On March 13, 2023, Euler Finance's lending pool suffered a flash loan attack, resulting in losses of approximately $200 million. After investigation, we found that the root cause is due to the lack of liquidity check in the function donateToReserves(). As a blockchain security company, we closely monitor such exploits that can have far-reaching implications in the DeFi space.
| Date | Attack type | Chain | Lost | Recovered |
|---|---|---|---|---|
| 20230313 | Business Logic Flaw | ETH | ~ $200 M | Yes |
1/ @eulerfinance is attacked. The root cause is due to the lack of liquidity check in the function donateToReserves()https://t.co/stWtPWK900
— BlockSec (@BlockSecTeam) March 13, 2023
See the detailed attack steps below. https://t.co/bm10OJHiXu pic.twitter.com/TDbYuzVWHe
Introduction
Euler Finance is a decentralized finance (DeFi) protocol built on the Ethereum blockchain. It allows users to lend and borrow a variety of crypto assets, and it has its native token called EUL, which is an ERC-20 token.
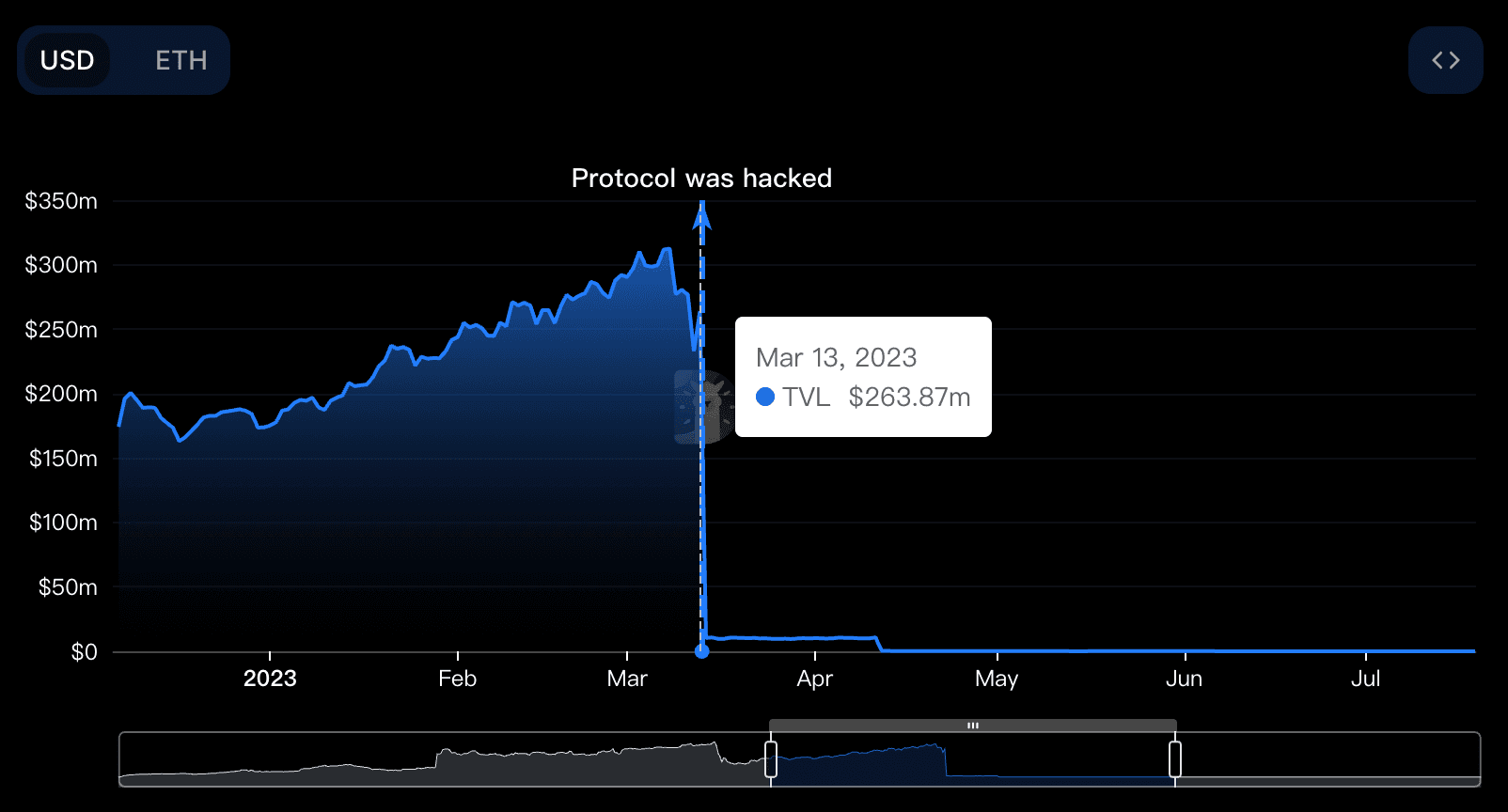
Before this attack occurred, Euler Finance was ranked in the top 30 on DefiLlama, making it one of the leading stablecoin protocols. However, after the attack, its TVL plummeted from $264 million to $10 million, experiencing a 96% decline.
Key Concepts
Euler Finance's self-borrow and soft liquidation mechanisms are two key concepts that help us better understand the cause of this attack. Self-borrowing allows users to mint more assets and increase debt by directly using newly minted EToken as collateral, effectively leveraging themselves. On the other hand, the soft liquidation mechanism enables liquidators to flexibly help the liquidated party repay their debt, rather than being restricted to a fixed coefficient for liquidation. These two concepts play a significant role in Euler Finance's operation and unfortunately provided the attacker with exploitable vulnerabilities.
Attack Analysis
The attacker's strategy can be broken down into the following key steps:
- Attacker flashloaned 30M DAI in AAVE
- The attacker deposited 20M DAI into Euler Finance and got back 20M eDAI in return
- Since Euler Finance provides the capability of leverage borrow, the attacker can mint 195M eDAI and 200M dDAI
- Continued above. 10M debt is repaid so that the attacker can mint more eDAI. Now the attacker holds 215M eDAI and 190M dDAI
- Step 2 is repeated. Now the attacker holds 410M eDAI and 390M dDAI
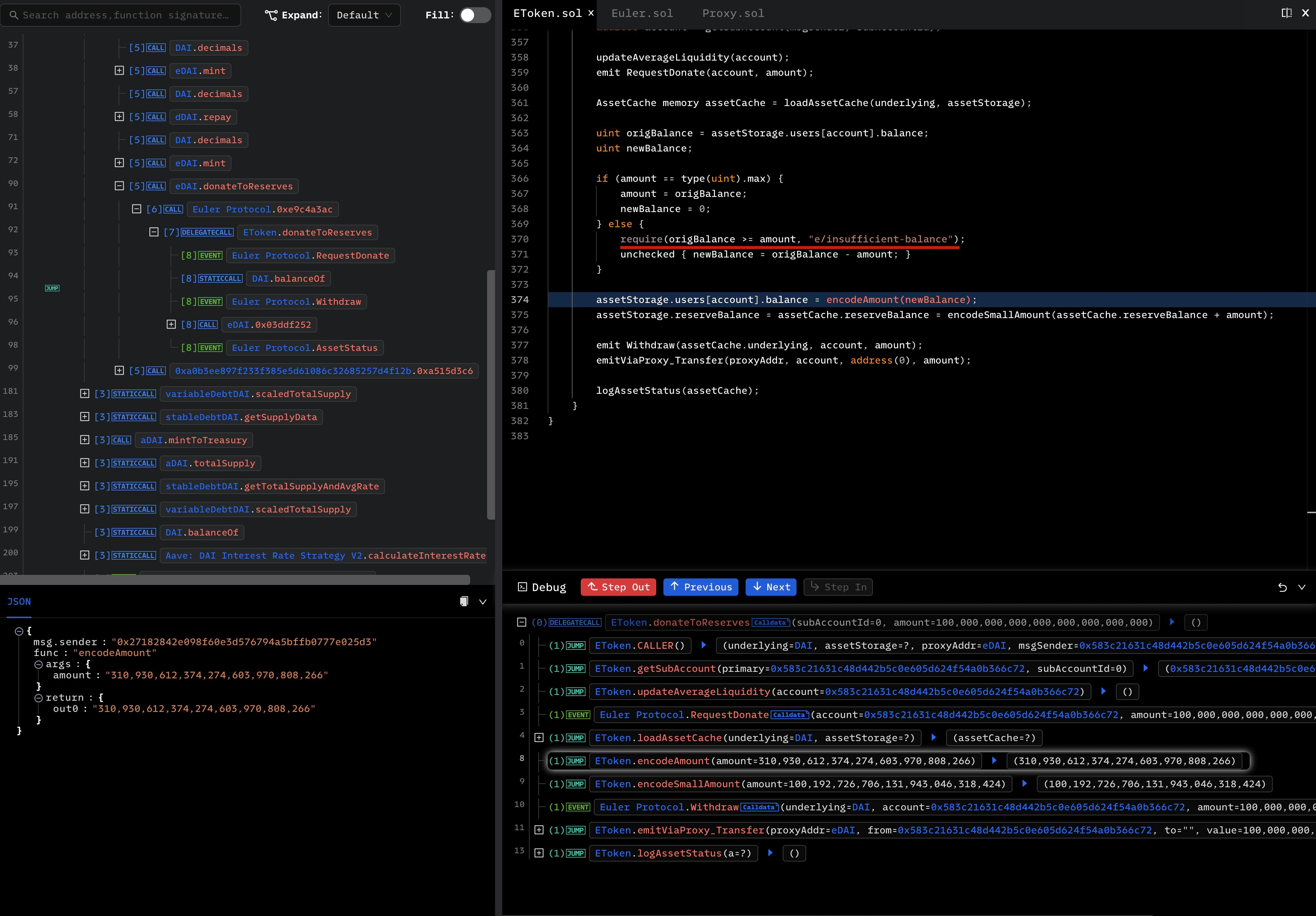
- Attacker invoked the function
donateToReserve()to donate 100M eDAI
However, during this process, the health factor of the attacker is not checked. In this case, the position can now be liquidated, which leaves the chance to gain profit.
- Attacker liquidated himself and got out 38M eDAI
- Flashloan is repaid.
Summary
The fundamental reason for this attack is the lack of liquidity checks in the donateToReserves function of Etoken, combined with a liquidation mechanism that dynamically updates discounts. These factors created an arbitrage opportunity, allowing the attacker to exploit a significant amount of crypto without the need for collateral or debt repayment.
Follow-up Steps
Remarkably, the stolen funds, amounting to approximately $135 million, primarily consisting of staked Ether (stETH) tokens, Bitcoin, and stablecoins DAI and USDC, were fully recovered. What makes this incident even more intriguing is the identity of the attacker — a 19-year-old Argentine genius named Federico Jaime. This young genius stole nearly $200 million worth of crypto in just 18 minutes through a few lines of code. However, out of moral considerations, he revoked the transaction and returned everything he had stolen just three weeks later.[1]
As a company dedicated to maintaining blockchain security, we have also been closely monitoring the progress of this attack. (Our official Twitter account has been continuously reporting on this incident, and interested readers can follow our account @BlockSecTeam@MetaSleuth to track the movement of these funds together.) On March 18th, the attackers returned 3000 Ether. One week later, the exploiter of the Euler vulnerability returned 51000 Ether to Euler Finance. They also returned the remaining funds in the following days. Incredibly, new fraud schemes emerged during the refund process. Scammers took advantage of this incident to set up the phishing website eulerrefunds.cxx and conducted phishing attacks, with some users already falling for it.
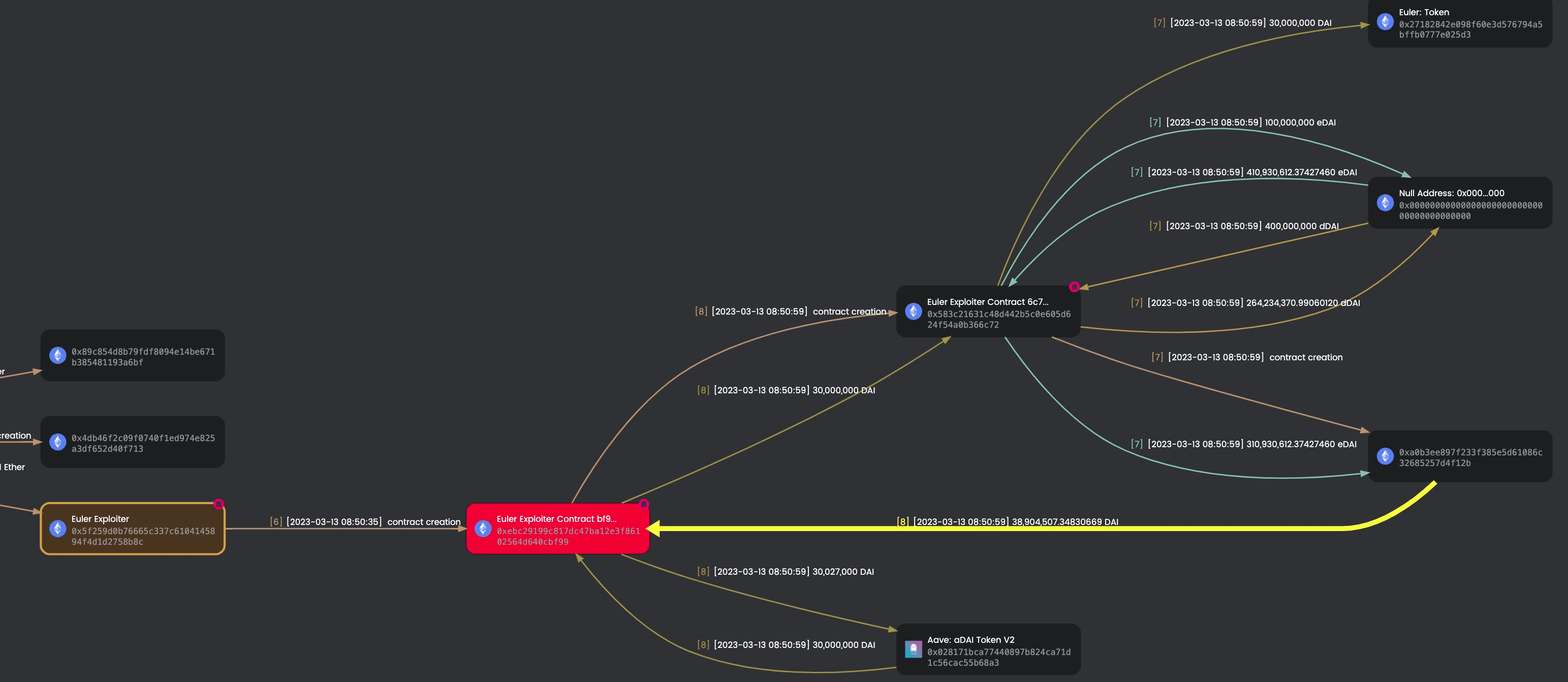
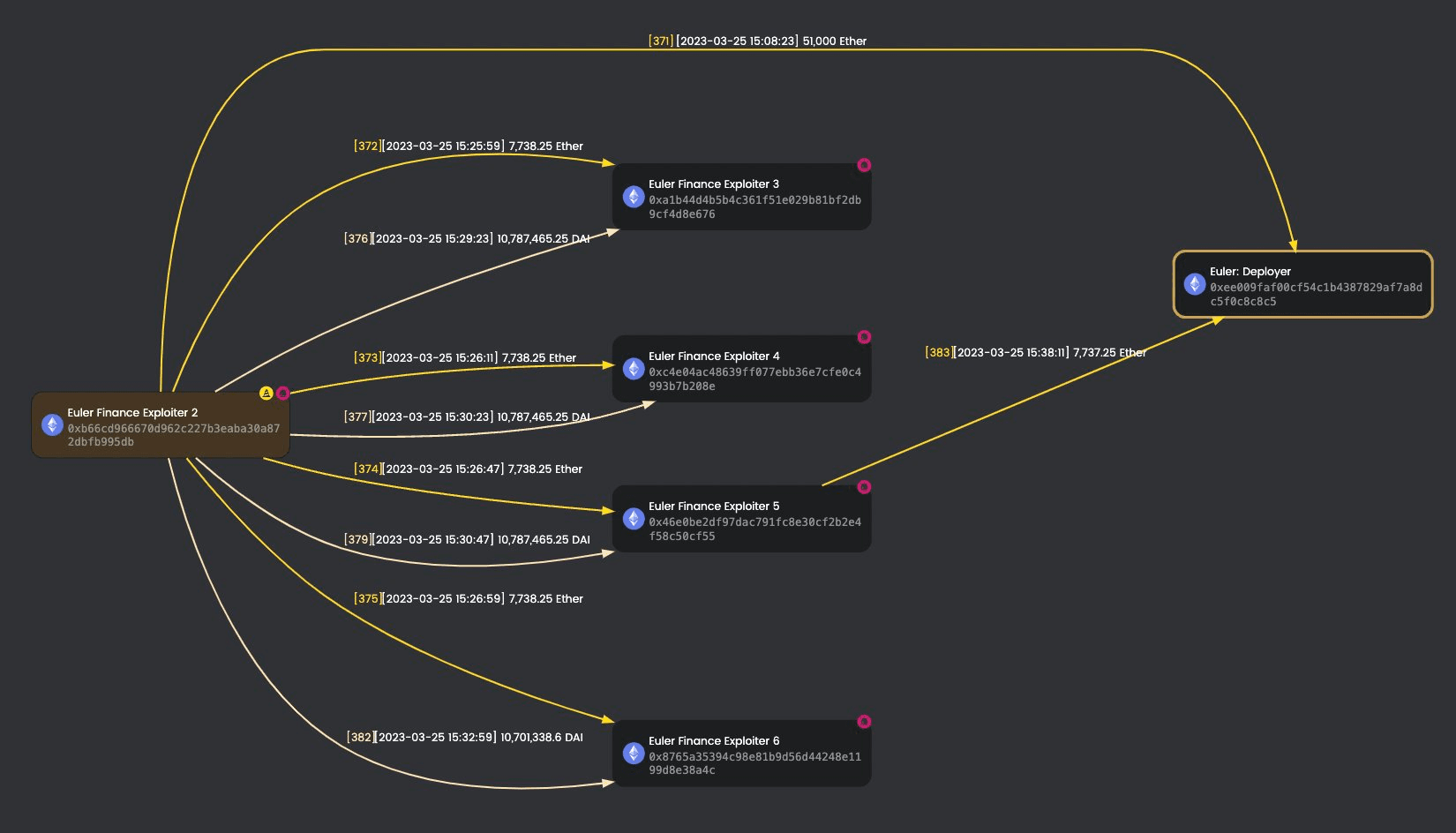
MetaSleuth is a high-performance cross-chain fund flow analytics tool that enhances the transparency of blockchain transaction activity. It allows users to nearly real-time track the trail of affected digital assets. By leveraging MetaSleuth, we were able to clearly see the fund flow tracing information related to both when this attack incident occurred and during the refund process.
More
The above are just representative cases. In fact, we have more cases focusing on blockchain security analysis.
BlockSec offers a full-stack security service for blockchain projects, assisting pre-launch to post-launch and incident response. During the development and testing stages, Expert Code Auditing Services and the Phalcon fork testing platform are employed to help identify potential security issues. Ensure robust post-launch security for your blockchain project with BlockSec Phalcon. This streamlined SaaS platform offers incident alerts and automatic blocking to prevent crypto hacks. It employs precise attack detection, scanning both pending and on-chain transactions, allowing you to swiftly intercept hackers. Additionally, MetaSleuth is an intuitive crypto tracking and investigation platform that helps enhance the traceability and transparency of assets.
Reference
[1]HE STOLE $200 MILLION. HE GAVE IT BACK. NOW, HE’S READY TO EXPLAIN WHY




