Introduction
On June 16th, 2022, Inverse Finance was attacked, leading to the loss of more than 1M. The attack transaction is https://versatile.blocksecteam.com/tx/eth/0x958236266991bc3fe3b77feaacea120f172c0708ad01c7a715b255f218f9313c. The root cause is that the price oracle utilized by Inverse Finance has been manipulated.
Attack Analysis
The attacker burrowed 27,000 WBTCs from Aave with flashloan first. After that, 225 of them were deposited into Curve and 5,375 crv3crypto was minted. The attacker deposited the 5,375 crv3crypto into the yvCurve-3Crypto and got 4,906 Yearn cToken, which will be used as the collateral in Inverse Finance.
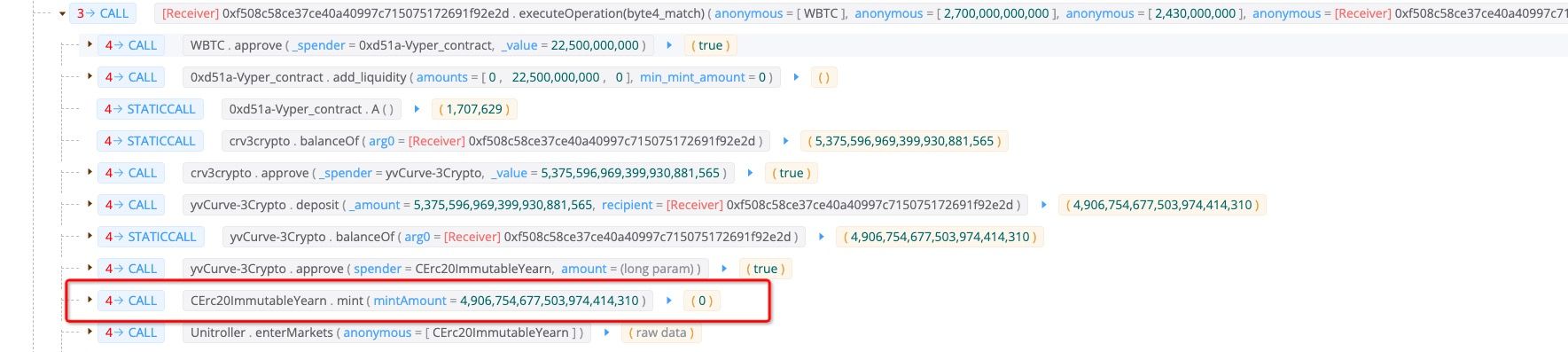
The remaining 26,775 WBTC is used to manipulate the price of the collateral. The attacker swapped 26,775 WBTC and got 75,403,376 USDT back. The swap lift the price of the oracle from 979 to 2,831.

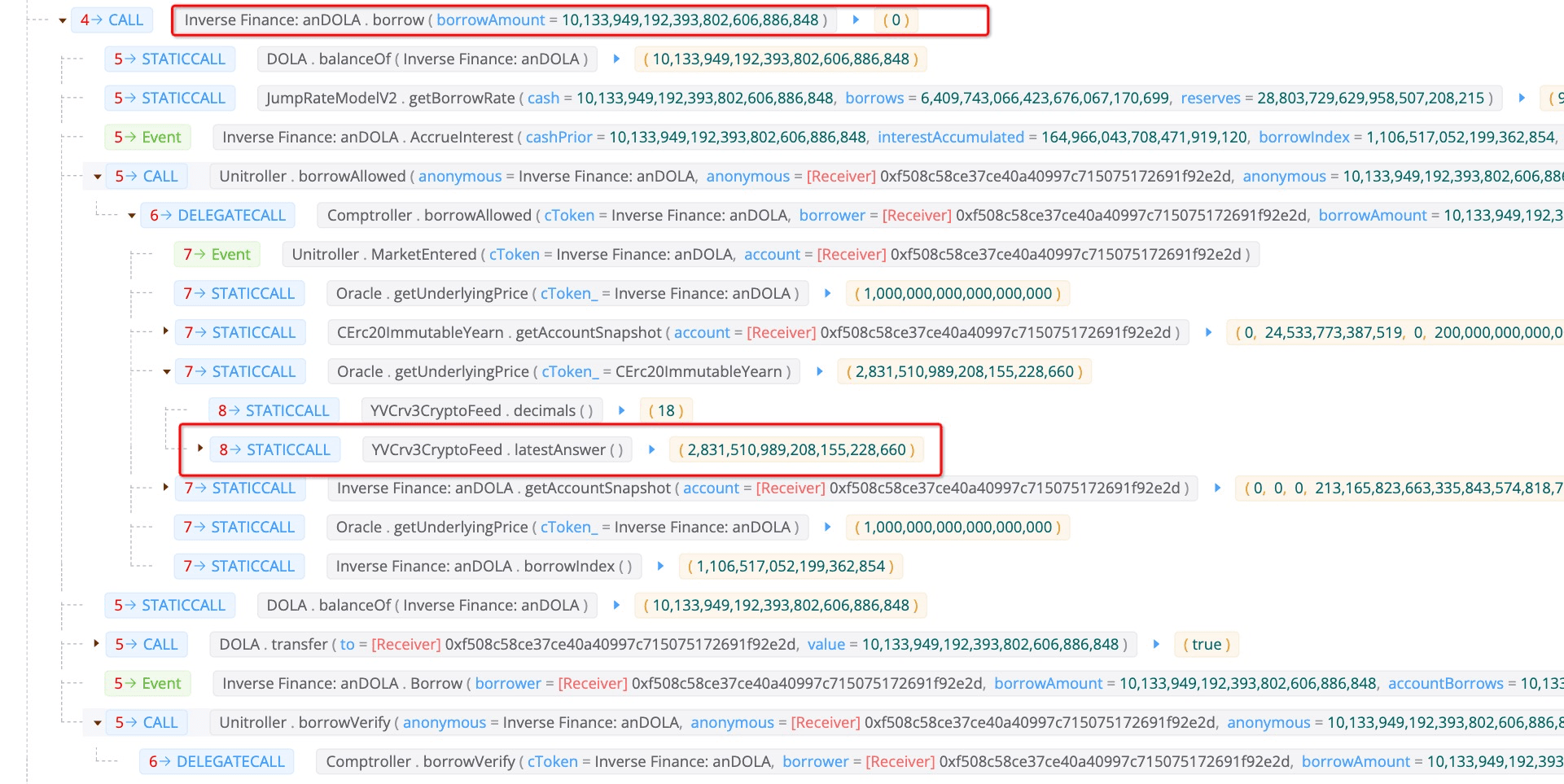
As we can see from the function borrowAllowed, it will check whether the user can borrow the specified amount of tokens with the deposited collaterals.
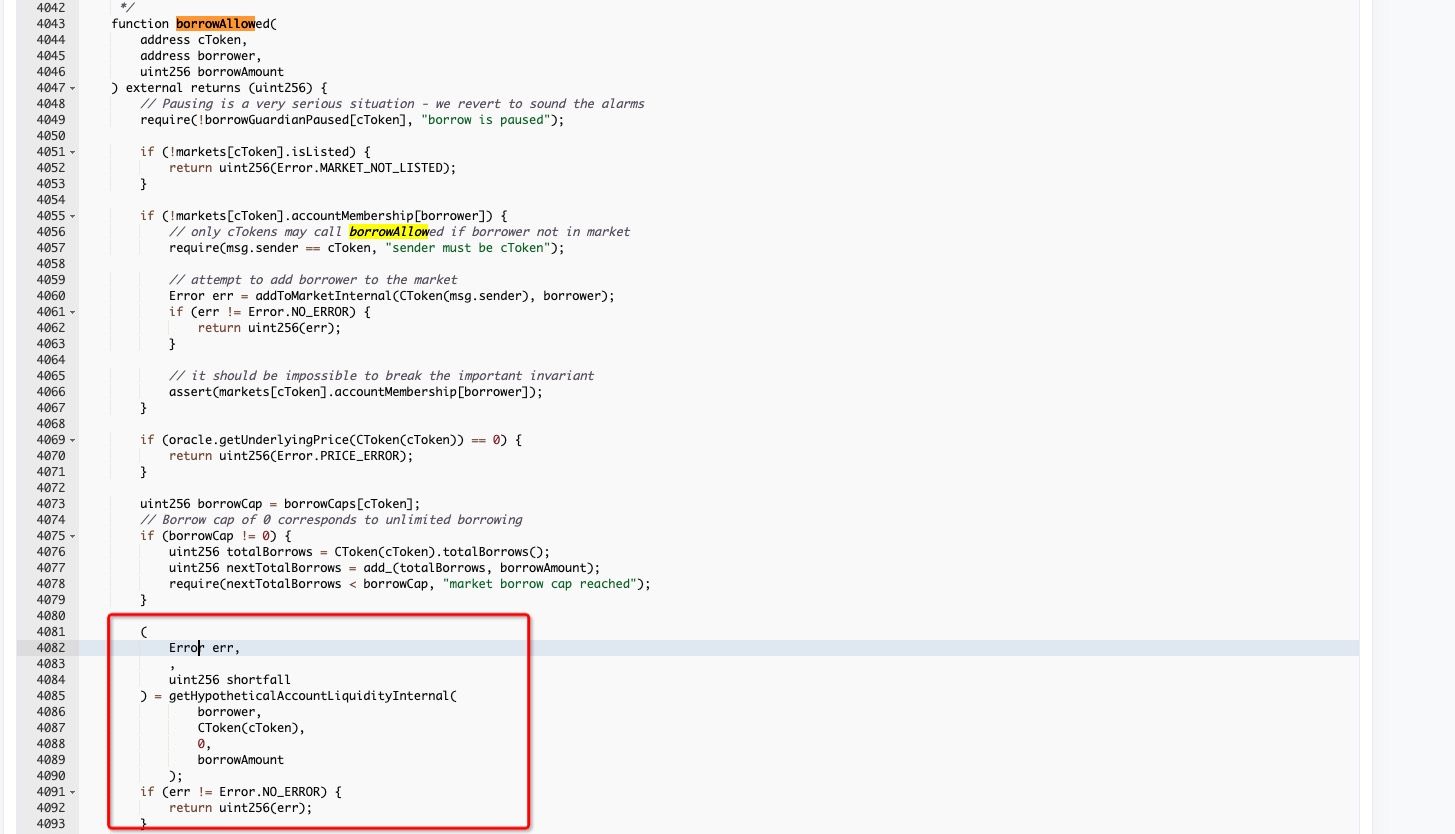
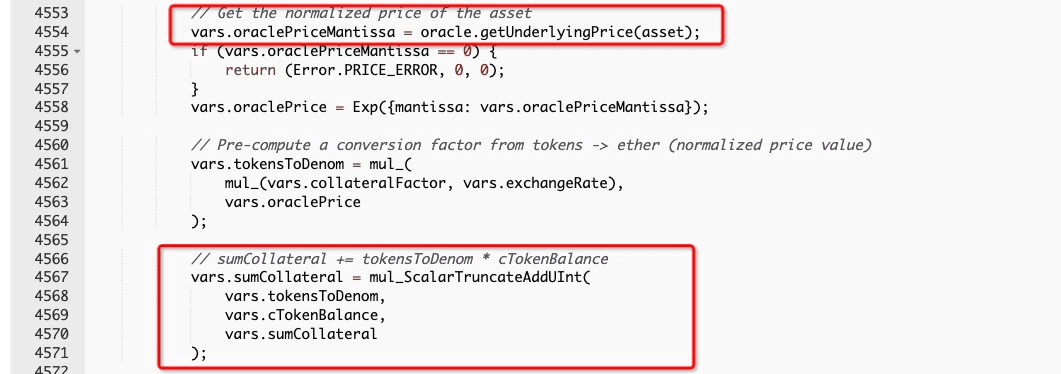
Specifically, function getHypotheticalAccountLiquidityInternal will be used to check whether the borrow behavior is safe. The price of the collateral is obtained with getUnderlyingPrice
Function getUnderlyingPrice invokes function latestAnswer to get the result. As mentioned before, the 26,775 WBTC is used to swap the USDT, resulting in the lifting of collateral price.
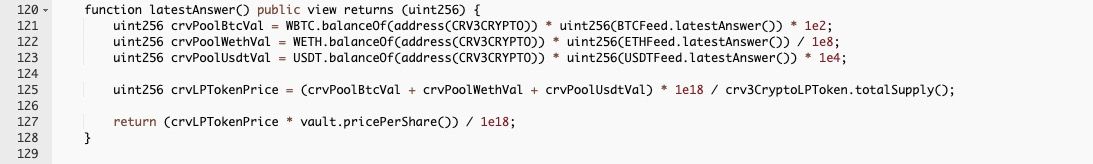
In this case, the attacker can borrow a large amount of (i.e., 10,133,949) DOLA, whose value is more than the deposited collateral.
Finally, the attacker swapped the 75,403,376 USDT back to 2,662,649 WBTC, and swapped the burrowed 10,133,949 DOLA to 9,881,355 3Crv, which is further removed from the liquidity pool to get 10,099,976 USDT.
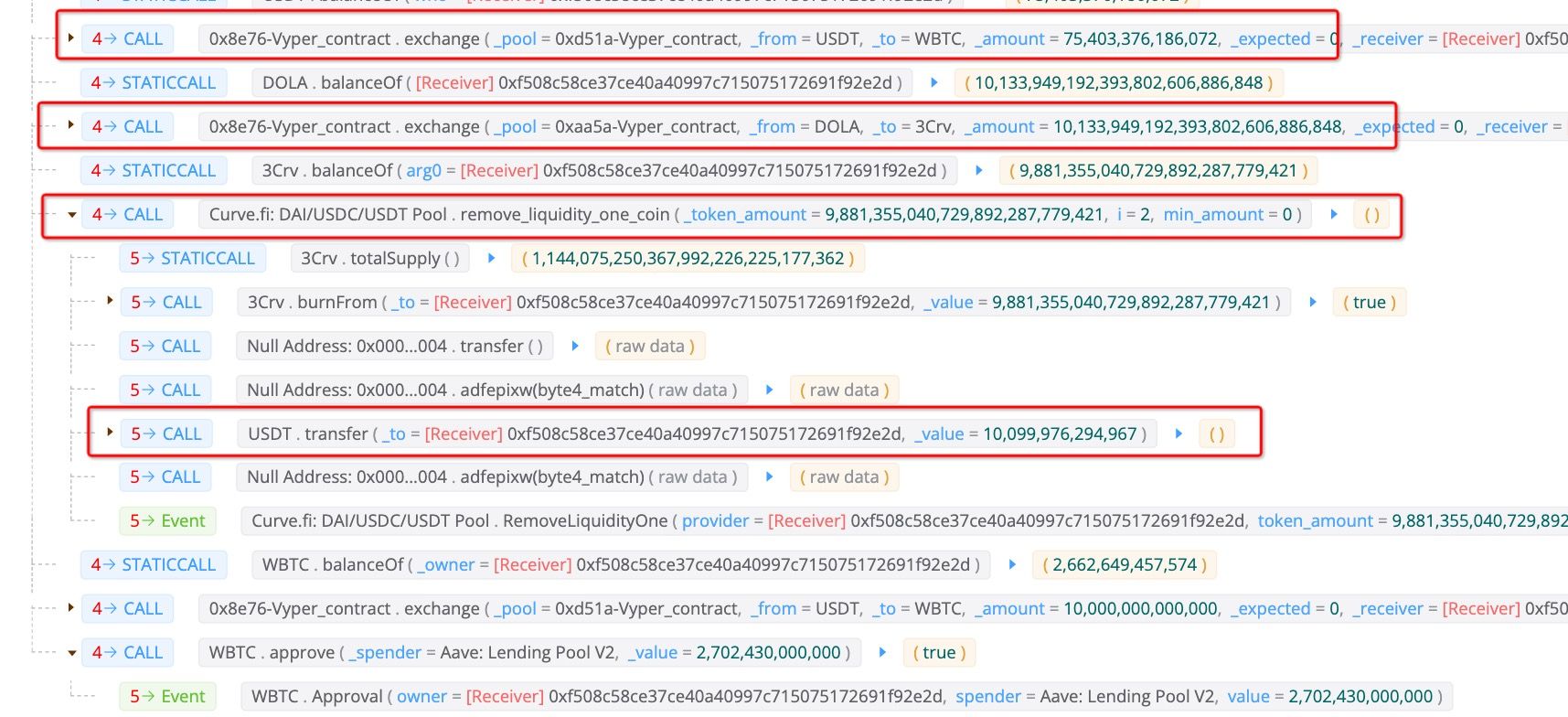
Then, 10,000,000 of the 10,099,976 USDT was swapped to WBTC again and used to repay the flashloan. Now the attack is completed. The attacker earns 99,976 USDT and 53.2 WBTC from this attack.

Summary
This is a traditional price manipulation attack. We are surprised that why such an attack can happen nowadays, this incident serves as a wake-up call for DeFi protocols to reinforce their security systems.
About BlockSec
BlockSec is a pioneering blockchain security company established in 2021 by a group of globally distinguished security experts. The company is committed to enhancing security and usability for the emerging Web3 world in order to facilitate its mass adoption. To this end, BlockSec provides smart contract and EVM chain security auditing services, the Phalcon platform for security development and blocking threats proactively, the MetaSleuth platform for fund tracking and investigation, and MetaDock extension for web3 builders surfing efficiently in the crypto world.
To date, the company has served over 300 esteemed clients such as MetaMask, Uniswap Foundation, Compound, Forta, and PancakeSwap, and received tens of millions of US dollars in two rounds of financing from preeminent investors, including Matrix Partners, Vitalbridge Capital, and Fenbushi Capital.
Official website: https://blocksec.com/
Official Twitter account: https://twitter.com/BlockSecTeam




