Illicit Fund Flow Case Study: LI.FI Attack
Case Background
On July 16, 2024, Li.Fi, a cross-chain bridge and DEX aggregator, experienced a significant security breach that exploited the Li.Fi Diamond Contract. Various stable tokens and other assets of roughly $11.6M were stolen from users. The attacker was able to drain funds from users who had granted infinite approvals to the attacked contract.
- Attacker’s Address: 0x8b3cb6bf982798fba233bca56749e22eec42dcf3
- Vulnerable Contract: 0x1231deb6f5749ef6ce6943a275a1d3e7486f4eae
- Examples of Attack Transaction: 0xd82f, 0x86fe, 0x606a
The vulnerability was in the function depositToGasZipERC20() of GasZipFacet contract. The GasZipFacet contract was deployed by the LI.FI team five days prior to the attack to enable gas refueling for bridging transactions. Function depositToGasZipERC20() included a user-controlled argument _swapData, which was later passed to the function call LibSwap.swap(). Unfortunately, LibSwap.swap included a low-level call that can execute arbitrary functions with the call target and call data specified by the attacker-controlled argument _swapData. The attacker leveraged this "arbitrary call vulnerability" to execute unauthorized transfers from users who had given infinite approval to the Li.Fi Diamond contract.
Money Flow Analysis
On July 16, 2024, the attacker initiated nearly one hundred transactions exploiting the arbitrary call vulnerability, transferring approximately $11 million worth of stable tokens (USDT, USDC, DAI) to Address 0x8b3c within 30 minutes. Almost all siphoned stable tokens were then quickly swapped for the Ethereum native token ETH. The DEX utilized by the attacker included Uniswap, Metamask Swap, among others. Swap transaction examples: 0xdf9b, 0x11d, 0xb4a4.
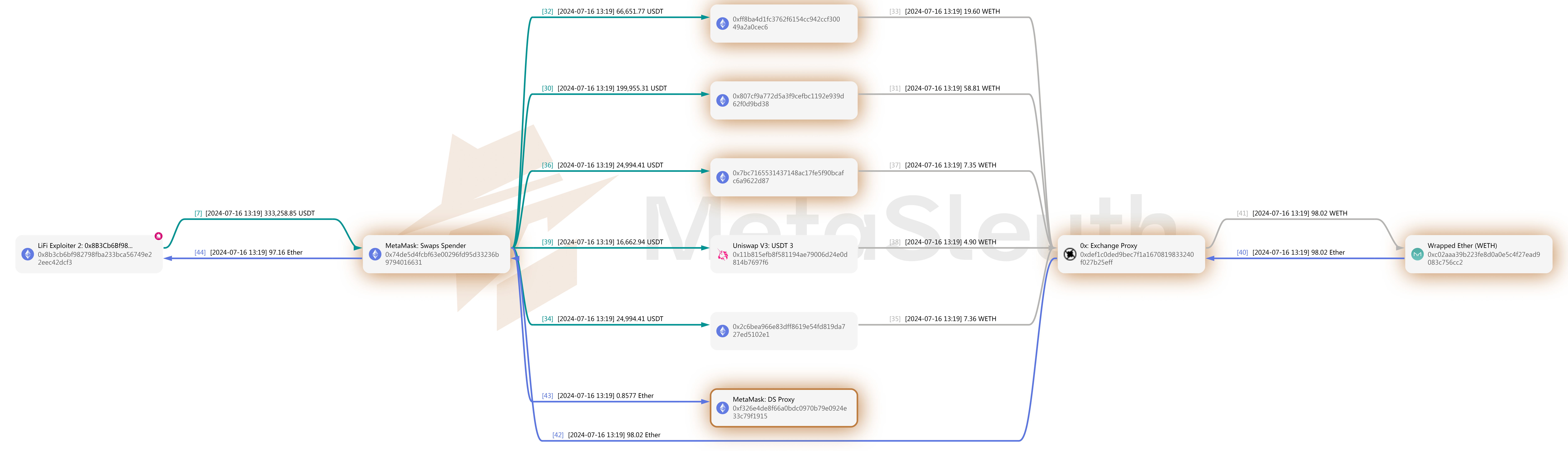
An example of the fund flow within a swap transaction 0x8e27 interacting with Metamask Swap Spender. The attacker swapped the illegally acquired 333,258 USDT into 97.16 ETH. All pools and proxies are clearly displayed using MetaSleuth.
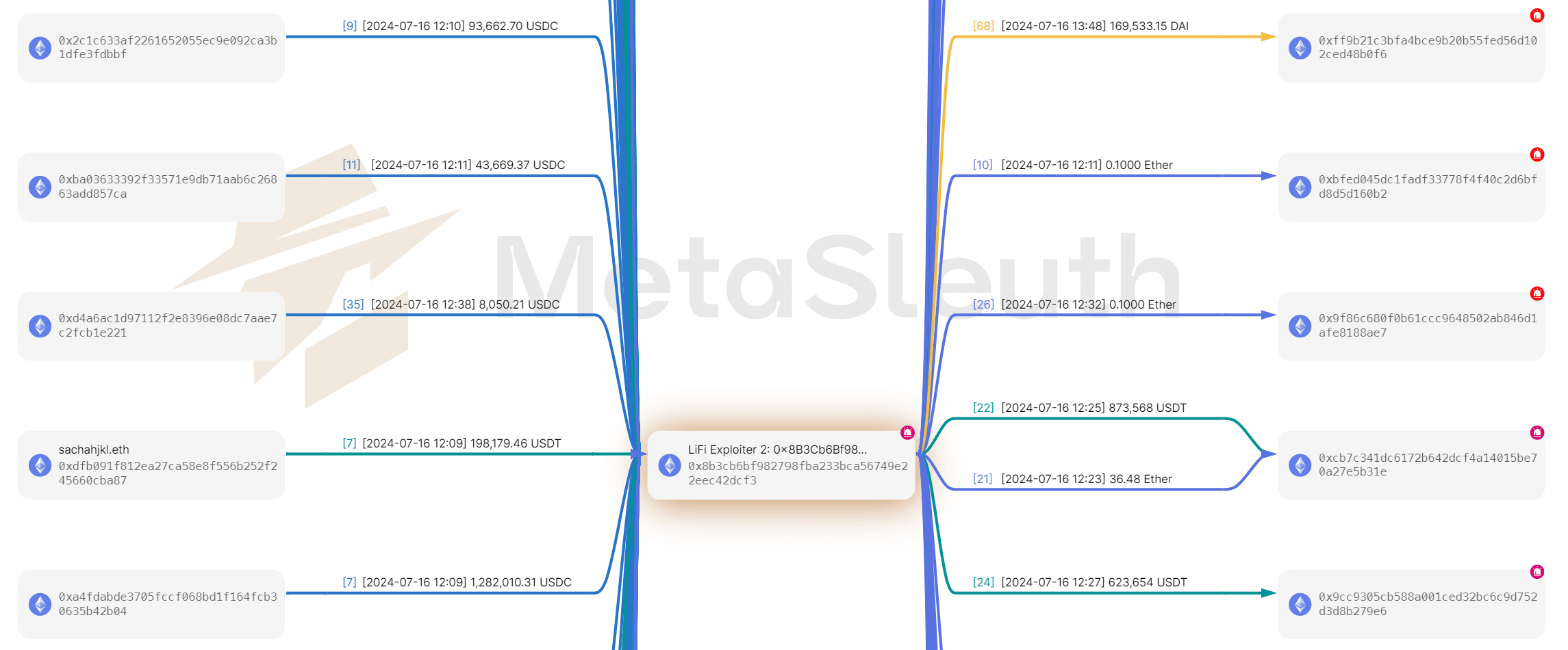
Within two hours of the attack, all the stolen assets were transferred to downstream addresses controlled by the attacker and nothing is left in the original attack address. There are a total of 32 downstream addresses directly connected to Address 0x8b3c (i.e., one hop away from the original attack address). Among these, 15 addresses received only 0.1 ETH from the attack address. As of October 22, 2024, the ETH held by these 15 addresses has not been transferred out. The remaining addresses have processed the rest of the large amounts of illicit funds.
Part of the fund flows from the victim addresses to the downstream addresses controlled by the attacker:
After transferring the illicit funds to the downstream addresses one hop away from Address 0x8b3c, the attacker began further moving the funds in batches. The transfer (laundering) process lasted for nearly three months. Almost all of the illicit funds were finally moved to Tornado Cash (99.9%), and a small portion were sent to the exchange eXch for direct cash-out. There were totally 114 transactions that the attacker used to interact with the Tornado Cash Router. Examples of transactions moving illicit gains to Tornado Cash: 0x07de, 0xfe82, 0x6a47, 0x8ea6. Examples of transaction moving illicit gains to eXch: 0xaa89, 0x7e65, 0x8572, 0x625c, 0x2dd2, 0xda71.
A part of the fund flows from layer2 addresses (2 hops away from the original attack address 0x8b3c) to layer4 addresses:
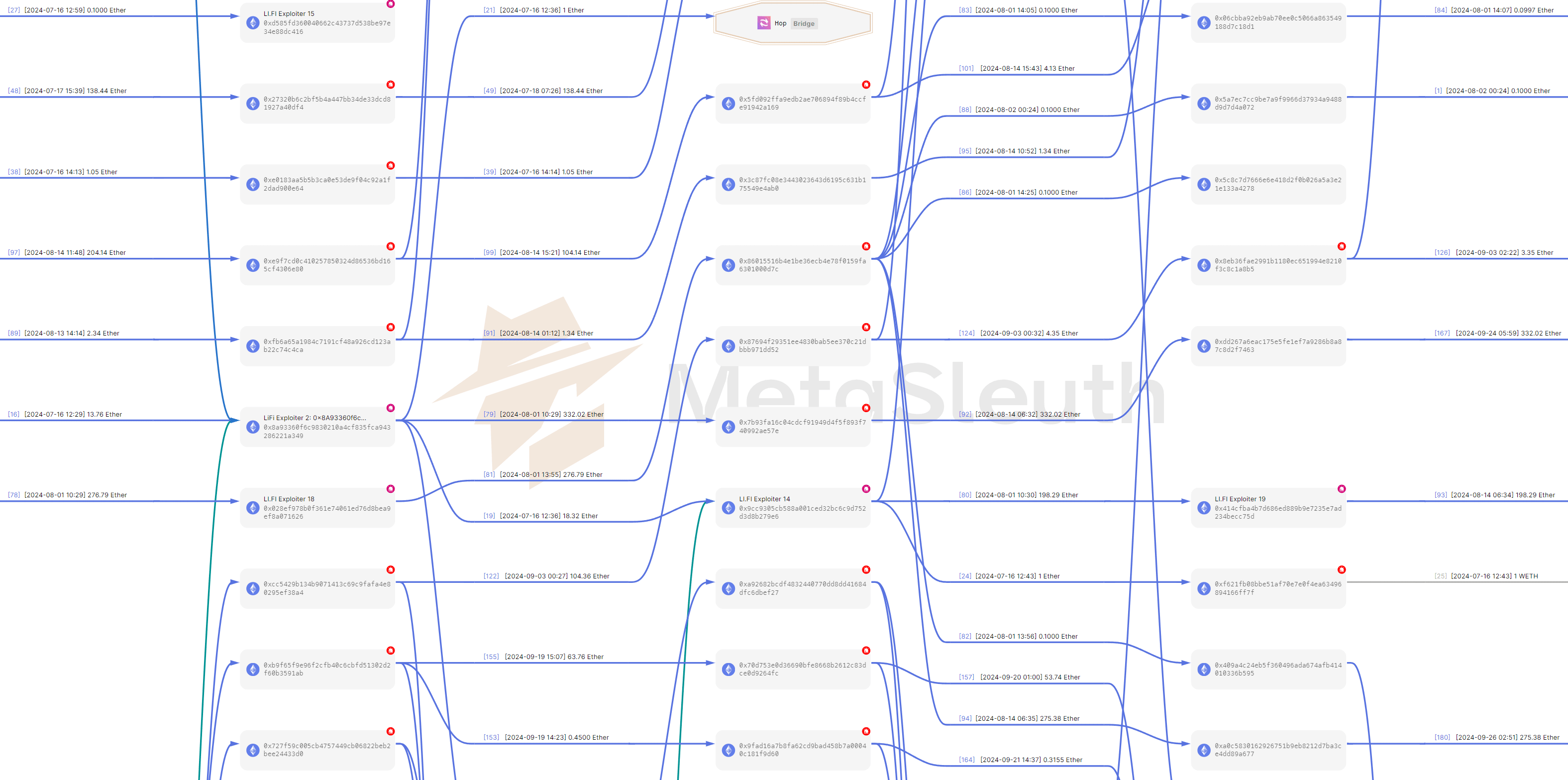
The first large-scale batch of transfers occurred within the first week following the attack, between July 16 and July 22. The attacker transferred approximately $500k worth of illicit assets from Address 0x6a6d to Tornado Cash. The attacker's transfer of illicit funds exhibited distinct characteristics: they moved the funds to downstream addresses that were far away from the attack address (high-risk address), gradually funneling a portion to Tornado Cash. In the first batch, the longest transfer path reached up to 20 hops. The attacker utilized extremely deep laundering path to obscure the illicit money flows. Between August and October, the remaining illicit funds were gradually transferred to Tornado Cash in transfer batches with the same characteristics.
An example of a transfer batch moving funds from Address 0x8e85 (one hop from 0x8b3c) to the Tornado Cash Router:
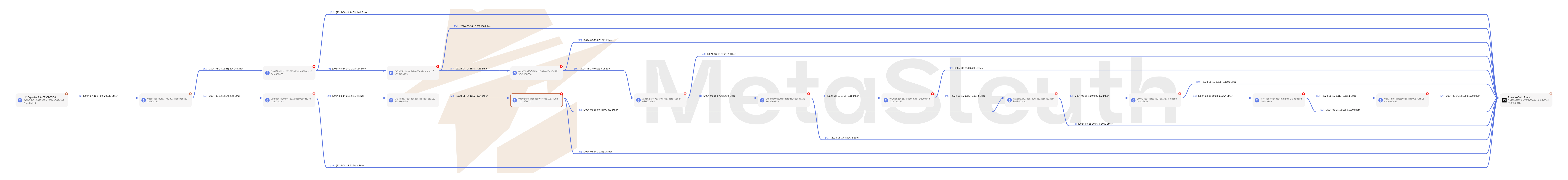
As the figure illustrates, between August 13 and August 16, 2024, the attacker gradually transferred 206 ETH to Tornado Cash over a 12-hop path. At Address 0xe9f7, the attacker split 204 ETH into two transactions: 100 ETH was sent to Tornado Cash, while 104 ETH was forwarded to further laundering addresses. This splitting pattern was consistent throughout the entire transfer process. That is, the attacker used a new, deeper address with each interaction involving Tornado Cash.
Combat Efforts
Two days after the attack, LI.FI officially released an incident report, claiming they had successfully disabled the vulnerable contract facet across all chains and prevented any further unauthorized access. LI.FI initiated a compensation plan and fully reimbursed the affected users. For the recovery of siphoned assets, they claimed that they would continue to engage with law enforcement authorities and relevant third parties, including security teams from the industry, to trace and attempt to recover funds drained. As of October 22, 2024, nearly all of the illicit funds have been transferred to Tornado Cash and Li.Fi has yet to release tracing reports.
Some Relevant Addresses and Transactions
| Addresses | Transactions | Illicit Money Flows |
|---|---|---|
| 0x8e85eace2fa757c1d97c5ebfb8b0622e5f23c5a1 | 0xe237, 0x0d23 | 206.49 ETH |
| 0xcb7c341dc6172b642dcf4a14015be70a27e5b31e | 0x050c, 0x37d4 | 873,568 USDT + 36.48 ETH |
| 0x7b93fa16c04cdcf91949d4f5f893f740992ae57e | 0x57ea, 0x52ac | 332.02 ETH |
| 0x3462d2523cded523ad47c14111aa1dcbe7773675 | 0xc66d, 0xc0ff | 120.55 ETH |
| 0xd0be9c4c84068a9964c3781f540f703c300db268 | 0x0c3b, 0x1670 | 275.38 ETH |
The fund flow overview:
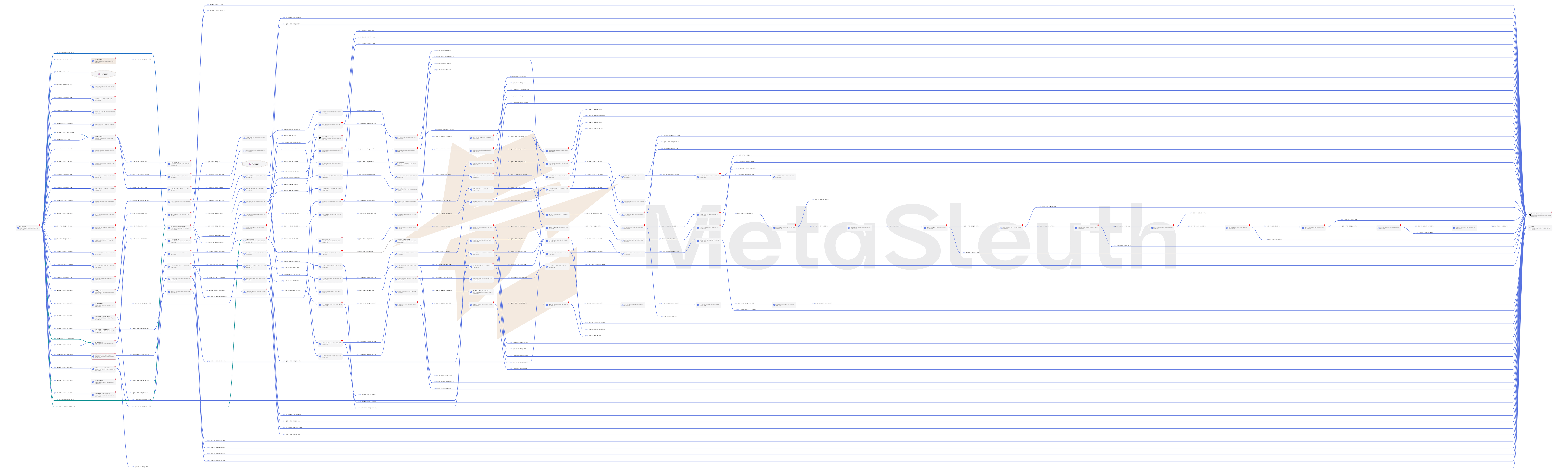
See more in MetaSleuth: https://metasleuth.io/result/eth/0x14c1597cc833783ed8ac08ecc9b704b0a398201d?source=c8cd3609-0402-45eb-bb9e-2f710bd66554




