Overview
Recently, Web3 phishing websites have caused losses totaling millions of dollars for numerous users. On these phishing websites, users unknowingly sign transactions that authorize their tokens to be transferred to accounts controlled by scammers. To protect users from phishing attacks, many Web3 wallets have implemented a blacklist mechanism to proactively block transactions involving known phishing accounts.
However, according to our observations, this strategy has proven to be ineffective in blocking phishing accounts. Scammers have developed several methods to bypass this security mechanism. The first method involves using the Create2 function to predict the address of a phishing contract and then deploying the phishing contract after successfully stealing tokens. The second method is to deploy new phishing contracts daily, at a rate that outpaces the updates to the blacklist.
Existing Wallet Security Alert Mechanism

The security alert mechanism within the wallet includes checks for both websites and accounts. Currently, all such systems maintain blacklists for website domains and accounts. When a user visits a website, the wallet checks if the domain is on the blacklist. If it is, access to the website is denied. Similarly, before a user signs a transaction, the wallet verifies whether the account involved in the transaction is blacklisted. If it is, the transaction is blocked to prevent the user from proceeding. These security features are exemplified by systems such as MetaMask.
Leveraging Create2 to Bypass Security Alert
The Create2 opcode in Ethereum allows for the prediction of contract addresses before their actual deployment. This is accomplished using the formula:
address = hash(deployer address, bytecode, salt)With the deployer's address, the bytecode of the contract, and a specified salt value, it becomes possible to determine the contract address in advance.
Obviously, with the deployer address, the bytecode, and a salt value, we can predict the contract address before deployment. On the phishing website, users are prompted to send ETH or approve tokens to an Externally Owned Account (EOA), which is anticipated through Create2 and not in the blacklist. Subsequently, upon successful token theft, the phishing contracts will be deployed, and the victims' tokens will be transferred to another account for further processing. The entire process occurs automatically.
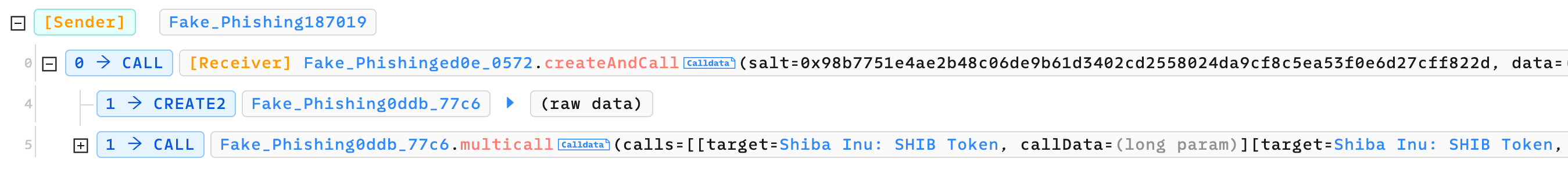
Here's an example demonstrated by Phalcon Explorer:
The phishing website initially requests users to approve tokens to 0x0ddb. Then, the scammer launches a phishing transaction, which consists of two internal transactions. The first internal transaction deploys the phishing contract using Create2. The second internal transaction invokes the phishing contract to transfer the victims' tokens.
Deploying Phishing Contracts Frequently to Bypass Security Alerts
Due to the brief period between phishing contract deployment and blacklist updates, scammers can exploit this gap to circumvent security alerts. They achieve this by deploying new phishing contracts daily. Consequently, when users visit phishing websites, these contracts are not yet blacklisted, thereby evading alerts in certain wallets.
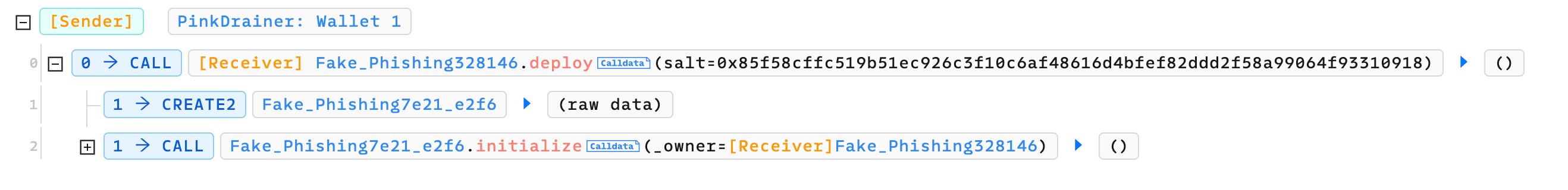
Here's an example case of Pink Drainer illustrated by Phalcon Explorer. The Deploy function of 0x5d77 is invoked on a daily basis to deploy new phishing contracts.
Summary
Phishing website developers are constantly creating new strategies to evade the security detection mechanisms employed by Web3 wallets. We remain vigilant, persistently monitoring their latest tactics. We urge users to exercise caution and meticulously review transaction details before signing transactions.
Related Reading
About BlockSec
BlockSec is a pioneering blockchain security company established in 2021 by a group of globally distinguished security experts. The company is committed to enhancing security and usability for the emerging Web3 world in order to facilitate its mass adoption. To this end, BlockSec provides smart contract and EVM chain security auditing services, the Phalcon platform for security development and blocking threats proactively, the MetaSleuth platform for fund tracking and investigation, and MetaSuites extension for web3 builders surfing efficiently in the crypto world.
To date, the company has served over 300 esteemed clients such as MetaMask, Uniswap Foundation, Compound, Forta, and PancakeSwap, and received tens of millions of US dollars in two rounds of financing from preeminent investors, including Matrix Partners, Vitalbridge Capital, and Fenbushi Capital.
Official website: https://blocksec.com/
Official Twitter account: https://twitter.com/BlockSecTeam




