The Wintermute has been exploited for more than 160M loss. The root cause is that the private key of the Wintermute project was compromised due to a vulnerability in the Profanity tool, which was used by Wintermute to generate the private key and the Ethereum account.
In this blog, we will describe the root cause of the vulnerability in Profanity and how the vulnerability can be exploited.
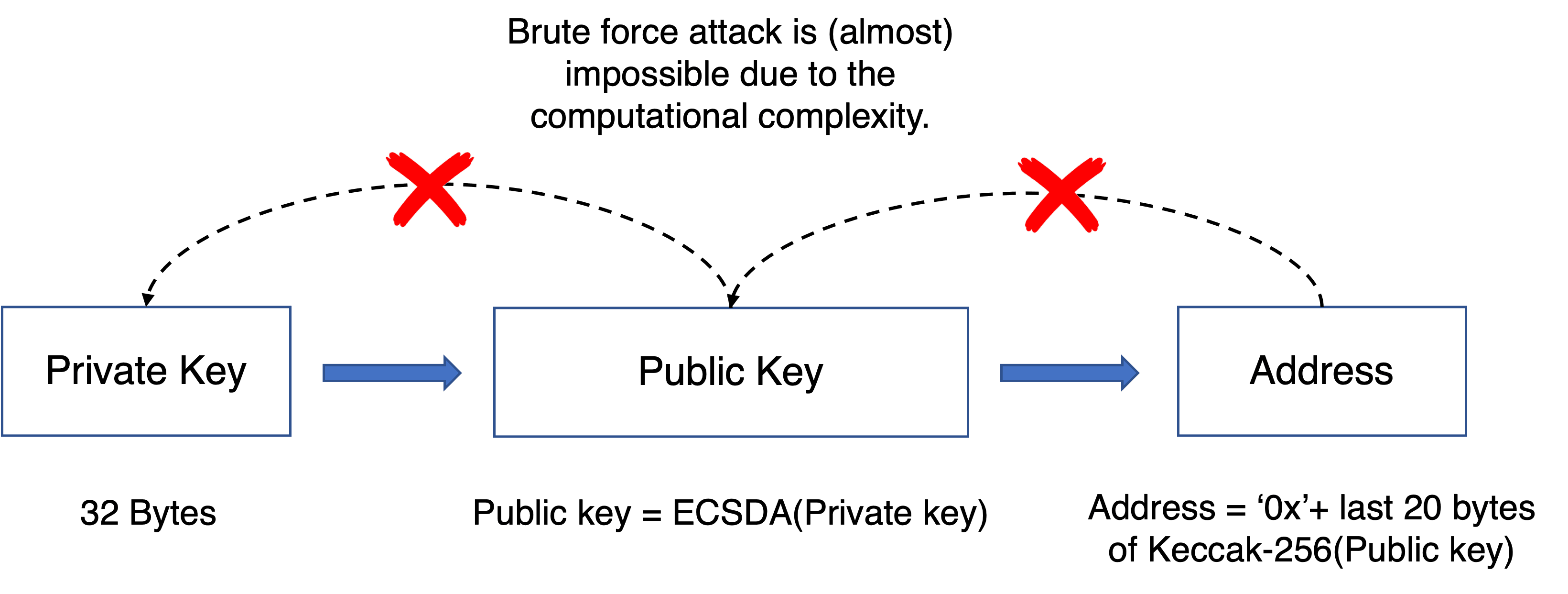
The Ethereum Address
The Ethereum address is generated from the Keccak-256 hash of the public key and is represented as hexadecimal numbers. The public key is generated from the private key using elliptic curve multiplication, which is irreversible. We can get a public key from a private key. However, we cannot get the private key given a public key, without brute force. Note that the length of the private key is 256 bits. Given a public key, you need at most 2^256 calculation to find the corresponding private key.
In a word, the relationship between the private/public key and the Ethereum address is shown in the following figure.
The Root Cause of the Vulnerability
The purpose of Profanity is to find a special Ethereum address, e.g., the five leading numbers of the address are zero. For this purpose, Profanity takes the following method.
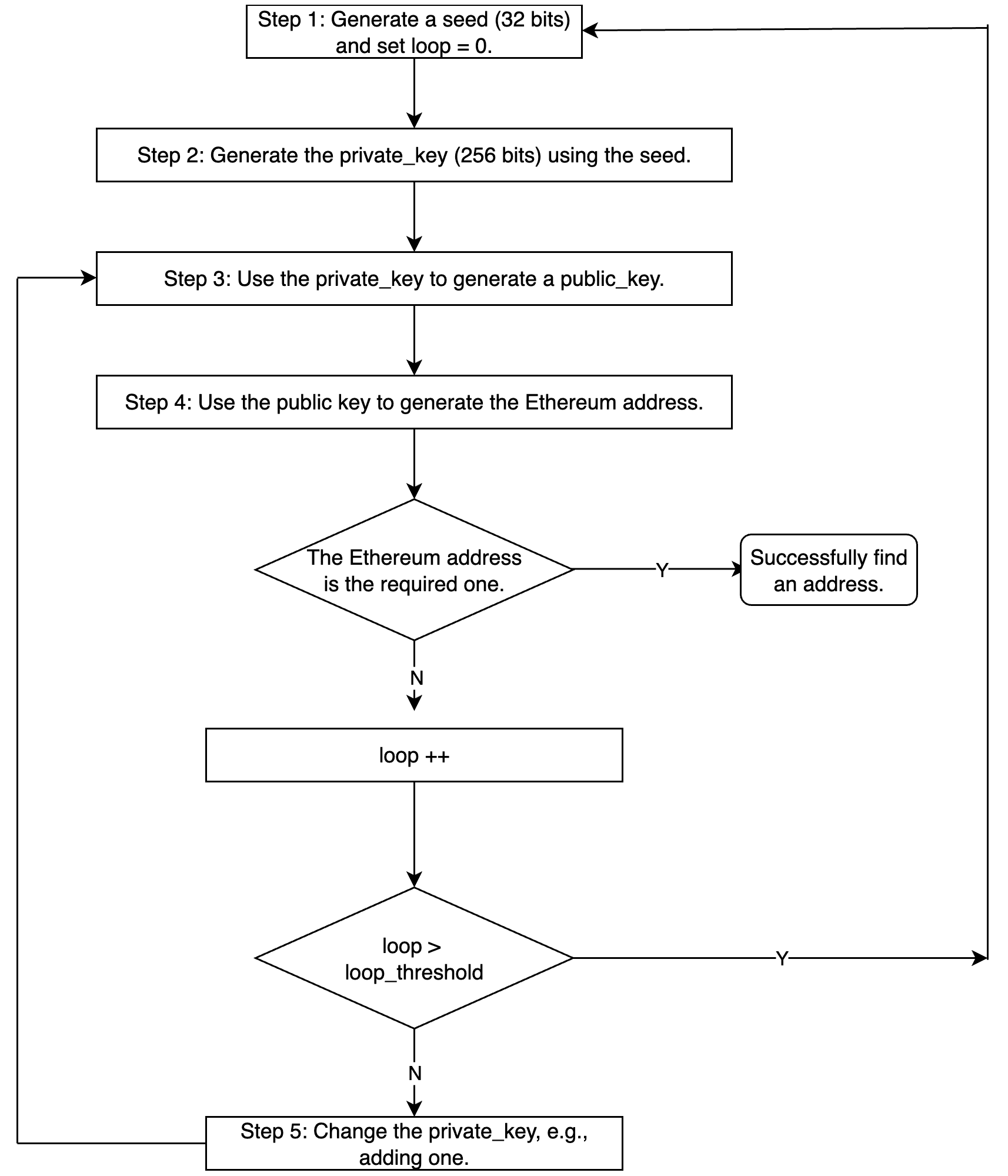
The detailed implementation may be slightly different.
Note that, the length of private_key is 256 bits (2^256 different values). However, there is a vulnerability in generating the private key. Specifically, the seed (in step 1) is only 32 bits, and the process from the seed in step 1 to the private_key in step 2 is deterministic.
What’s the security impact here?
How to Exploit
Let’s say we have an Ethereum address with many valuable assets. If we can get its private key, then we can own this account and transfer all the assets out. However, as previously discussed, we must brute force the whole 2^256 space to find the private key, which is nearly impossible.
But what if the Ethereum address is generated from the Profanity tool? We can brute force to locate the private key with a much lower difficulty. We only need to specify the seed from 0 to 2^32-1 and repeat the same process until we locate the private key that can generate the same public key (and the Ethereum address). Since we only at most 2^32 * loop_threashold calculation. This is doable in a couple of hours or days/weeks if we have a powerful GPU cluster.
However, this is still an optimized algorithm. You can refer to the article from Slowmist for more details.
Takeaway
Making a DeFi project secure is not an easy job. Besides the code audit, we think the community should take a proactive method to monitor the project status, and block the attack before it even takes place.
About BlockSec
BlockSec is a pioneering blockchain security company established in 2021 by a group of globally distinguished security experts. The company is committed to enhancing security and usability for the emerging Web3 world in order to facilitate its mass adoption. To this end, BlockSec provides smart contract and EVM chain security auditing services, the Phalcon platform for security development and blocking threats proactively, the MetaSleuth platform for fund tracking and investigation, and MetaSuites extension for web3 builders surfing efficiently in the crypto world.
To date, the company has served over 300 esteemed clients such as MetaMask, Uniswap Foundation, Compound, Forta, and PancakeSwap, and received tens of millions of US dollars in two rounds of financing from preeminent investors, including Matrix Partners, Vitalbridge Capital, and Fenbushi Capital.
Official website: https://blocksec.com/
Official Twitter account: https://twitter.com/BlockSecTeam




