What's four meme
Four.meme is a fair launch platform on the BNB Chain that eliminates pre-sales, seed rounds, and team allocations for memecoins, ensuring everyone participates on equal footing. Leveraging the chain’s low-cost transactions and robust infrastructure, it offers features like multi-token trading, liquidity incentives, and community-driven programs (airdrops, referrals, and more), simplifying the process of discovering, launching, and investing in new memecoins.
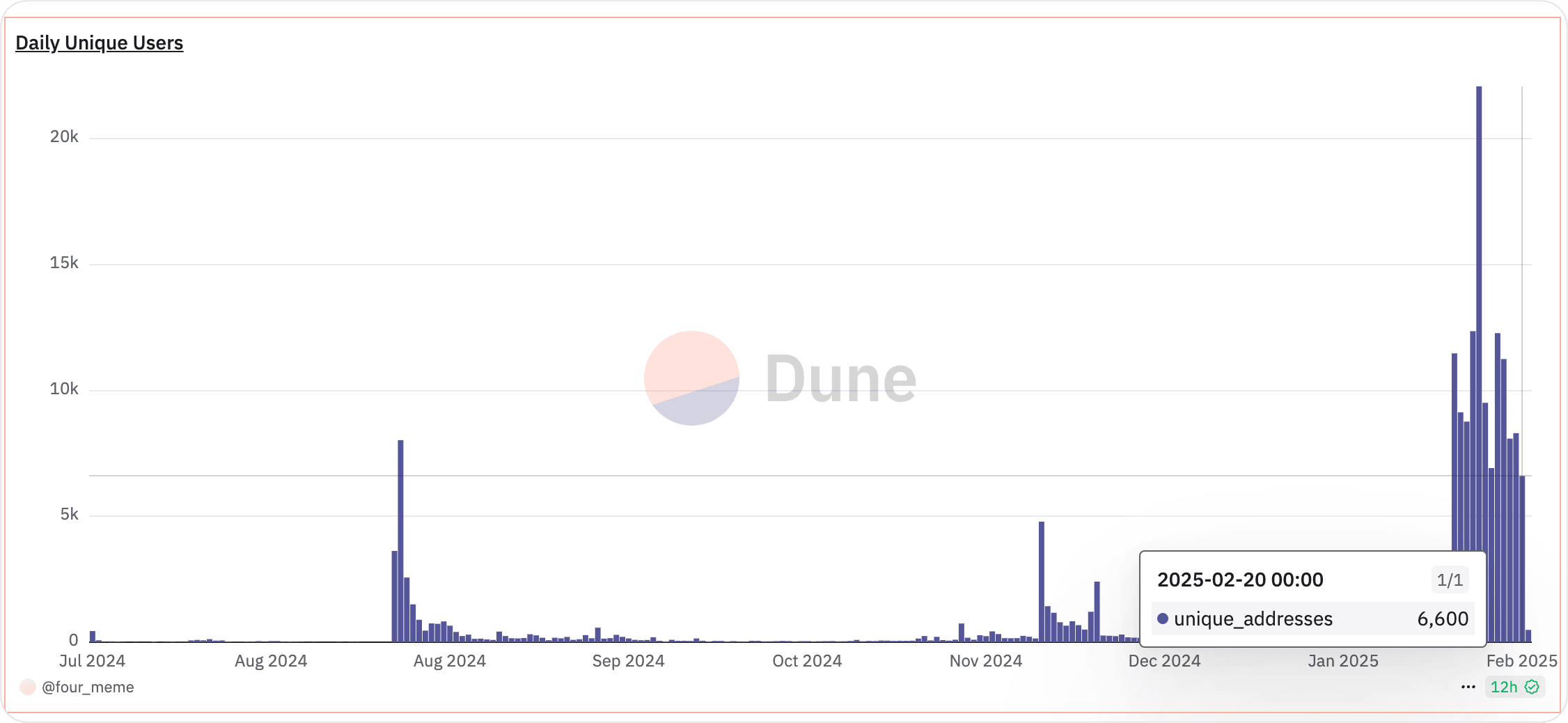
Moreover, as showing following, its trading volume has been hitting new highs lately, reflecting its rapidly growing popularity.
Sandwich Attack
Meanwhile, sandwich attacks have been on the rise, as malicious traders exploit transaction ordering on blockchains to maximize their profits at the expense of unsuspecting users.
Principle of Sandwich Attacks
In a sandwich attack, an attacker scans the mempool for a large or influential transaction. They then quickly place a transaction before the target (front-running) to push the price higher, allow the victim’s transaction to execute at this unfavorable price, and finally place another transaction immediately after (back-running) to sell at the now-inflated price. This “sandwich” of trades allows the attacker to pocket the price difference.
A Real Example
In the following, we will use a real example which happened recently.
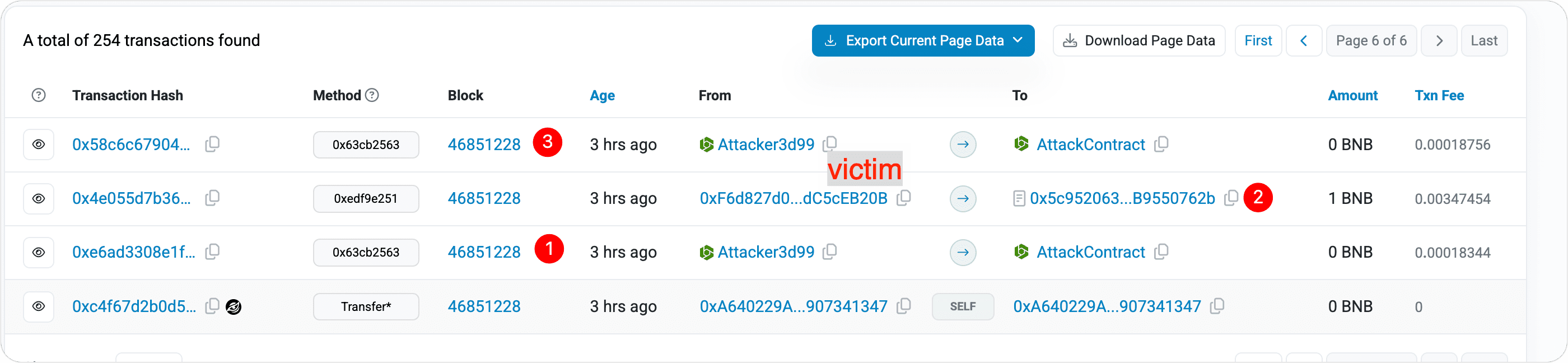
Tx1
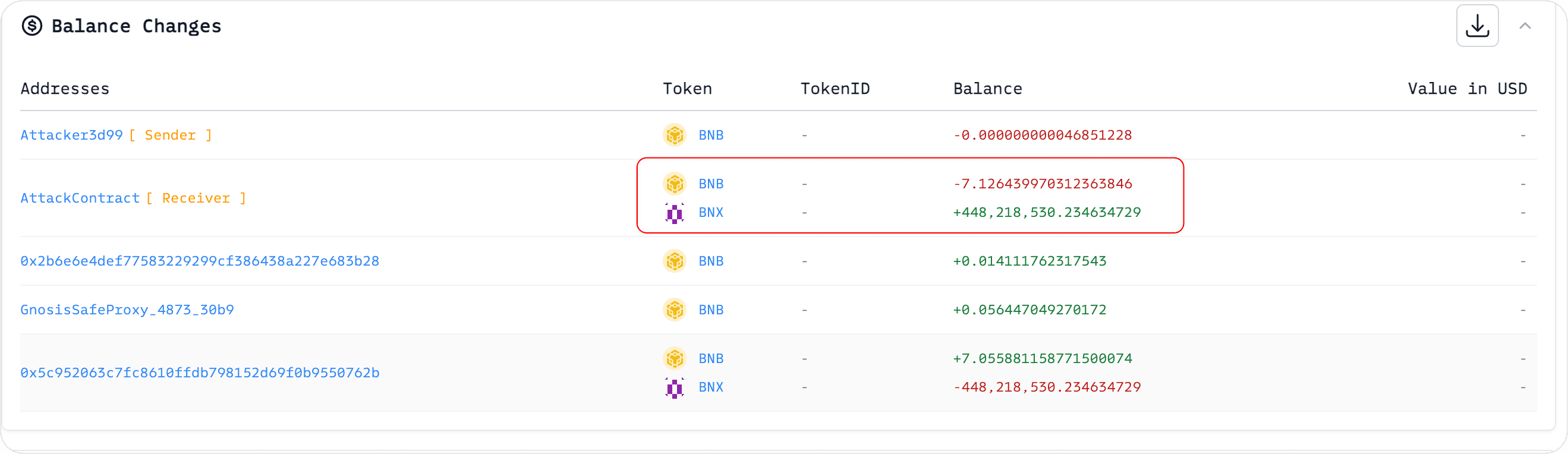
The attacker, knowing the victim intended to buy BNX, preemptively spent 7.126439970312363846 BNB to acquire 448,218,530.234634729 BNX tokens in advance.
TX2
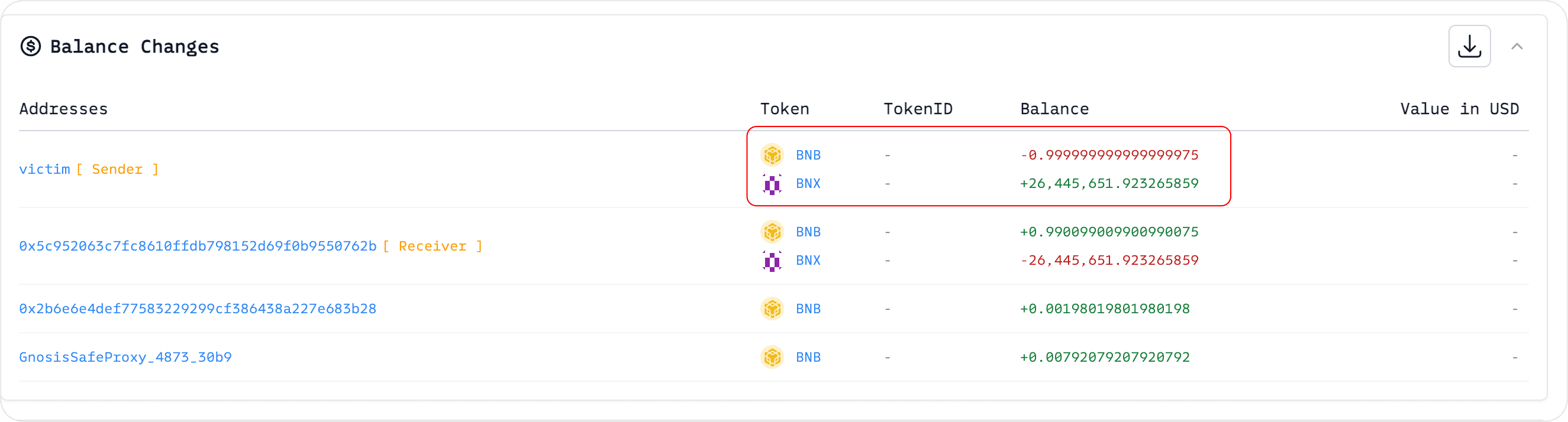
The victim spent 1 BNB to purchase 26,445,651.923265859 BNX tokens.
TX3:
Since the victim’s purchase with BNB drove up BNX’s price, the attacker then sold BNX at a higher rate for profit. Through this sandwich attack, the attacker gained 7.130040296271196866 BNB - 7.126439970312363846 BNB = 0.00360032595883302 BNB.
In this scenario, the victim (wallet 0xf6d827d0a4ee02a424ec85a3bcb8dc7dc5ceb20b) ended up paying a higher price for BNX because, without the attacker’s first trade, the victim could have purchased BNX more cheaply.
How to Avoid Becoming a Victim of a Sandwich Attack
To evade sandwich attacks, the key is preventing attackers from detecting your transaction before it’s included on-chain. One effective approach involves submitting trades through private relays or protected mempools, where transactions remain hidden until they’re finalized in a block. This makes it harder for malicious actors to front-run and back-run your trade.
To address this, BlockSec has introduced an MEV protection RPC that shields users throughout their DeFi journey. Switching to BlockSec’s ANTI-MEV RPC is easy—just replace your wallet’s RPC with https://bsc.rpc.blocksec.com.
Below, we’ll demonstrate how to configure MetaMask to use BlockSec’s ANTI-MEV RPC; other wallets may follow a similar setup process.
Step 1: click on the top left to show the networks.

Step 2: Edit the network

Step 3: Click to add the RPC URL


Input https://bsc.rpc.blocksec.comfor BSC (or https://eth.rpc.blocksec.comfor Ethereum).
Ensure that the default RPC URL is the one we just set.

summary
Sandwich attacks can inflate token costs for unsuspecting traders, especially in hype-driven environments like Four.meme. Attackers front-run pending trades and quickly sell for profit, leaving victims to pay higher prices.
By switching to BlockSec’s anti-MEV RPC (https://bsc.rpc.blocksec.com), you hide your transaction data from these malicious bots. This approach reduces the risk of sandwich attacks so you can trade more safely on Four.meme.




