgCJ6kit5FybXjvriW3xELsFDhYrPSqtJNmcD):
- 5STJNDbQBMbigzHf6mzCrtiM6s8QJjpQazzu5j7zC61uBB46V9NkumCw8UwWHXg7YxpomAFN664PnxHYMAU353q2
- 3z6C72fm6VVGdkFW3VcpjTccq725ZuVWpcZJv3GM3DBp3D3oLVjq2nyaRDhNZbmG95fi9cTTZfZ8bT22rdXjdEfR
- 64wMUp3VFz7pxZEpZak9uXAPfbEMBDiTWUGZLgECLn8fSMPexuR5ifRqJTSTpe98ELzRG676Pfe9xoXmG9DreiG1
The Fund Flow Overview
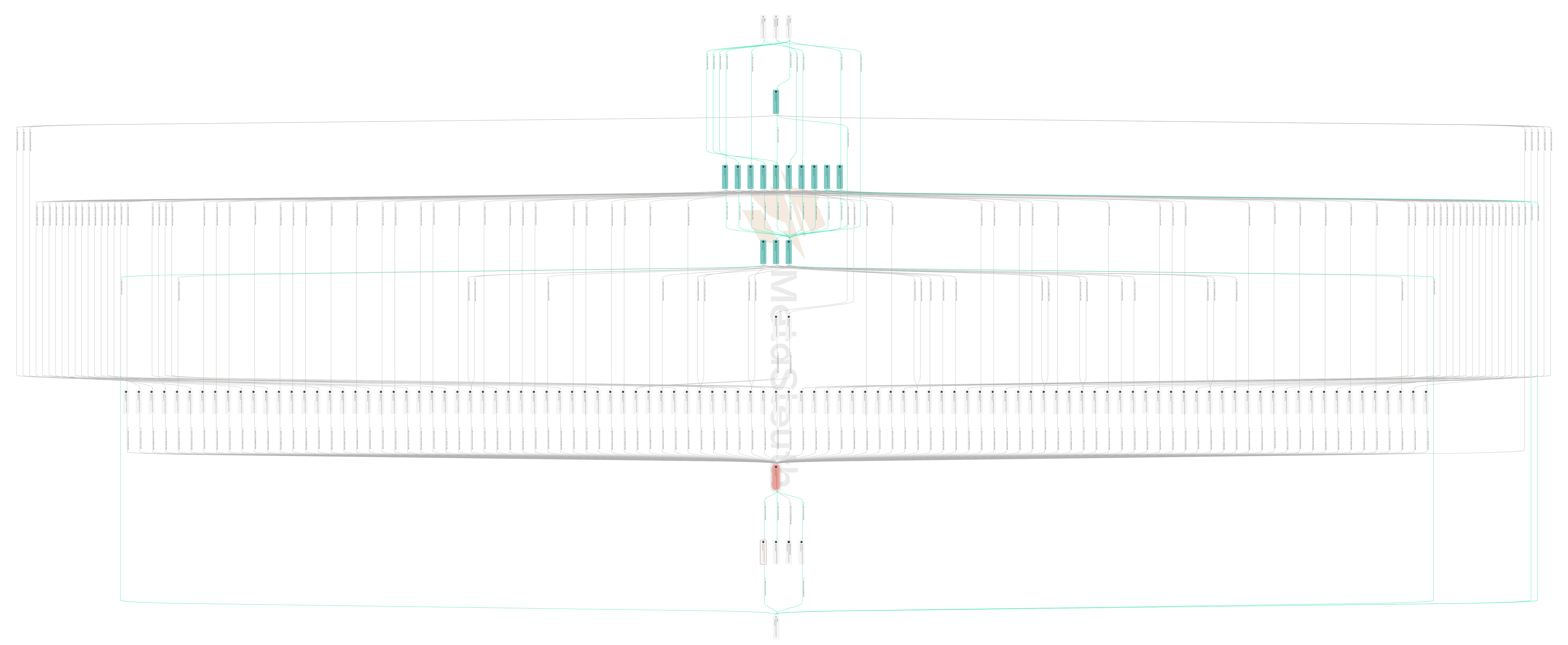
The 104 addresses controlled by the perpetrators to disperse SHAR, the transactions through which they gathered SOL from four exchanges for the dump, and other detailed fund flows can be explored in MetaSleuth. Explore more details and find out valuable clues now: https://metasleuth.io/result/solana/CHj3vHyMhF6DF3VkwhzgK833o7uvsN7CrPVyUdmbFo5E?source=5e4fca36-208b-4714-afb3-0800d5355323




