Case Background
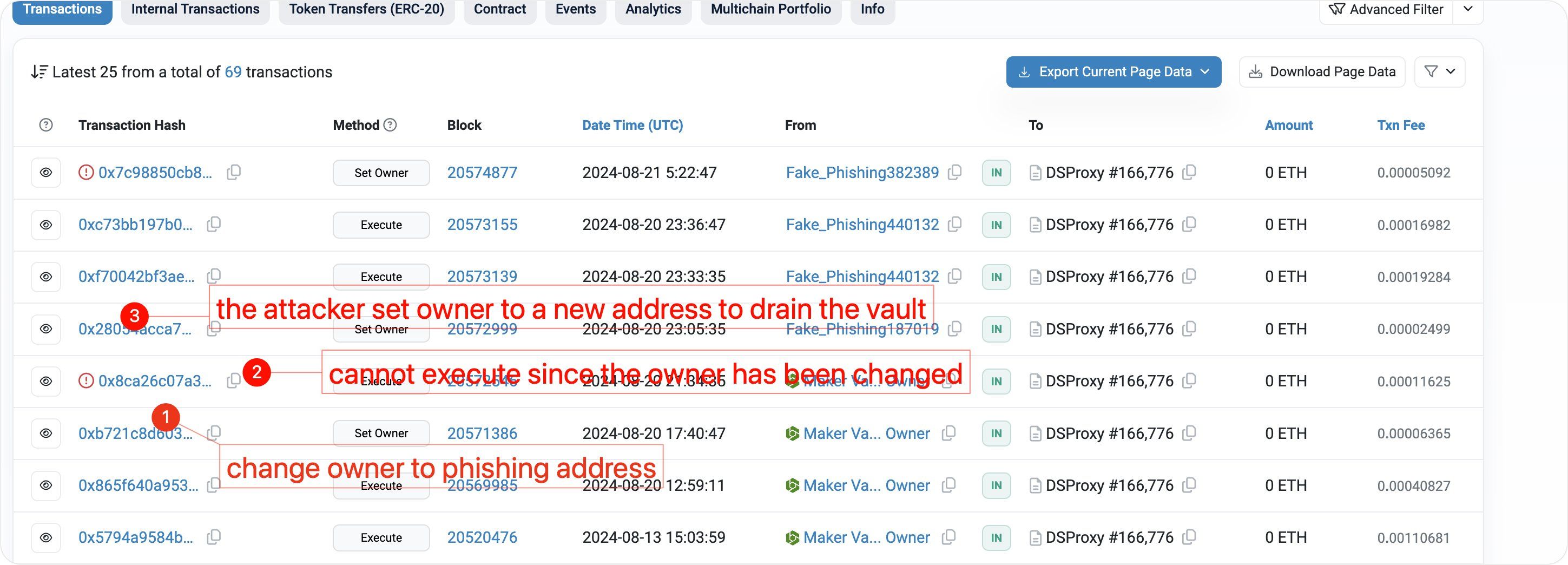
On August 20, 2024, a phishing transaction profited more than 54M stable token DAI. The drained address is a vault funded by Gemini, and the associated "Maker Vault Owner" address is 0xf2b8. The phisher lured the victim (the original owner of the vault) into signing a transaction to change the vault owner to an addresses controlled by the phisher and then executes a transaction to drain the vault.
- Phishing Address: 0x0000db5c8b030ae20308ac975898e09741e70000
- Address Draining the Vault: 0x5D4b2A02c59197eB2cAe95A6Df9fE27af60459d4
- Transactions changing the Owner: 0x2805, 0xb721
- Draining Transaction: 0xf700
Money Flow Analysis
On August 20, 2024, the original owner of the victim vault was tricked to sign a transaction that change the vault owner to a address controlled by the phisher. About five hours later, the phisher send a transaction to further change the owner to a new address. 20 minutes after the new address getting full control on the vault, it signed a transaction that had 55M DAI siphoned from the vault.
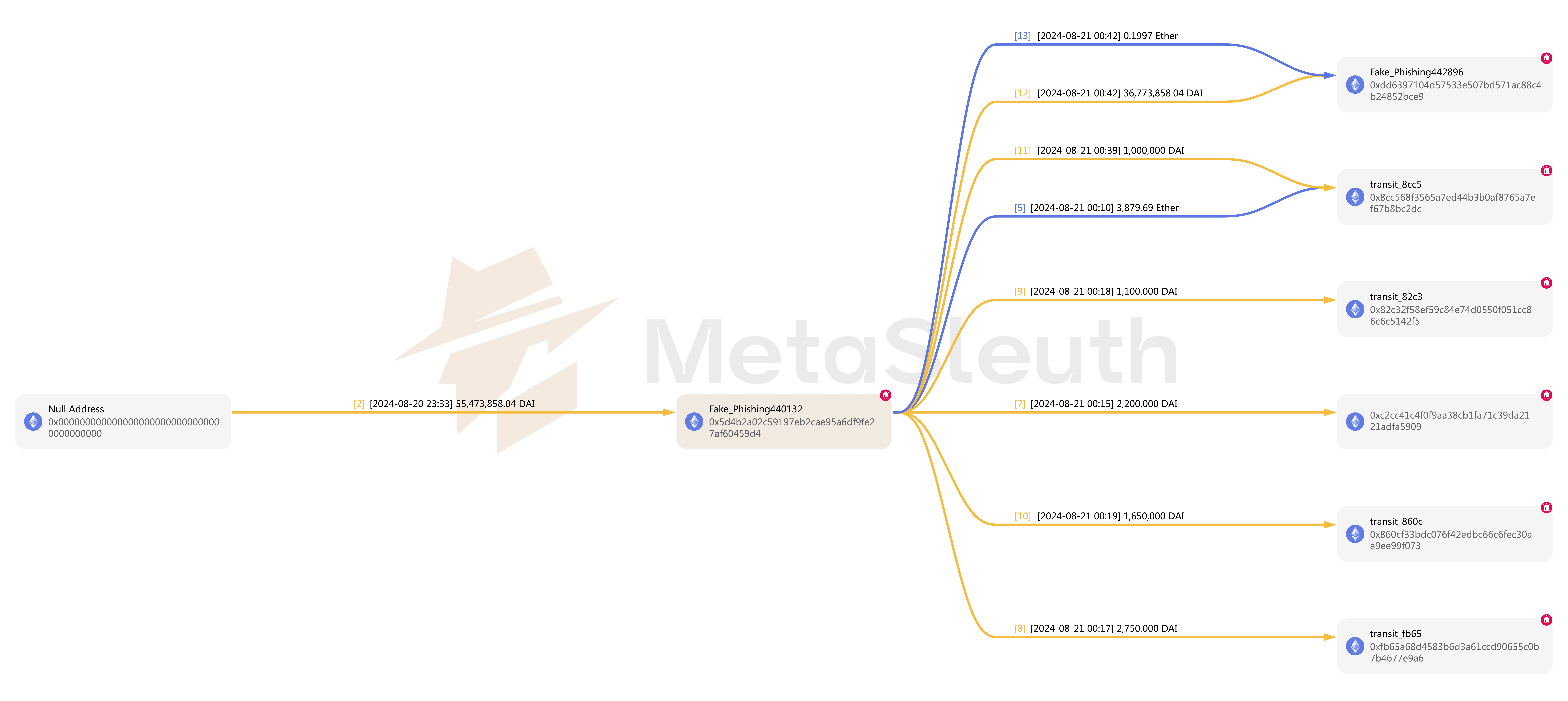
Then, within two hours, all illegally acquired DAI tokens are transferred to downstream addresses controlled by the phisher and nothing is left in the initial address draining the vault. There are a total of six downstream addresses directly connected to Address 0x5D4b (i.e., one hop away from the initial address). The majority of DAI tokens (44M) are directly transferred to downstream addresses, while 10M are swapped for the native token (3880) ETH and then moved to address 0x8cc5. The DEX used for the swap is CoW Protocol: GPv2Settlement. The swap transaction: 0x7c63.
The fund flow graph for the siphoned DAI from the original address 0x5D4b to the 1-hop downstream addresses.
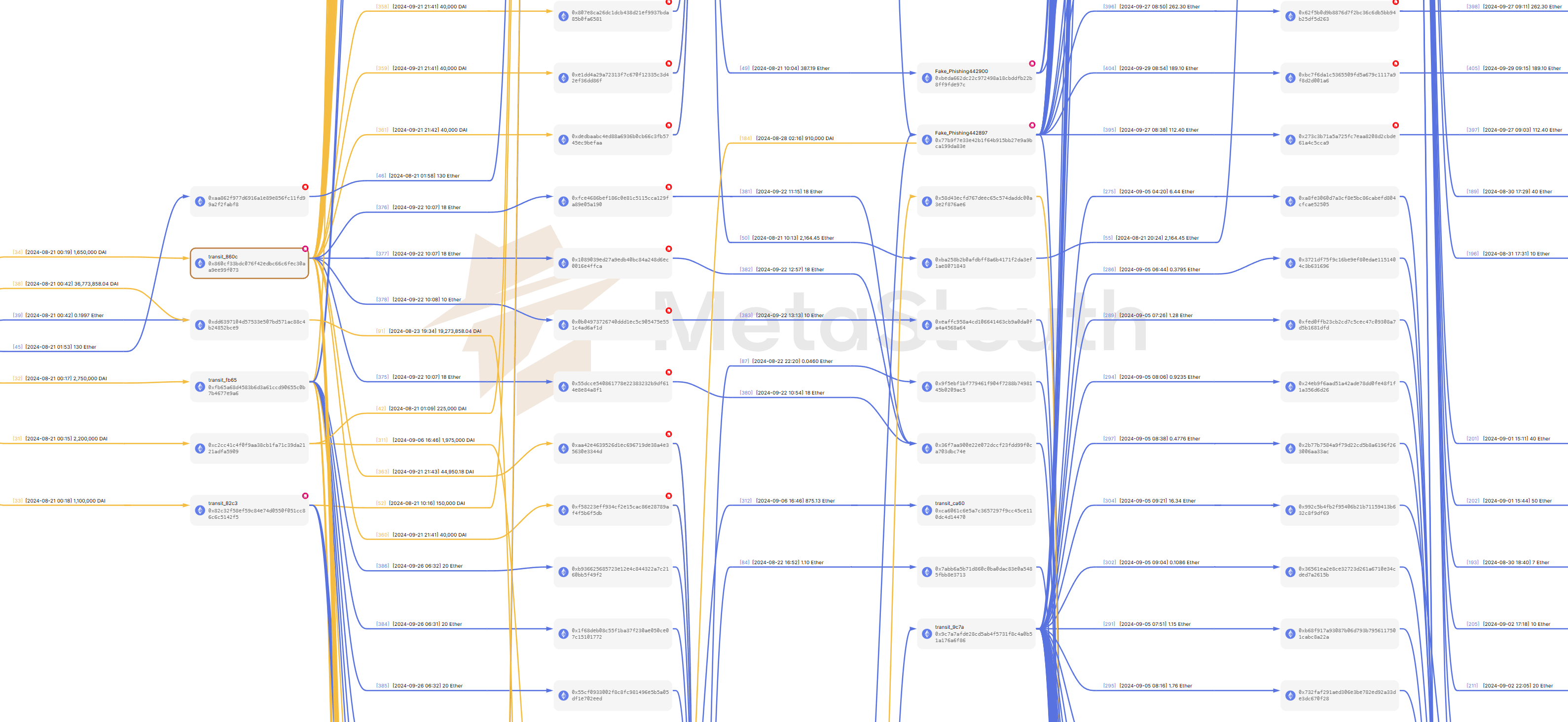
After transferring the illicit funds to the 1-hop downstream addresses, the attacker began further moving the funds to deeper addresses in batches. During the transfer process, the phisher gradually swapped the DAI held by downstream addresses for ETH. At downstream addresses 4 hops from the initial address, all the stolen DAI had already been swapped into ETH. These illicit assets, in the form of ETH, then flowed into centralized exchanges (eXch, KuCoin, ChangeNOW) and cross-chain bridges (THORChain, Hop Protocol). (Click the name to explore these cash-out addresses.) Examples of transactions depositing illicit gains to eXch: 0x2e42, 0xa982, 0x1e1e, 0xb7a9. Examples of transactions moving illicit gains to THORChain: 0x5c06, 0xf824, 0x391e.
A part of the fund flows from layer2 addresses (2 hops away from the initial address) to layer5 addresses:
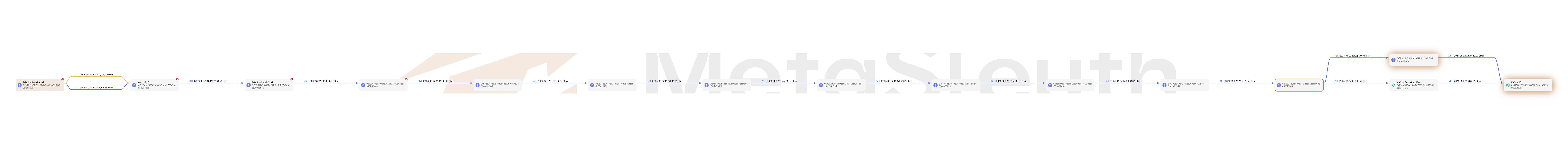
Among the transfers of illicit gains to deep downstream addresses, the longest transfer path reached up to 12 hops, where about 80k dollars were moved to the exchange KuCoin 17. As the below fund flow graph illustrates, between August 21 and August 22, 2024, the attacker gradually transferred 38 ETH to the centralized exchange over a 12-hop path.
To avoid drawing excessive attention from large transfer amounts, the perpetrators tend to split large funds across multiple addresses and use smaller transfers to move the assets to deeper addresses. An example of splitting 1.65M DAI into 36 small pieces, processed by a 1-hop address 0x860c:
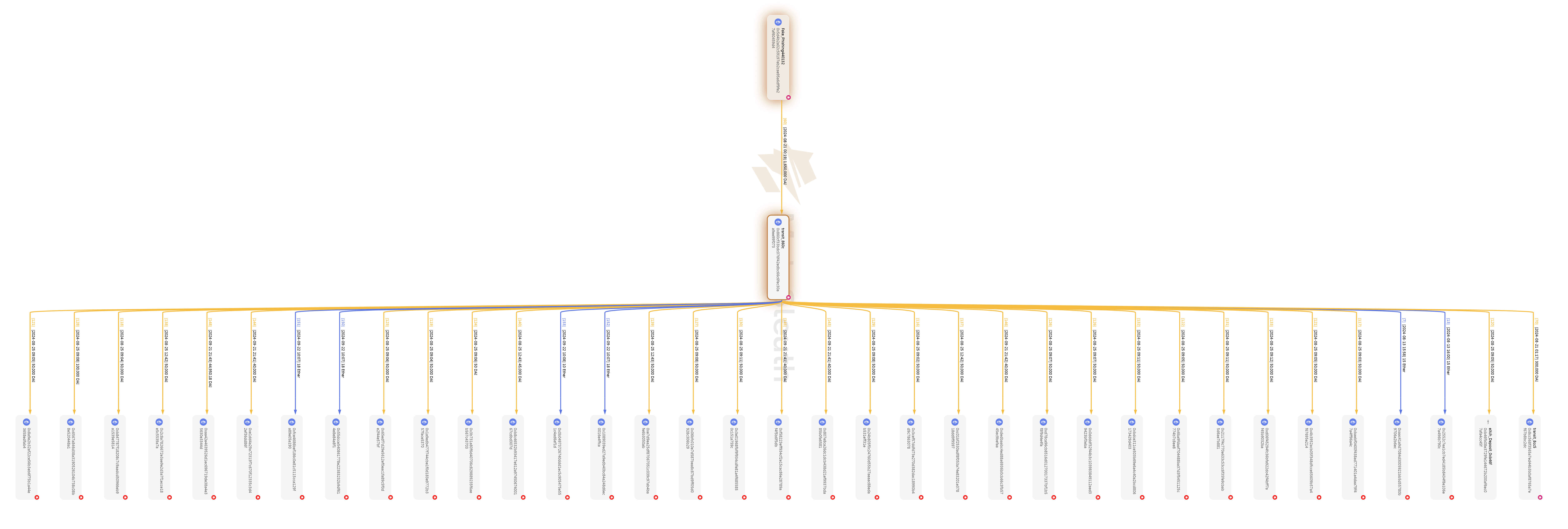
Some Relevant Addresses and Transactions
| Addresses | Transactions | Illicit Money Flows |
|---|---|---|
| 0x860cf33bdc076f42edbc66c6fec30aa9ee99f073 | 0xa11e, 0x9ef1 | 1,650,000 DAI |
| 0xdd6397104d57533e507bd571ac88c4b24852bce9 | 0x7af2, 0x1d45 | 36,733,858 DAI |
| 0x8cc568f3565a7ed44b3b0af8765a7ef67b8bc2dc | 0x7e10, 0x5d08 | 3879 ETH + 1,825,000 DAI |
| 0xca6061c6e5a7c3657297f9cc45ce110dc4d14470 | 0xee0d | 875 ETH |
| 0x77b9f7e33e42b1f64b915bb27e9a9bca199da83e | 0xf97a, 0xbc5c | 2164 ETH |
The fund flow overview:
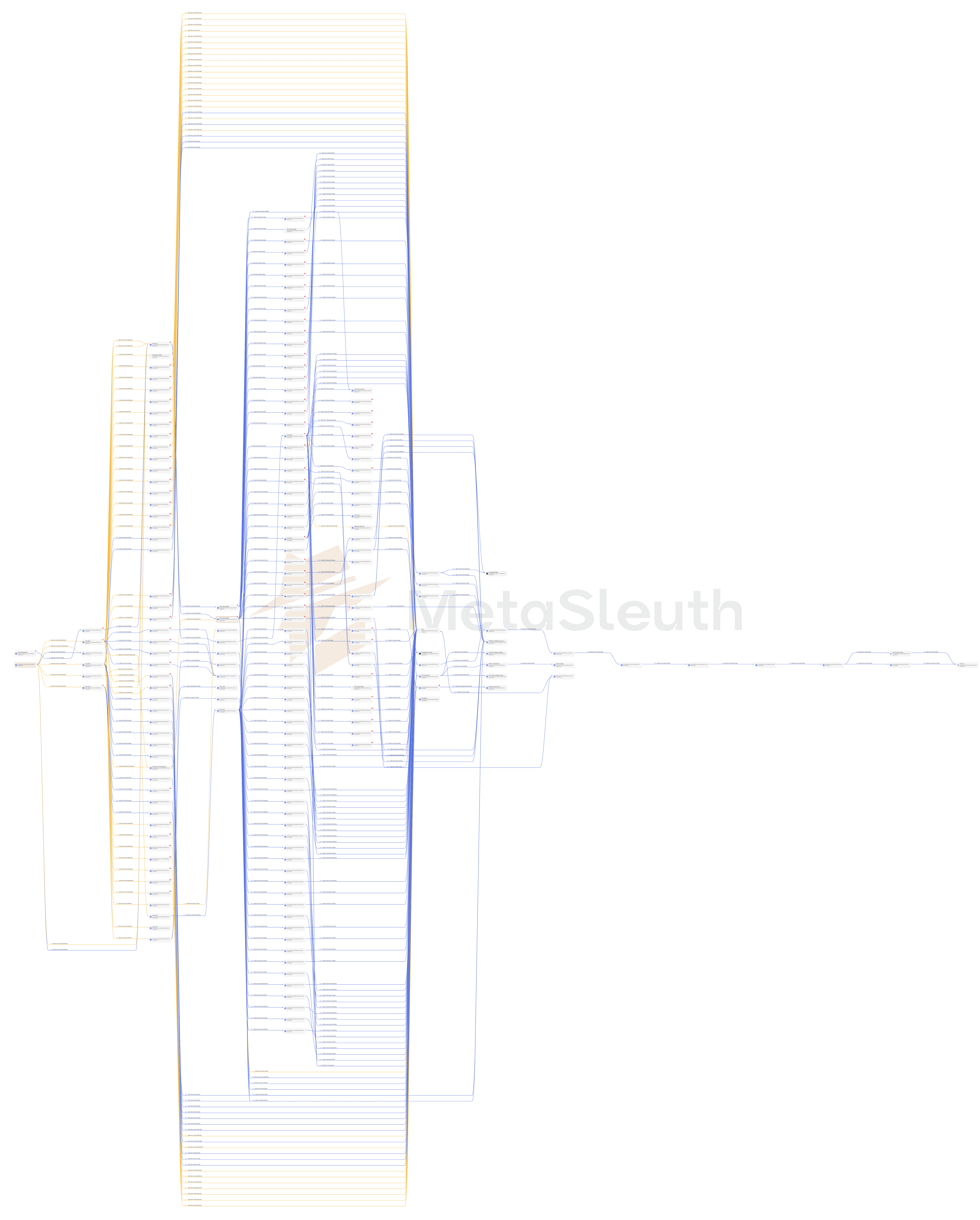
Explore details in MetaSleuth: https://metasleuth.io/result/eth/0x5d4b2a02c59197eb2cae95a6df9fe27af60459d4?source=c81289c1-2bd9-49af-a397-e4cc71990595




