DeFi hacks are still happening. For the stolen funds of the DeFi projects, it’s usually hard to recover them. Some projects negotiate with the hacker to offer a bounty and promise the drop of legal actions. It works sometimes but set up a bad example. It likes to encourage people to hack to get a bounty, instead of responsible discourse.
BlockSec has taken a different approach to help multiple projects recover their stolen funds. Besides the usual way to track the fund flow and cooperate with centralized entities like exchanges, we want to share our three success stories of recovering stolen funds purely through technical methods, including the recent Platypus Finance, TransitSwap, and Saddle Finance.
Platypus Finance: Rescued 2.4 Million USD
The Block has a good story on how our recovery of the funds for Platypusdefi works. Basically, the attacker made a mistake in that there is no way to move the funds from the attack contract. That’s because the attacker forgot to write the code logic to transfer the tokens from the attack contract.
However, our team found there is a way to leverage the existing code in the attack contract to move USDC from the contract to the project’s contract. Basically, the attacker contract has a function that if it was invoked, then the attack contract will approve a fixed number of USDC to the project’s contract. This code was used for the attack purpose. However, we can reuse this code logic to approve the USDC to the project’s contract, and then upgrade the project’s contract (it’s a proxy contract) to move the USDC from the attacker contract.
We evaluated this idea with our PoC and shared the information with Platypusdefi. We closely work with them and this method works! 2.4 million USDC has been recovered in the following transaction.
- https://phalcon.blocksec.com/explorer/tx/avalanche/0x5e3eb070c772631d599367521b886793e13cf0bc150bd588357c589395d2d5c3
- https://phalcon.blocksec.com/tx/avax/0x5e3eb070c772631d599367521b886793e13cf0bc150bd588357c589395d2d5c3
We have successfully recovered the 2.4 million USDC from the attacked contract: https://t.co/lpDYQtu9bf
— Platypus 🔺 (🦆+🦦+🦫) (@Platypusdefi) February 17, 2023
We would like to express our gratitude to @BlockSecTeam for their time and effort in helping us achieve a successful outcome. We are truly thankful for their assistance!
TransitSwap: Rescued 246K USD
The TransitSwap on BSC was attacked on October 1, 2022. Some attack transactions were front-run by a Bot.
However, we found that this bot was suspective to the profanity tool vulnerability. The vulnerability is due to insufficient randomness when generating the private key. We have developed a tool that can recover the private key of such vulnerable addresses.
We successfully recovered the bot’s private key. However, the fund is in the Bot contract, instead of the EoA. We managed to decompile the contract and find a function that can be used to transfer the funds.
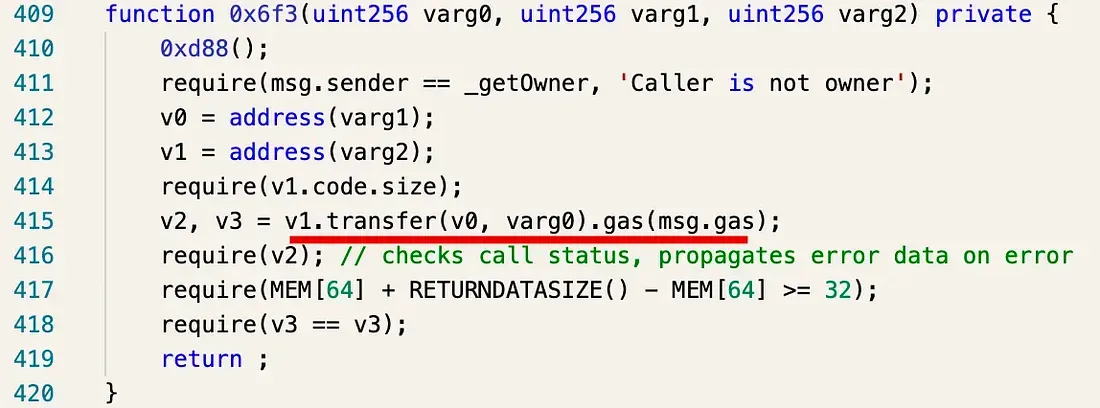
We have transferred the funds to the official TransitFinance Funds Receiver address.
📢📢📢Updates about TransitFinance
— Transit Swap | Transit Buy | NFT (@TransitFinance) October 6, 2022
With the help of BlockSec @BlockSecTeam, about $246K attacked by the 4th attacker has been fully refunded. https://t.co/G7iB3JvspP
Read more on How we recover the stolen funds for TransitSwap (and BabySwap)
Saddle Finance: Rescued 3.8 Million USD
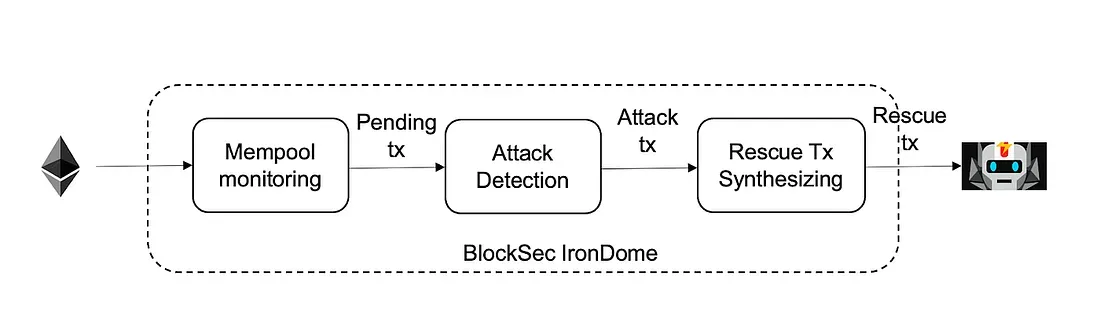
For the saddle finance, we took another way to perform the rescue. The basic idea is listening to the pending pool of Ethereum, detecting the attack transaction through our transaction pre-execution system Mopsus, and blocking the attack by automatically synthesizing a rescue transaction that will move vulnerable assets into our secure account, and front-running the attack transaction by FlashBot. The following figure shows the architecture.,
The following timeline shows how our system rescued 3.8 million USD for Saddle Finance at the end of April 2022. In particular, our system finished the whole process to detect the attack transaction and automatically synthesized the rescue tx in less than one second. We returned all the rescued funds to Saddle Finance. Click the link for the original hack tx and our rescue tx.
Read More: Securing Web3 Through Proactive Threat Prevention
Summary
The above three are only representative cases. In fact, we have more successful cases to rescue funds.
We always think the security of DeFi cannot be solved through a single methodology. There is no silver bullet. BlockSec has developed a couple of tools (and is developing more) and services to help secure the whole ecosystem. We have Phalcon, a transaction explore for BlockChain, security code audit service (Covering Solidity, Rust, Go and Move), and proactive attack mitigation services. We have built a couple of tools for crypto users to combat phishing attacks, including MetaSleuth, a crypto fund analysis tool, and MetaSuites, a browser extension for blockchain browsers. We continuously reported phishing URLs and addresses to MetaMask and Etherscan. BlockSec has collaborated with partners including Cronos, Forta, Tokenlon, KeyStone, Goplus, and more to secure the whole crypto ecosystem.
Do not hesitate to contact us if you have any questions.
Learn more about BlockSec: Website | Document | Twitter | Blog | TG Group




