After investigating the report named Analysis of the Wintermute Hack: An Inside Job published by James Edwards (@libreshash), we believe that the accusation of the Wintermute project is not as solid as the author claimed.
0x1. The privilege of the account 0x0000000fe6a514a32abdcdfcc076c85243de899b
The report just looked up the current state of the account in the mapping variable _setCommonAdmin, however, it is not reasonable because the project may take actions to revoke the admin privilege after knowing the attack.
The storage slot key of _setCommonAdmin[0x0000000fe6a514a32abdcdfcc076c85243de899b] is 0x1488acaeec0884899a8f09209808003200bbe32c28e8f074961d28a1dc78daa1, and we just investigated the storage change in history accordingly. The result shows that the value has been altered twice in the following two transactions:
- 0x37ab1d41fe3fa405b993c72ad9812d2074d55639f31ead8db2668993f3028f2a (at block 15007314);
- 0x3456571463b98eb253bfd894f06ed706073942a89fb21c42fc12ea56c190b528 (at block 15575003).
The first modification just changed the value from 0 to 1; while the second changed the value from 1 to 0, as follows:
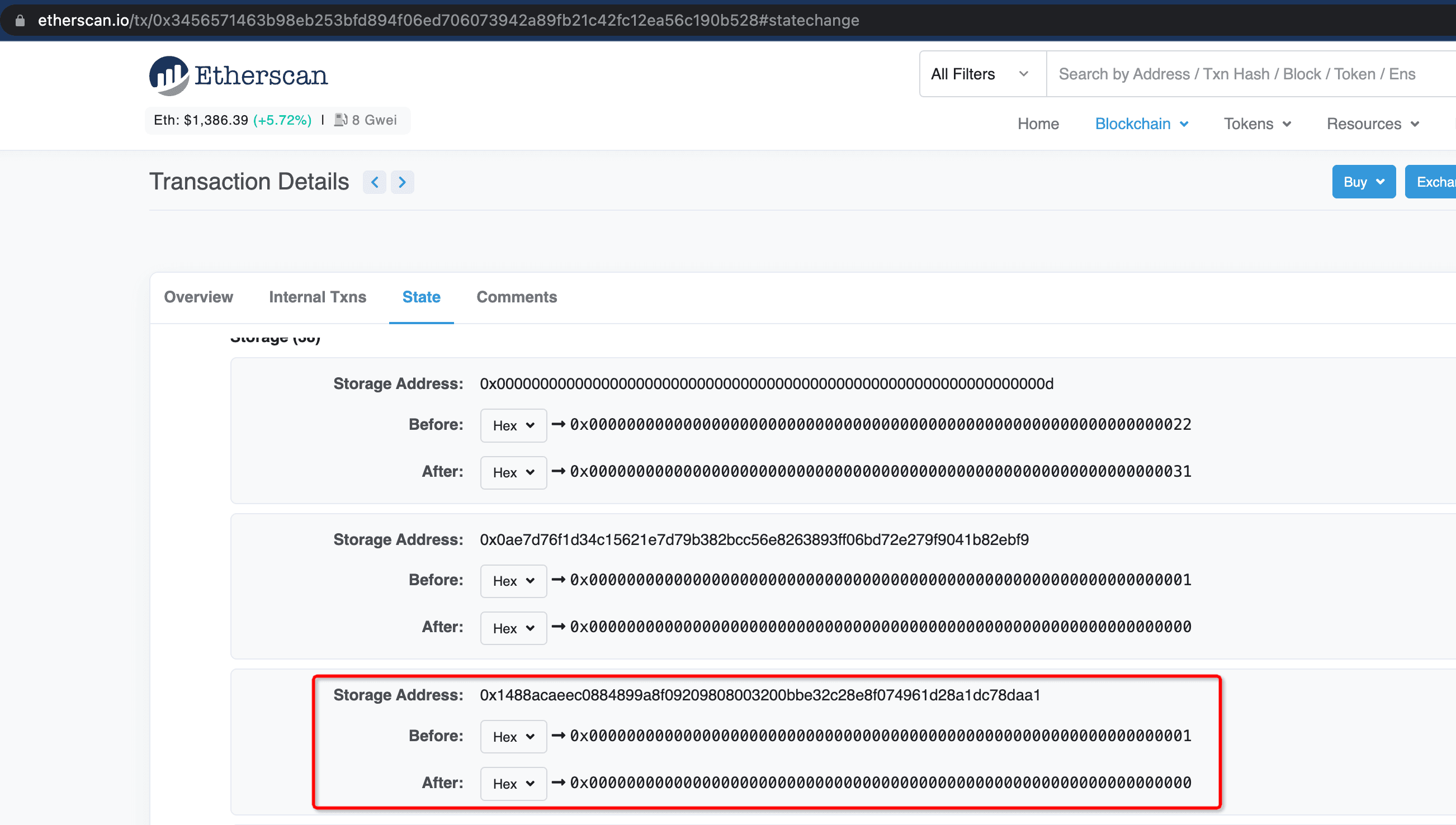

Note that the attack analyzed in the report occurred at block 15572515 (0xd2ff7c138d7a4acb78ae613a56465c90703ab839f3c8289c5c0e0d90a8b4ce16), which is in between the first modification and the second one.
Obviously, the second modification of the value means the project just revoked the admin privilege of the account.
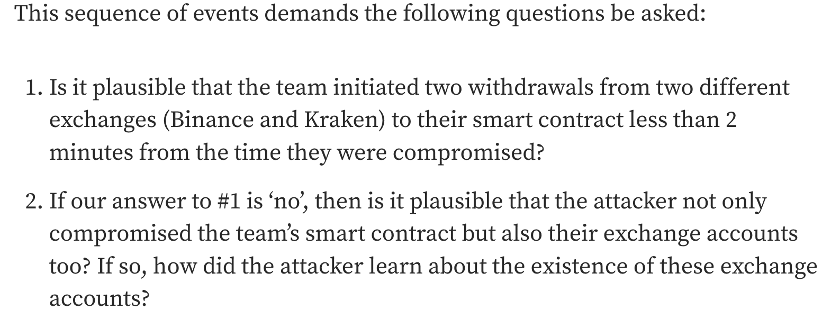
0x2. The suspicious activity
The report regarded the following activity as suspicious:
However, it is not as plausible as it claimed. The attacker could monitor the activity of the transferring transactions to achieve the goal. It is not quite weird from a technical point of view. For example, there exist some on-chain MEV-bots which continuously monitor the transactions to make profits.
0x3. Conclusion
In brief, this report is not convincing enough to accuse the Wintermute project.
About BlockSec
BlockSec is a pioneering blockchain security company established in 2021 by a group of globally distinguished security experts. The company is committed to enhancing security and usability for the emerging Web3 world in order to facilitate its mass adoption. To this end, BlockSec provides smart contract and EVM chain security auditing services, the Phalcon platform for security development and blocking threats proactively, the MetaSleuth platform for fund tracking and investigation, and MetaDock extension for web3 builders surfing efficiently in the crypto world.
To date, the company has served over 300 esteemed clients such as MetaMask, Uniswap Foundation, Compound, Forta, and PancakeSwap, and received tens of millions of US dollars in two rounds of financing from preeminent investors, including Matrix Partners, Vitalbridge Capital, and Fenbushi Capital.
Official website: https://blocksec.com/
Official Twitter account: https://twitter.com/BlockSecTeam




