On May 8th, Peckshield reported a security incident about RariCapital. After careful investigation, we found that it's a type of price manipulation attack (indirect one) that was described in our paper: DeFiRanger: Detecting Price Manipulation Attacks on DeFi Applications. In the paper, we focus on the detection of two types of new attacks on DeFi apps, including direct and indirect price manipulation attacks. The former one means that an attacker directly manipulates the token price in DEX by performing an unwanted trade in the same DEX by attacking the vulnerable DeFi app. The latter one means that an attacker indirectly manipulates the token price of the vulnerable DeFi app. This security incident is one example of an indirect price manipulation attack.
Root Cause
We analyzed the root cause of the attack and found that the insecure price dependency is the reason. Specifically, the price of the LP token of Rari depends on the LP token value ibEth held by Rari (in Ether). Unfortunately, the ibEth LP token price can be manipulated by attackers invoking the work function of ibEth.
Rari_token_value_held_by_attacker = eth_reserve_in_Rari * Rari_token_number/Rari_token_total_supply
ibEth_token_value_held_by_Rari = eth_reserve_in_ibEth * ibEth_token_number/ibEth_token_total_supply
The eth_reserve_in_Rari is affected by ibEth_token_value_held_by_Rari, which is manipulated by the attacker through increasing the eth_reserve_in_ibEth (by invoking the work function.)
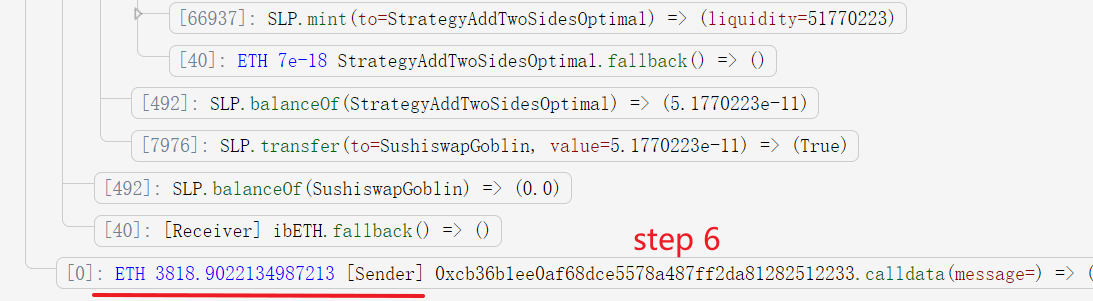
Using our system DefiRanger, we easily recover the DeFi semantics shown in the figure. The number of LP token in liquidity mining (deposit Ether to get LP token) and liquidity cancel (withdraw LP token to get Ether) is different (with the red circle) with the same number of Ether (with the green background).
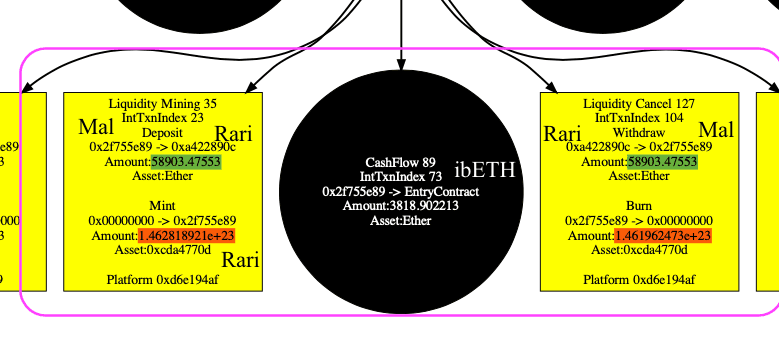
Attack Process
The attack process is shown in the following steps.
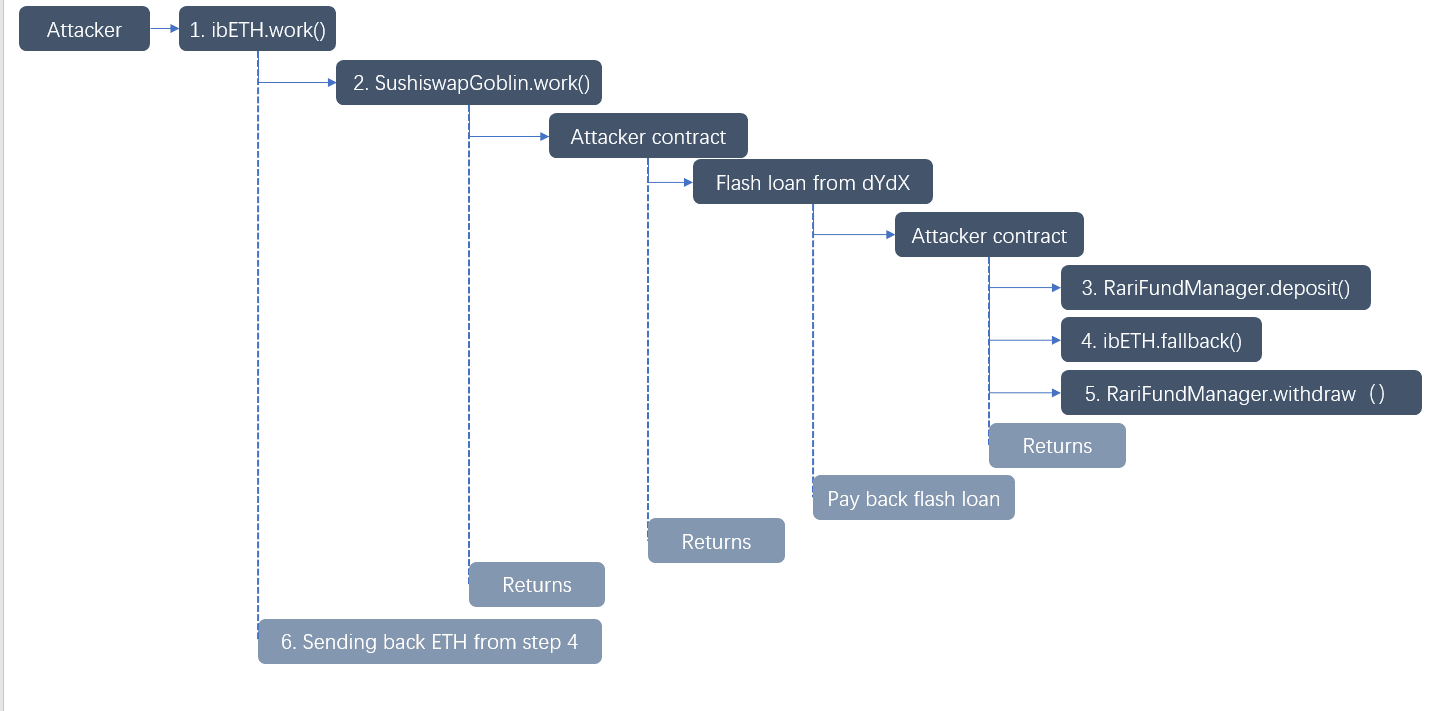
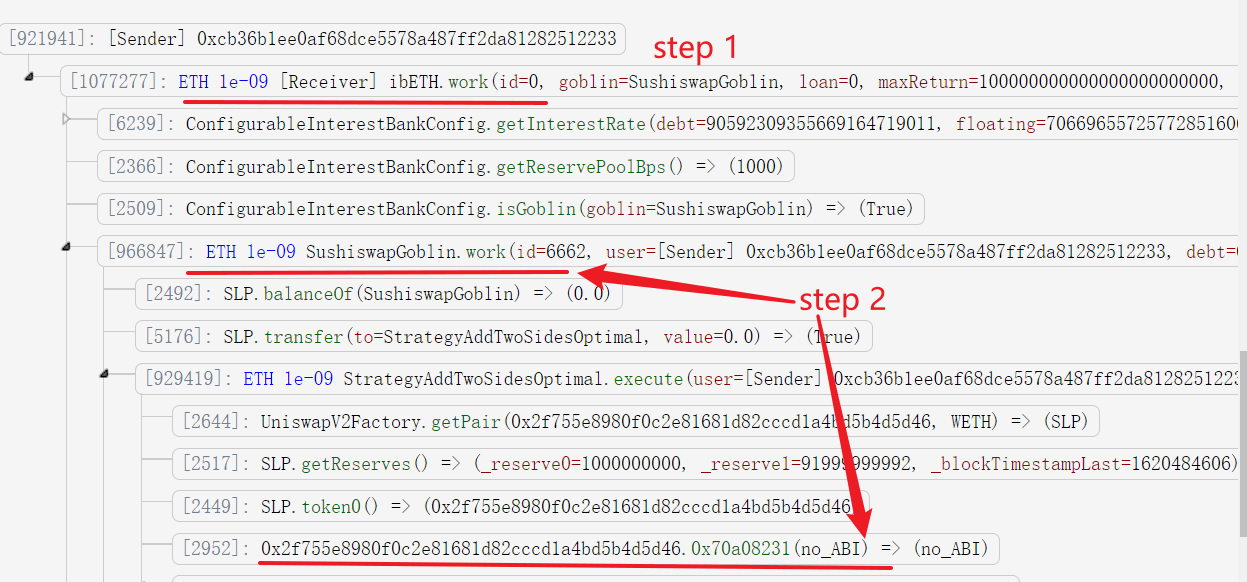
- The attacker invokes the
workfunction of ibEth. - This function invokes the
SushiswapGoblin.workfunction, which further invokes the attacker controlled contract (0x2f755e8980f0c2e81681d82cccd1a4bd5b4d5d46).
- The contract first deposits 58903.4755276693 Ether (borrowed from flash loan) into Rari and obtains the LP token of Rari (146281892117489076580650).
- The attacker transfers 3818.9022134987213 Ether into ibEth. This is the critical step, that will raise the price of the LP token of ibEth (without affecting its total supply). This further affects the LP token price of Rari. That's because the total Ether reserve in Rari's pool increases due to the raised price of ibEth LP token it holds. Note that, the attacker cannot manipulate the token price of Rari or ibEth by adding liquidity, since this will also increase the total supply of the token.
- The attacker withdraws the Ether. Since the Rari token's price is higher, the attacker can use less Rari LP token (146196247321127203315331 instead of 146281892117489076580650) to get the same number of Ether to return the flash loan.
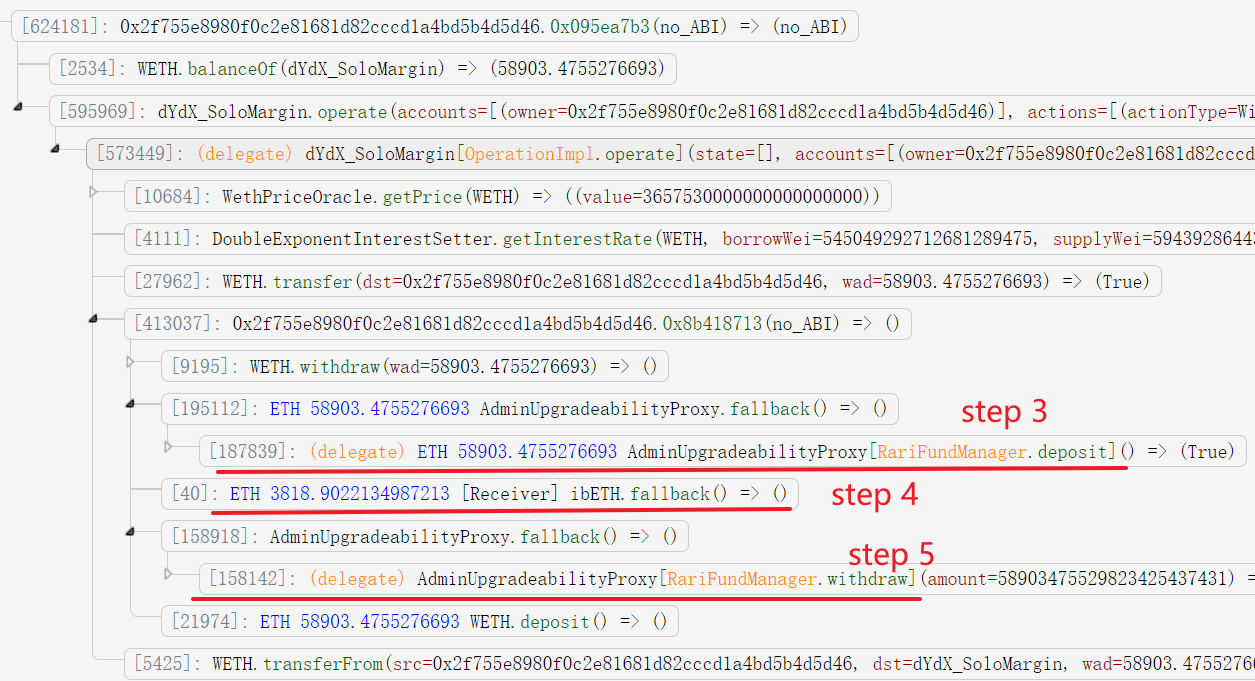
- The attacker obtains the returned Ether at the end of the
workfunction.
Summary
In conclusion, the security breach faced by RariCapital is a stark reminder of the sophisticated threats looming over DeFi applications. Through a clever exploitation strategy, attackers performed an indirect price manipulation attack. The incident has unveiled critical vulnerabilities associated with the use of insecure price dependencies in smart contracts. This attack highlights the urgent need for DeFi projects to adopt robust detection systems like DeFiRanger to safeguard against both direct and indirect manipulation tactics that threaten the integrity and security of the burgeoning DeFi ecosystem.
About BlockSec
BlockSec is a pioneering blockchain security company established in 2021 by a group of globally distinguished security experts. The company is committed to enhancing security and usability for the emerging Web3 world in order to facilitate its mass adoption. To this end, BlockSec provides smart contract and EVM chain security auditing services, the Phalcon platform for security development and blocking threats proactively, the MetaSleuth platform for fund tracking and investigation, and MetaDock extension for web3 builders surfing efficiently in the crypto world.
To date, the company has served over 300 esteemed clients such as MetaMask, Uniswap Foundation, Compound, Forta, and PancakeSwap, and received tens of millions of US dollars in two rounds of financing from preeminent investors, including Matrix Partners, Vitalbridge Capital, and Fenbushi Capital.
Official website: https://blocksec.com/
Official Twitter account: https://twitter.com/BlockSecTeam




