The blog is published by BlockSec Team, Zhejiang University, China
On 16th Dec 2020, our monitoring system ThunderForecast reported a series of suspicious transactions. Then, we used the EthScope system developed by our research team to analyze these transactions and confirmed that all reported transactions are malicious. In this blog, we illustrate the attack with rich details to help understand the intention of each behaviour of the attacker.
What is Plouto Vault?
Plouto is an open decentralized asset management protocol. Plouto protocol comes up with a key idea called “Open Vault”. With this idea, except standard investing strategies, asset managers can also deploy their protocol with other third parties or even design their own strategies with Plouto Vault. In this attack, the attacker leveraged Plouto Vault’s vulnerability that the minting token amount depends on the corresponding token amount at the YPool. Finally, the attacker arb out a total of 698,775.32 USD.
Details
We now start revealing more details of this attack with one attack transaction 0x49112d…
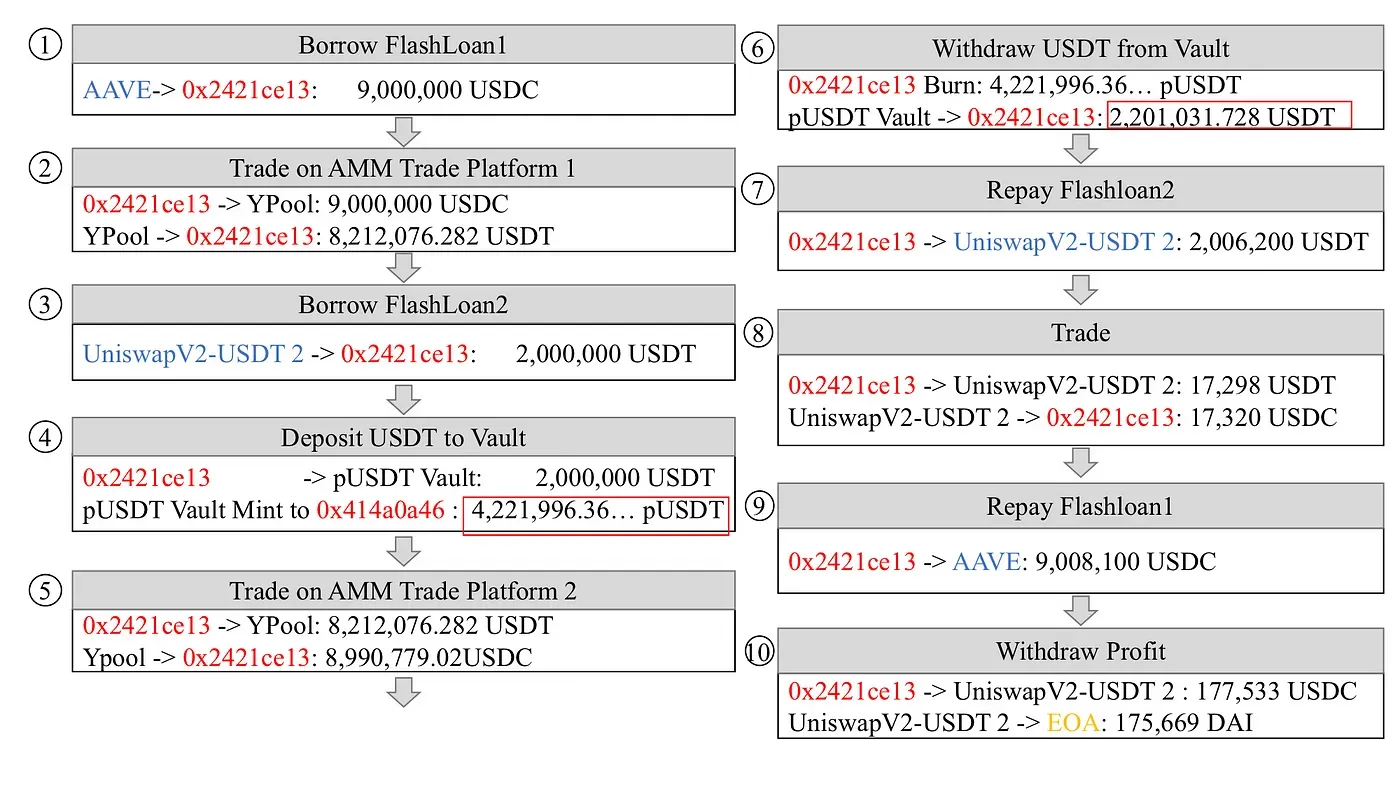
There are ten steps involved:
- Step 1: Take a flash loan of 9,000,000 USDC from AAVE.
- Step 3: Take a flash loan of 2,000,000 USDT from UniswapV2.
- Step 7: Return 2,006,200 USDT flash loan lent on UniswapV2.
- Step 8: Swap 17,298 USDT to 17,320 USDC at the UniswapV2-USDT pool. The exchanged USDC is used to pay back the first flash loan lent on AAVE.
- Step 9: Return 9,008,100 USDC flash loan lent on AAVE.
- Step 10: Swap 177,533 USDC to 175,669 DAI and send the profit to the attacker’s EOA.
Gain&Loss
In the transaction mentioned above, the attacker manipulates the liquidity of USDT at the YPool and arb out 175,669 DAI from Plouto Vault.
The scale of the attack
Based on the feature of the attack, we detect 1 malicious contract 0x2421ce… and 8 transactions(The largest profit gained in transaction 0x49112d… event reaches 175,669.88 USD) launched by the attacker 0x43c162…. According to the data on Ehterscan, The attacker arb out a total of 698,775.32 USD.
The End
With the development of the DeFi ecosystem on Ethereum and the continuous updating of DeFi services (Flash Loan), security issues have gradually become prominent. Behind this attack, Flash Loan provided a lot of “convenience” for the attacker to implement liquidity manipulation. Recently, Harvest platform suffered from an attack which leverages a strong dependency between contracts.
Timeline
- 2020/12/16: Found suspicious transactions
- 2020/12/17: Finished the analysis
- 2020/12/18: Details were released
About BlockSec
BlockSec is a pioneering blockchain security company established in 2021 by a group of globally distinguished security experts. The company is committed to enhancing security and usability for the emerging Web3 world in order to facilitate its mass adoption. To this end, BlockSec provides smart contract and EVM chain security auditing services, the Phalcon platform for security development and blocking threats proactively, the MetaSleuth platform for fund tracking and investigation, and MetaSuites extension for web3 builders surfing efficiently in the crypto world.
To date, the company has served over 300 esteemed clients such as MetaMask, Uniswap Foundation, Compound, Forta, and PancakeSwap, and received tens of millions of US dollars in two rounds of financing from preeminent investors, including Matrix Partners, Vitalbridge Capital, and Fenbushi Capital.
Official website: https://blocksec.com/
Official Twitter account: https://twitter.com/BlockSecTeam




