In 2023:
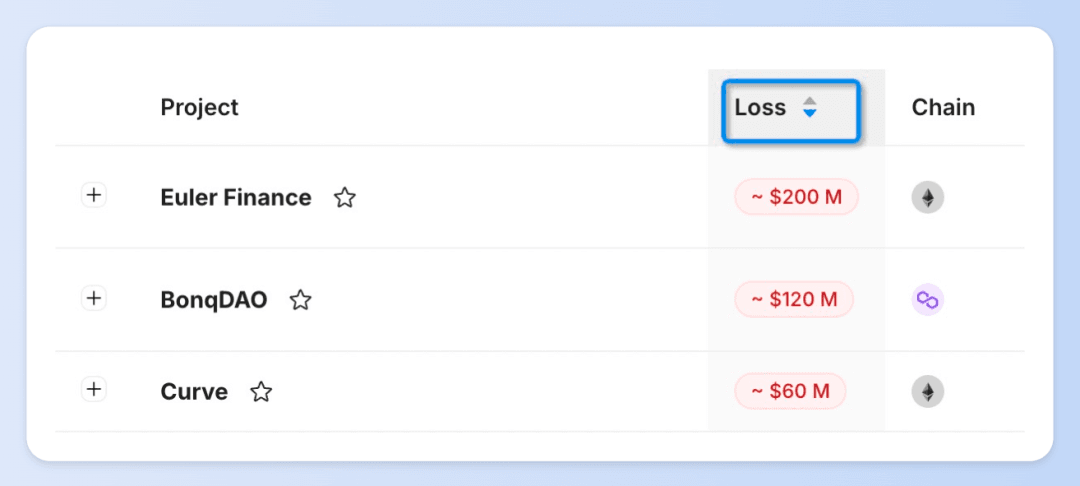
The Web3 space was rocked by a significant hack incident where Euler Finance was compromised, leading to nearly $200 million in asset losses—the most substantial financial impact recorded for the year.
The most common attack vector stemmed from business logic flaws, which accounted for 15 incidents with each incurring losses over $80,000, including notable hacks on Euler Finance and Platypus.
Precision loss emerged as a new type of exploited vulnerability, with the KyberSwap incident leading to approximately $46 million in losses due to precision loss during tick calculations.
As the Web3 ecosystem continues its rapid expansion, the lure of vast profits has led to an increase in hacking incidents. To combat this, Phalcon has introduced a "Security Incidents" dashboard that allows users to systematically track the latest security incidents.
You can click here to access the dashboard, or visit the homepage of our website, and then choose "Explore Transactions" to find this dashboard.

A Closer Look at 2023's Hacks and Their Exploits
You might be wondering: Isn't the Mixin Network incident the largest hack in 2023?
Indeed, that was significant, but our list focuses on hacks resulting from vulnerability exploits. Losses due to rug pulls, poor private key management, and other factors are not included in our statistics.
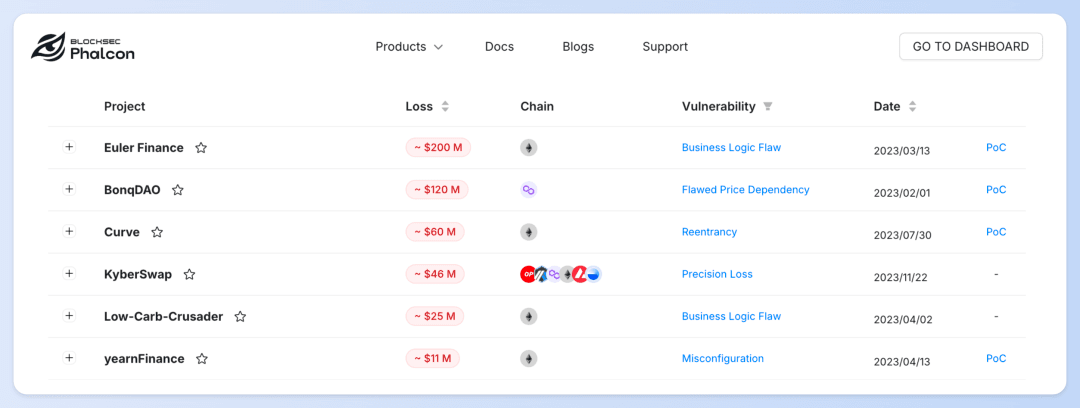
In Phalcon's "Security Incident" dashboard, we've compiled nearly 70 hacking incidents from 2023 resulting from vulnerability exploits, each with losses exceeding $100,000.
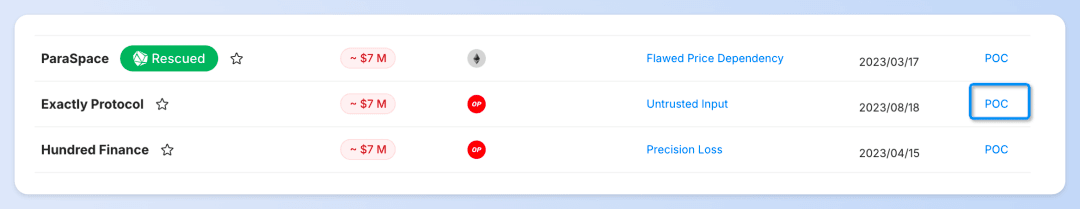
Take the Exactly Protocol Incident as an example:
You can learn about basic information such as the assets lost, the blockchain where the attack occurred, and the timing of the attack.
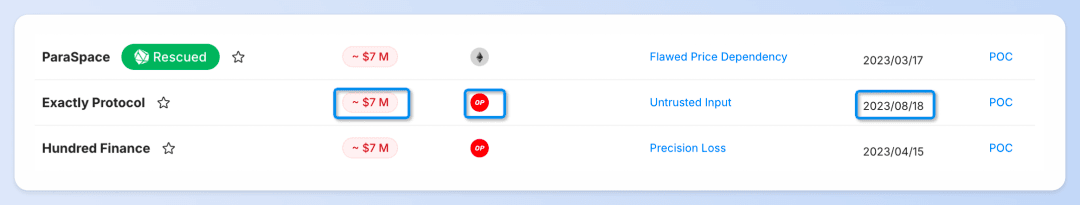
We also show the exploited vulnerability types for each incident, with a click-through option for in-depth root cause analysis. These analyses are provided by our dedicated security experts, who are consistently present to furnish the community with critical insights as soon as security incidents occur.
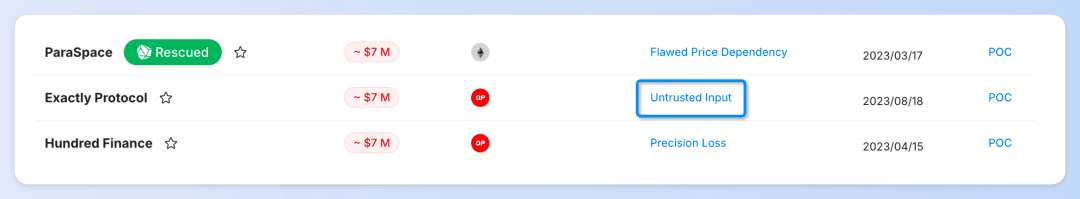
Additionally, this section includes PoC (proof of concept) codes compiled by our partner, DeFiHackLabs.
You can use Phalcon Fork to debug the PoC (Proof of Concept) code of security incidents and share the PoC code and transactions with the community.
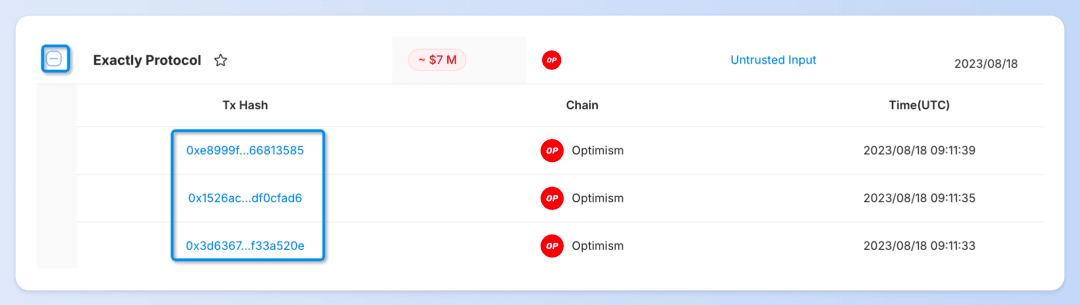
Click the ➕ next to the protocol name to expand and view each specific attack transaction. A simple click on the transaction hash allows you to examine the transaction's flow of funds, balance changes, and invocation flow via Phalcon Explorer.
Information ➔ Insight
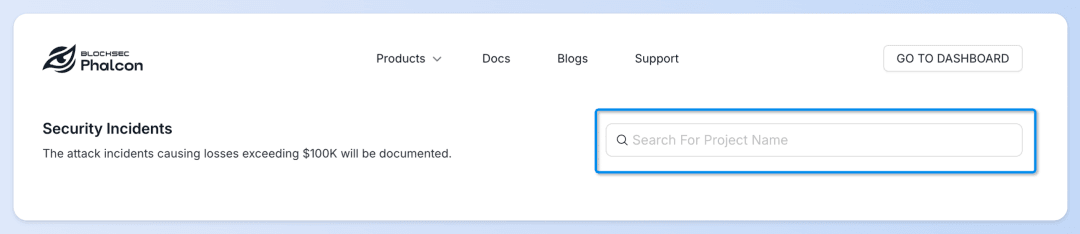
📌 Want to know about attack incidents related to a specific protocol?
👉 Type the [protocol name] in the search box for instant results.
📌 Curious about the most critical attack incidents of 2023?
👉 Choose [Loss - Descending] to quickly identify security incidents with the most significant losses.
📌 Interested in the trend of attack incidents in 2023?
👉 Select [Date - Ascending] to track how attack frequencies and methodologies evolved throughout the year.

📌 Looking for attack incidents caused by a specific type of vulnerability?
👉 Use the filter to select the [vulnerability type] to quickly locate relevant incidents.
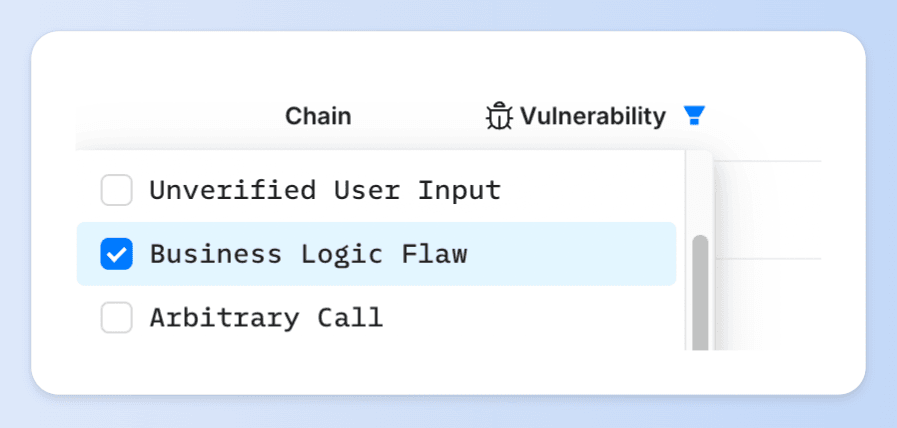
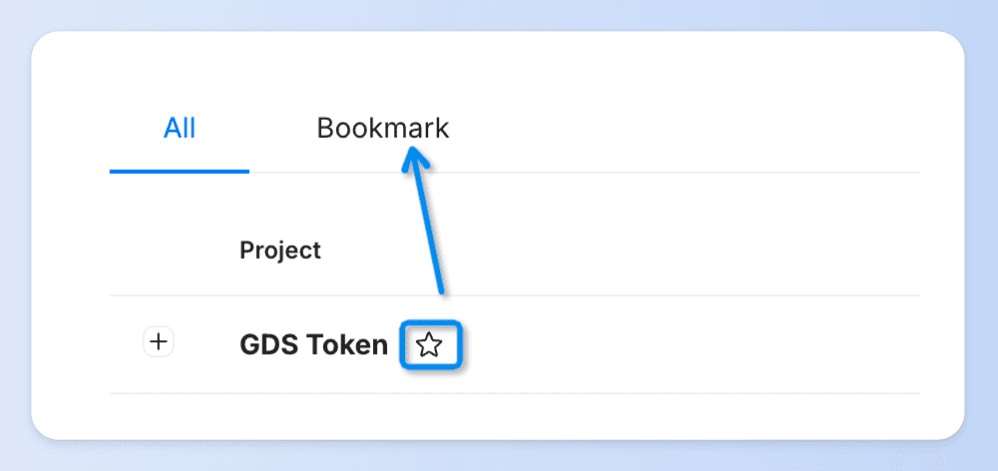
📌 If you want to compare and analyze multiple attack incidents
👉 Click on ⭐️ to bookmark the incident for easy reference later.
Start Exploring Now
Phalcon's "Security Incidents" dashboard not only provides Web3 security information to general users but also offers a platform for security researchers and developers to learn and review. By analyzing actual attack techniques and understanding how hackers exploit vulnerabilities, they can better identify and reinforce potential weak spots in their systems.
We'll keep our data up-to-date, ensuring you have access to the most recent hacking incident information and insights.
Explore Phalcon's "Security Incidents" dashboard now, and join us in building a more secure Web3 world.




