According to the report from the LI.FI project and the Daniel Von Fange's twitter, we notice the LI.FI attack on March 20th, 2022. Since there is no detailed technical analysis of this vulnerability, we further analyze the attack in the following. We find the root cause of this attack is unchecked external call.
Attack Transaction
We started from the attack transaction to illustrate the attack process. The following screenshot shows the result of our transaction visualization system.
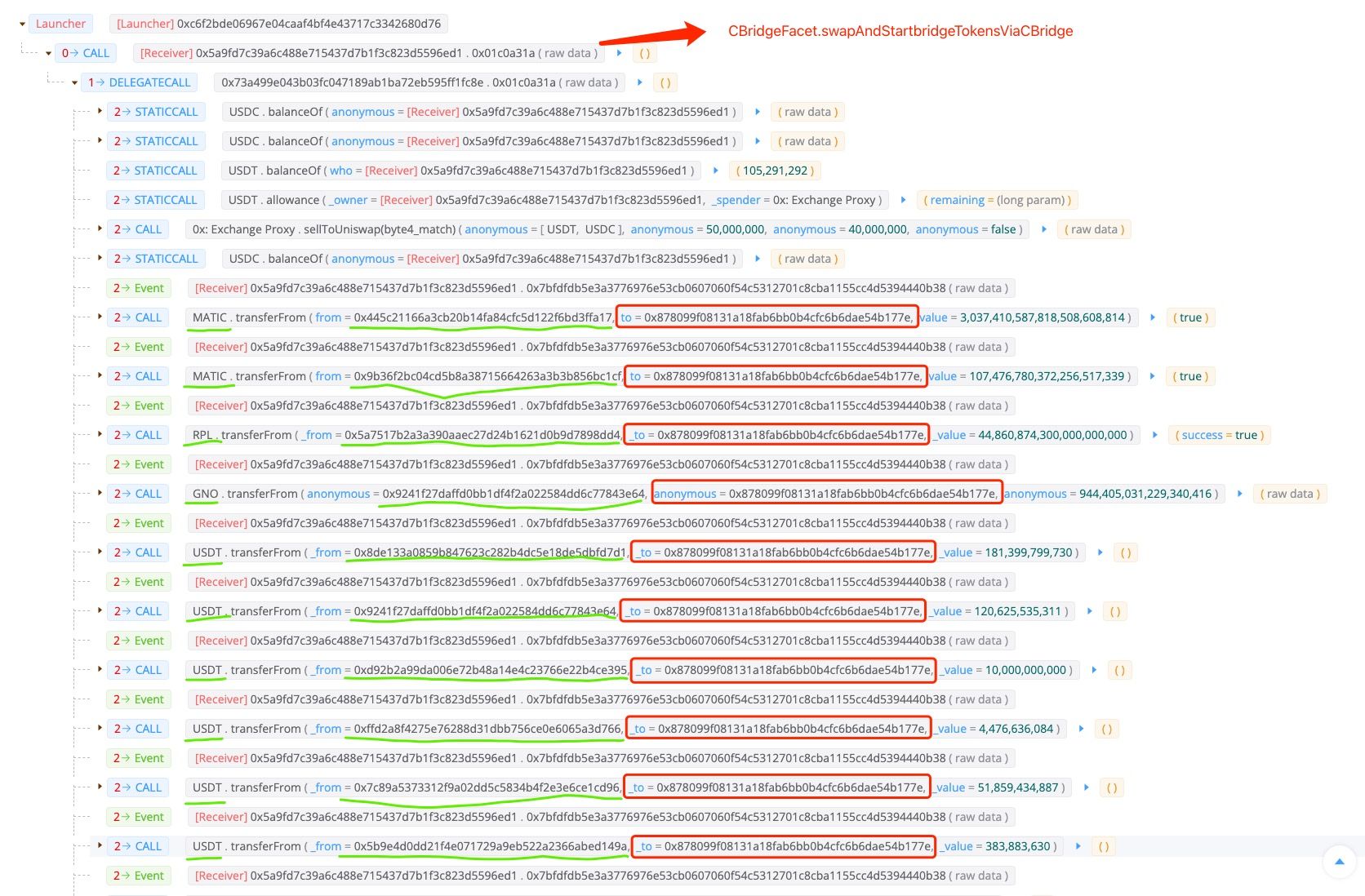
As shown in the above picutre, the whole attack process is fairly simple, which has no malicious smart contracts deployed and no flashloan involved. The only step the attacker performed is invoking the swapAndStartBridgeTokensViaCBridge(0x01c0a31a) function of the
CBridgeFacet contract, which then transfers various of tokens (e.g. USDC, MATIC, RPL, GNO, USDT, MVI, AUDIO, AAVE, JRT, and DAI.) from different spenders to the EOA controllered by the attacker.
Code Analysis
We then dive in to the codes of the victim logic contract.
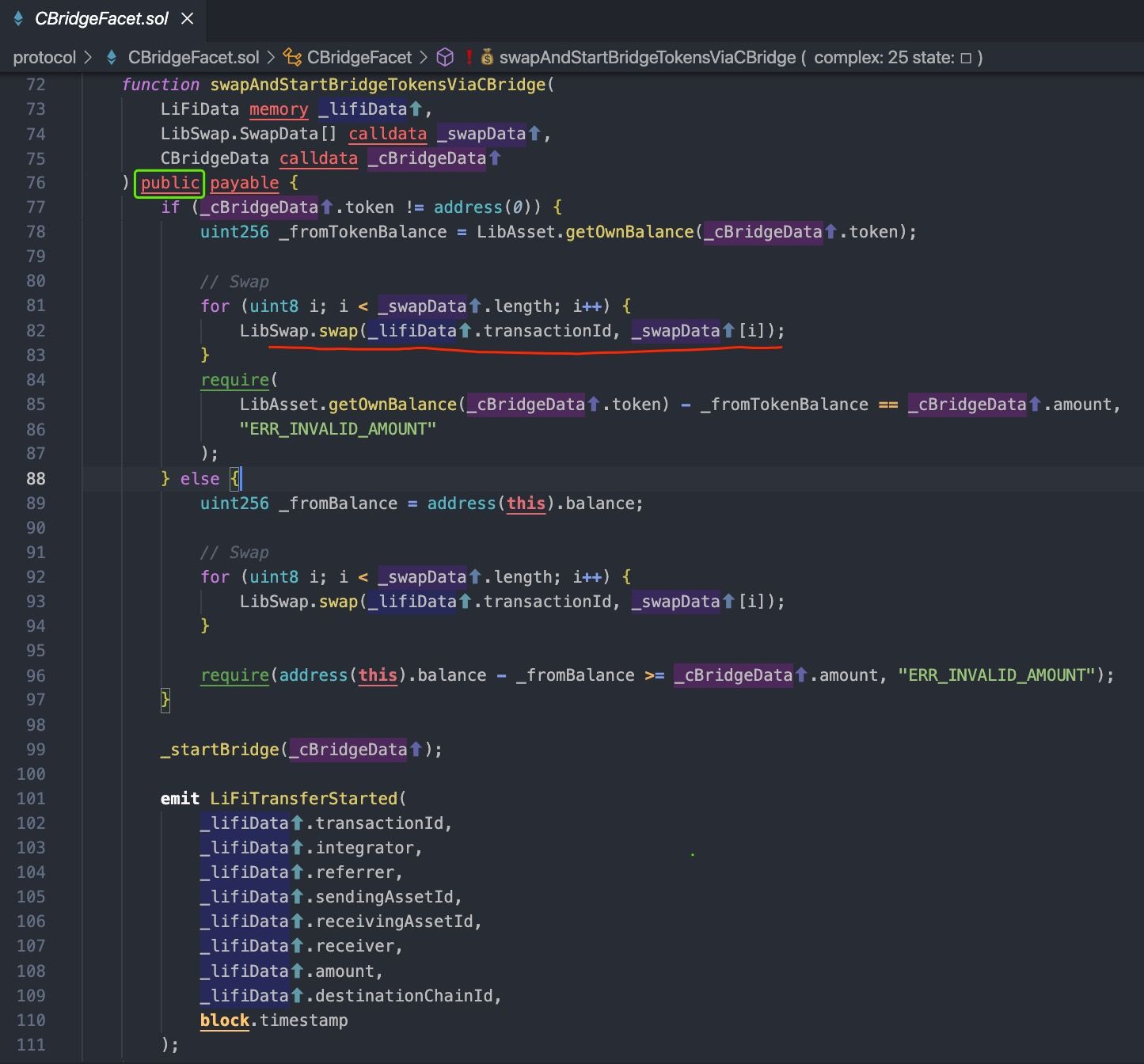
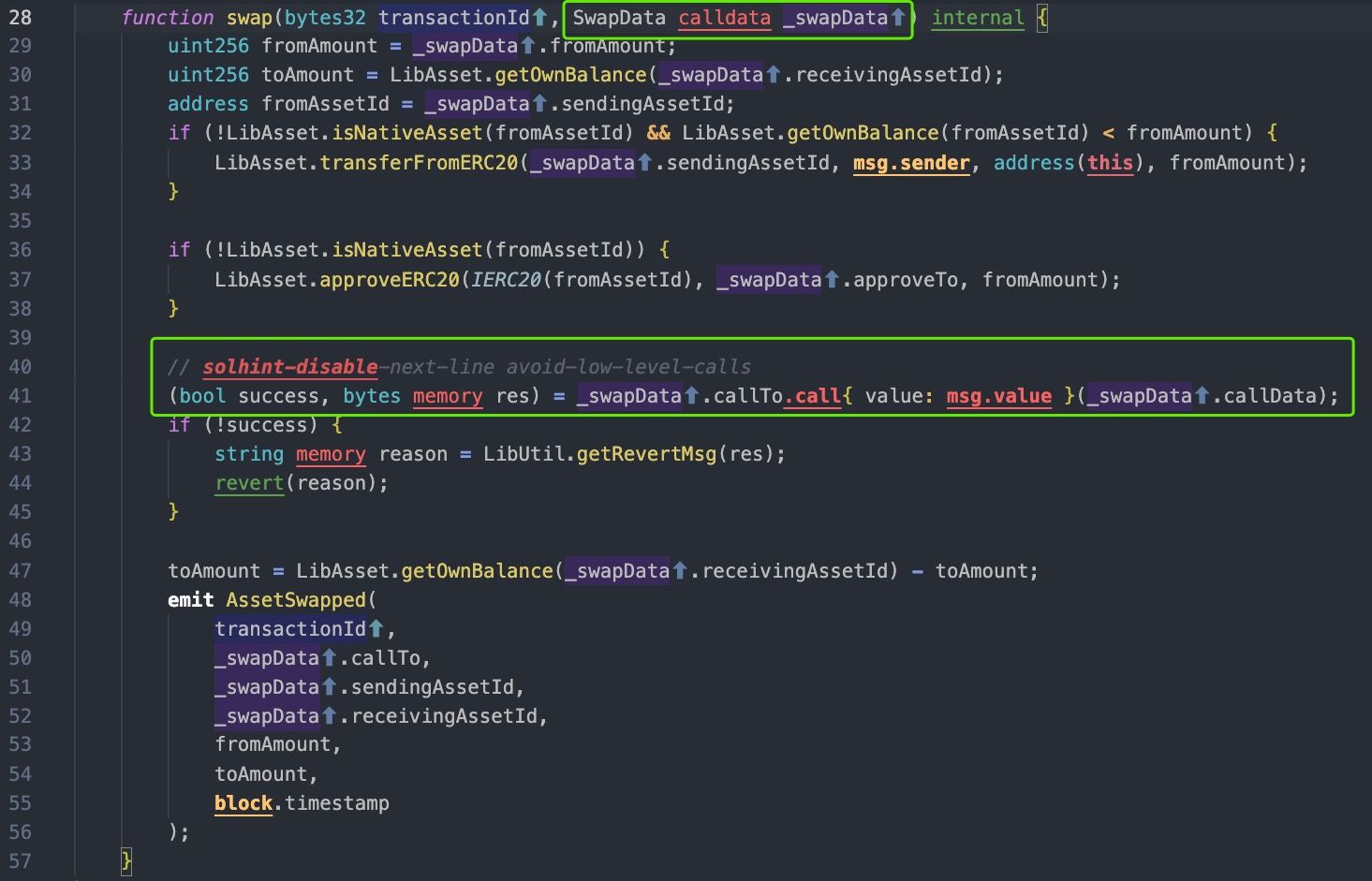
According to the above code, the swapAndStartBridgeTokensViaCBridge is an entrance of a cross-chain transaction in the source chain.
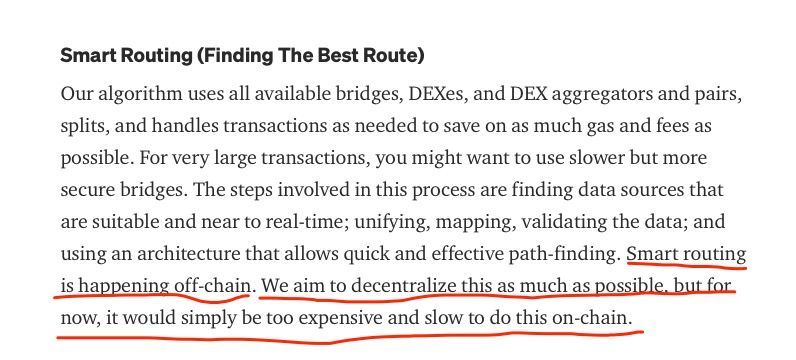
The LIFI project claims they can find the best route for users, named Smart Routing that is happening off-chain. In particular, front-end website computes the best route and encodes the parameters (including swap contract and routing path) into the parameters of the swapAndStartBridgeTokensViaCBridge function.
Clearly, the LIFI project does not consider that the function can be invoked by any accounts on blockchain, since the function performs no checks on the parameters, such as white-list and swap slippage. The most serious part is that the CBridgeFacet contract requires users to approve tokens, which causes the users' money at risk.
Profit
As a result, the attacker steals the money of LIFI users who approved their tokens to the CBridgeFacet contract by invoking the swapAnStartBridgeTokensViaCBridge function, which then invokes the transferFrom functions of different tokens. The loss statistics are shown in below table. The total losses are around $596K, which basically the same with the statistics from the LIFI project.
| Token | Amount | Price |
|---|---|---|
| GNO | 0.94 | 310.22 |
| USDC | 202,012.28 | 0.999655 |
| MATIC | 3,144.89 | 1.46 |
| AUDIO | 1,202.37 | 1.10 |
| AAVE | 8.99 | 149.99 |
| RPL | 44.86 | 31.2 |
| MVI | 22.95 | 131.82 |
| USDT | 368,745.29 | 1 |
| DAI | 8,421.49 | 0.999847 |
| JRT | 136,805.06 | 0.03789613 |
Lessons
This LIFI is a cross-chain bridge aggregator, and the victim contract is the entrance of the cross-chain transfer. The vulnerability is not due to complicated cross-chain logic, which has been shown in the previous security incidents in the corss-chain bridge. Instead, the root cause of this attack is the unchecked external call that is one of the top-10 common issues in solidity.
Since the DeFi projects becoming more complex, the project developers need to pay more attentions to write safe codes in addition to writing correct business codes. We strongly recommend that the project should NOT deploy unaudited contracts on blockchains.
About BlockSec
BlockSec is a pioneering blockchain security company established in 2021 by a group of globally distinguished security experts. The company is committed to enhancing security and usability for the emerging Web3 world in order to facilitate its mass adoption. To this end, BlockSec provides smart contract and EVM chain security auditing services, the Phalcon platform for security development and blocking threats proactively, the MetaSleuth platform for fund tracking and investigation, and MetaDock extension for web3 builders surfing efficiently in the crypto world.
To date, the company has served over 300 esteemed clients such as MetaMask, Uniswap Foundation, Compound, Forta, and PancakeSwap, and received tens of millions of US dollars in two rounds of financing from preeminent investors, including Matrix Partners, Vitalbridge Capital, and Fenbushi Capital.
Official website: https://blocksec.com/
Official Twitter account: https://twitter.com/BlockSecTeam




