A new academic paper, "Unmasking the Shadow Economy: A Deep Dive into Drainer-as-a-Service Phishing on Ethereum," has provided the first systematic look into a sophisticated criminal enterprise plaguing the Web3 space. This joint research by Zhejiang University and Mohamed bin Zayed University of Artificial Intelligence (MBZUAI) uncovers the mechanics of "Drainer-as-a-Service" (DaaS)—a thriving underground economy that has stolen over 💲135 million from 76,582 victims.
We at BlockSec are especially proud that the paper's first author, Bowen He, conducted part of this pivotal research during his internship with our team.
The DaaS Business Model: Industrializing Cybercrime
Unlike traditional, ad-hoc phishing, DaaS operates like a structured B2B software company. The paper details a clear operational pipeline:
- Operators (The Developers): These are the masterminds who develop and maintain sophisticated "wallet drainer" toolkits. These kits include phishing website templates and, crucially, automated profit-sharing smart contracts.
- Affiliates (The Distributors): They "lease" or acquire these toolkits. Their job is to deploy the phishing sites and drive traffic, luring victims through social media, fake airdrops, and compromised accounts.
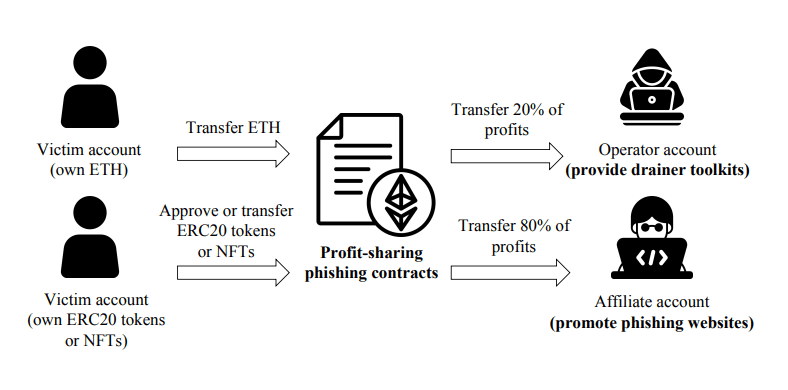
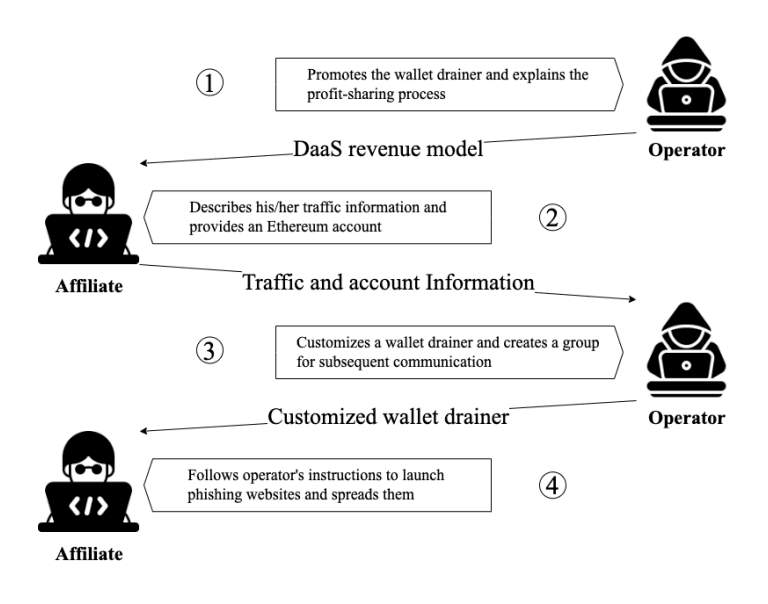 Once a victim is deceived into signing a malicious transaction, the stolen funds are automatically divided by the smart contract. The paper finds that the most common split is 20% to the operator and 80% to the affiliate. This high commission powerfully incentivizes affiliates to maximize their reach and scale the attacks, fueling the entire ecosystem.
Once a victim is deceived into signing a malicious transaction, the stolen funds are automatically divided by the smart contract. The paper finds that the most common split is 20% to the operator and 80% to the affiliate. This high commission powerfully incentivizes affiliates to maximize their reach and scale the attacks, fueling the entire ecosystem.
Mapping a $135M Heist: The "Snowball Sampling" Approach
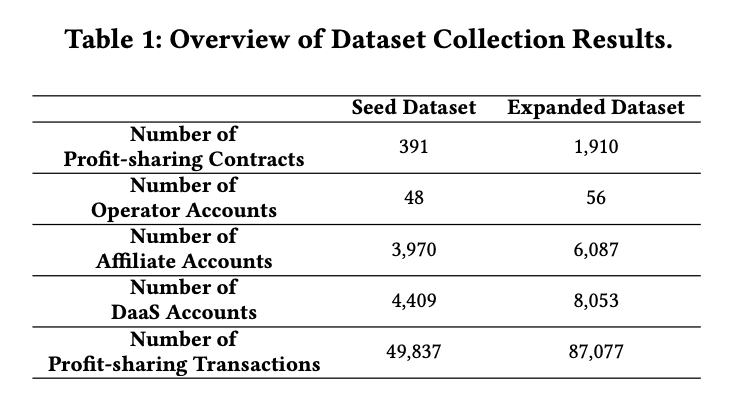
To quantify this shadow economy, the researchers developed an innovative "snowball sampling" approach. Starting from a seed set of known phishing addresses, they traced on-chain profit-sharing transactions to recursively discover new operators, affiliates, and contracts.
The findings from March 2023 to April 2025 are staggering:
-
● Total Stolen: 💲135 million ($23.1M for operators, $111.9M for affiliates)
-
● Criminal Infrastructure: 1,910 profit-sharing contracts and 87,077 profit-sharing transactions.
-
● Criminal Network: 56 core operator accounts and 6,087 affiliate accounts.
The attacks are technically sophisticated. The paper reveals that drainers use different methods depending on the asset:
-
● For ETH: Victims are tricked into calling a payable function (e.g., named "claim" or "mint").
-
● For ERC-20s & NFTs: Phishing sites prompt victims to approve their assets to the drainer contract. The operator then uses a TransferFrom function to execute multiple transfer calls in a single transaction, draining various assets at once.
The Dominant Crime Families
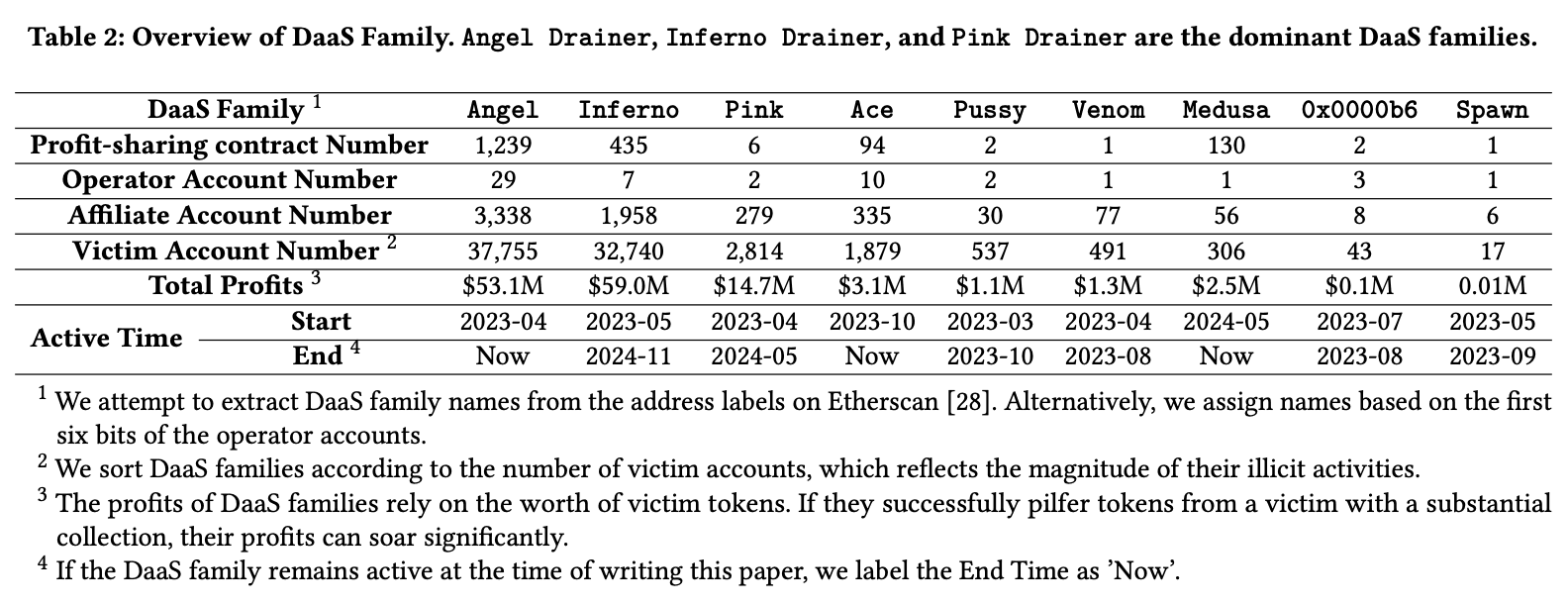
The DaaS landscape is not a fragmented market. The research identifies nine major "families," with three groups dominating the network and capturing 93.9% of all illicit profits:
- Angel Drainer ($53.1M)
- Inferno Drainer ($59.0M)
- Pink Drainer ($14.7M)
 These are not just brand names; they are distinct organizations with unique operational strategies. The paper highlights how they manage their affiliate networks:
These are not just brand names; they are distinct organizations with unique operational strategies. The paper highlights how they manage their affiliate networks:
-
● Advanced Management: Top families like Angel and Inferno Drainer provide affiliates with dedicated admin panels to track their earnings in real-time.
-
● Gamified Incentives: They employ leveling systems. For instance, Inferno Drainer categorizes affiliates into tiers based on profit ($10k, $100k, $1M), offering top-tier members better support and rewards.
-
● Bonus Rewards: To motivate performance, Angel Drainer randomly awards NFTs to high-earning affiliates, while Inferno Drainer periodically gives out rewards in ETH and even BTC to top performers.
A Massive Security Blind Spot
Using toolkit file fingerprints and monitoring Certificate Transparency logs for suspicious domain names, the researchers actively hunted for DaaS websites. They successfully identified and reported 32,819 phishing sites.
However, the most alarming discovery was the inadequacy of current industry defenses. The study found that only 10.8% of the DaaS-related addresses in their dataset were previously flagged on public trackers like Etherscan. This reveals a vast blind spot, allowing these criminal networks to operate with relative impunity.
Why This Research Is a Critical Wake-Up Call
The DaaS phenomenon proves that Web3 phishing has evolved from a simple scam into an industrialized, service-based criminal economy. It expertly exploits the permissionless and composable nature of DeFi for malicious ends.
This research underscores an urgent need for multi-layered security:
-
● Proactive Threat Detection: Going beyond simple blacklists to identify criminal infrastructure as it's being built.
-
● Advanced Wallet Security: Implementing robust transaction simulation and clear, human-readable warnings before users sign away their assets.
-
● Ecosystem-Wide Collaboration: Creating faster, more comprehensive channels for sharing threat intelligence and labeling malicious addresses.
This research marks a turning point. Phishing on Ethereum is no longer a side hustle—it’s an industrialized, revenue-sharing economy operating in plain sight. At BlockSec, we will continue to leverage cutting-edge research to build the next generation of security tools that can effectively counter these evolving, professionalized threats.
See the paper: https://assets.blocksec.com/pdf/1761189308551-2.pdf




