In this tutorial, we will guide you through the basic functionalities of MetaSleuth by tracing the stolen funds in a phishing transaction. Together, we will explore how to use MetaSleuth to analyze transactions, track specific funds, and monitor untransferred funds.
MetaSleuth Tutorial - Use MetaSleuth to track the stolen funds in a phishing transaction
We have identified a phishing transaction on the Ethereum network with the hash 0x2893fcabb8ed99e9c27a0a442783cf943318b1f6268f9a54a557e8d00ec11f69. Now, let's delve into our analysis.
Getting Started
Begin by visiting the MetaSleuth platform at https://metasleuth.io/. Choose Ethereum as the network and input the transaction you're interested in. For our case, we'll use the following transaction hash: 0x2893fcabb8ed99e9c27a0a442783cf943318b1f6268f9a54a557e8d00ec11f69.

Main functional components
Once the transaction analysis is complete, you will be directed to the MetaSleuth analysis page, where you can see all the asset transfers that took place in the transaction. If the analysis target is an address, the displayed information will be more complex. We will cover address analysis in a separate tutorial.
In addition to the central asset transfer graph, the page includes various other functional components. Here is a simplified diagram, and you are encouraged to explore their specific usage during the analysis process.

Track the funds
The transaction we are focusing on involves only one asset transfer: Address 0xbcd131, which is the victim, transferred 2586 MATIC to Fake_Phishing180627.
To continue tracking the destination of the stolen MATIC tokens, it's straightforward. Simply select the Fake_Phishing180627 address node and click on the "+" button on the right side of the node.
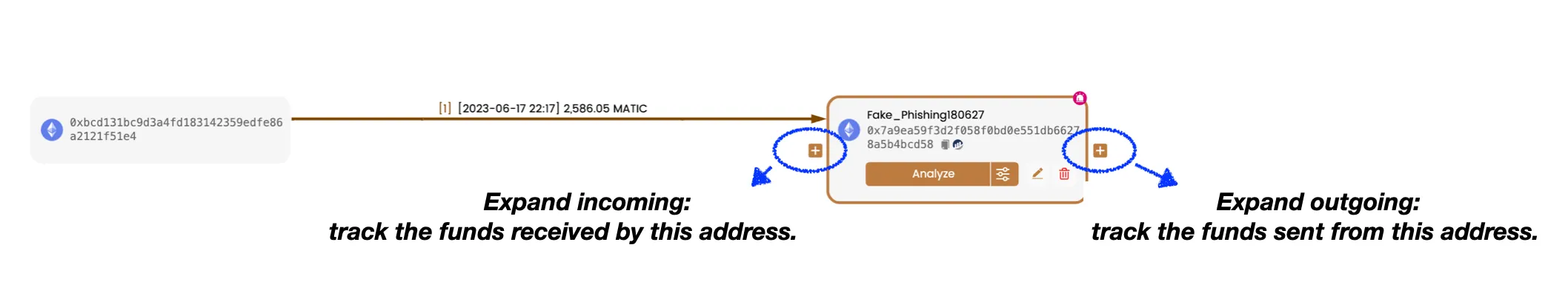
This feature is called Expand outgoing and allows you to trace the assets sent from this address. In most cases, this feature provides the desired data. However, for addresses with a high transaction volume, you may need to utilize advanced features such as Advanced Analyze and Load More to obtain the required data.
After clicking the "+" button, we can see numerous outgoing Ether transfers from Fake_Phishing180627. But what about the MATIC we want to track?

Filter the canvas
MetaSleuth does not display all the data it retrieves on the canvas to ensure a clean and readable representation of the overall fund flow. However, MetaSleuth provides various tools to help users locate the desired data and add it to the canvas. In this case, we can utilize the Token Filter to add all the MATIC asset transfers obtained by MetaSleuth to the canvas.

After confirming, we can see an additional MATIC transfer on the canvas, originating from Fake_Phishing180627 and going to Uniswap V3: MATIC. This is exactly the stolen funds we are tracking.
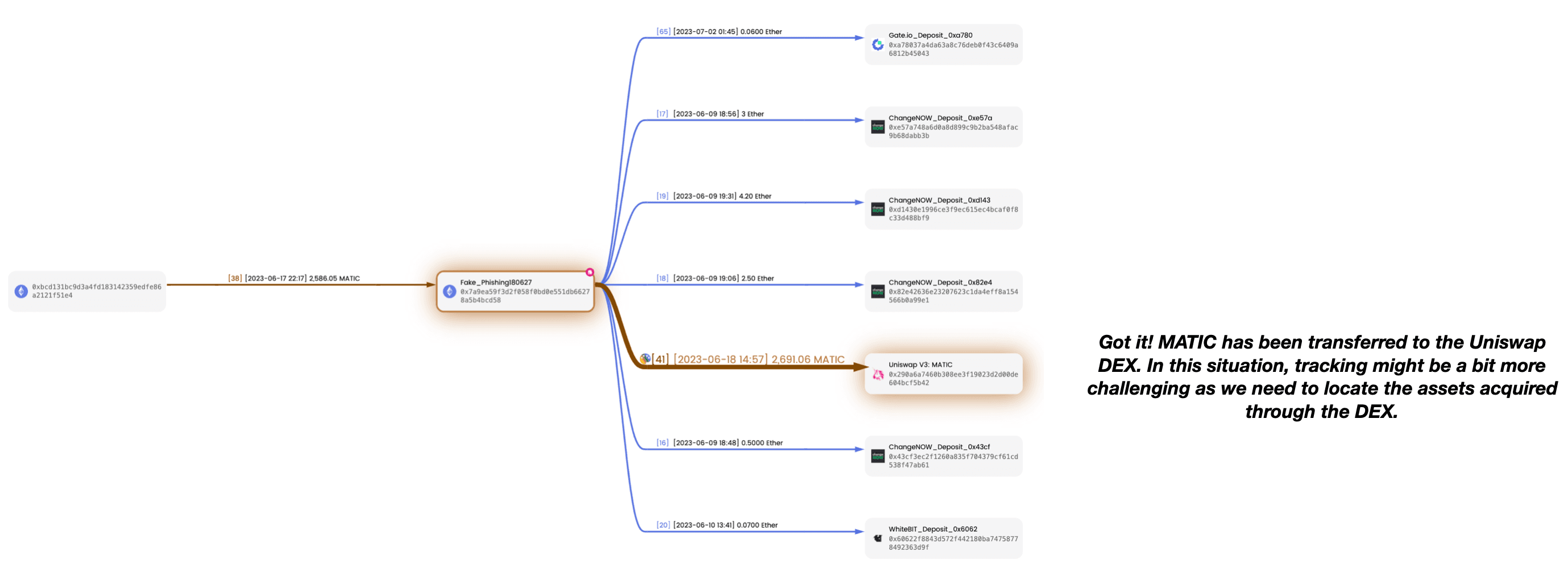
When it comes to assets sent to decentralized exchanges (DEX) like Uniswap, our focus is not on the MATIC tokens transferred out from the address Uniswap V3: MATIC, but rather on the assets obtained by Fake_Phishing180627 through the swap action on Uniswap.
So, what assets did Fake_Phishing180627 receive through this swap? Let's investigate this swap transaction to find out.
Add specific data
First, we need to determine the transaction to which the MATIC transfer from Fake_Phishing180627 to Uniswap V3: MATIC belongs. Click on the asset transfer edge on the canvas, and in the Edge List that appears below, click on Details to access the Transaction List. Find the transaction hash for this transfer and copy it.
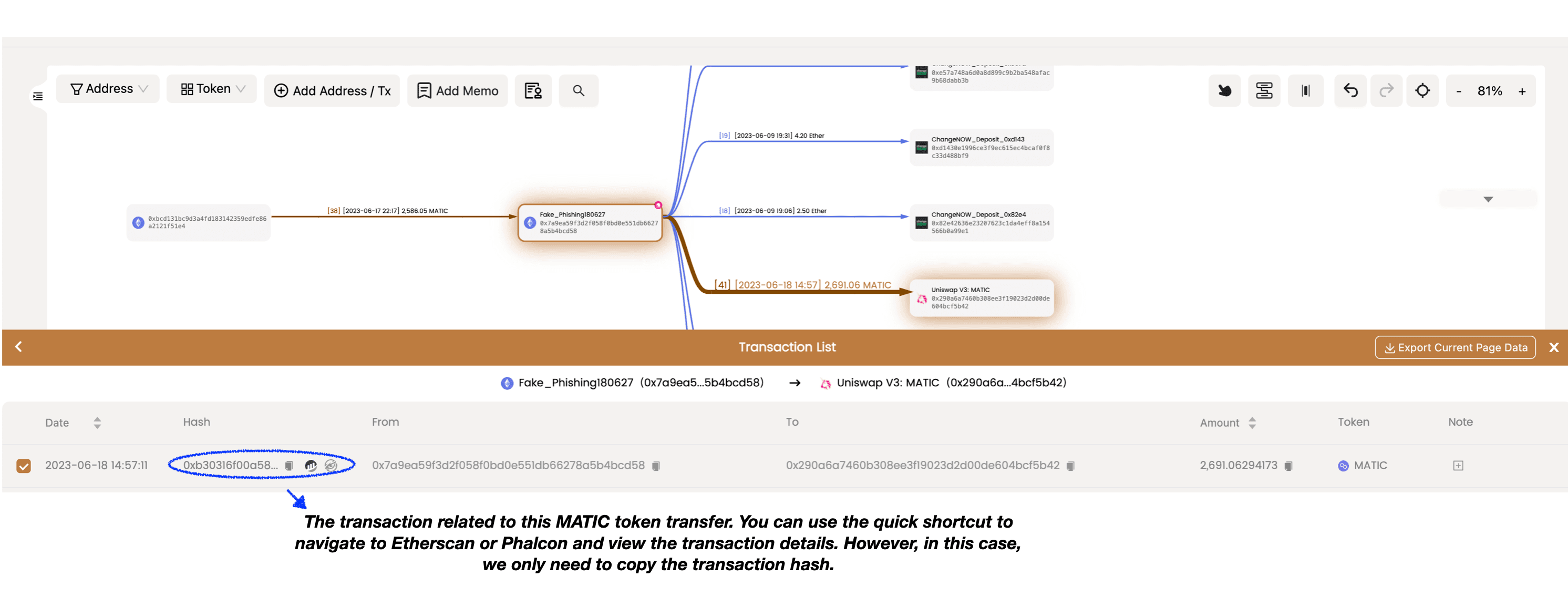
Then, we can add this transaction to the canvas using the Add Address / Tx functionality located in the top left corner of the canvas. This will allow us to explore the asset transfers that took place within this transaction and gain a clearer understanding of its contents.

After adding it, all the asset transfers within this transaction will be visible on the canvas. It becomes clear that Fake_Phishing180627 swapped MATIC for 0.944 Ether through Uniswap. This 0.944 Ether is the asset we need to track further.

Track specific funds
Among the various Ether transfers originating from Fake_Phishing180627, which ones should we track?
By clicking on Fake_Phishing180627, you can observe the asset transfers associated with this address in the left-hand address panel. You might have noticed that there is more data available here compared to what is displayed on the canvas (as mentioned earlier, MetaSleuth emphasizes simplicity and readability in the fund flow diagram and does not show all data by default).
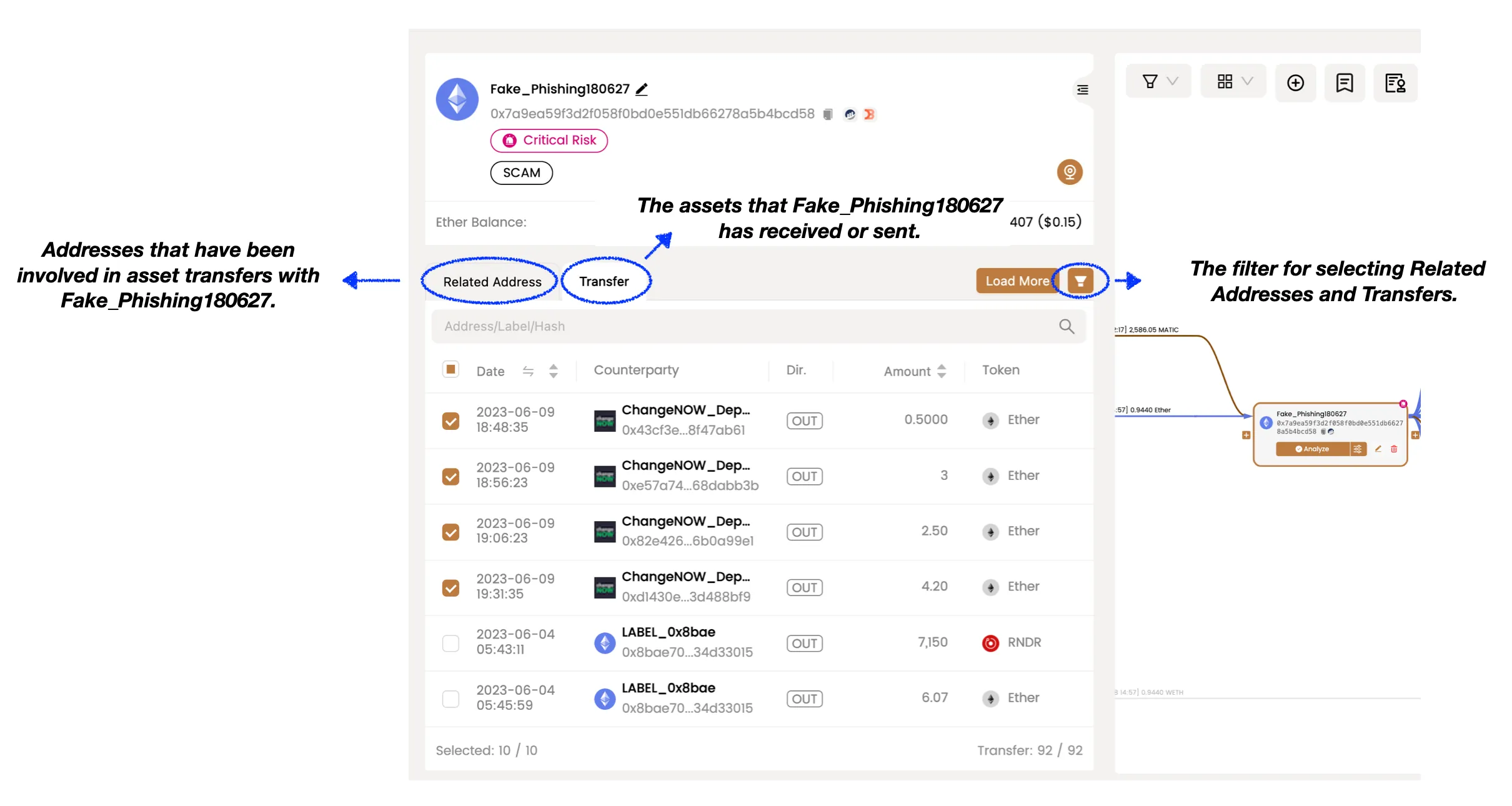
The transaction where Fake_Phishing180627 swapped MATIC for Ether occurred on 2023-06-18 at 14:57:11. Therefore, our primary focus should be on Ether token transfers that occurred after this specific time. To filter the data, we can utilize the filter function.
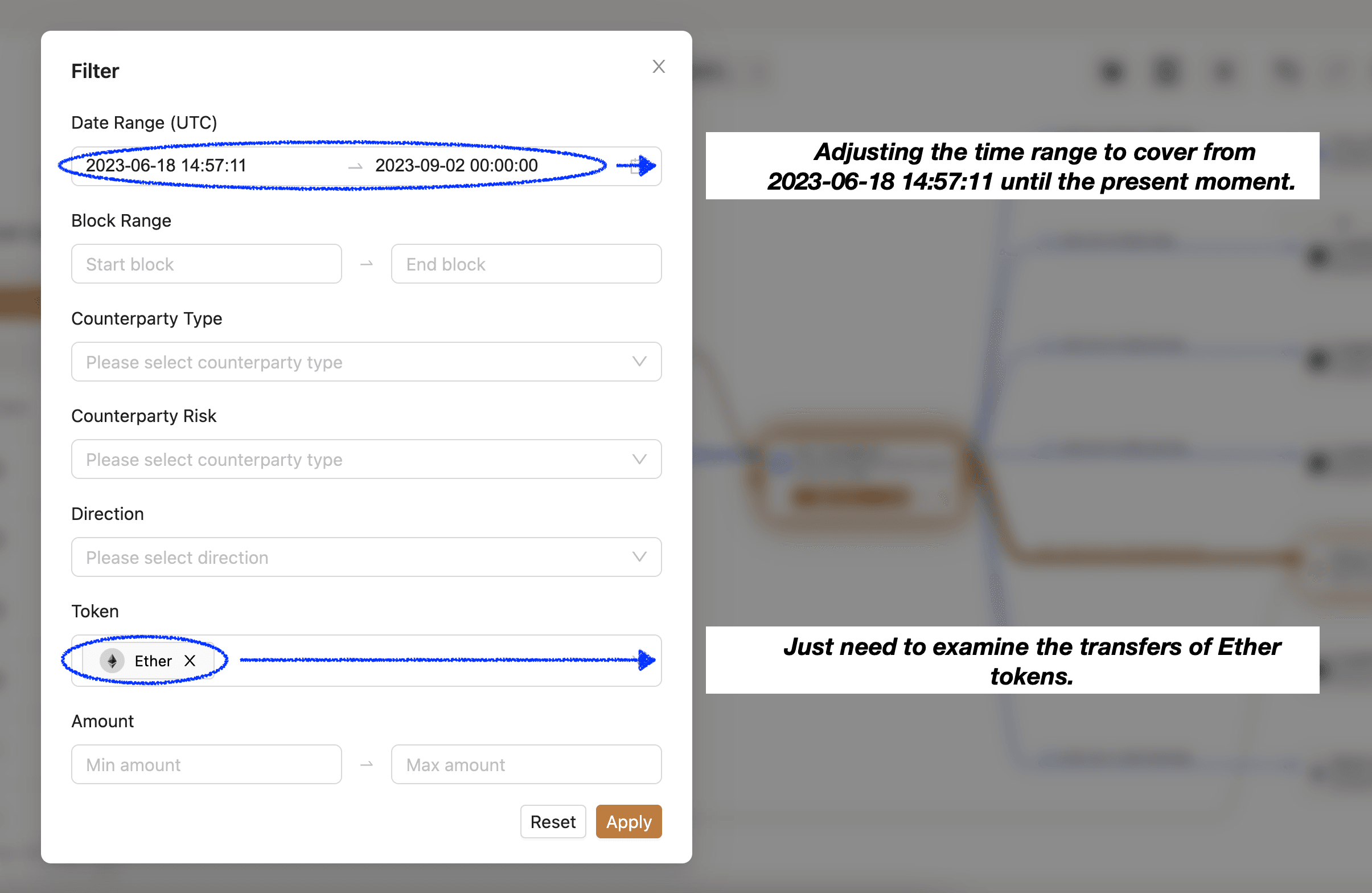
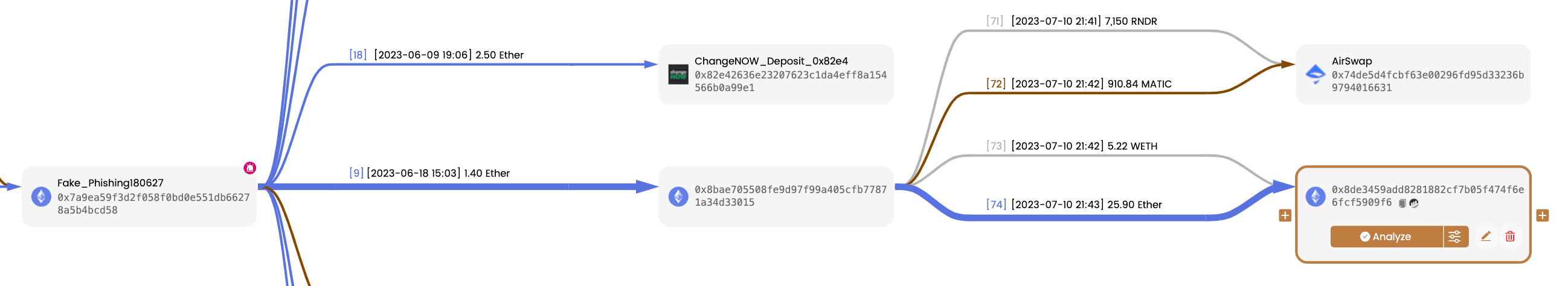
Within the filtered results, it is evident that approximately 6 minutes after the swap action, 1.4 Ether was transferred from the address Fake_Phishing180627 to the address 0x8bae70. This transfer likely contains the funds we are seeking to trace.

We can mark and display them on the canvas, continuing to track the assets of 0x8bae70. By doing so, we can observe that the funds eventually settle in the address 0x8de345
Monitor untransferred funds
To stay informed about the funds that have not been transferred yet, we can actively monitor them. By enabling monitoring, you will receive email notifications whenever relevant asset transfers occur. To explore additional monitoring features, please visit the MetaSleuth Monitor Dashboard at https://metasleuth.io/monitor.

Summary
Although this was a brief exploration, we hope that MetaSleuth has provided you with a convenient and smooth tracking and investigation experience. We will release more instructional material in the future and welcome your suggestions. Join our Telegram group at https://t.me/MetaSleuthTeam.
About MetaSleuth
MetaSleuth is a comprehensive platform developed by BlockSec to assist users in effectively tracking and investigating all crypto activities. With MetaSleuth, users can easily track funds, visualize fund flows, monitor real-time fund movements, save important information, and collaborate by sharing their findings with others. Currently, we support 13 different blockchains, including Bitcoin (BTC), Ethereum (ETH), Tron (TRX), Polygon (MATIC), and more.
Website: https://metasleuth.io/
Twitter: @MetaSleuth
Telegram: https://t.me/MetaSleuthTeam




