Phalcon supports the debugging of a transaction, a powerful feature that can significantly improve the analysis efficiency for complex transactions. In the following, we will use the transaction of the exploitation of the Euler protocol to illustrate this feature.
Click the link for this transaction: https://phalcon.blocksec.com/explorer/tx/eth/0xc310a0affe2169d1f6feec1c63dbc7f7c62a887fa48795d327d4d2da2d6b111d
How to Enter the debug mode
There are two different ways to enter the debug mode. The first one is entering the debug mode from a specific line in the invocation flow view, and the second one is clicking the Debug button.
Method-I: Through the execution trace
The Invocation Flow in Phalcon provides a view that lets users take a complete picture of the hack transaction and identify possible exploitation locations. This is useful when hundreds of external calls and events are included in the transaction.
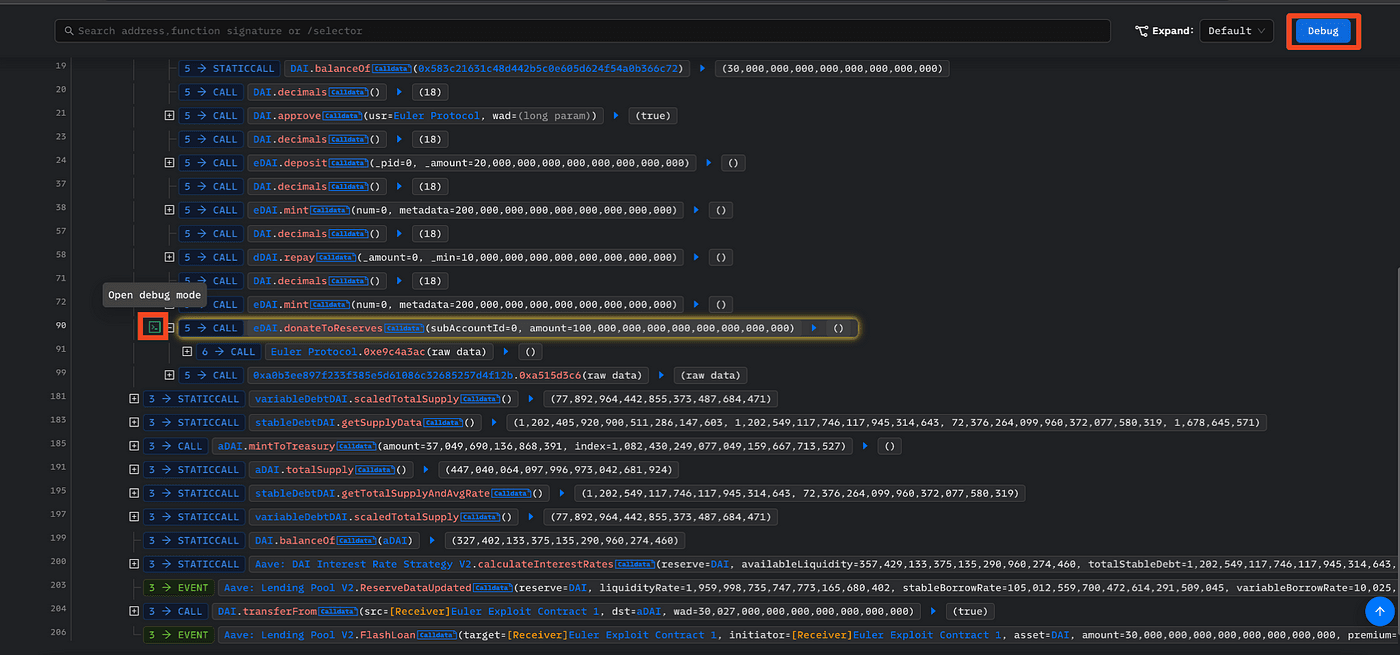
In the case of the Euler protocol exploitation, the hack transaction consists of many steps, including borrowing Flashloan from Aave, depositing Dai into the Euler protocol, etc. But in one of the steps, the exploiter called donateToReserves() to "donate" a massive fund to the Euler protocol, which warrants our vigilance. In this case, we can directly debug the transaction from this step by clicking the debug icon.
Method II: Through the Debug button
Another way to enter the debug mode is by clicking the Debug button in the upper right corner.
Debug View Layout
After entering the Debug mode, we can see the following screen.
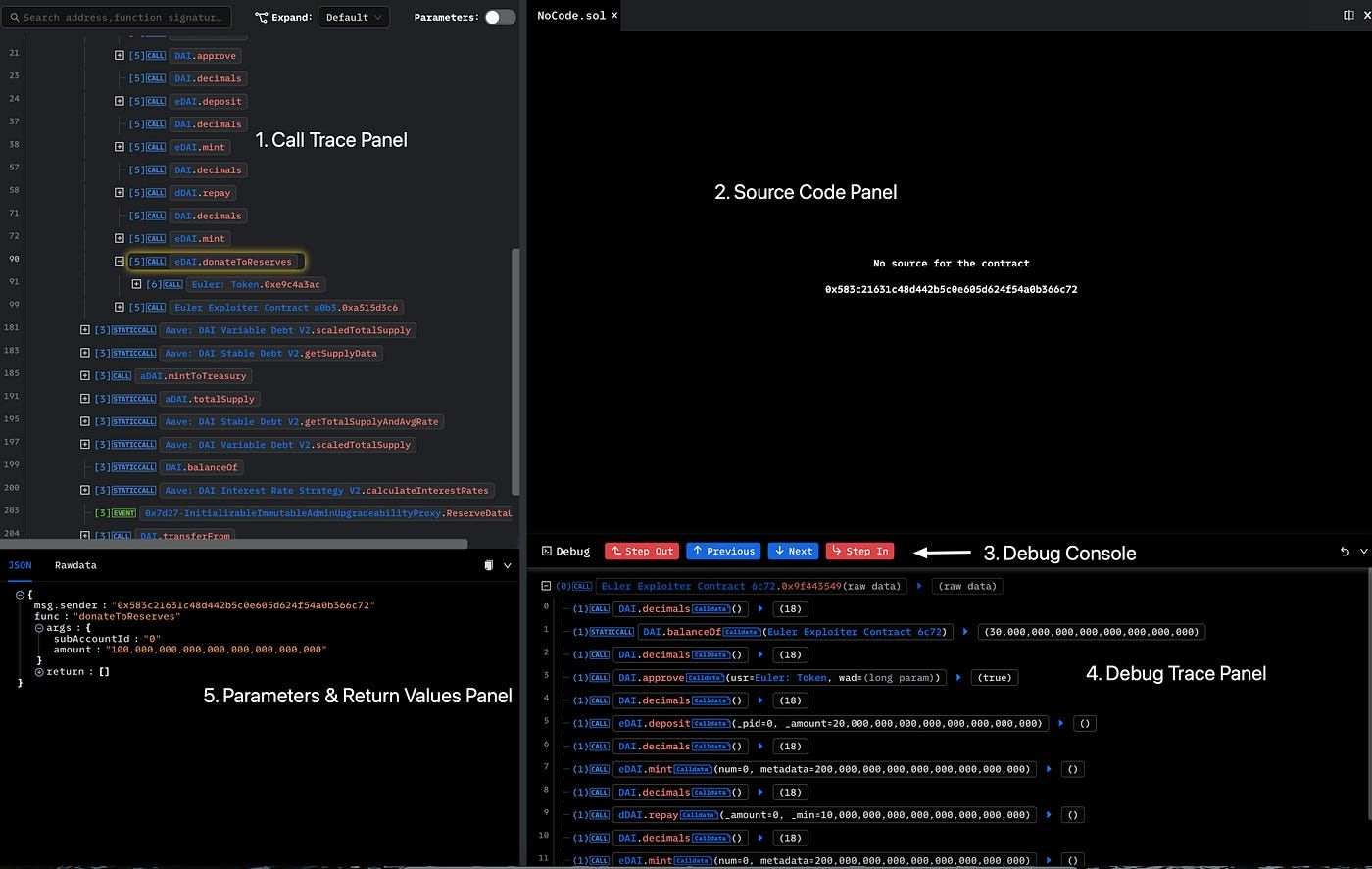
This screen has five panels, which are as follows.
- Call Trace Panel: Showing the trace of external calls and events.
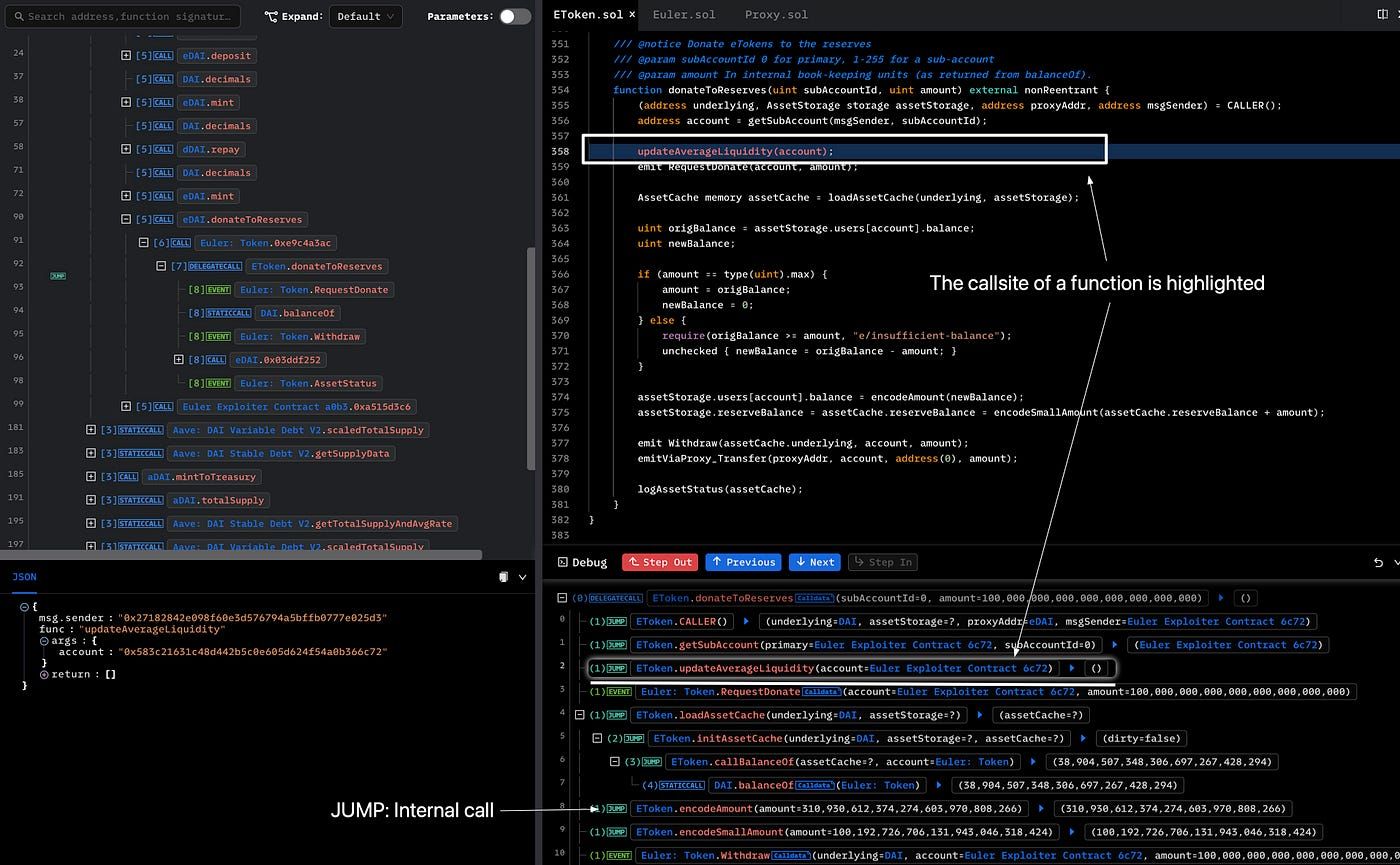
- Source Code Panel: Providing the contract’s source code and the current line (highlighted) referring to the call site of a function.
- Debug Console: a call-level single-step debug console.
- Debug Trace Panel: Showing the call stack of the current contract with a combination of internal and external calls.
- Parameters & Return Values Panel: Showing call parameters and return values.
Sometimes, the source code panel does not show the code. It’s because the panel shows the call site of the function by default. Due to the reason that the hacking contract is not unverified (not open-sourced), the source code cannot be shown.
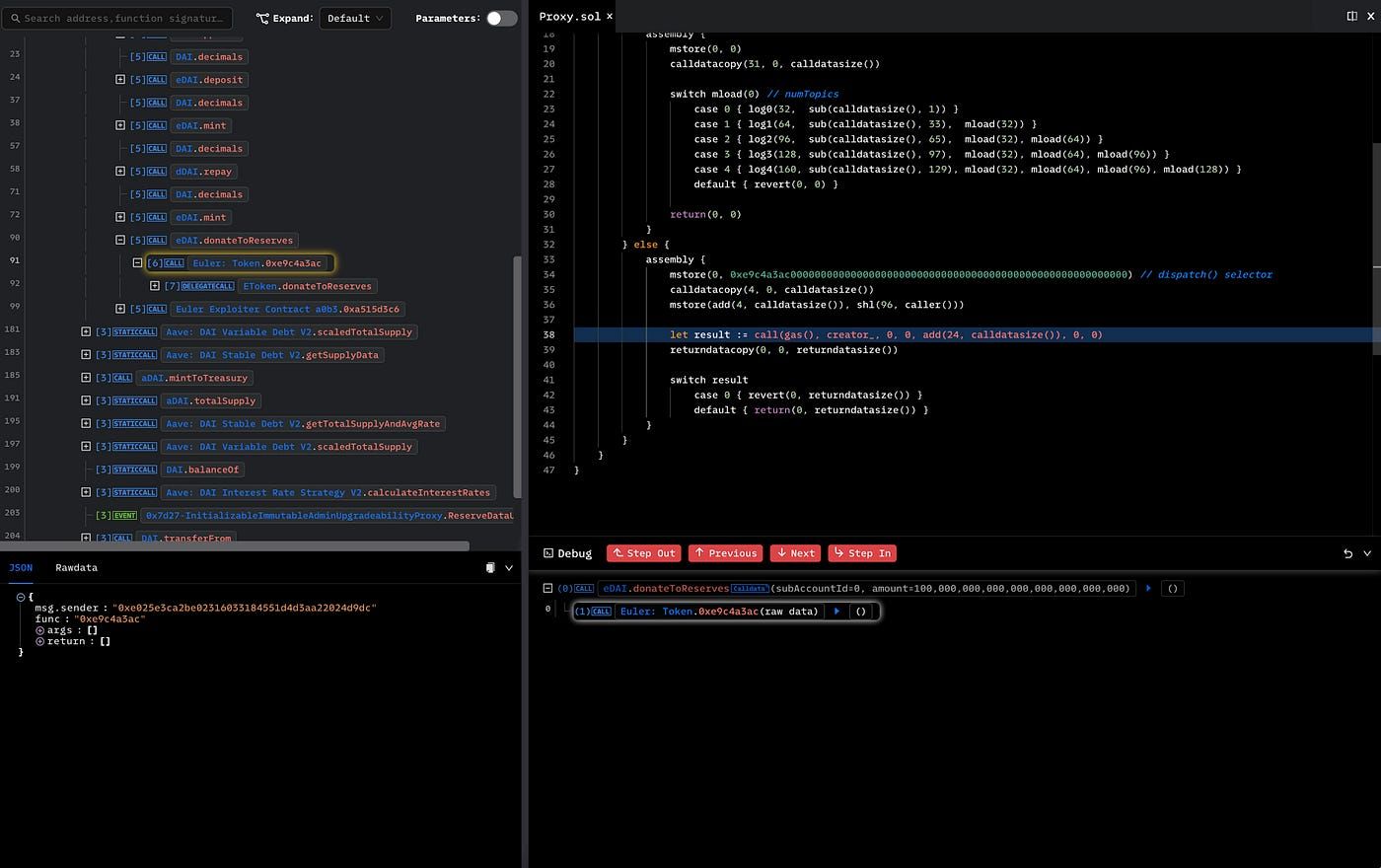
The eDai contract is verified, so we can Step In to see the specific implementation of donateToReserves(). After clicking Step In, the current line becomes the call site inside the eDai contract. It’s a proxy contract, and the code is shown in the following.
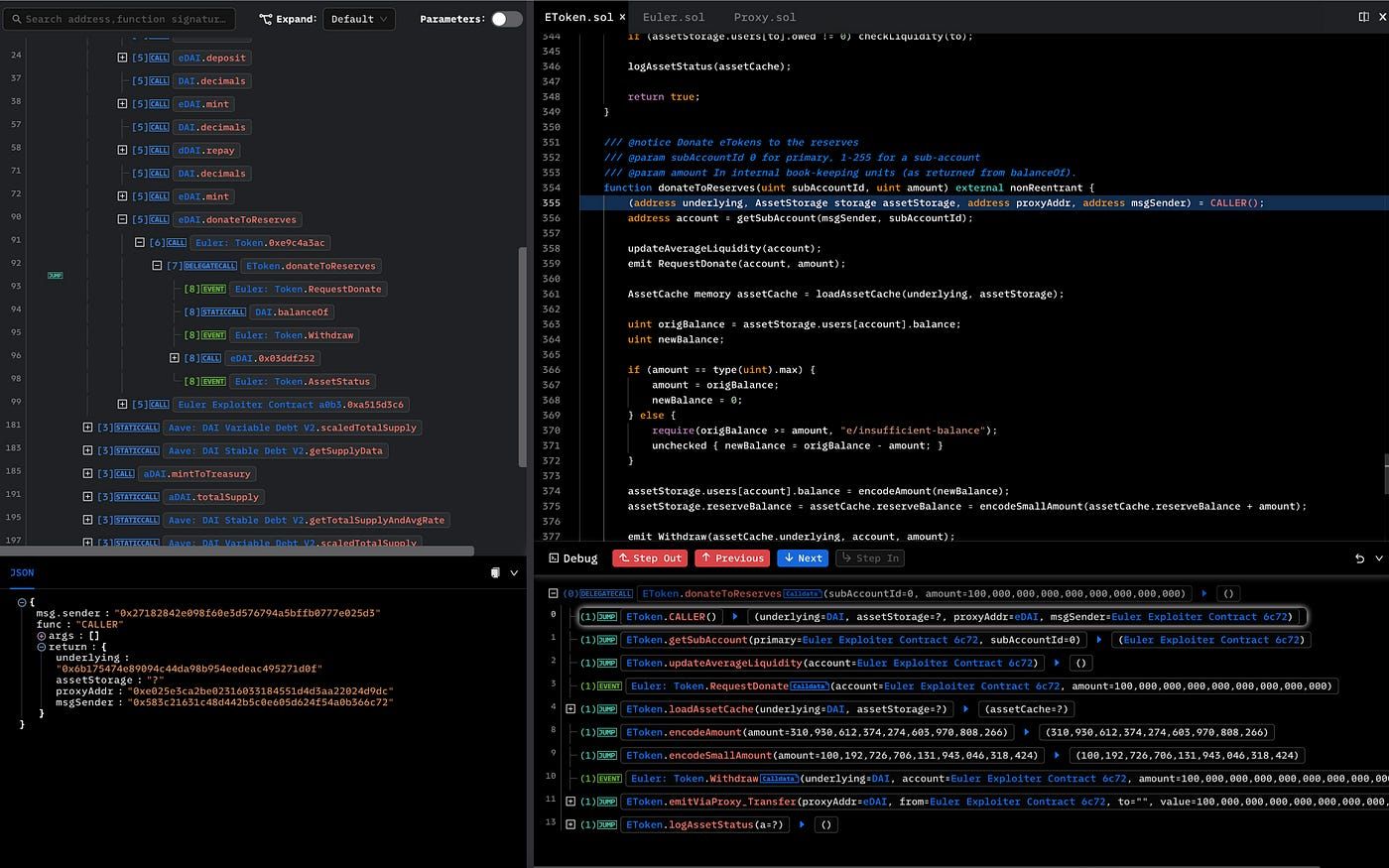
After Step In again, we can finally see the concrete implementation of donateToReserves().
How to use the Debug console
The debug console is to help understand the detailed call trace, including the internal function call (The Jump at the first of a line refers that this is an internal call). Note that the Call Trace Panel does not have an internal call trace.
To traverse between the detailed execution, Phalcon provides four buttons on the Debug Console, and Next and Previous have slightly different logic under the two colors.
- Next (Red Button): Go to the next call site in the whole call trace.
- Next (Blue Button): Go to the next call site of the current function.
- Previous(Red Button): Go to the previous call site in the whole call trace.
- Previous(Blue Button): Go to the previous call site of the current function.
- Step In: Go to the callee function.
- Step Out: Return to the call site of the current function.
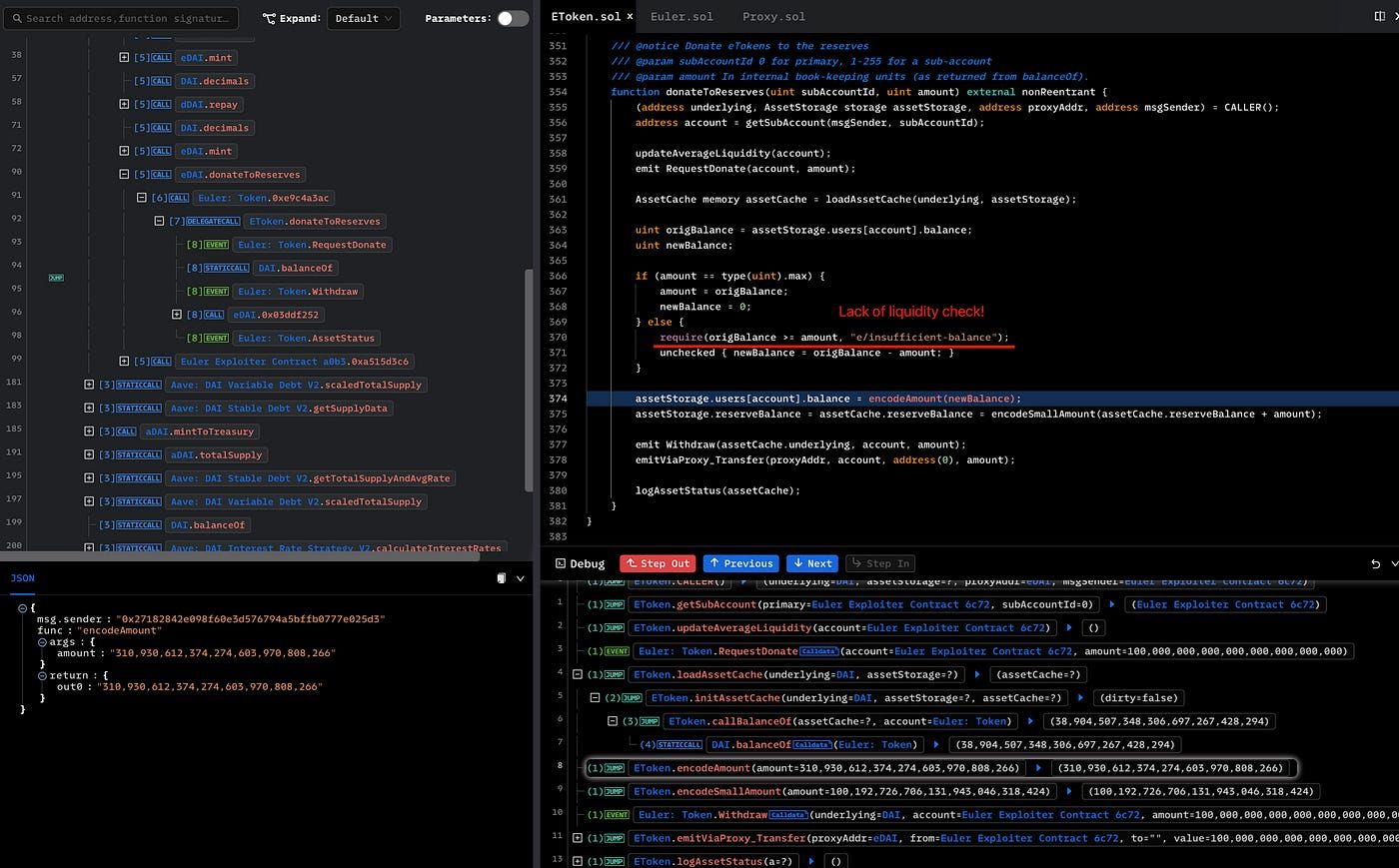
For instance, we can click the Next button to analyze the implementation of donateToReserves(). We can find that the hacker donated 100 million eDAI, making the eDAI less than the dDAI and eligible for liquidation. Therefore, the root cause is that donateToReserves() lacks liquidity check for eligible liquidation, and the exploiter liquidated himself/herself and took out 38 million eDAI.
Debug View Sharing
The debug of a transaction can be shared directly via URL, which contains the trace’s row number. When others open the link, the same debug view will be shown. This is useful when you want to share the analysis result with others. Team members can use this to collaborate, analyze and discuss together!
In summary, the typical workflow of using Phalcon Debuge to analyze a hack transaction is as follows.
- Find the possible issue in Invocation Flow and start debugging from there.
- Debug the source code and check the parameters and return values of internal calls.
- Share the view of your analysis with the team members (or public readers) for collaboration.
Other Features
Phalcon Debug has many features to help you improve efficiency.
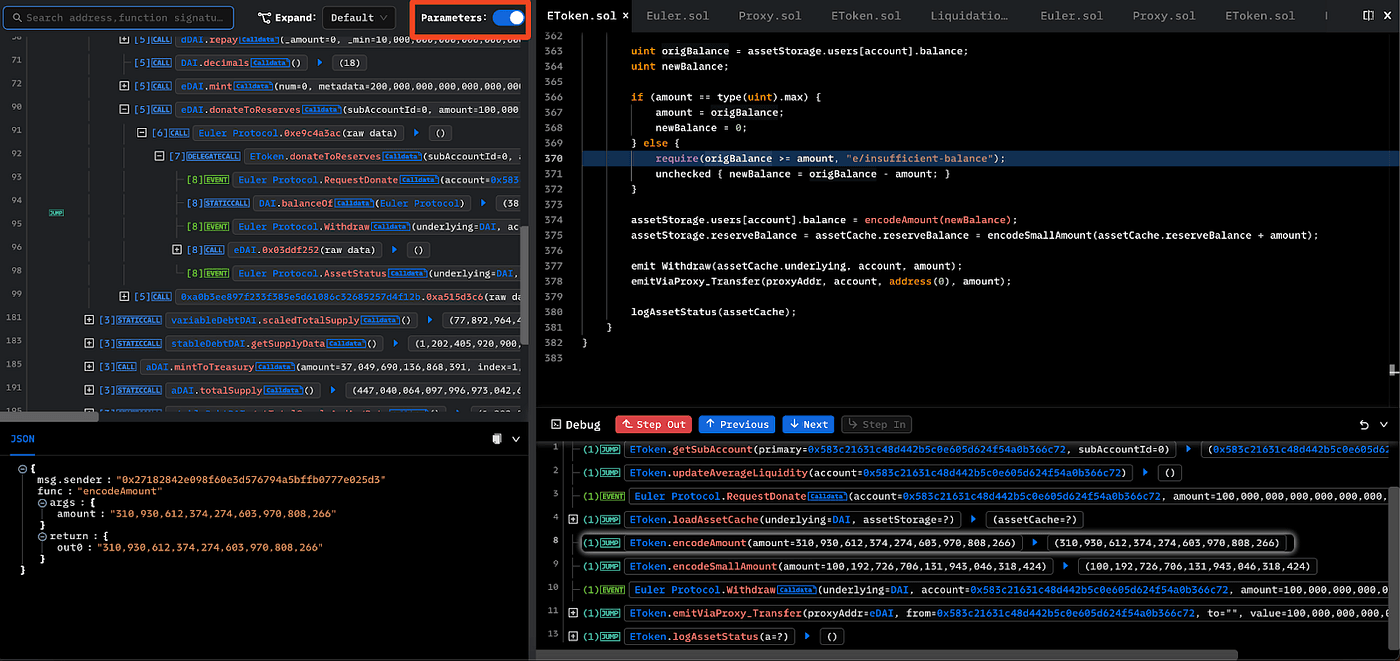
- The Call Trace View can show the full parameters by turning on the following switch.
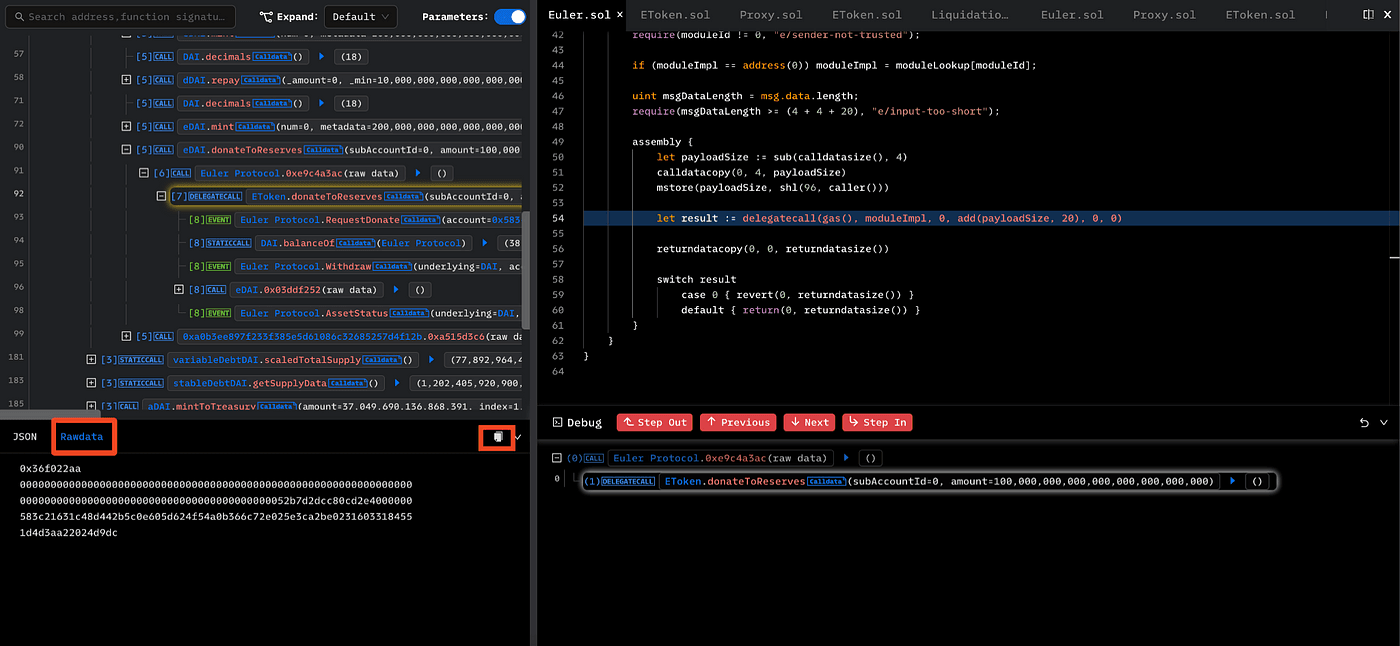
- For external calls, click “Rawdata” can see the raw call parameters.
Learn more about BlockSec: Website | Document | Twitter | Medium | TG Group




