Introduction:
In the rapidly evolving landscape of blockchain technology, security remains a paramount concern. As the adoption of Web 3.0 continues to grow, the need for robust security measures becomes more pressing. To address this, BlockSec who conduct cutting-edge research, provide reliable security services and build insightful tools, has formally agreed to partner with Intelligence On Chain's (IOC) brand new suite of services called 'AЯMRD.'

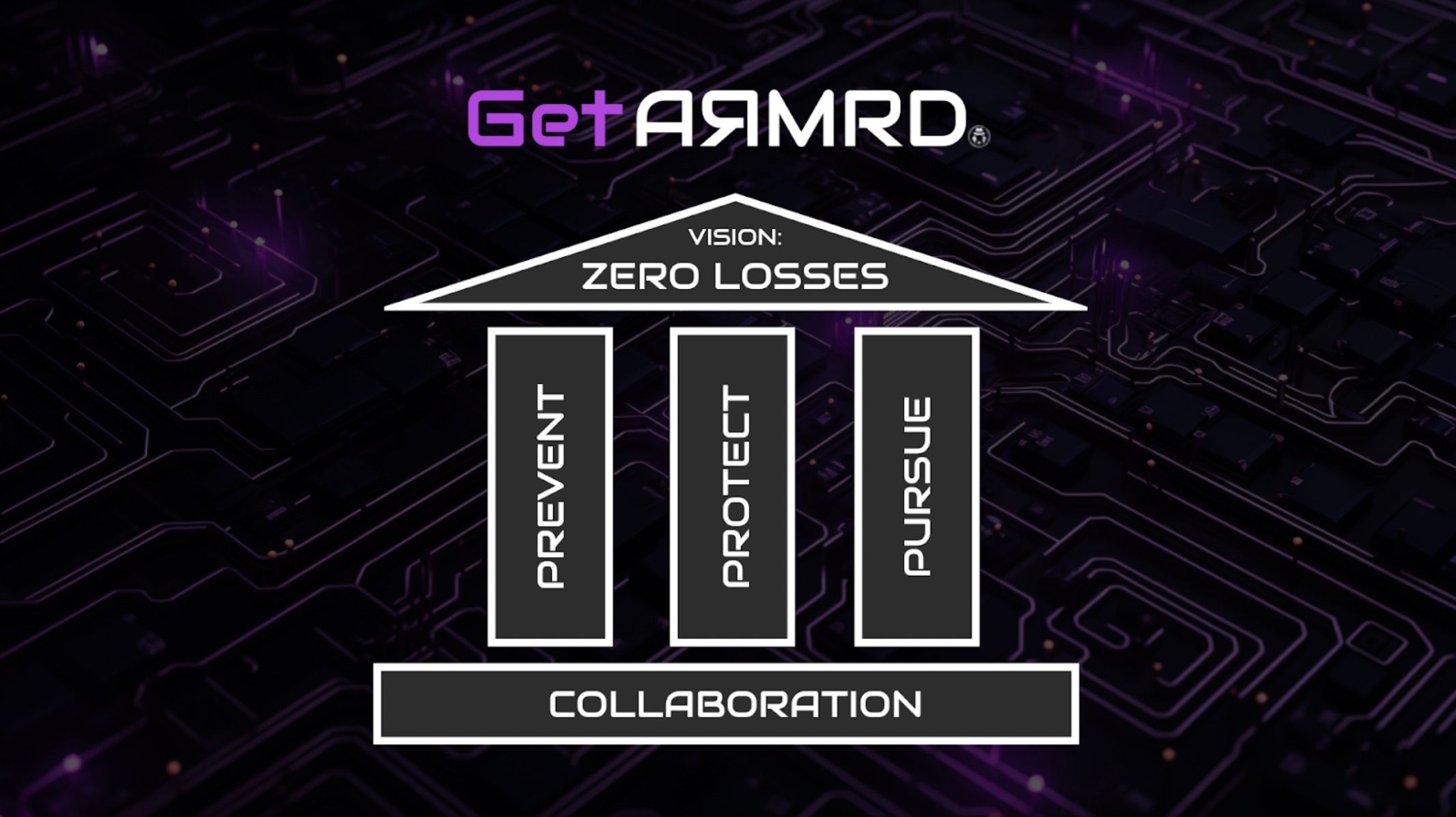
IOC have positioned AЯMRD to become the Ultimate Web 3.0 Help desk, by offering a whole suite of services to new and existing crypto projects, that provide end to end security.
The collaboration between BlockSec, IOC, and AЯMRD marks a significant stride towards fortifying the foundations of decentralised applications. By leveraging cutting-edge tools and high-quality auditing services, the partnership is poised to set new standards for security in the blockchain space, ensuring a safer and more secure future for Web 3.0.
The Partnership:
BlockSec, has entered into a strategic partnership with IOC and AЯMRD to provide advanced auditing services and leverage their innovative tools for enhanced security, within the AЯMRD ecosystem. This collaboration aims to make the Web 3.0 space safer by proactively preventing attacks during both the design and live phases of smart contracts.
Utilising BlockSec's Smart Contract Auditing Services:
BlockSec's smart contract auditing services play a pivotal role in securing smart contracts. By thoroughly reviewing the codebase and identifying vulnerabilities, BlockSec ensures that smart contracts are resistant to potential exploits. This proactive approach is essential in preventing security breaches that could compromise the integrity of decentralised applications (DApps).
Phalcon: A Cutting-Edge Security Solution:
As part of this collaboration, BlockSec will deploy BlockSec Phalcon as a part of AЯMRD, the Web 3.0 Helpdesk allowing IOC to offer attack detecting and automated defense for protocols as a part of its package. Phalcon employs state-of-the-art techniques to identify and mitigate potential threats as they occur and prior to the attacked being confirmed on the blockchain, significantly reducing the impact of vulnerabilities in their smart contracts. Phalcon will be combined with many more offerings (within AЯMRD) and available through a subscription model.

IOC commits to using MetaSleuth exclusively:
In an effort to provide all-round comprehensive security package, IOC has agreed to exclusively utilise MetaSleuth as its Ethereum Virtual Machine (EVM) visualisation tool, which has unique advantages in cross-chain analysis, intelligently displaying key pathways, and matching flashswap transactions. In the event that a client is exposed to a hack or exploit, IOC will pursue the attackers using MetaSleuth, a long time preferred tool.

Making Web 3.0 Safer:
The combined efforts of BlockSec, IOC, and AЯMRD represent a significant step forward in making Web 3.0 safer for users and developers alike. By incorporating smart contract auditing services, advanced security tools like Phalcon, and real-time visualisation with MetaSleuth, the partnership aims to create a resilient blockchain ecosystem that withstands potential attacks.