
The BabySwap and TransitSwap on BSC were attacked on October 1. Some attack transactions were front-run by a Bot. Interestingly, this bot was susceptible to the profanity tool vulnerability, and we successfully recovered its private key. We also managed to reverse-engineer the bot contract and withdraw the funds from the bot contract to our secure account. We have transferred the funds to TransitSwap and are connecting BabySwap at the current stage.
The detection of the attack to BabySwap
On 2022–10–01 14:47 (UTC), our internal system reported an attack transaction. Our further analysis showed that this is due to the controlled factories in the smart router contract. However, we did not disclose the details at that time since the project was still vulnerable. We contacted BabySwap through Twitter DM and TG but got no response.
During the investigation, we found this transaction was issued by a bot account, which front-run the original attack transaction. Also, this account has a pattern with eight leading zeros, looks like it’s generated by the profanity tool, which is vulnerable to the profanity tool vulnerability.
The recovery of the private key of the bot
On 2022–10–01 16:10 (UTC), our tool successfully recovered the private key of this bot in around 20 minutes. For the recovered private key, we transferred the funds to a secure account (which is the typical process of our rescue). Otherwise, others who also recover the private key can take over the account, and the funds in the account will be at risk.
Transfer the funds out the bot
The challenge is that the funds are in the contract deployed by the bot instead of the bot EOA account itself. How to transfer the funds is a challenge.
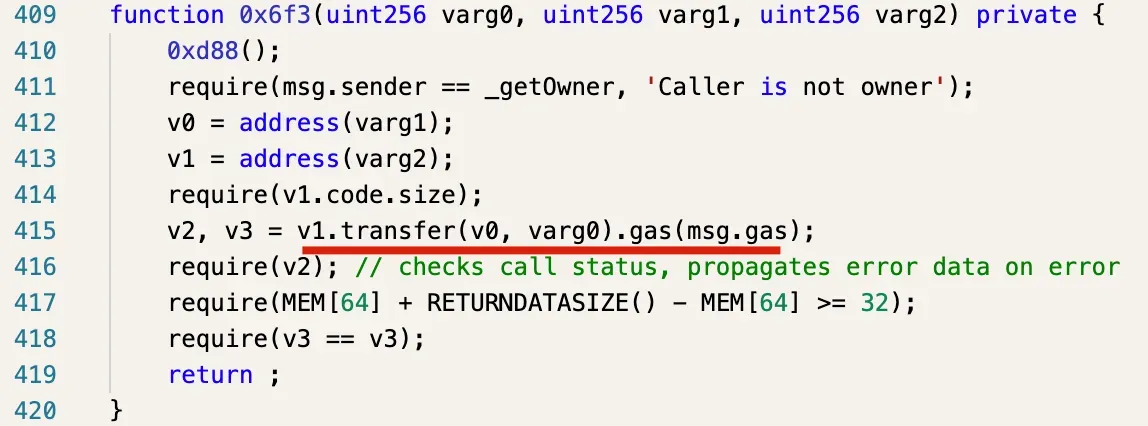
We decompiled the contract and found that there is a withdraw function in the contract (as shown in the following figure).

This function can be leveraged to withdraw the funds in the contract. The first argument is the token address, and the second argument should be zero.
We sent a transaction and successfully withdrawn the funds from the contract to the bot and then transferred the funds to our secure account.
Here comes another attack!
A couple of hours later, our system reported another attack on the TransSwap. There are a couple of attack transactions from different addresses, and one transaction was front-run by this bot again! However, since the contract deployed by the bot is a different one, the function to transfer the funds out is different.
Return the funds
After internal deliberation, we decided to return the funds to attacked projects (instead of the bot) for the following reasons.
- First, the funds are obtained by the bot through the attack on vulnerable contracts. Though the bot front-ran the attack transaction (instead of launching the attack in the first place), we still think the front-running transaction of an attack transaction is also an attack.
- Second, the funds belong to the victims of the attack, i.e., the users of the affected DeFi protocols. Users suffered a lot due to the vulnerability in the DeFi protocol. They should receive the funds from the attackers.
We have transferred the funds to the official TransitFinance Funds Receiver address and are contacting BabySwap.
Update of the rescue
We are still in the process of rescuing vulnerable addresses. The challenge is that you cannot tell whether an address is vulnerable before recovering its private key. Even though we have an optimized algorithm, due to the limitation of computing power, we still need more time to finish the whole rescue. We will release a detailed report later to deliberate the whole process and answer the following questions.
- How many addresses are vulnerable?
- What’s the impact of the vulnerability, i.e., how many assets are at risk due to the vulnerability?
- What’s the whole situation of the attack of this vulnerability?
Stay tuned and safe.
About BlockSec
BlockSec is a pioneering blockchain security company established in 2021 by a group of globally distinguished security experts. The company is committed to enhancing security and usability for the emerging Web3 world in order to facilitate its mass adoption. To this end, BlockSec provides smart contract and EVM chain security auditing services, the Phalcon platform for security development and blocking threats proactively, the MetaSleuth platform for fund tracking and investigation, and MetaSuites extension for web3 builders surfing efficiently in the crypto world.
To date, the company has served over 300 esteemed clients such as MetaMask, Uniswap Foundation, Compound, Forta, and PancakeSwap, and received tens of millions of US dollars in two rounds of financing from preeminent investors, including Matrix Partners, Vitalbridge Capital, and Fenbushi Capital.
Official website: https://blocksec.com/
Official Twitter account: https://twitter.com/BlockSecTeam




