CVE-2021-39137 is a vulnerability which has been reported and fixed a few days ago. However, not all Ethereum nodes have applied the patch. We observe this vulnerability has been exploited by a malicious transaction.
Attack Transaction
https://tx.blocksecteam.com/tx/0x1cb6fb36633d270edefc04d048145b4298e67b8aa82a9e5ec4aa1435dd770ce4
This transaction has a STATICCALL with the address 0x4. This is a pre-compiled smart contract dataCopy. The argument is as follows.
inOffset = 0, inSize = 32, retOffset = 7 and retSize = 32.
The 0x4 smart contract
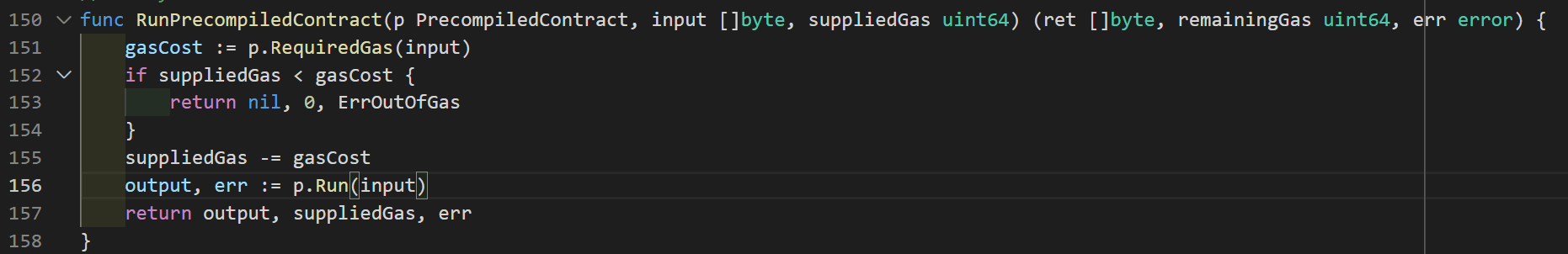
Figure 1
Since the target of the STATICCALL is the 0x4 pre-compiled contract, it will execute the RunPrecompiledContract function in Figure 1.
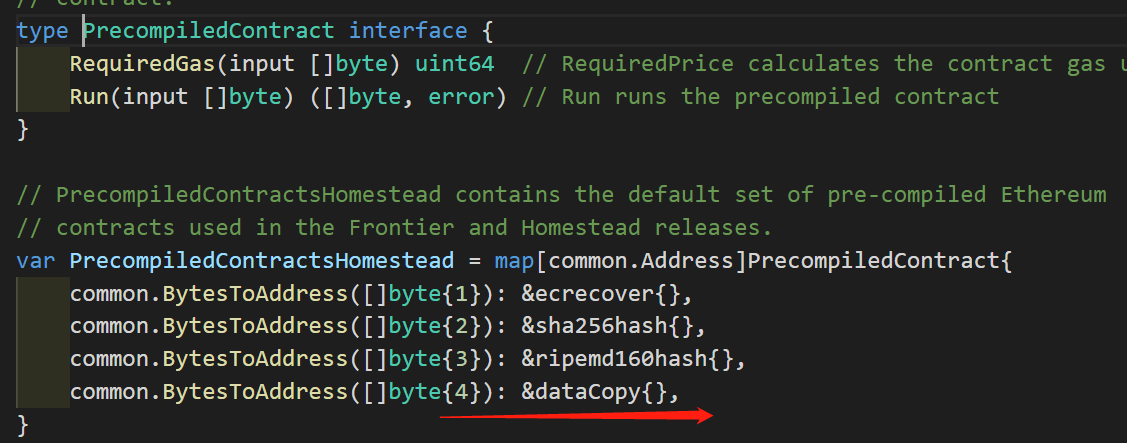
Figure 2

Figure 3
According to Figure 2/3, the 0x4 smart contract is simply returning the reference of the in pointer.
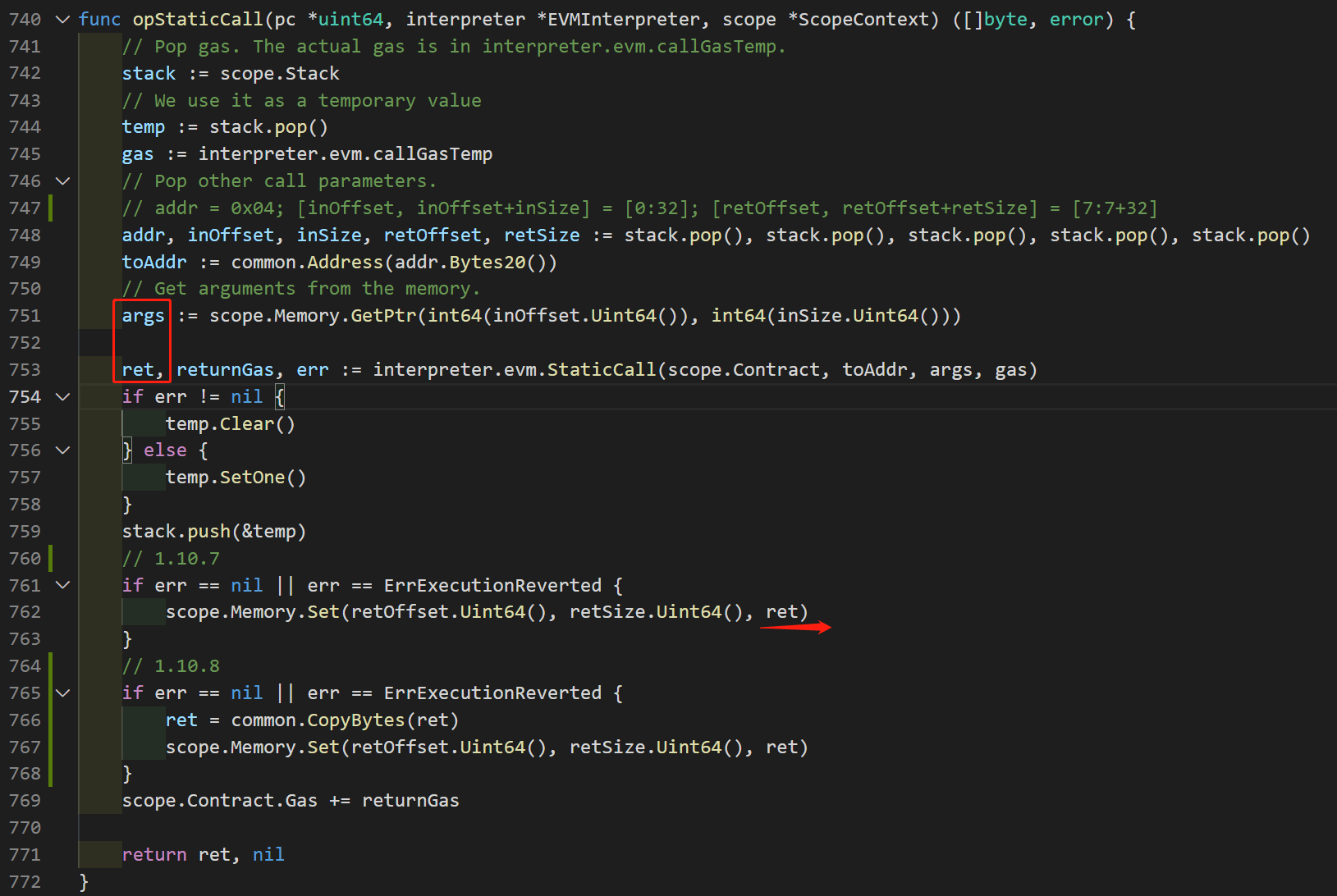 Figure 4
Figure 4
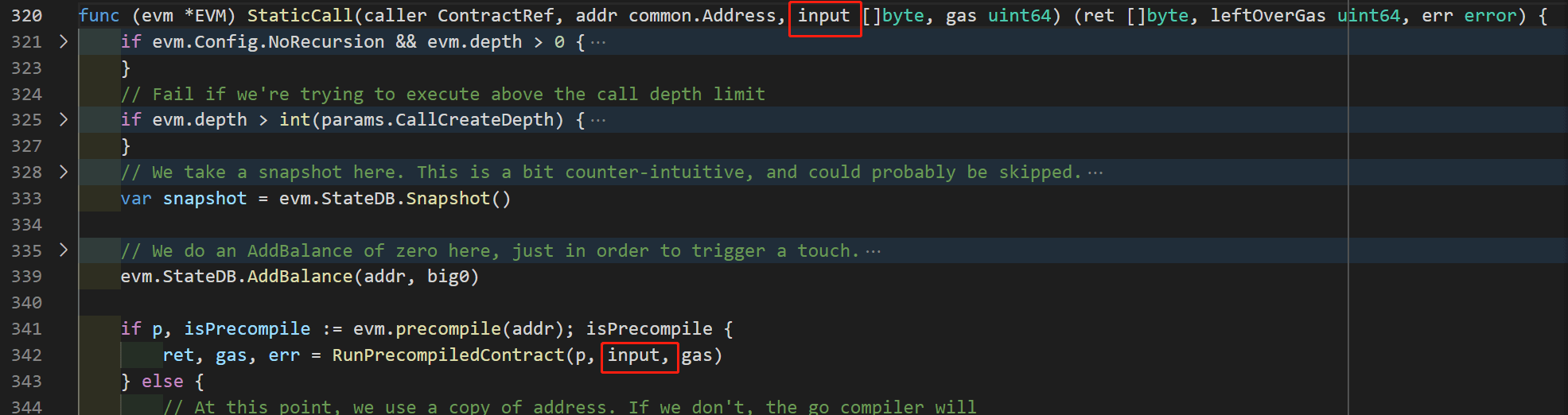
Figure 5
Figure 4 is the code for the opcode STATICCALL. In line 751, args points to [inOffset ~ inOffset + inSize ] of the EVM memory, which is Mem[0:32].
According to Figure 5 and the analysis of the code logic of 0x04 (Figure 2/3), the return value (ret) is a reference to the same memory as args. That is to say, it also points to Mem[0:32].
Vulnerability
In the vulnerable code (version 1.10.7), line 762 copies the content of ret to Mem[retOffset : retOffset + retOffset], i.e., copy Mem[0:32] to Mem [7:7+32]. This operation accidentally changes the content of ret. This means the return value of the 0x4 pre-compiled contract has been modified.
In the fixed version (1.10.8), it makes a copy of ret (line 766). This can fix the vulnerability since the copy in line 767 cannot modify the content of ret.
The CVE-2021–39137 vulnerability was exploited by a malicious transaction due to nodes not updating their patches in time. This flaw involved a defect in the Ethereum Virtual Machine's memory operations but has been fixed in version 1.10.8. To ensure system security, it is recommended that all Ethereum nodes update to the latest version immediately.
Credits
The attack is analyzed by Siwei Wu, Yufeng Hu, Lei Wu, Yajin Zhou@BlockSec




