The research has been accepted at SIGMETRICS 2025, a premier computer science conference, and we've open-sourced our dataset at https://github.com/blocksecteam/phishing_contract_sigmetrics25.
Since the rise of Decentralized Finance (DeFi), the blockchain space has drawn significant capital and user investment. However, this growth has been accompanied by a surge in phishing attacks, leading to substantial user losses. To avoid detection, scammers are no longer relying solely on Externally Owned Accounts (EOAs). Instead, they've shifted toward deploying smart contracts. In this article, we present our latest research on phishing contracts and demonstrate how our timely, comprehensive, and accurate phishing intelligence helps crypto projects safeguard user funds and maintain compliance.
Key Features of Phishing Contracts
Traditionally, scammers lured users into signing transactions that send ETH or tokens directly to their EOAs. But that tactic has become easy to spot: wallets like MetaMask and Coinbase now warn users against sending funds to known malicious EOAs.
In response, scammers now use phishing contracts to mimic legitimate project behavior and obfuscate intent. Instead of transferring assets directly to an attacker's EOA, victims are tricked into signing transactions that interact with malicious contracts, effectively handing over control of their tokens without realizing it.
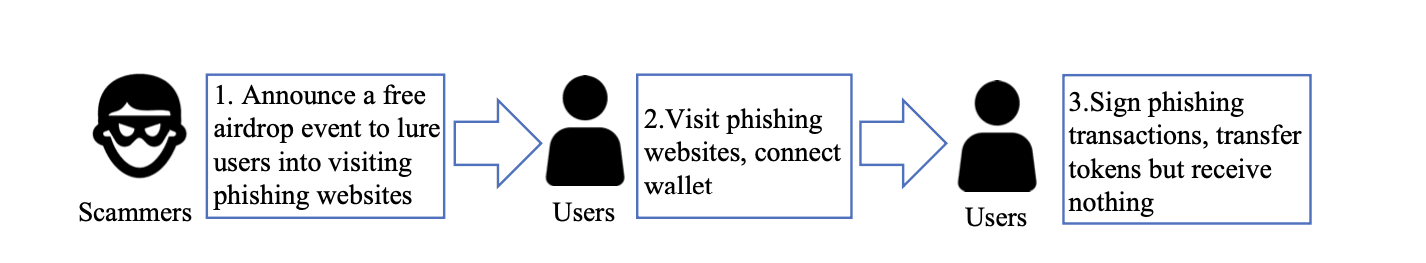
These phishing contracts often contain:
- Deceptive payable functions, named like Claim or SecurityUpdate, that trick users into sending ETH.
- Multicall functions, designed to batch multiple token transfers into a single transaction—ideal for draining ERC20 tokens or NFTs after a user unknowingly grants approval.
Detection of Phishing Contracts
This study focuses on phishing contracts on Ethereum. To enable large-scale phishing contract detection, we have designed a system that extracts suspicious function selectors from contract bytecode, simulates transactions, and analyzes the outcomes. Using this approach, we identified 37,654 phishing contracts deployed between December 29, 2022, and January 1, 2025.
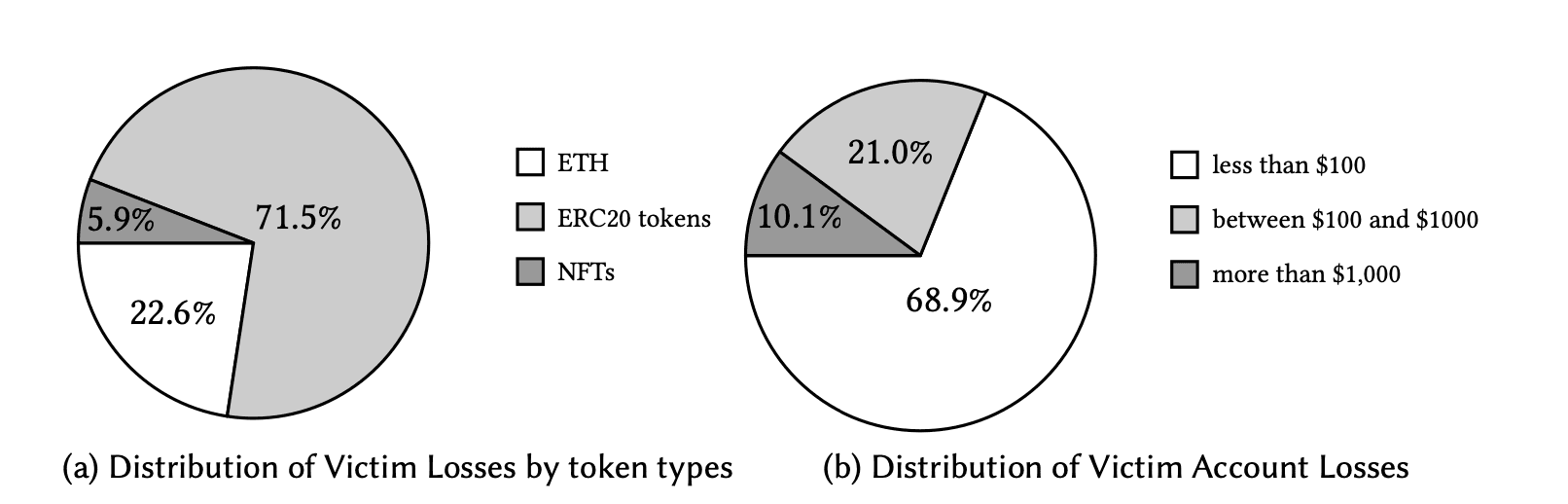
Distribution of User Losses
Phishing contracts have led to substantial user losses. From December 29, 2022, to January 8, 2025, we discovered 211,319 phishing transactions affecting 171,984 victims, with total losses reaching $190.7 million. Notably, 89.9% of victims lost less than $1,000. Many users fell for phishing schemes multiple times, often due to unrevoked token approvals or repeatedly signing malicious transactions. Among them, less experienced Web3 users are especially vulnerable.
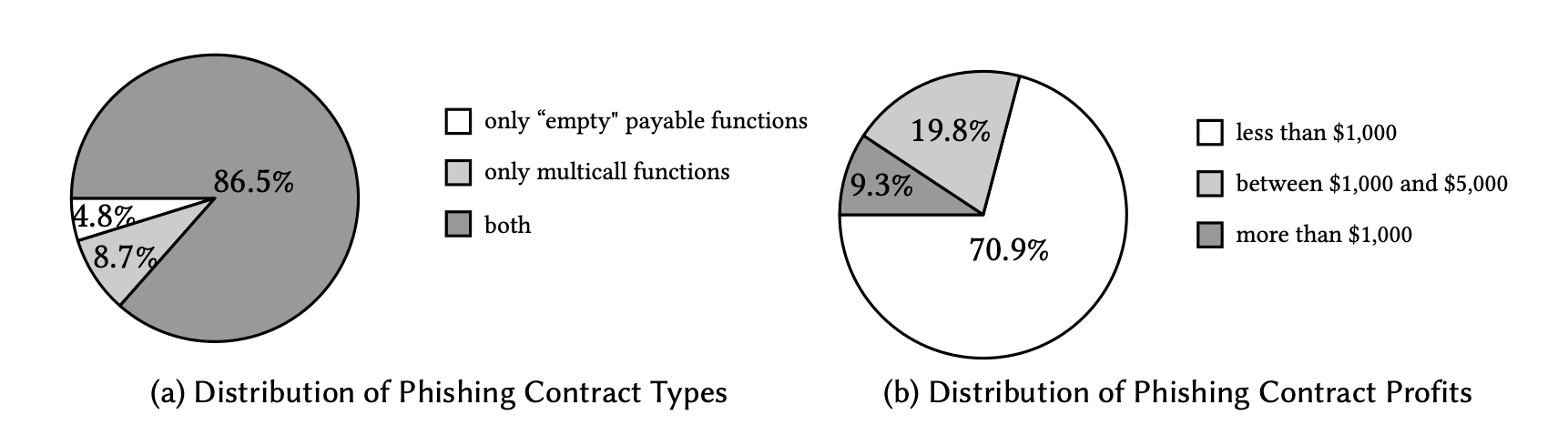
Distribution of Phishing Contracts
Most phishing contracts (86.5%) have both "empty" payable functions and multicall functions to target various token types. 70.9% of them earned less than $1,000, and 96.2% remained active for less than one day. Scammers rapidly deploy new contracts to bypass account labeling mechanisms.
Distribution of Contract Deployers
Nine accounts deploy 91.1% of all phishing contracts. Scammers often use tokens stolen from victims to fund the deployment of new phishing contracts. Notably, eight of these nine major deployers show fund flow connections, suggesting they operate as a coordinated phishing group. Together, they have deployed 85.7% of all phishing contracts.
Mitigation Methods of Phishing Contracts
Our work reveals the widespread prevalence of phishing contracts on Ethereum and the significant losses they have caused to users. Hence, we propose practical and effective strategies to protect users from these threats.
What Can Users Do
User perspective. When accessing a decentralized application and requesting services, users should closely inspect the website, including the URL, main page, sublinks, Twitter, and Discord links. Before signing a transaction, users should carefully review the transaction details, including the account and function call parameters. Additionally, they can verify the address label on Etherscan to determine if it is an official account.
What Can Service Providers Do
Service providers—including CEXs, DEXs, wallets, wallets, PayFi platforms, stablecoins, and bridges—should actively maintain and update lists of phishing websites and accounts to protect users from potential threats. When certain accounts are identified as deploying phishing contracts on their platforms, these providers should restrict or deny access to their services. However, the inherent anonymity of blockchains and the complexity of on-chain interactions—especially in cross-chain activities—pose significant challenges for institutions in conducting effective risk assessments.
To address these challenges, we have integrated these research findings into the Phalcon Compliance APP. This platform leverages a massive, real-time database with over 400 million address labels, unlimited transaction hop tracing, and an AI-powered behavioral analysis engine. With these capabilities, the APP enables institutions to quickly identify phishing addresses and suspicious entities interacting with them.
Beyond phishing addresses, the Phalcon Compliance APP also detects other risky entities, such as attackers, sanctioned entities, mixers, money launderers, and dark webs, as well as suspicious behaviors like high-frequency transfers, large transfers, and transit addresses. When illegal activities are detected, the APP promptly notifies institutions through seven different channels, ensuring they can respond immediately. Besides, the APP offers a range of features, including task delegation, comment addition, blacklisting, and one-click generation of Suspicious Transaction Reports (STRs). Together, these tools provide a comprehensive solution for identifying and mitigating risks while simplifying compliance workflows.
🔥 Experience It Today!
Don't miss out—book a product demo of Phalcon Compliance APP now! Schedule your demo in just 10 seconds. The first 30 users to book will receive a limited-time free trial!
🔗 Book a Demo: https://blocksec.com/book-demo




