As DeFi and decentralized finance grow fast, more individuals and companies are using this new financial infrastructure every day. But with this growth comes real risk. When you use DeFi protocols and smart contracts, you face problems that traditional finance cannot handle. These include illicit fund flows, smart contract exploits, scams, phishing attacks, and real-time compliance gaps. Old security tools were not built for this kind of decentralized ecosystem.
Now imagine this. One unsafe transaction. One missed risk signal. That single event can lead to frozen accounts, regulatory pressure, loss of user trust, or even serious business disruption. What looks like growth today can quickly turn into an existential risk for your platform tomorrow.
This is where Phalcon Compliance comes in. Phalcon Compliance delivers enterprise-grade DeFi Safety with real-time AML/CFT monitoring, deep risk assessment, and regulator-ready reporting. You can detect risks before execution, protect users and wallets, and operate with confidence at scale.
Before we explain how Phalcon Compliance works, let’s step back.To understand DeFi Safety, you first need to understand how DeFi really works and why traditional security and compliance models fail in a decentralized world.
1.Status Quo: Why DeFi Safety Is the Question You Can’t Ignore?
If you are building, running, or integrating with DeFi today, you are no longer testing an experiment. You are operating real decentralized finance infrastructure. DeFi has moved far beyond early innovation. It now powers crypto exchanges, payment flows, lending and trading protocols, asset custody, and on-chain settlement at global scale.
For many platforms, DeFi is no longer optional. It is core infrastructure. As more capital, users, and institutions enter this ecosystem, the real question is no longer if risks exist, but rather, when they will appear. Smart contract vulnerabilities, exploits, illicit fund flows, and systemic failures are not edge cases. They happen again and again across DeFi protocols. These are real DeFi security risks, not theoretical problems.
In this environment, DeFi Safety becomes the key differentiator. It separates platforms that earn user trust and scale safely from those that collapse under pressure. Simply put: In decentralized finance, safety decides who can operate long term and who cannot.
2. Why DeFi Safety Matters?
DeFi is not just decentralized banking. It is automated financial infrastructure built on blockchains, smart contracts, and dApps. In traditional finance, banks and intermediaries act as a safety layer. They review transactions, apply manual controls, and fix problems after incidents happen. In decentralized finance, these buffers are gone. No intermediaries means no safety net. This creates a clear trade-off. On one side, you get transparency, permissionless access, and composability across protocols. On the other side, you face automatic execution, irreversible transactions, and a much larger attack surface.
DeFi runs on simple if–then logic. A smart contract follows code, not judgment.Once a transaction is approved, it executes. There is no pause button. That is why risk in DeFi cannot be fixed after the fact. There is no rollback. No manual review. No second chance. This is where DeFi Safety becomes a first-principles requirement. To stay secure, platforms need real-time risk monitoring, pre-transaction detection, and automated protection built directly into the transaction flow. Without this, long-term and sustainable operation in DeFi is simply not possible.
3. Major Risks in DeFi : Why DeFi Safety Fails Without Deep, Real-Time Risk Awareness?
The risks in DeFi are not abstract. They are real. And they happen often. Most DeFi security risks fall into four main categories:
-
Smart contract risks
-
Scams and malicious actors
-
Economic and Structural Risks
-
Cross-Chain and Bridge Risks
Each category alone can cause major losses. Together, they explain why DeFi Safety is no longer optional. It is an urgent requirement for anyone operating in decentralized finance.
Smart Contract Risks
Smart contracts sit at the core of every DeFi protocol. They replace human judgment, institutional controls, and legal enforcement with code. This automation is what allows decentralized finance to scale. But it is also the source of its most serious security vulnerabilities.
Bugs, Logic Flaws, and Exploitability
Smart contracts are software. There is no perfect software.
Even well-audited protocols can contain hidden risks, such as:
-
Implementation bugs introduced during development
-
Logic flaws where incentives break under edge cases
-
Unchecked conditions that attackers can manipulate
-
Integration risks from external contracts or oracles
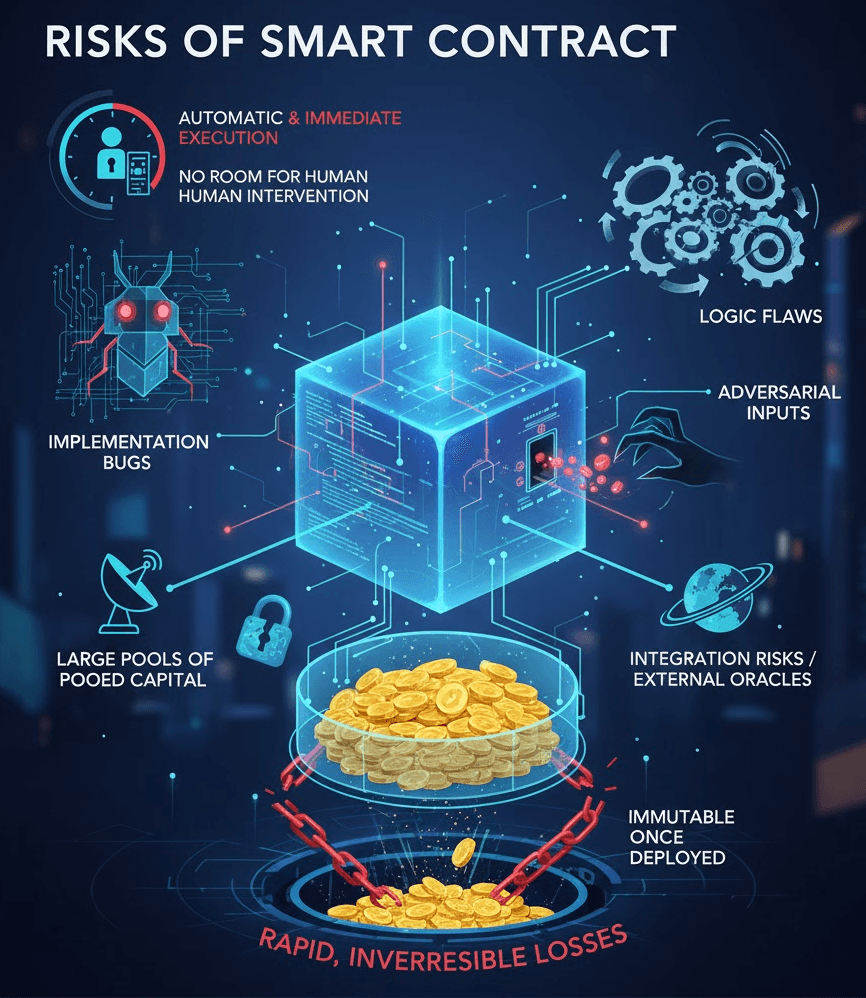
In DeFi, these flaws are amplified by three factors.
First, contracts are immutable once deployed or extremely costly to upgrade safely. Second, they often control large pools of pooled capital, making them attractive attack targets. Third, execution is automatic and immediate, leaving no room for human intervention once an exploit path is discovered.
Scams and Malicious Actors
Smart contract risks start in code. But scam-related risks start with people. In DeFi, exploiting human behavior is cheap and highly effective. There are no gatekeepers.
No identity checks by default. This makes scams, phishing, and social engineering some of the most common DeFi security threats today.
Common Scam Patterns in DeFi
DeFi’s permissionless nature enables a wide range of malicious tactics, including:
-
Honeypot contracts, where funds can be deposited but not withdrawn
-
Phishing attacks that trick users into signing malicious approvals
-
Fake protocol interfaces designed to imitate legitimate platforms
-
Impersonation and fake support accounts posing as official representatives
These attacks are not isolated incidents. They run at scale, across multiple chains, and evolve faster than public warnings. By the time one scam is exposed, new versions are already live.
Social Engineering at Scale
Scammers now rely heavily on social engineering. They target users through Telegram, Discord, and X (Twitter) direct messages. These channels help attackers build trust, create urgency, and push users to act fast. In DeFi, a single bad decision is often enough. One malicious signature. One unsafe approval. That is all it takes to drain a wallet.
For institutions, these attacks extend beyond individual users. Attackers target operational wallets, hot wallets used for liquidity or settlement and employees with signing authority. This turns social engineering from a consumer problem into a serious enterprise DeFi Safety issue. It affects users, funds, and platform trust at the same time.
On-Chain Laundering Amplifies the Threat
The real danger often comes after the initial theft. Illicit funds rarely stay in one place.They are quickly:
-
Split across multiple addresses
-
Routed through mixers or privacy protocols
-
Bridged across chains
-
Recombined through liquidity pools or aggregators
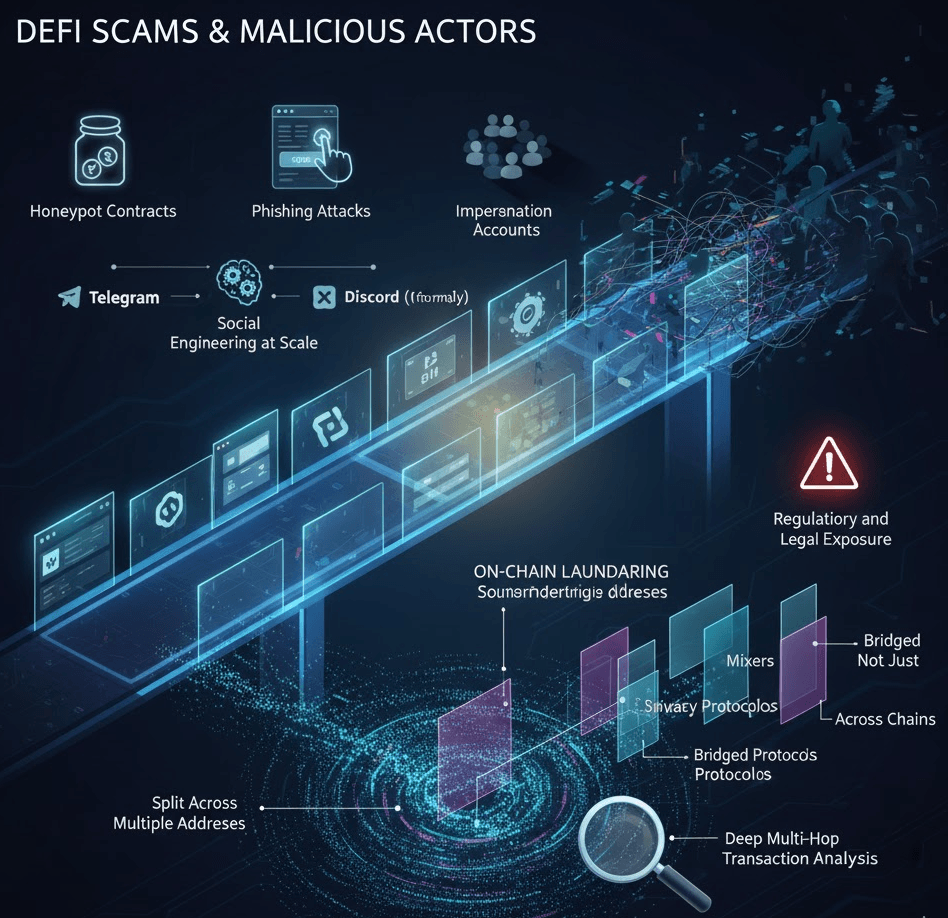
This process hides fund origin and breaks simple tracking. Without real-time monitoring, deep transaction analysis, and cross-chain detection, platforms may accept illicit funds without knowing it. That is how DeFi scams turn into compliance risk, regulatory exposure, and long-term damage to your ecosystem.
Economic and Structural Risks
Beyond code vulnerabilities and scams, DeFi carries risks that are economic and structural in nature. These risks emerge not from malicious intent, but from flawed assumptions, incentive misalignment, or system design failures.
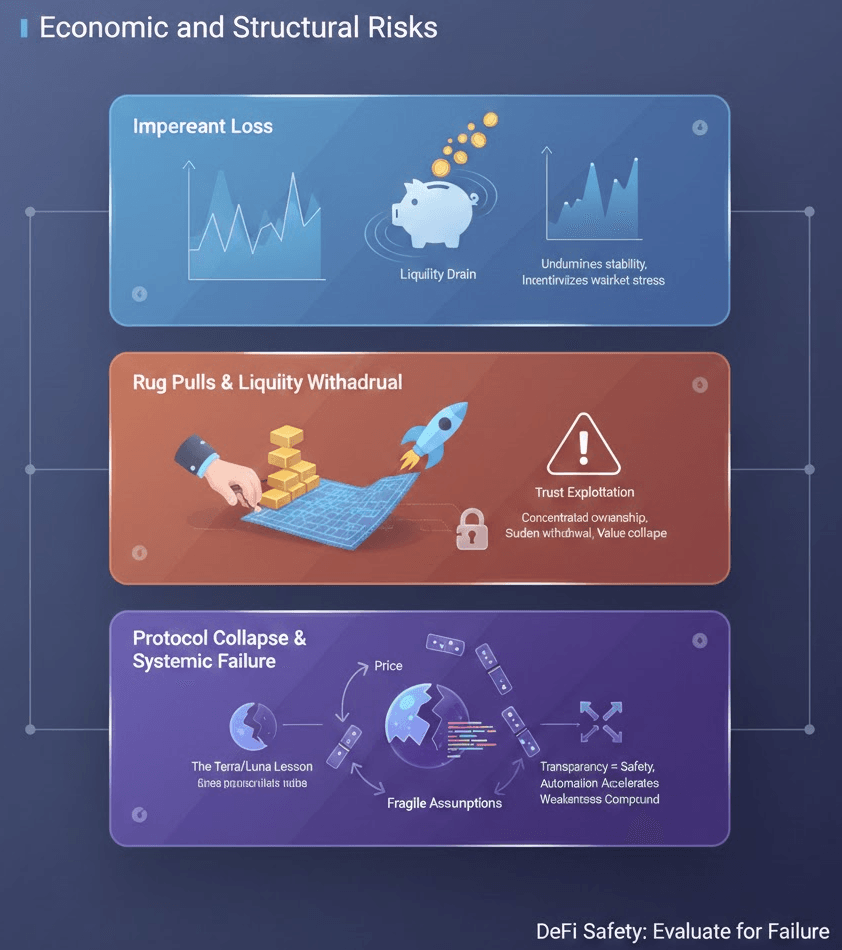
Impermanent Loss
Impermanent loss is a well-known risk for liquidity providers, but its implications are often underestimated.
When assets in a liquidity pool change in relative price, liquidity providers may end up with fewer valuable assets than if they had simply held them. While trading fees can offset this effect, they do not eliminate it, especially during periods of high volatility.
At scale, impermanent loss can:
-
Undermine liquidity stability
-
Incentivize rapid capital withdrawal
-
Exacerbate market stress during downturns
For protocols and platforms that rely on deep liquidity, impermanent loss becomes a systemic risk, not just an individual one.
Rug Pulls and Liquidity Withdrawal
Rug pulls represent one of the most damaging classes of DeFi failures.
They typically involve:
-
Concentrated token ownership
-
Control over liquidity pools
-
Sudden withdrawal of base assets
-
Collapse of token value
What distinguishes rug pulls from simple scams is that they often appear legitimate initially, exploit trust built through marketing or partnerships and use protocol mechanics as the attack vector.
For users and institutions alike, rug pulls highlight a critical DeFi Safety lesson: technical functionality does not guarantee economic integrity.
Protocol Collapse and Systemic Failure
The most severe DeFi risks occur when entire systems fail, not just individual components.
Protocol collapses often involve:
-
Feedback loops between price, collateral, and incentives
-
Overreliance on a single asset or mechanism
-
Inability to absorb shocks during stress events
The Terra/Luna Lesson
The collapse of Terra/Luna remains the most instructive example of systemic DeFi failure.
Despite transparent mechanics and widespread adoption, the system relied on fragile assumptions about market behavior and demand elasticity. When those assumptions broke, the collapse cascaded rapidly, wiping out tens of billions in value.
The key lesson for DeFi Safety is clear:
-
Transparency does not prevent failure
-
Automation accelerates failure once it begins
-
Structural weaknesses compound under stress
DeFi systems must be evaluated not only for how they function in normal conditions, but for how they behave when assumptions fail.
Cross-Chain and Bridge Risks
As DeFi becomes increasingly multi-chain, bridges have emerged as one of the most critical risk vectors.
Bridges often rely on:
-
Complex validator or relayer systems
-
External trust assumptions
-
Liquidity pooling across chains
Failures or compromises at the bridge layer can lead to:
-
Large-scale fund losses
-
Rapid cross-chain laundering
-
Fragmented visibility into fund provenance
From a DeFi Safety perspective, cross-chain activity amplifies risk by:
-
Breaking linear transaction visibility
-
Allowing attackers to “reset” exposure across networks
-
Increasing dependency on external systems beyond the core protocol
Effective DeFi Safety must therefore extend across chains, not remain isolated within a single network.
Why These Risks Redefine DeFi Safety
Taken together, these risks fundamentally redefine what safety means in decentralized finance.
Rather than regarded as a checklist or a one-time audit, DeFi is the ability to detect risks in real time, understand fund provenance and exposure, respond proportionally before damage occurs and operate sustainably under adversarial conditions.
In a system where execution is automatic and outcomes are irreversible, risk awareness must be continuous and deeply contextual. This is why DeFi Safety has become the central problem for the next phase of on-chain finance and why solving it correctly determines who can operate at scale, and who cannot.
4. Why Traditional DeFi Safety Approaches Fail
Why DeFi Safety Cannot Rely on Web2-Era Risk Models
Nowadays, many teams still attempt to secure their systems using traditional risks and compliance approaches. Static blocklists, one-time screening, and manual review processes are familiar tools from Web2 finance, and at first glance, they seem applicable.
However, when applied to decentralized systems, these methods consistently fail. The reason is about a fundamental mismatch between how DeFi works and how traditional safety models were designed. Understanding this mismatch is essential to understanding why DeFi Safety requires an entirely different approach.
Static Blocklists
Static blocklists are one of the most common safety mechanisms inherited from traditional finance. They rely on maintaining lists of known malicious, sanctioned, or high-risk addresses and blocking interactions with them.
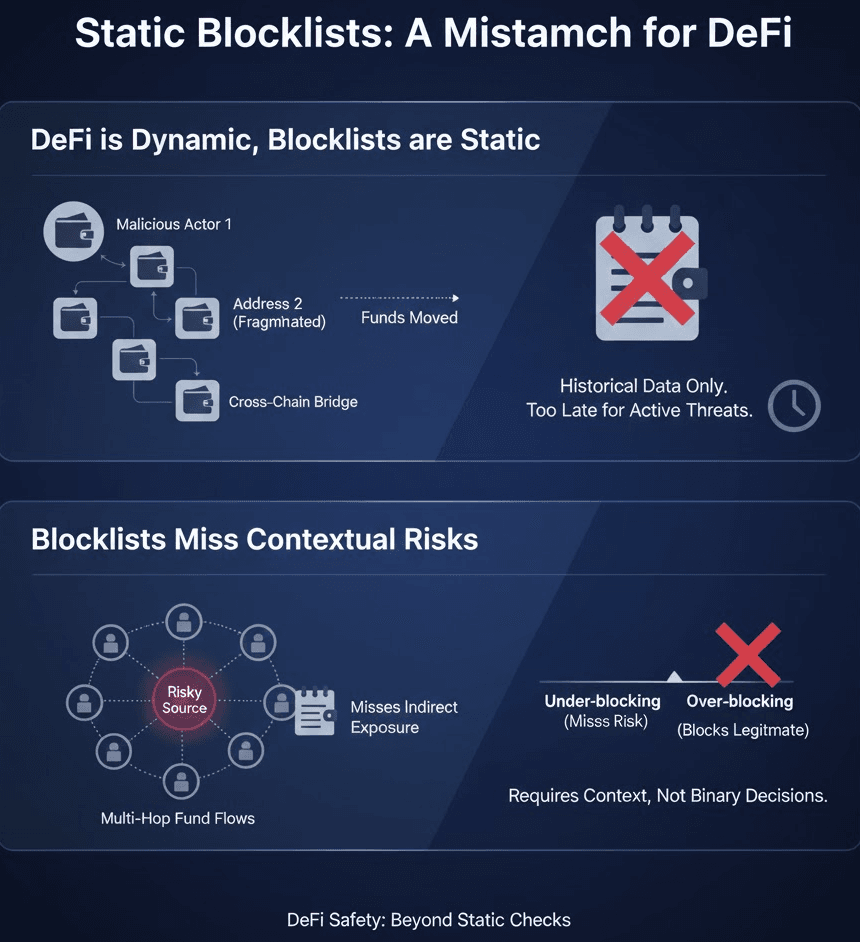 In DeFi, this approach breaks down almost immediately.
In DeFi, this approach breaks down almost immediately.
DeFi Is Dynamic Whereas Blocklists Are Static
On-chain identities are fluid. Creating new addresses is trivial, and malicious actors routinely rotate addresses, fragment funds across many wallets, use intermediaries to confuse origin, bridge assets across chains to reset visibility.
A blocklist only captures historical risks, not active or emerging threats. By the time an address is flagged, funds have usually already moved. From a DeFi Safety perspective, this is too late.
Blocklists Miss Contextual Risks
More importantly, blocklists operate at the address level, not at the fund-flow level. They cannot explain whether an address is indirectly exposed to illicit funds, how many hops separate current funds from risky sources, what percentage of assets are tainted, and whether exposure is historical or ongoing effective DeFi Safety depends on context, not binary decisions. Static blocklists force platforms to choose between under-blocking (missing real risk) and over-blocking (destroying legitimate activity).
One-Time Screening
Another common practice is one-time screening, checking an address or transaction once, usually at onboarding or deposit, and assuming that risk status remains unchanged.
This model fundamentally misunderstands how risk behaves in DeFi.
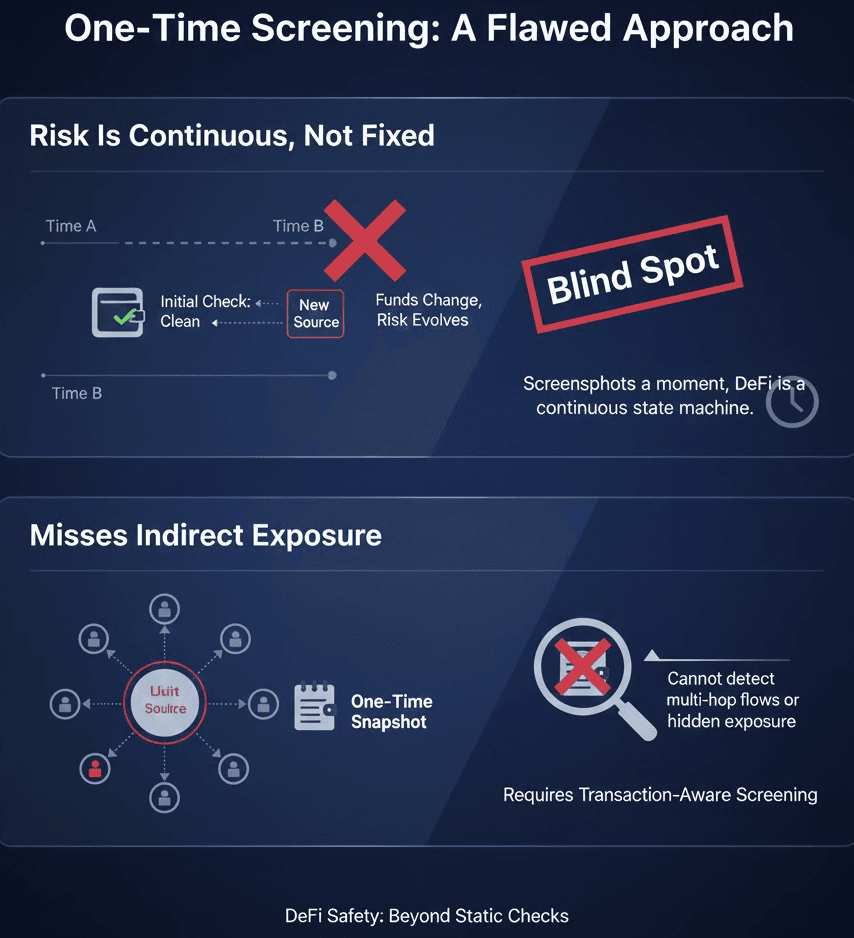
Risk in DeFi Is Continuous, Not Fixed
In decentralized finance, risk is not a static attribute of an address. It evolves constantly as new funds enter a wallet, counterparties change, protocol interactions occur, and indirect exposure accumulates over time.
An address that appears clean today may become risky tomorrow. One-time screening freezes risk assessment at a single moment, while DeFi operates as a continuous state machine.
From a DeFi Safety standpoint, this creates blind spots that attackers actively exploit.
One-Time Screening Misses Indirect Exposure
Most serious DeFi incidents do not involve direct interaction with known bad actors. Instead, they involve multi-hop fund flows, liquidity pool exposure, cross-chain movement and delayed laundering strategies.
A snapshot check cannot detect these patterns. True DeFi Safety requires continuous transaction-aware screening, not isolated checks.
Manual Review
When automated systems fail to provide confidence, teams often rely on human analysts. In traditional finance, manual review is a critical layer of defense.
In DeFi, manual review is structurally incompatible with the system itself.
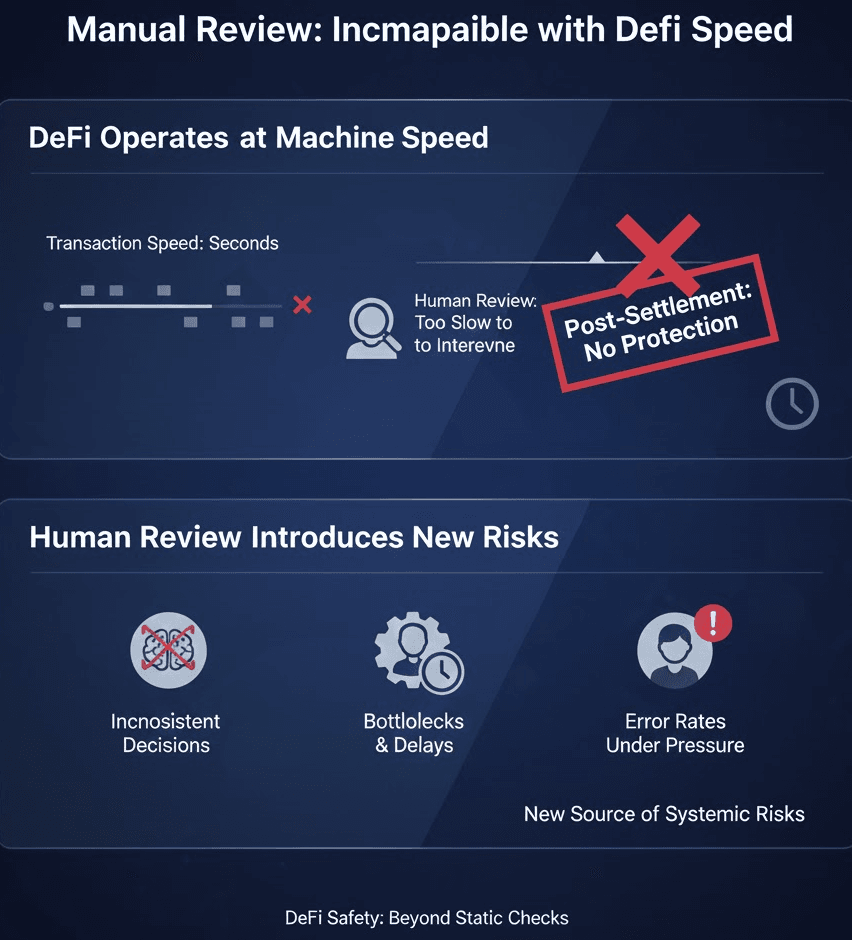
DeFi Operates at Machine Speed
Transactions in DeFi settle within seconds. Automated trading systems, bots, and smart contracts operate continuously, across multiple chains, at volumes that exceed human capacity.
Manual review cannot intervene before settlement, scale with transaction throughput and respond in real time.
By the time a human evaluates a transaction, execution has already occurred. From a DeFi Safety perspective, post-settlement review is not protection.
Human Review Introduces New Risks
At scale, manual processes introduce inconsistent decisions, operational bottlenecks, delayed response during high-volume periods, increased error rates under pressure.
Instead of improving safety, manual review becomes a new source of systemic risks.
Web2 Risk Management
The most important reason traditional approaches fail is conceptual. DeFi Safety is not Web2 risk management applied to blockchain.
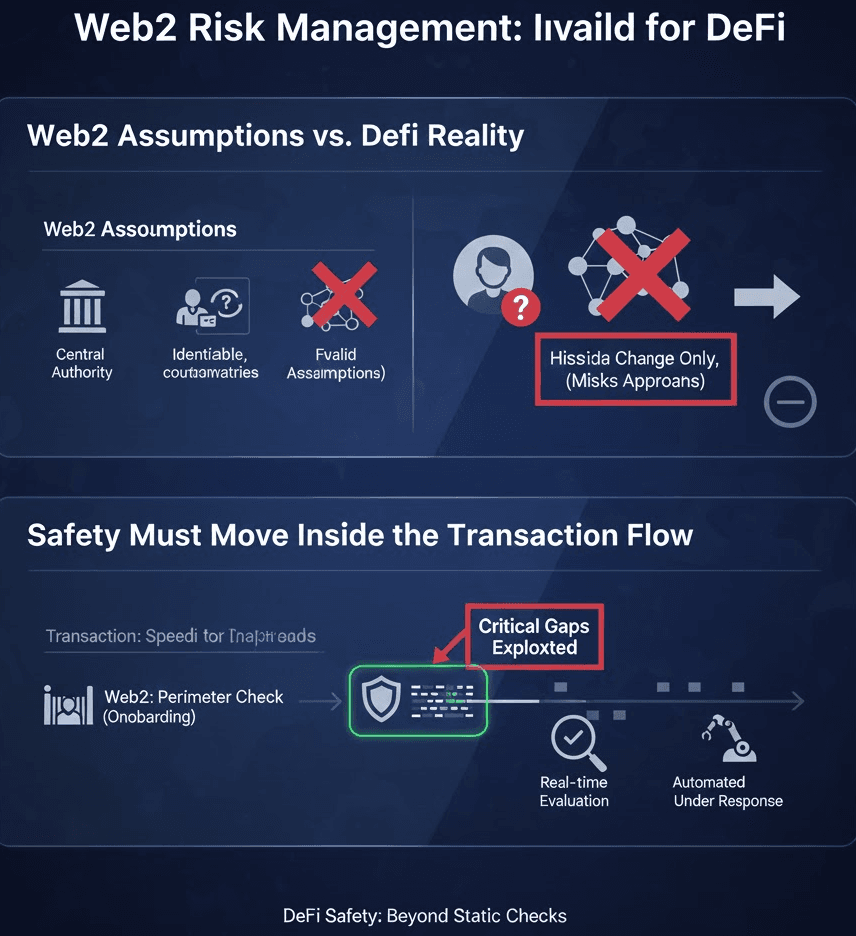
Web2 Assumptions Do Not Hold in DeFi
Traditional financial risk models assume stable, identifiable counterparties, centralized enforcement points, reversible transactions, and layered institutional oversight.
DeFi assumes the opposite pseudonymous participants, no central authority, irreversible execution, and autonomous, code-driven enforcement.
Applying Web2 controls to DeFi is ineffective since the underlying assumptions are invalid. DeFi Safety must be native to on-chain behaviors, not adapted from off-chain systems.
Safety Must Move Inside the Transaction Flow
In Web2 systems, safety often lives at the perimeter during onboarding or periodic reviews. In DeFi, safety must exist inside the transaction flow itself.
Effective DeFi Safety requires real-time risk evaluation before execution, continuous monitoring of fund movement, automated, proportional responses and explainable, regulator-grade evidence.
Anything less leaves critical gaps that attackers and systemic failures will exploit.
What This Means for DeFi Safety
The failure of traditional approaches does not mean DeFi cannot be secured. It means DeFi Safety must be rethought from first principles.
Strong DeFi Safety is:
-
Dynamic, not static
-
Continuous, not one-time
-
Automated, not manual
-
Contextual, not binary
-
Designed for on-chain systems, not borrowed from Web2
As decentralized finance becomes permanent infrastructure, safety must evolve with it. Platforms that continue to rely on legacy models will struggle to scale sustainably.
DeFi Safety is no longer about adapting old tools, but rather building systems that understand how value actually moves on-chain.
5.How to Evaluate DeFi Safety?
If static blocklists and one-time audits are insufficient, the next question is clear:What signals actually indicate DeFi Safety?
Key indicators include:
-
Audit depth and recency, not just audit presence
-
Bug bounty programs and incident response history
-
Upgradeability and admin key design, including multisig and timelocks
-
Liquidity concentration and withdrawal behavior
-
Oracle dependencies and external integrations
-
Quality of documentation and threat modeling
No single signal guarantees safety.
DeFi Safety emerges from correlated signals, continuously monitored over time.
Practical DeFi Safety Checklist
Risk awareness alone is not enough. DeFi Safety ultimately comes down to what you do before, during, and after interacting with a protocol.
Before Interaction: Reduce Risk at the Entry Point
-
Verify the official domain and contract address from multiple sources
-
Review audit scope, recency, and known limitations
-
Check upgradeability, admin privileges, and pause mechanisms
-
Limit token approvals to the minimum required amount
-
Separate wallets by function (treasury, operations, testing)
During Interaction: Monitor What Actually Happens
-
Watch for unexpected approvals, transfers, or balance changes
-
Be cautious with transactions that introduce complex call paths or cross-chain steps
-
Treat any urgent prompts or unsolicited messages as suspicious
After Interaction: Close the Risk Window
-
Revoke unused or unlimited token approvals
-
Monitor post-transaction fund movements
-
Document incidents and response actions for future review or reporting
In DeFi, safety is not a one-time decision. It is a continuous operational discipline.
6. Why Phalcon Compliance can provide optimal solutions to DeFi Safety?
DeFi Safety does not break because teams are careless or unprepared.It breaks because most security and compliance models were designed for systems that behave very differently from DeFi.
DeFi is continuous, transaction-driven, allowing manual intervention. And it operates in an open environment shaped by real-time, adversarial behavior. In such conditions, safety cannot rely on static blocklists, one-time screening, or post-incident reviews. These controls react after risk has already materialized.
Effective DeFi Safety requires real-time, on-chain risk intelligence that understands how funds move, how exposure evolves, and how risk must be managed before execution. This is exactly the problem Phalcon Compliance is designed to solve.
What Real DeFi Safety Actually Requires
After understanding why traditional approaches fail, the next question becomes unavoidable: what does effective DeFi Safety actually require?
If DeFi operated like traditional finance, incremental improvements would be enough. But DeFi does not fail because of poor execution, but rather wrong safety model itself. Real DeFi Safety must be built around how value moves on-chain, not how risk was historically managed off-chain.
In this regard, DeFi Safety is not a single tool or control. It is a capability model. Platforms that operate safely over the long term share a common set of capabilities that allow them to understand risks before it materializes and respond proportionally in real time.
From Broken Models to a DeFi-Native Safety Framework
In previous sections, we established that static blocklists, one-time screening, and manual review fail because DeFi is:
-
Continuous, not episodic
-
Transaction-driven, not account-driven
-
Automated, not discretionary
-
Irreversible, not recoverable
As a result, DeFi Safety must shift from reactive control to real-time intelligence. The question is no longer how do we block bad actors, but rather how do we continuously understand, who we are interacting with, how funds are moving, and what risk we inherit if a transaction executes.
Answering this question requires five core capabilities.
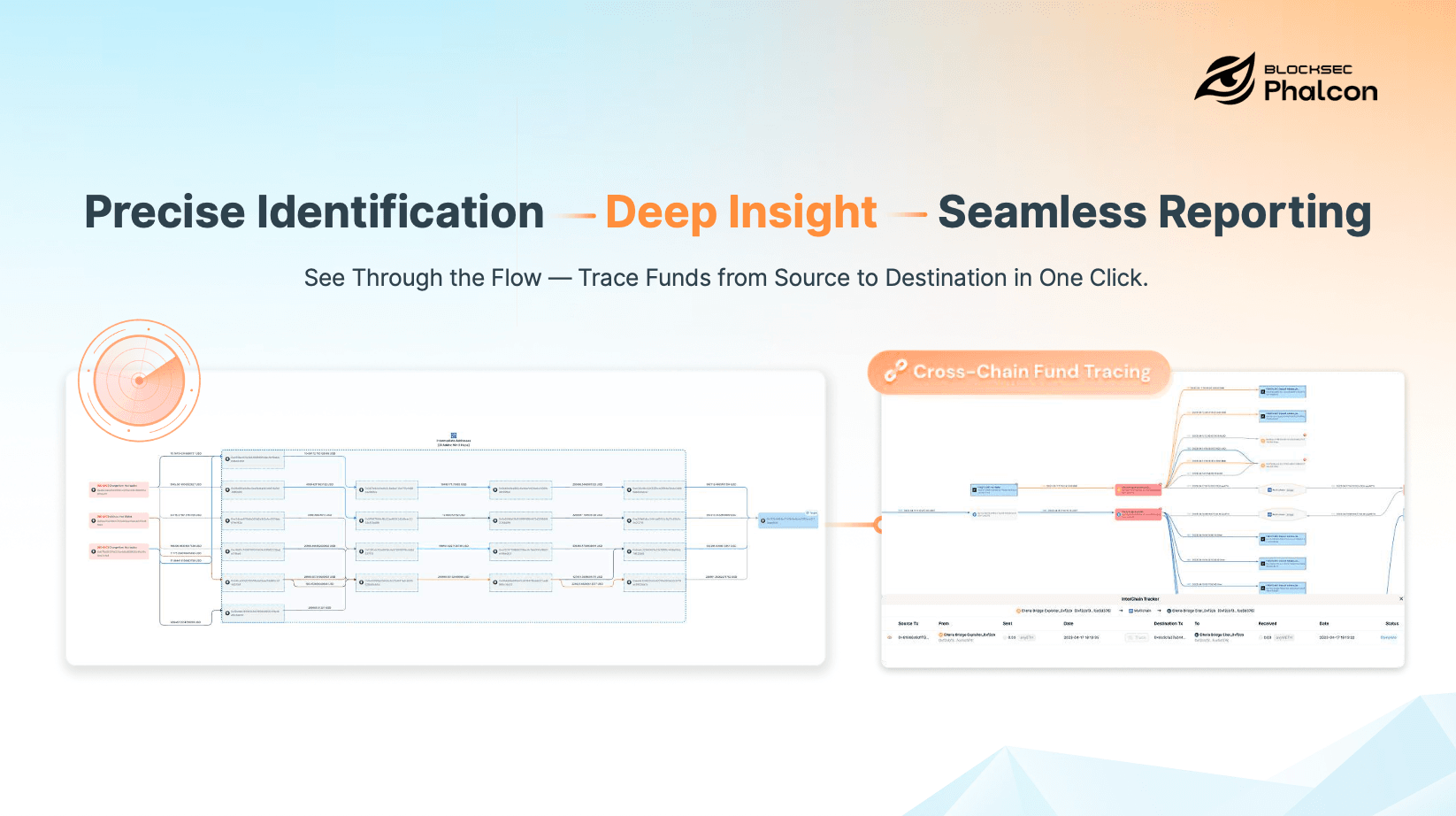
Precise Identification: Knowing Who You Are Really Transacting With
Every DeFi interaction begins with an address.
But an address alone tells you nothing.
In DeFi, Precise Identification means going beyond raw wallet addresses to understand who or what controls the address, what category it belongs to (exchange, mixer, protocol, scam, bridge, etc.), how it has behaved historically on-chain, and how it is viewed under regulatory and compliance frameworks.
 This is the foundation of Know Your Address (KYA).
This is the foundation of Know Your Address (KYA).
Without precise identification, DeFi Safety collapses into guesswork. Two addresses can look identical at the surface level while representing completely different risk profiles. One may be a liquidity pool contract; the other may be a laundering relay controlled by an illicit network.
DeFi Safety requires semantic understanding, not syntactic matching. You must know who you are dealing with before you can decide whether to interact.
Deep Insight: Understanding How Funds Actually Flow
Identification alone is not sufficient.
Most DeFi risks do not come from direct interaction with obviously malicious entities. It comes from indirect exposure, funds that have passed through multiple hops, protocols, or chains before reaching you.
This is where Deep Insight becomes critical.
Deep Insight means the ability to trace funds across multiple hops, quantify how much of a balance is tainted, distinguish between historical and active exposure, and aggregate risk across chains and protocols.
This capability is the core of Know Your Transaction (KYT).
In DeFi, risk is inherited. When you accept funds, you inherit the history embedded in those funds. Without deep transaction analysis, platforms are blind to this inheritance and may unknowingly facilitate laundering, sanctions evasion, or other illicit activities.
True DeFi Safety requires understanding how funds arrived, not just where they currently sit.
About Phalcon Compliance
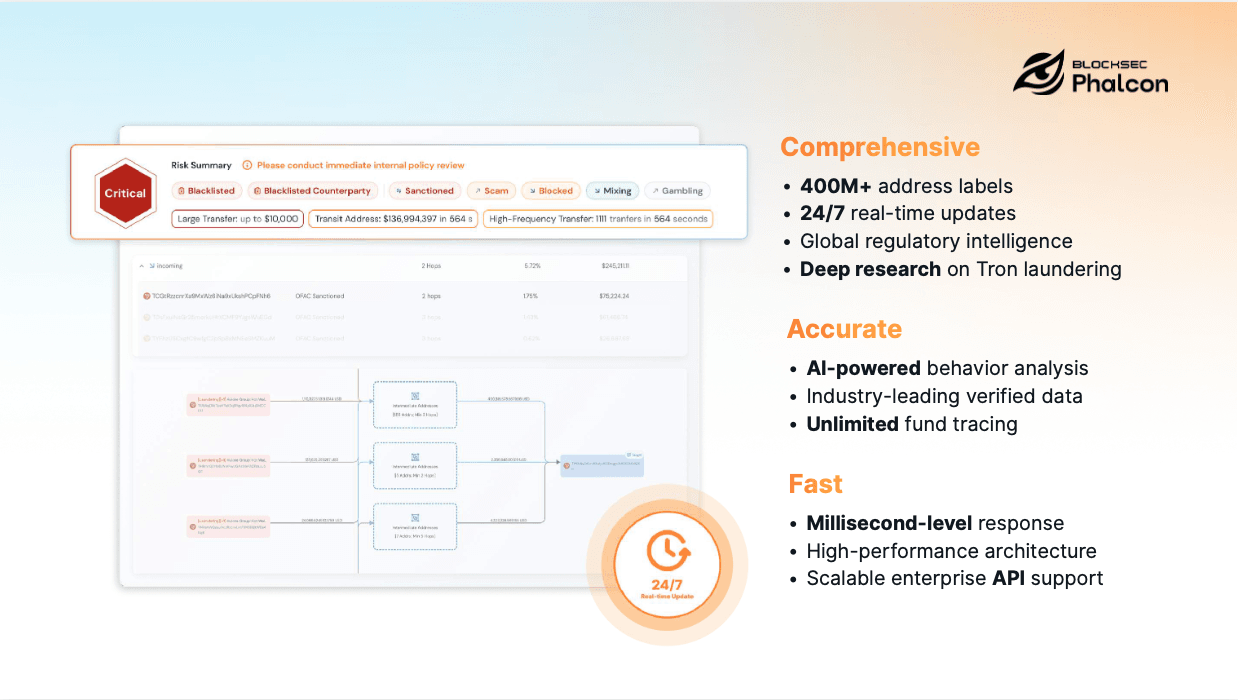
Phalcon Compliance is a Real-Time AML/CFT Solution for Crypto Compliance designed specifically for DeFi and institutional on-chain financial environments.
Rather than adapting Web2-era controls, it is built around the DeFi-native capability model described above address identification, deep transaction insight, real-time detection, proportional risk response, and regulator-grade evidence.
Phalcon Compliance operates at on-chain speed, supports institutional-scale transaction volume, and aligns with global regulatory expectations. It is designed for exchanges, payment providers, custodians, stablecoin issuers, and other platforms where DeFi Safety is not optional.
Importantly, Phalcon Compliance is not positioned as a single feature or dashboard. It functions as foundational safety infrastructure, enabling platforms to embed DeFi Safety directly into transaction flows rather than bolting it on after the fact.
7. Conclusion: DeFi Safety Is the Foundation, Not the Cost
DeFi Safety is not an operational cost, but a condition for long-term operation. In an environment defined by automation, irreversibility, and continuous risks, safety must be embedded directly into how value moves on-chain. Platforms that treat safety as foundational will scale with confidence. Those that treat it as an afterthought will eventually fail. This is where DeFi-native, real-time compliance infrastructure comes in and becomes essential. Phalcon Compliance, in particular, reflects this shift, not as products to be bolted on, but as systems that enable sustainable, defensible on-chain finance.
FAQ
1.How safe is DeFi?
DeFi is not inherently safe or unsafe. Unlike traditional finance, DeFi operates through open, automated smart contracts with no intermediaries, no manual intervention, and no transaction reversibility. This means risks are not absorbed by institutions but borne directly by users and protocols. From a DeFi Safety perspective, safety depends on protocol design, code quality real-time risk visibility, and how quickly risks are detected and mitigated. DeFi can be safe relative to its design assumptions, but it is never risk-free.
2.Is DeFi safer than centralized exchanges?
DeFi and centralized exchanges fail in fundamentally different ways. Centralized platforms expose users to custody and counterparty risk, account freezes or regulatory intervention, and opaque internal risk controls. DeFi removes custodial dependency but introduces smart contract risk, systemic and composability risk, and irreversible execution. From a DeFi Safety standpoint, neither model is universally safer. DeFi shifts risk from institutions to code, making transparency higher but requiring stronger real-time risk awareness.
3.Why do DeFi hacks still happen in 2025?
Because DeFi’s attack surface continues to expand. Even long-established protocols remain vulnerable. The Curve incident demonstrated that exploits can originate from deep dependency layers, such as compiler-level bugs, rather than protocol logic itself. This shows that audits do not eliminate all risk, hidden exploit paths can exist for years, and attackers continuously adapt.
4.Why is DeFi still so vulnerable to hacks?
This vulnerability is partly structural. DeFi is open-source by design, permissionless, automated and irreversible, and increasingly interconnected through bridges. While these traits enable innovation, they also reduce reaction time. Without real-time monitoring and transaction-level risk intelligence, platforms cannot respond before losses occur.
5.How can users and institutions stay safer in DeFi?
DeFi Safety cannot rely on static blocklists or one-time screening. Effective safety requires precise counterparty identification (KYA), deep, multi-hop transaction analysis (KYT), real-time detection before execution, proportional and risk-based responses, as well as explainable and regulator-grade evidence. The objective is not zero risk, but controlled, visible, and defensible risk.




