Our internal analysis tool found a bug in Tether Gold contract on April 5th, which allows an attacker to transfer anyone’s XAUt (Tether Gold) token to a predefined address. The team received our report and said they had located this issue internally. Today we found that the issue has been fixed, and we want to share the details here. Also, we will illustrate how to use Phalcon Fork to develop and debug the PoC of this vulnerability.
0x0. The vulnerability
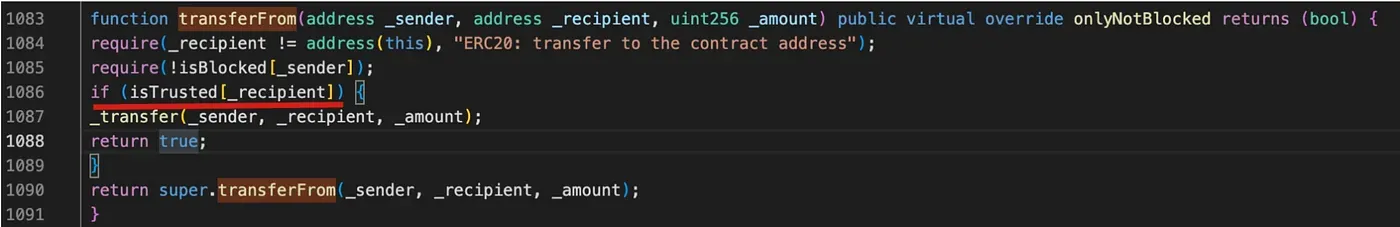
In the transferFrom function of the contract, anyone can invoke this function to transfer other users’ tokens into a trusted receipt defined by the token Owner. Though this vulnerability cannot be directly exploited to transfer the tokens to the attacker’s account, the attacker can still transfer the pool’s token to manipulate the token price in the pool (say WETH-XAUt pool) to profit.
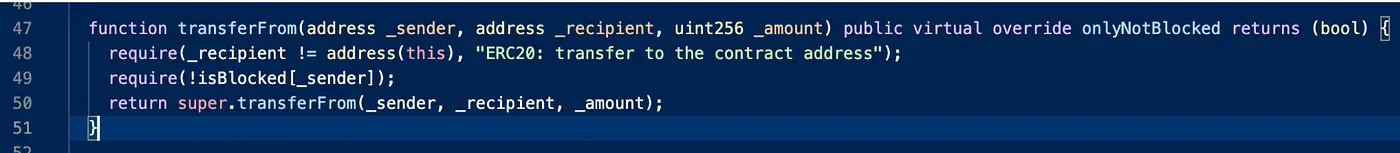
The fix to this vulnerability is straightforward, as shown in the following.
0x1. How to exploit the vulnerability
To write and debug the PoC, we can use the Phalcon Fork for this purpose. First, we can create a Fork before the vulnerability is patched. I used the block height 17038763 when creating the Fork through the Fork API.
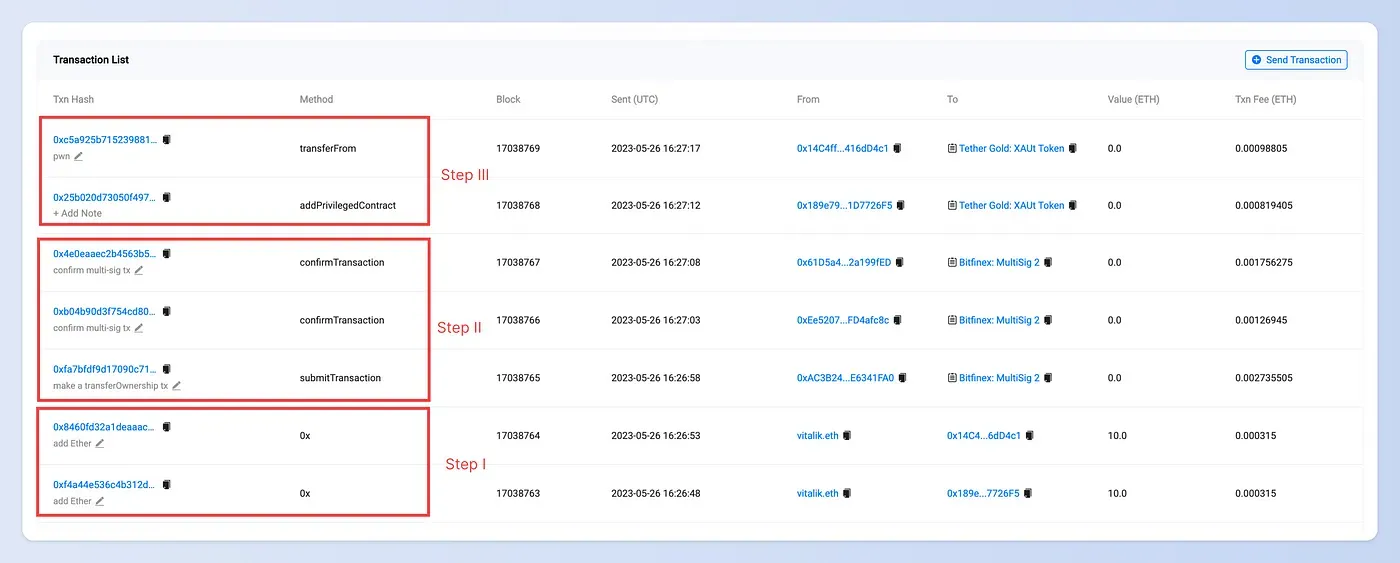
Step I: prepare enough Ether
The first step is to get enough Ether for the gas fee for the exploiter. If there is no Ether in the account, the transaction that sends Ether from the vitalik.eth will be issued.
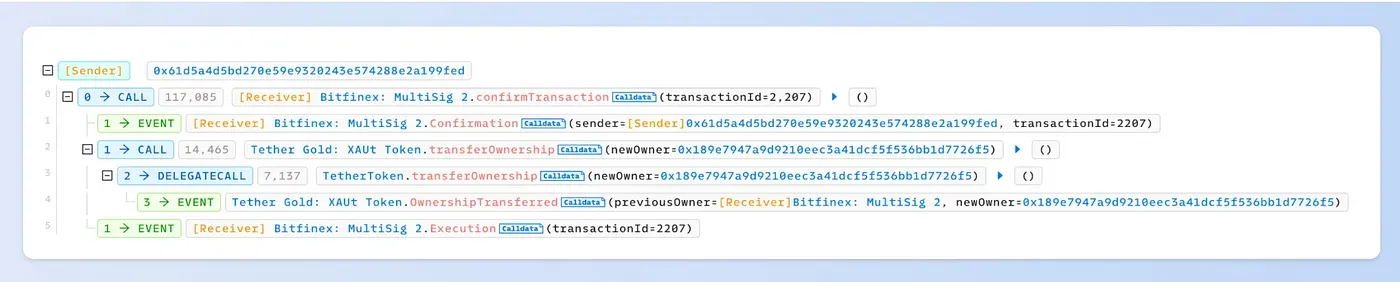
Step II: transfer the ownership of the Tether Gold contract
The owner of the Tether Gold contract is a multisig wallet (0xC6CDE7C39eB2f0F0095F41570af89eFC2C1Ea828). To transfer the ownership to the exploiter, we need to submit a multisig transaction and then confirm the transaction.
Step III: Add a privileged account to the Tether Gold contract
We added a new account 0x189e7947a9d9210eec3a41dcf5f536bb1d7726f5 as a privileged account. And then, we invoke the transferFrom function to transfer the XAUt token from a victim to the privileged account.
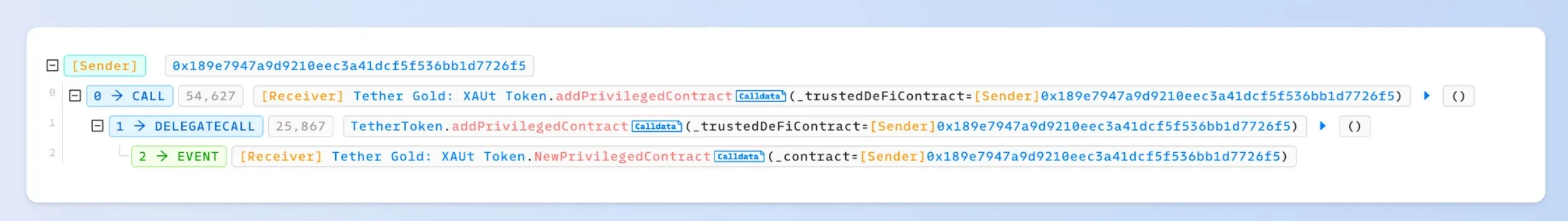
0x2. PoC
Please find the PoC on this github:




