Web3 moves fast, and sometimes uncomfortably fast.
DeFi stacks itself like composable LEGO bricks. Layer 2 solutions push the limits of throughput. Meme coins experiment with live economic incentives. RWAs steadily migrate on-chain. The technical frontier shifts almost every day.
Yet one thing has never changed and it is security.
In this decentralized wilderness, a single overflow, a subtle logic misalignment, or even a neglected configuration parameter can vaporize hundreds of millions of dollars. Security is no longer a backend KPI. It is the lifeline of any Web3 project, the foundation of user trust, and the dividing line between short-lived hype and long-term industry leadership.
BlockSec is a global leader in blockchain security, shaped not only by frontier research but by battle-tested experience. Across dozens of live incidents, we have blocked more than 20 critical attacks and prevented over $20M in losses. These are not theoretical claims but are verifiable outcomes.
This field experience defines our philosophy: in Web3, 99% secure is still zero.
Our audits therefore go far beyond “finding superficial bugs.” We combine academic-grade analysis with attacker-level reasoning to build defense-in-depth, covering everything from foundational assumptions to high-level business logic.
Smart Contract Audits: A Deep Dive from Code to Logic, with Coverage for Zero-Day Threats
1. Why “Rubber-Stamp” Code Scanning Fails in Web3
Many teams still treat security as a checkbox: run an automated scanner once, declare the system “audited,” and move on. History shows the opposite. A large number of projects are audited but still got hacked. The issue is not whether an audit happened, but how it was done.
Traditional audits focus on syntax-level correctness, e.g, passing the language-level check. Web3 audits do not.
In Web3, the smart contract is the financial system. Assets are controlled directly by code. An attacker can follow every syntax rule and still drain the treasury entirely “within the rules” of the protocol.
Common patterns include, but are not limited to:
-
Flash-loan-driven price manipulation
-
Cross-protocol attacks that stitch together vault and fund flows
-
Improper privilege controls that can be combined and escalated
-
Abuse of liquidations, incentives, or bonding curves
-
Governance takeovers via proxy mechanisms
These are not “missing checks” or “uninitialized variables.” They are economic and logical exploits executed inside the rule set.
Automated scanners cannot reliably model how prices interact with assets, how multi-contract state changes within a single transaction, how edge-case execution order affects outcomes, or how an economic model can be manipulated. They are structurally blind to these systemic risks.
The problem is not how much effort you devote but what methodology you adopt. Logic flaws and deep architectural weaknesses live at a level traditional tools were never capable to locate.
BlockSec’s audit philosophy is therefore simple: think like an attacker, validate like a scientist. We don’t just ask whether the code is syntactically correct. We ask whether it is logically robust, economically sane, and resilient under worst-case, adversarial conditions.
2. BlockSec Smart Contract Audits: Beyond Code with Business Logic and Economic Model Review
At BlockSec, a smart contract audit is not just a static code review. It is a deep examination of business logic, cross-protocol interactions, state-machine behavior, and economic incentives.
Many incidents happen not because the code fails to implement the developer’s intent, but because that intent is fragile when exposed to an adversarial environment.
We focus on several key dimensions:
-
DeFi composability risk
-
Relying on a single oracle source, making prices vulnerable to flash-loan manipulation
-
Using AMM state as the basis for liquidation or minting, which can be manipulated
-
Flawed LP token accounting that lets users redeem more than their fair share
-
Depending on external protocol state (Aave, Uniswap, Curve, etc.), which can shift within the same transaction
-
Yield strategies that amplify losses under extreme conditions
-
-
Tokenomics fragility: Economic models may look elegant on paper while hiding dangerous incentive structures:
-
Inflation or minting models that fall into reflexive death spirals under stress
-
Reward formulas without caps, which invite infinite farming via scripts
-
Staking schemes that can be abused through looping and repeated claiming
-
Vesting logic with boundary conditions that allow users to bypass lockups
-
-
State-machine boundary bugs: Many protocols are state machines at their core. Attacks often happen at the boundaries:
-
Initialization gaps during the first interaction, when state is not fully set
-
Time-window transitions that allow checks to be bypassed
-
Constraints that only apply on some paths, letting attackers trigger critical logic via alternative routes
-
Reentrancy that is “allowed” but, under certain state combinations, breaks the expected execution order
-
-
Mathematical weaknesses in complex derivatives: In derivatives protocols, seemingly minor design choices can create extreme risks:
-
Pricing curves that develop singularities under stress
-
Mismatched ordering between settlement and liquidation
-
Margin algorithms that amplify edge-case values
-
Poorly chosen risk parameters that enable cheap, high-leverage exposure
-
BlockSec audits these logic- and economics-level risks from first principles. We analyze business models, incentive structures, state machines, and permission design to ensure that protocols remain stable under adversarial trading and sophisticated exploitation strategies.
3. Dynamic Threat Intelligence and Zero-day Coverage
Attack techniques in Web3 evolve every day. To stay ahead, a security team needs long-term, real-world on-chain experience instead of just tools.
One of BlockSec’s core advantages is the large-scale threat intelligence we have built through Phalcon Security, our real-time on-chain monitoring and incident-response system.
3.1 Detecting Zero-Day Attacks Early: From “Seeing Attacks” to “Anticipating Attacks”
Phalcon Security monitors on-chain behavior in real time. In many cases, it flags abnormal transaction patterns before the community even realizes an attack is underway. Key capabilities include:
-
Real-time identification of unknown attack patterns (zero-day exploit detection).
-
Behavior-based monitoring rather than signature matching (is harder for attackers to evade).
-
Early warnings at the very start of an attack chain (long before losses materialize).
-
Intercepting critical transactions within an exploit chain (when possible)
This is a capability that traditional “audit-only” firms generally lack, as they do not maintain continuous on-chain security sensing.
We’ve published a blog series on Phalcon's Hack Blocking Saga.
3.2 Rapid Analysis of Complex Exploits: From Incident Alerts to Deep Exploit Analysis
Once an attack is detected, BlockSec’s research team can rapidly:
-
Reconstruct the full attack path
-
Identify the core exploit primitive
-
Analyze state transitions (state-machine diffs)
-
Trace asset flows through chains and protocols
-
Build cross-contract call graphs for complex, multi-contract exploits
We have been one of the first teams in the world to publish detailed technical analyses of many high-profile incidents. Our audits combine speed and depth. This insight comes from real attack experience. It offers a clear view of the attacker’s perspective, which few firms can match. We created Phalcon Explorer, a security analysis tool. Many researchers and incident responders use it to investigate exploits. It helps them trace fund flows and replay transaction execution across many chains.
There are several articles covering our security incident analysis:
In-Depth Analysis: The Balancer V2 Exploit
In-depth Analysis and Reflections on the Resupply Protocol Attack Incident
Bybit $1.5B Hack: In-Depth Analysis of the Malicious Safe Wallet Upgrade Attack
These analyses are not just for public reports; they feed directly into our internal knowledge base. Our auditors constantly work with the latest attacker techniques and defensive strategies, not last year’s playbook.
3.3 Weaponizing Cutting-Edge Attack Research: Upgrading Our Audit Method Every Day
At BlockSec, exploit research never stops at a paper or a blog post. We turn it into systems and workflows.
-
We add the latest attack techniques to our internal attack simulation framework.
-
We automatically translate exploit primitives into detection rules.
-
We convert real-world exploit chains into fuzzing cases and symbolic execution cases.
-
We extract recurring exploitation patterns into audit checklists and reasoning templates.
We also document what we learn in our Security Incidents Library. It is a curated database of on-chain attack cases with losses over $100K. It is built for community learning.
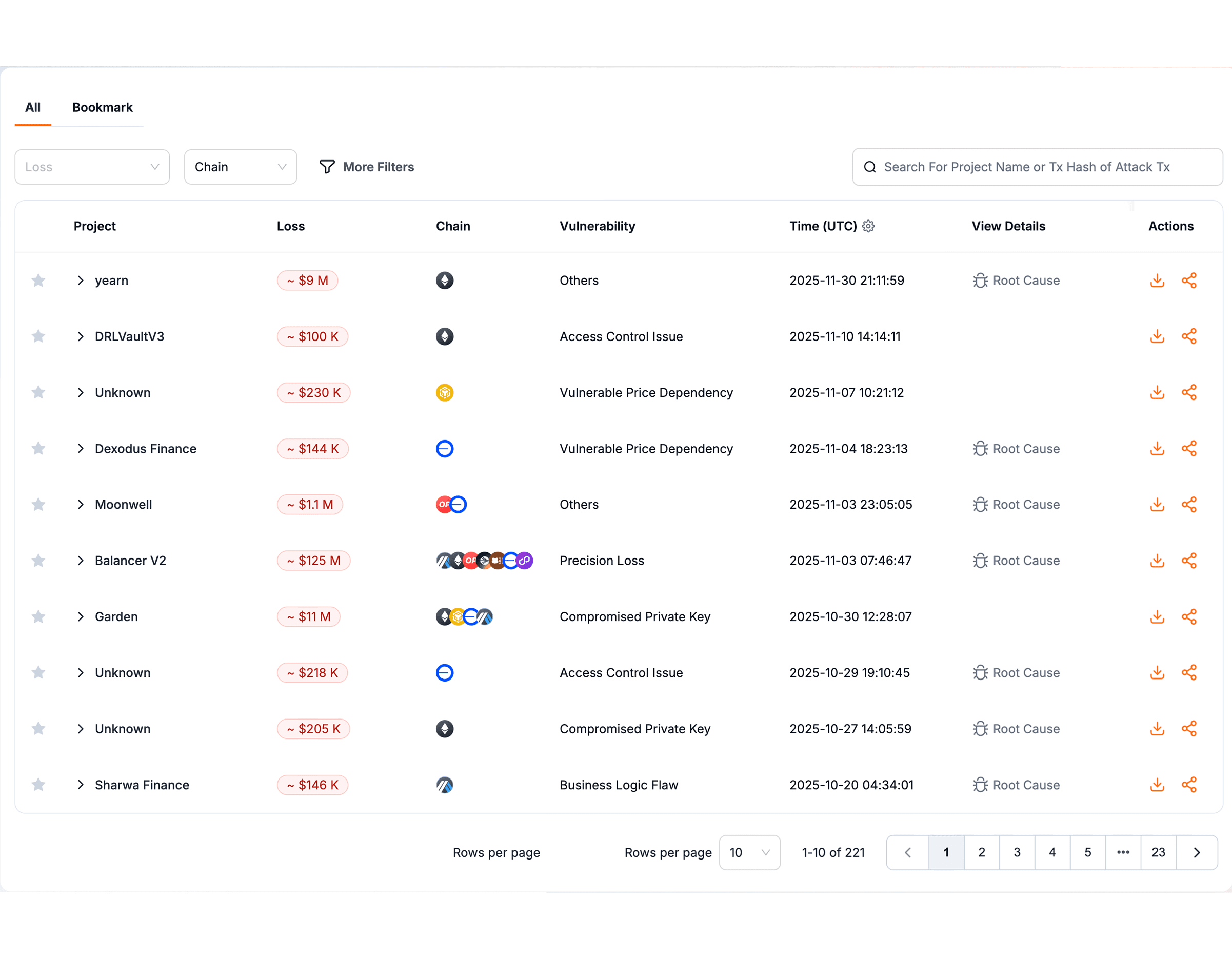
The result is simple: BlockSec auditors use latest attack methods to assess protocol risk. Our audit methodology is designed to evolve continuously alongside the threat landscape.
EVM Chain Audits: Building a Stronger Web3 Foundation
Smart contracts are the skyscrapers of Web3. Blockchain infrastructure is the foundation underneath. That includes L1s, rollups, cross-chain bridges, consensus protocols, and smart contract VMs. If the foundation has cracks, even the best apps will eventually fail.
Chain-level audits are inherently harder. They are at least an order of magnitude more complex than standard smart contract reviews. A serious infrastructure audit demands a system-level understanding of operating systems, networking, databases, virtual machines, cryptography, and consensus theory.
This is where BlockSec creates real separation from typical audit providers.
1. Deep expertise across the blockchain infrastructure stack.
Auditing blockchain infrastructure is not something you can do by “knowing Solidity.” It demands a system-level understanding of how a blockchain actually runs. This is where BlockSec has rare depth.
(1) Research Depth, Proven by Top-Tier Publications
BlockSec’s infrastructure research is published in top systems and security venues, such as:
-
USENIX ATC 2024 (top-tier systems conference)
-
EuroSys 2025 (top-tier European systems conference)
-
CCS 2024, including a Distinguished Paper Award (top-tier security conference)
These works cover topics such as:
-
EVM performance optimization with semantic consistency guarantees.
-
Security boundaries of Solana’s parallel execution model.
-
Exploit surfaces in high-performance node architectures.
-
Potential attack surfaces across Layer 2 systems.
(2) Invited Talks at Prestigious Infrastructure & Security Conferences
BlockSec has also been invited to present this work at major global conferences, such as:
-
DSS (a core blockchain security conference)
-
ACM DeFi (focused on DeFi security)
-
Black Hat (a premier security conference)
BlockSec is therefore not just an external auditor. We are an active contributor to the underlying blockchain infrastructure itself.
You can find our research at: https://blocksec.com/research
2. Our Key Edge: Differential Testing and Fuzzing
Infrastructure systems are too complex to rely on manual review alone. BlockSec has built a full-cycle automated testing pipeline that has been successfully applied to leading public chains such as MegaETH and EOS.
-
Differential testing engine: We use our own differential-testing framework to compare a client implementation against a reference such as Geth. Even tiny state inconsistencies can eventually cause consensus divergence and chain forks. Differential testing is one of the most effective tools for exposing deep, latent bugs.
-
Customized fuzzing: We build protocol-specific fuzzing systems that bombard nodes with hundreds of millions of random and malformed inputs. The goal is to trigger crashes, assertion failures, or undefined behavior before attackers discover them.
3. Battle-Tested Results: Seven-Figure Bug Bounties and Multi-Chain Zero-Day Discoveries
These techniques have uncovered high-severity vulnerabilities in major ecosystems including Solana VM, Aurora, Moonbeam, and Filecoin. Across these findings, BlockSec has received over USD 1M in bug bounties. These are evidence that we are not just “good at auditing,” but capable of discovering true zero-day vulnerabilities in blockchain infrastructure.
BlockSec’s Core Advantage: Where Academic Rigor Meets Hacker Thinking
Why BlockSec? Because security is ultimately an adversarial game—people versus people. BlockSec has a top team of skilled security researchers, PhDs, and experienced white-hat hackers.
Our audits are not assembly-line work. They are expert-led and tailored, shaped like real offensive and defensive exercises. Each project is reviewed by at least four independent auditors. Then, an audit supervisor leads a formal cross-review process to double-check the findings.
1. Academic Foundation: Research-Driven, Evidence-Based
In blockchain security, scale is not the advantage. Understanding is. You need strong fundamentals. You need to know how attacks evolve. Furthermore, you need to spot systemic risk before it turns into loss. That insight comes from years of research, strong publications, and a good talent pipeline.
BlockSec’s core team includes security researchers, PhDs, and master’s graduates from leading universities worldwide. We work continuously on blockchain security and smart contract analysis. We’ve published over 50 papers in leading international venues. These include IEEE S&P, USENIX Security, NDSS, and CCS. These papers push the research frontier. They also feed directly into industry practice. You can find our research at: https://blocksec.com/research
We also collaborate closely with universities in Hong Kong SAR and Mainland China and beyond:
-
Co-building joint Web3 security research labs [Link1 Link2 Link3]
-
Sponsor the BlockSec Blockchain Security Award [Link1 Link2]
-
Co-supervising master’s and PhD students in Web3 security [See BlockSec Research]
-
Co-authoring research proposals that have received support from the Hong Kong Innovation and Technology Commission
This is our method: research at the core, impact in the field. It keeps our perspective ahead of the curve. It helps us find the root causes of systemic risk. And it is a key reason we have stayed technically leading in this space.
2. Hacker Thinking: A System-Level, Risk-Oriented Audit Method
Blockchain security is not a simple “more code, more bugs” problem. It is an adversarial game. You have to divide limited resources from an attacker’s point of view. The real threats come from attack surfaces that can cause serious, widespread losses. That’s why BlockSec uses a risk-oriented approach to set audit priorities.
At the start of an engagement, we work closely with the project team. We map the system and its threat model. Then we focus on the modules that have the greatest financial impact, the most complexity, and the key business logic. Typical examples include:
-
Core treasury/vault contracts that custody user funds
-
Permission management for token minting and burning
-
Complex cross-chain bridge logic
-
Core governance contracts
From a hacker’s perspective, these components are the command centers of the system. If one of them falls, the damage is systemic and often irreversible.
By focusing effort on these high-value targets, and applying a layered, staged review strategy, we ensure that the protocol’s most critical and fragile components receive the strongest protection. Our goal is clear: identify and neutralize systemic risks with maximum precision.
3. Better Tools, Better Audits: Combining Static/Dynamic Analysis with LLM-Driven Next-Gen Automation
Entering the AI era does not mean large language models can solve security on their own. On the contrary, they do offer powerful new ways to amplify human expertise.
Traditional static and dynamic analysis tools are excellent at matching precise code patterns and identifying known vulnerability classes. LLMs, on the other hand, are better at understanding semantics, reasoning over long-range context, and explaining why a particular behavior is risky.
By combining the two, we significantly expand coverage and analytical depth, especially for subtle logic flaws and complex exploit paths.
BlockSec deeply integrates mature static/dynamic analysis with LLM capabilities. We build our own next-generation automated detection tools. And we embed them directly into our audit workflow. The result is higher audit efficiency and much stronger security research productivity.
4. Continuous Collaboration and Closed-Loop Delivery: Beyond a Report, Full-Lifecycle Security Support
An audit is not a one-off transaction. In Web3, real risk starts compounding after deployment. Liquidity moves. User behavior shifts. External dependencies change. Each of these can open new attack surfaces.
BlockSec’s delivery is therefore never “just a report.” It is a full lifecycle, closed-loop security service.
4.1 Fix Validation: Closing the Loop from Findings to Resolution
For every issue, we don’t state the conclusion. We provide impact analysis, likely exploit paths, and remediation guidance aligned with best practices and industry standards. After fixes are implemented, we run second-round verification on the updated code.
We maintain frequent, direct communication with the project’s engineering team. The goal is to make sure vulnerabilities are truly fixed, not noted as “resolved” in a document.
Fix validation is a required step in BlockSec’s audit process. It is not optional.
4.2 Ongoing Advisory: Your Long-Term Security Partner
Security needs change as Web3 products iterate. BlockSec helps teams during the audit and continues to support after launch. This includes:
-
New-feature advisory (e.g., governance modules, cross-chain flows, token models/tokenomics).
-
Security reviews for upgrade and rollout paths.
-
Parameter tuning and economic model optimization advice.
-
Risk analysis for contract migration and refactoring.
-
Security judgment for specific adversarial scenarios (MEV, arbitrage, and extreme on-chain states).
Our goal is not to hand over a report. It is to help the protocol stay secure under real market conditions.
4.3 On-Chain Attack Monitoring: Powered by Phalcon’s “War-Grade” Detection
BlockSec has a key advantage: Phalcon Security. It’s a top-notch system for real-time on-chain monitoring. It was forged in real offensive and defensive engagements. It brings zero-day detection and automated response capabilities.
In short, BlockSec doesn’t deliver an audit report. We deliver a full lifecycle security loop:
Find vulnerabilities → Confirm fixes → Monitor risk → Respond to attacks → Continuously upgrade
Only this closed-loop ability can make a Web3 protocol strong in a real-world hostile environment.
Conclusion: Make Security Your Advantage
Web3 is full of uncertainty. Security is the one constant.
BlockSec has proven its capability in real incidents. We’ve worked with 500+ teams. And we help protect tens of billions of dollars in on-chain assets.
Choose BlockSec, and you get more than a report. You get an elite security team. It’s built from PhDs, white-hat hackers, and senior engineers. We use differential testing, fuzzing, static and dynamic analysis, and advanced reasoning to help you identify landmines, build defenses, and stay ahead of attackers.
To request a smart contract audit or EVM chain audit, visit:https://blocksec.com/expert-contact?service=codeAuditingService
BlockSec helps your project stay secure—from launch to long-term operation.




