This series of articles, excerpted from the "Security Special Edition 05" co-curated by OKX Web3 and BlockSec, addresses the security concerns faced by DeFi users and DeFi project teams.
Q1: What criteria or metrics can be employed for a preliminary evaluation of a DeFi project's security and risk profile?
BlockSec Security Team: Before investing in a DeFi project, it is essential to conduct a comprehensive security assessment of the project. This is especially true for participants with larger amounts of capital, as the necessary due diligence in security can ensure the safety of funds to the greatest extent.
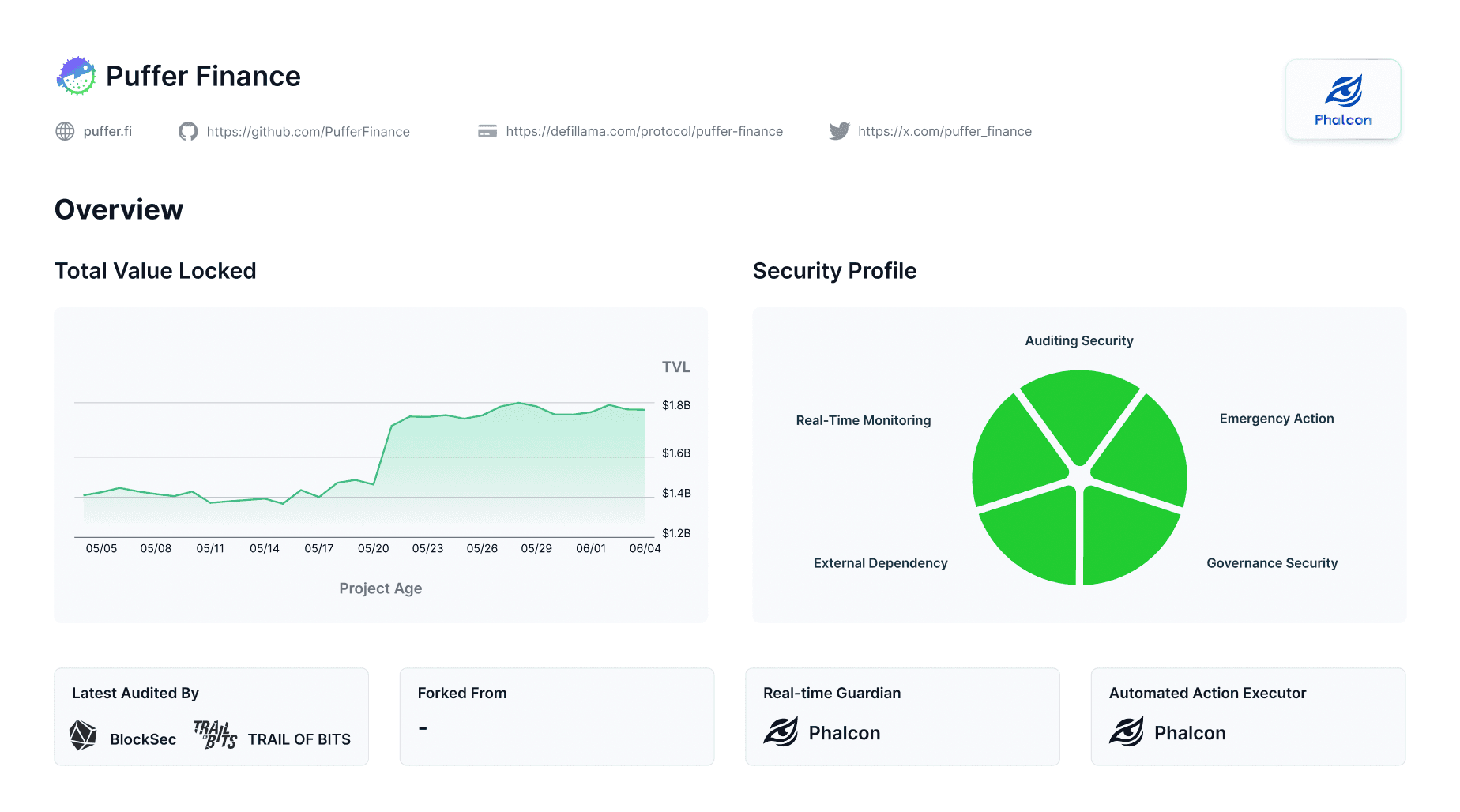
Firstly, it is recommended to conduct a comprehensive assessment of the project's code security, including whether the project has been audited by an audit company with a good security reputation, whether multiple audit companies are involved, and whether the latest code has been audited. Generally speaking, if the code running online has been audited by multiple security companies with a good reputation, it will greatly reduce the risk of security attacks.
Secondly, it is important to see whether the project party has deployed a real-time security monitoring system. Security audits ensure static security and cannot solve dynamic security issues caused after the project goes live. For example, if the project party improperly adjusts key operational parameters of the project or adds new pools. If the project party has adopted some real-time security monitoring systems, its operational security level will be higher than protocols that have not adopted such a solution.
Thirdly, access the project's capacity for automated emergency response, an aspect often overlooked. We've observed that in numerous security incidents, projects lack automatic circuit breakers for critical functions. Manual handling of emergencies has proven inefficient and sometimes ineffective.
Fourthly, scrutinize the project's reliance on external dependencies and their robustness. DeFi projects often depens on third-party data, like pricing and liquidity. Therefore, it is necessary to assess the project's security from the number of external dependencies, the security of the external dependency projects, and whether there is monitoring and real-time processing of abnormal data from external dependencies. Generally speaking, projects that depend on top-tier projects and have fault tolerance and real-time processing of abnormal data from external projects will be safer.
Fifthly, whether the project party has a relatively good community governance structure is crucial. This includes whether the project party has a community voting mechanism for major events, whether sensitive operations are completed with multi-signature, whether multi-signature wallets have introduced neutral community participation, and whether there is a community security committee, etc. These governance structures can improve project transparency and reduce the possibility of users' funds being rugpulled in the project.
Finally, the history of the project party is also very important. It is necessary to conduct background checks on the project team and core members. If the core members of the project party have a history of multiple attacks or rugpulls in previous projects, then the security risks of such projects will be relatively higher.
In summary, before participating in DeFi projects, users, especially those with large amounts of capital, should do their research, from the code security audit before the project goes live to the construction of real-time security monitoring and automatic response capabilities after the project goes live, to examine the project party's security investment and safety, and to conduct due diligence from the perspectives of external dependencies, governance structure, and the history of the project party to ensure the safety of funds invested in the project.
OKX Web3 Wallet Security Team : While absolute security in DeFi projects can't be guaranteed, users can gauge their secutiy and risk profiles by considering these key dimensions.
- Project Technical Security :
- 1)Check whether the project has been audited by multiple reputable and experienced audit firms.
- 2)Review the number and severity of issues reported in the audit reports and ensure all have been addressed.
- 3)Verify that the code deployed matches the version that was audited.
- Open Source Code :
- 1)Determine if the project's code is open source, allowing community and security experts to review and potentially find security issues.
- 2)Investigate the background of the development team, their experience in blockchain and security, and the level of transparency and public information available about the team.
- 3)Bug Bounty: Look for the presence of a bug bounty program to incentivize security researchers to report vulnerabilities.
- Financial and Economic Security :
- 1)Locked Funds: Examine the amount of funds locked in smart contracts, as higher amounts may indicate greater trust in the project.
- 2)Trading Volume and Liquidity: Assess the project's trading volume and liquidity; low liquidity may increase the risk of price manipulation.
- 3)Token Economic Model: Evaluate the tokenomics, including token distribution, incentive mechanisms, and inflation models, and check for overly concentrated token holdings, among other things.
- Operational and Management Security :
- 1)Governance Mechanisms : Understand the project's governance structure, whether it has decentralized governance, and if the community can vote on important decisions. Analyze the distribution of governance tokens and the concentration of voting power.
- 2)Risk Management Measures : Determine if the project has risk management measures and contingency plans to address potential security threats and economic attacks. Also, consider the project's transparency and community communication, such as regular progress reports, security updates, and proactive engagement with the community.
- Market and Community Perception :
- 1)Community Engagement: Assess the project's community activity and user base; an active community often indicates broad support for the project.
- 2)Media and Social Media Sentiment: Analyze the project's reception in media and social media to understand the perspectives of users and industry experts.
- 3)Partnerships and Investors: Review whether the project has support from well-known partners and investors, which can lend credibility to the project, but should not be the sole determinant of its security.
Q2:How should users review audit reports and the open-source status, etc.?
BlockSec Security Team : For audited projects, the project team typically shares audit reports openly via official channels.These audit reports are typically found in the project party's documentation, Github code repositories, and other channels. In addition, it is necessary to verify the authenticity of the audit reports, including checking the digital signature of the audit report and contacting the audit company for secondary confirmation.
So, how should investors read such audit reports once they have them?
Firstly, check if the audit report has been audited by security companies with a high reputation, such as BlockSec, OpenZeppelin, Trail of Bits and other leading audit companies.
Secondly, check whether the issues mentioned in the audit report have been fixed, and if not, assess the project's justifications. Distinguish between valid and invalid vulnerabilities, as audit standards vary by firm. Prioritize valid findings and consider enlisting your own security experts for an independent review.
Thirdly, ensure the audit report's timing aligns with recent project updates. Verify that the audit encompasses all current online code, as projects often audit only portions due to cost constraints. Focus on whether the core protocol code was included in the audit.
Fourthly, ensure the audit report's timing aligns with recent project updates. Verify that the audit encompasses all current online code, as projects often audit only portions due to cost constraints. Focus on whether the core protocol code was included in the audit.
Fifthly, confirm if the project's online code is open-sourced and matches the audit report. Typically, audits are conducted on Github code, not the deployed version. If the deployed code isn't open-sourced or significantly deviates from the audited code, this discrepancy warrants close attention.
In summary, reading audit reports is a highly professional task, and it is recommended to introduce independent third-party security experts to provide consulting opinions during the process.
OKX Web3 Wallet Security Team : Users can access DeFi project's smart contract audit reports and open-source status via official or third-party platforms like OKLink. Common steps to review these include:
Firstly, look for official announcements or websites. Most trustworthy DeFi projects will display their relevant documentation information on their official website. On the project's documentation page, there is usually a page link to the audit report and the contract address deployed by the project party under "Security," "Audit," or "Contract Address." In addition to the project party's official website, they usually display the audit report and deployed contract address information on official social media such as Medium, Twitter, etc.
Secondly, after reading the project party's official website, you can use the OKLink browser to query the contract address information provided by the project party and view the open-source code information of the deployed contract at that address in the "Contract" column.
Thirdly, after obtaining the project party's audit report and open-source code information of the deployed contract, you can start reading the project party's audit report. When reading the audit report, pay attention to the following points :
- 1)Understand the structure of the audit report and have an overall concept of the content of the audit report. The audit report is roughly divided into Introduction, Issues Found, Solutions and Recommendations, and Audit Results.
- 2)When reading the Introduction, we need to pay attention to the scope and objectives of the audit report. The audit report usually marks the Github Commit Id of the audited files, and we need to compare whether the files audited in the audit report are consistent with the open-source code deployed on the chain.
- 3)When reviewing the 'Issues Found,' 'Solutions and Recommendations,' and 'Audit Results,' ensure the project team has addressed vulnerabilities per the recommendations and conducted follow-up audits to confirm all issues are resolved.
- 4)Compare multiple reports. For projects with multiple audits, compare the reports to track the project's security enhancements.
Q3 : What is the importance of hacking history and bug bounty programs in evaluating DeFi project security?
OKX Web3 Wallet Security team : Hacking history and bug bounty program provide certain reference value for the security evaluation of DeFi project, mainly reflected in the following aspects:
Firstly, the history of hacker attacks
- 1)Reveals historical vulnerabilities: The history of attacks can demonstrate the specific security vulnerabilities that the project has had in the past, allowing users to understand what security issues have been exploited and whether these issues have been thoroughly resolved.
- 2)Assesses risk management capabilities: How the project responds to historical security incidents can reflect its ability to manage risks and handle crises. A project that responds positively, fixes vulnerabilities in a timely manner, and compensates affected users is generally considered a more reliable and mature investment choice.
- 3)Project reputation: Frequent security issues may diminish user trust in the project, but if the project can demonstrate the ability to learn from mistakes and strengthen security measures, this can also build its long-term reputation.
Secondly, bug bounty programs
The implementation of bug bounty programs in DeFi and other software projects is an important strategy for improving security and uncovering potential vulnerabilities. These programs bring multiple aspects of reference value to the security assessment of projects :
- 1)Enhances external auditing: Bug bounty programs encourage security researchers worldwide to participate in the security auditing of projects. This "crowdsourcing" approach to security testing can reveal issues that internal audits may overlook, thereby increasing the chances of discovering and resolving potential vulnerabilities.
- 2)Verifies the effectiveness of security measures: Through bug bounty programs, projects can test the effectiveness of their security measures in practice. If a project's bug bounty program has been running for a long time but has few serious vulnerabilities reported, this may be an indicator that the project is relatively mature and secure.
- 3)Continuous security improvement: Bug bounty programs provide a mechanism for continuous improvement. As new technologies and attack methods emerge, bug bounty programs help project teams update and strengthen their security measures in a timely manner to ensure that the project can cope with the latest security challenges.
- 4)Establishes a security culture: Whether a project has a bug bounty program and the seriousness and activity level of that program can reflect the project team's attitude towards security. An active bug bounty program shows the project's commitment to establishing a solid security culture.
- 5)Enhances community and investor confidence: The presence and effectiveness of a bug bounty program can prove to the community and potential investors the project's emphasis on security. This can not only enhance user trust but may also attract more investment, as investors tend to choose projects that demonstrate a high sense of security responsibility.